So, we'll just put those tidbits of information aside for the time being.
What I would like to know is your opinion based on your experience.
What has given you problems for whatever reason. etc.
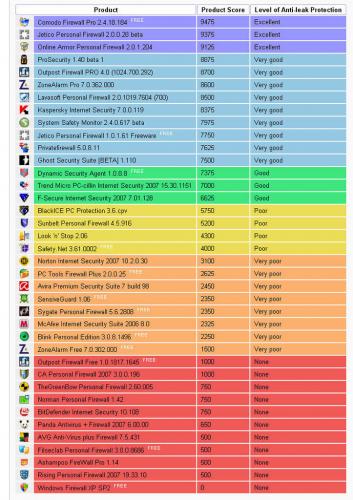
That, and the chart might be useful.
I'm concerned at how so-called 'Firewalls' only guard against threats coming in.
Seems like once a program latches onto your system, most firewalls will allow it to 'phone home' at will.














 Sign In
Sign In Create Account
Create Account

