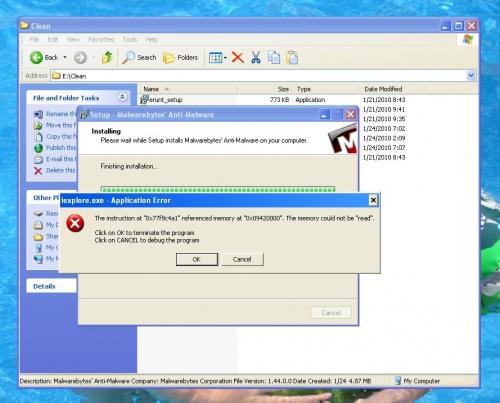
I'd appreciate any help with this! THANKS!!!
Here is my Hijack this log:
________________________________________________
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 9:41:09, on 1/21/2010
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Safe mode with network support
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Lavasoft\Ad-Aware\AAWService.exe
C:\WINDOWS\Explorer.EXE
C:\Program Files\Adobe\Acrobat 8.0\Acrobat\Acrobat.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
E:\Clean\Howdy.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.yahoo.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft....k/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft....k/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft....k/?LinkId=54896
R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://go.microsoft....k/?LinkId=74005
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = *.local
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll
O2 - BHO: Adobe PDF Conversion Toolbar Helper - {AE7CD045-E861-484f-8273-0445EE161910} - C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll
O2 - BHO: Java™ Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O2 - BHO: JQSIEStartDetectorImpl - {E7E6F031-17CE-4C07-BC86-EABFE594F69C} - C:\Program Files\Java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
O3 - Toolbar: Adobe PDF - {47833539-D0C5-4125-9FA8-0819E2EAAC93} - C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll
O4 - HKLM\..\Run: [ccApp] "C:\Program Files\Common Files\Symantec Shared\ccApp.exe"
O4 - HKLM\..\Run: [vptray] C:\PROGRA~1\SYMANT~1\VPTray.exe
O4 - HKLM\..\Run: [IAAnotif] "C:\Program Files\Intel\Intel Matrix Storage Manager\Iaanotif.exe"
O4 - HKLM\..\Run: [Adobe_ID0EYTHM] C:\PROGRA~1\COMMON~1\Adobe\ADOBEV~1\Server\bin\VERSIO~2.EXE
O4 - HKLM\..\Run: [AGRSMMSG] AGRSMMSG.exe
O4 - HKLM\..\Run: [IgfxTray] C:\WINDOWS\system32\igfxtray.exe
O4 - HKLM\..\Run: [HotKeysCmds] C:\WINDOWS\system32\hkcmd.exe
O4 - HKLM\..\Run: [Persistence] C:\WINDOWS\system32\igfxpers.exe
O4 - HKLM\..\Run: [Acrobat Assistant 8.0] "C:\Program Files\Adobe\Acrobat 8.0\Acrobat\Acrotray.exe"
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [Ad-Watch] C:\Program Files\Lavasoft\Ad-Aware\AAWTray.exe
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKLM\..\Run: [iTunesHelper] "C:\Program Files\iTunes\iTunesHelper.exe"
O4 - HKLM\..\Run: [SunJavaUpdateSched] "C:\Program Files\Java\jre6\bin\jusched.exe"
O4 - HKLM\..\Run: [lekarutay] Rundll32.exe "c:\windows\system32\rudajeki.dll",a
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O4 - HKCU\..\Run: [extrac64_cab.exe] C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\extrac64_cab.exe
O4 - Startup: ERUNT AutoBackup.lnk = C:\Program Files\ERUNT\AUTOBACK.EXE
O8 - Extra context menu item: Append to existing PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
O8 - Extra context menu item: Convert link target to Adobe PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
O8 - Extra context menu item: Convert link target to existing PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
O8 - Extra context menu item: Convert selected links to Adobe PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
O8 - Extra context menu item: Convert selected links to existing PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
O8 - Extra context menu item: Convert selection to Adobe PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
O8 - Extra context menu item: Convert selection to existing PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
O8 - Extra context menu item: Convert to Adobe PDF - res://C:\Program Files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~2\Office12\EXCEL.EXE/3000
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~2\Office12\REFIEBAR.DLL
O9 - Extra button: AIM - {AC9E2541-2814-11d5-BC6D-00B0D0A1DE45} - C:\Program Files\AIM\aim.exe
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search && Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O14 - IERESET.INF: START_PAGE_URL=http://www.gc.peachnet.edu
O15 - Trusted Zone: http://gil.gsc.edu
O15 - Trusted Zone: http://mail.gsc.edu
O15 - Trusted Zone: http://webmail.gsc.edu
O15 - Trusted Zone: http://www.gsc.edu
O15 - Trusted Zone: http://data.gc.peachnet.edu
O15 - Trusted Zone: http://mail.gc.peachnet.edu
O15 - Trusted Zone: http://titan.gc.peachnet.edu
O15 - Trusted Zone: http://troy.gc.peachnet.edu
O15 - Trusted Zone: http://webmail.gc.peachnet.edu
O15 - Trusted Zone: http://www.gc.peachnet.edu
O15 - Trusted Zone: http://vista.uga.edu
O15 - Trusted Zone: http://*.view.usg.edu
O15 - Trusted Zone: http://webct.usg.edu
O16 - DPF: {0CCA191D-13A6-4E29-B746-314DEE697D83} (Facebook Photo Uploader 5 Control) - http://upload.facebo...toUploader5.cab
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.mi...b?1189700275796
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://update.micros...b?1189700230250
O16 - DPF: {6F15128C-E66A-490C-B848-5000B5ABEEAC} (HP Download Manager) - https://h20436.www2....re/HPDEXAXO.cab
O16 - DPF: {8100D56A-5661-482C-BEE8-AFECE305D968} (Facebook Photo Uploader 5 Control) - http://upload.facebo...oUploader55.cab
O16 - DPF: {DF780F87-FF2B-4DF8-92D0-73DB16A1543A} (PopCapLoader Object) - http://l.yimg.com/jh...aploader_v6.cab
O20 - AppInit_DLLs: zarorero.dll c:\windows\system32\rudajeki.dll
O21 - SSODL: vukuvumiy - {b77ff2dd-e48d-441b-b911-f4dda1820c22} - c:\windows\system32\rudajeki.dll
O22 - SharedTaskScheduler: kupuhivus - {b77ff2dd-e48d-441b-b911-f4dda1820c22} - c:\windows\system32\rudajeki.dll
O23 - Service: Adobe Version Cue CS3 - Adobe Systems Incorporated - C:\Program Files\Common Files\Adobe\Adobe Version Cue CS3\Server\bin\VersionCueCS3.exe
O23 - Service: Apple Mobile Device - Apple Inc. - C:\Program Files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
O23 - Service: Bonjour Service - Apple Inc. - C:\Program Files\Bonjour\mDNSResponder.exe
O23 - Service: Symantec Event Manager (ccEvtMgr) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\ccEvtMgr.exe
O23 - Service: Symantec Settings Manager (ccSetMgr) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\ccSetMgr.exe
O23 - Service: Symantec AntiVirus Definition Watcher (DefWatch) - Symantec Corporation - C:\Program Files\Symantec AntiVirus\DefWatch.exe
O23 - Service: FLEXnet Licensing Service - Macrovision Europe Ltd. - C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe
O23 - Service: Intel® Matrix Storage Event Monitor (IAANTMON) - Intel Corporation - C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: iPod Service - Apple Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: Java Quick Starter (JavaQuickStarterService) - Sun Microsystems, Inc. - C:\Program Files\Java\jre6\bin\jqs.exe
O23 - Service: Lavasoft Ad-Aware Service - Lavasoft - C:\Program Files\Lavasoft\Ad-Aware\AAWService.exe
O23 - Service: LiveUpdate - Symantec Corporation - C:\PROGRA~1\Symantec\LIVEUP~1\LUCOMS~1.EXE
O23 - Service: PrismXL - New Boundary Technologies, Inc. - C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
O23 - Service: SAVRoam (SavRoam) - symantec - C:\Program Files\Symantec AntiVirus\SavRoam.exe
O23 - Service: Symantec Network Drivers Service (SNDSrvc) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\SNDSrvc.exe
O23 - Service: Symantec SPBBCSvc (SPBBCSvc) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\SPBBC\SPBBCSvc.exe
O23 - Service: Symantec AntiVirus - Symantec Corporation - C:\Program Files\Symantec AntiVirus\Rtvscan.exe
--
End of file - 10368 bytes

 This topic is locked
This topic is locked



















 Sign In
Sign In Create Account
Create Account

