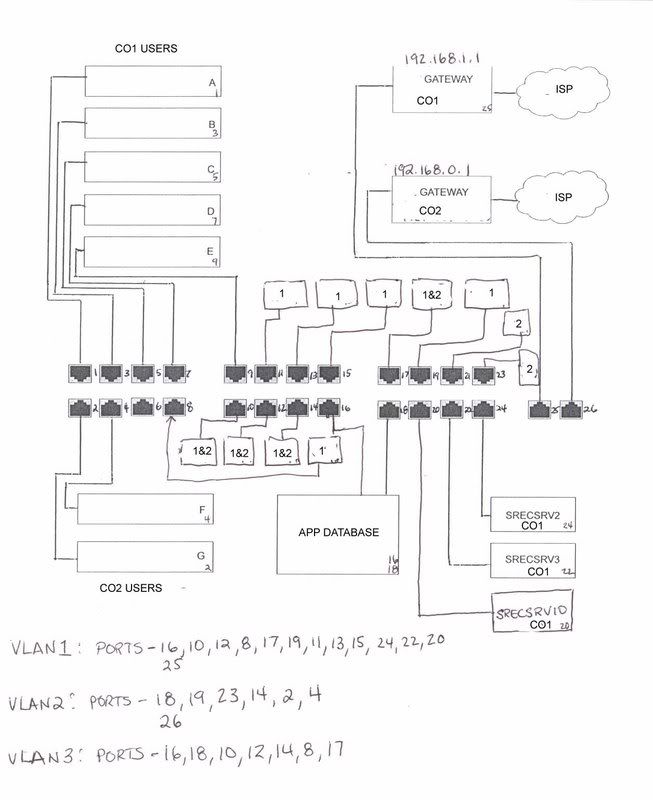
We have two companies who share a financial database application. At one point both were connected to the same LAN and there were no issues. Well, the bosses decided to give me one day to reconfigure the network and separate both companies onto two separate LANs (each with their own ISP). That went all well and fine but now I have to also allow a handful of users access to this shared application database.
LAN 1 is 192.168.1.1, workgroup CO1 and LAN 2 is 192.168.1.2, workgroup CO2. The application database is workgroup APP.
The application database has two NICs, one connected to LAN 1 with a static IP of .26, gateway 192.168.1.1 and one connected to LAN 2 with a static IP of .36, gateway 192.168.1.2.
From either LAN I can ping BOTH NICs. LAN 1 (the original LAN) connects without any issues, but LAN 2 has issues connecting at times. I normally have to reboot the computer, open up a command line and ping the .36 NIC, then browse to the application database box and then open the application to connect to the database. If I try doing this without these steps it cannot find the path to the application database (even though I can always ping both NICs).
So in a nutshell I need a way for users to connect to this database without having to go through all these steps.
Any thoughts? (Sorry if I didn't explain it well... it's still convoluted in my brain.... )















 Sign In
Sign In Create Account
Create Account

