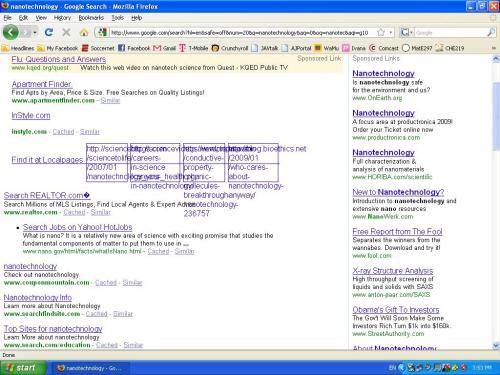
Now my Google seems to be hijacked; the search result does not match with the keyword.
I searched for "nanotechnology" and usually the first on the results is Wikipedia, but now the results give me links such as couponmountain.com, apartmentfinder.com, tazinga.com, myoptumhealth.com etc.
Attached is the screenshot of the search result in google.
Following is the Malwarebytes log:
Malwarebytes' Anti-Malware 1.41
Database version: 2991
Windows 5.1.2600 Service Pack 2
10/19/2009 2:35:10 PM
mbam-log-2009-10-19 (14-35-10).txt
Scan type: Quick Scan
Objects scanned: 94046
Time elapsed: 4 minute(s), 45 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 1
Registry Keys Infected: 4
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 4
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
C:\WINDOWS\system32\iehelper.dll (Trojan.Vundo.H) -> Delete on reboot.
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{f5f14e7a-f59d-45a0-bdc5-a9f5454f0bcf} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{f5f14e7a-f59d-45a0-bdc5-a9f5454f0bcf} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{f5f14e7a-f59d-45a0-bdc5-a9f5454f0bcf} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\AvScan (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\system tool (Rogue.Installer) -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\iehelper.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\Program Files\adqmuo\kwnxsysguard.exe (Rogue.Installer) -> Quarantined and deleted successfully.
C:\Documents and Settings\Windows XP\Local Settings\Temporary Internet Files\Content.IE5\GXYT8HIL\op[1].exe (Rogue.Installer) -> Quarantined and deleted successfully.
C:\WINDOWS\syssvc.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Next scan after system reboot:
Malwarebytes' Anti-Malware 1.41
Database version: 2991
Windows 5.1.2600 Service Pack 2
10/19/2009 3:20:41 PM
mbam-log-2009-10-19 (15-20-41).txt
Scan type: Full Scan (C:\|D:\|)
Objects scanned: 141774
Time elapsed: 34 minute(s), 21 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Edited by andytheo, 19 October 2009 - 05:27 PM.

 This topic is locked
This topic is locked













 Sign In
Sign In Create Account
Create Account

