Please help.
XP Internet Security 2010 [Solved]
#1
![XP Internet Security 2010 [Solved]: post #1](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 05 March 2010 - 03:17 PM
Posted 05 March 2010 - 03:17 PM

Please help.
#2
![XP Internet Security 2010 [Solved]: post #2](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 05 March 2010 - 05:39 PM
Posted 05 March 2010 - 05:39 PM

Database version: 3827
Windows 5.1.2600 Service Pack 2
Internet Explorer 6.0.2900.2180
3/5/2010 7:48:30 PM
mbam-log-2010-03-05 (19-48-30).txt
Scan type: Quick Scan
Objects scanned: 118447
Time elapsed: 10 minute(s), 20 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 3
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Edited by kelisjunky, 05 March 2010 - 07:50 PM.
#3
![XP Internet Security 2010 [Solved]: post #3](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 06 March 2010 - 06:51 AM
Posted 06 March 2010 - 06:51 AM

DO NOT use any TOOLS such as Combofix, Vundofix, or HijackThis fixes without supervision.
Doing so could make your pc inoperatible and could require a full reinstall of your OS, losing all your programs and data.
Vista and Windows 7 users:
1. These tools MUST be run from the executable. (.exe) every time you run them
2. With Admin Rights (Right click, choose "Run as Administrator")
Stay with this topic until I give you the all clean post.
You might want to print these instructions out.
I suggest you do this:
XP Users
Double-click My Computer.
Click the Tools menu, and then click Folder Options.
Click the View tab.
Uncheck "Hide file extensions for known file types."
Under the "Hidden files" folder, select "Show hidden files and folders."
Uncheck "Hide protected operating system files."
Click Apply, and then click OK.
Vista Users
To enable the viewing of hidden and protected system files in Windows Vista please follow these steps:
Close all programs so that you are at your desktop.
Click on the Start button. This is the small round button with the Windows flag in the lower left corner.
Click on the Control Panel menu option.
When the control panel opens you can either be in Classic View or Control Panel Home view:
If you are in the Classic View do the following:
Double-click on the Folder Options icon.
Click on the View tab.
If you are in the Control Panel Home view do the following:
Click on the Appearance and Personalization link.
Click on Show Hidden Files or Folders.
Under the Hidden files and folders section select the radio button labeled Show hidden files and folders.
Remove the checkmark from the checkbox labeled Hide extensions for known file types.
Remove the checkmark from the checkbox labeled Hide protected operating system files.
Please do not delete anything unless instructed to.
We've been seeing some Java infections lately.
Go here and follow the instructions to clear your Java Cache
Next:
Please download ATF Cleaner by Atribune.
Download - ATF Cleaner»
Double-click ATF-Cleaner.exe to run the program.
Under Main choose: Select All
Click the Empty Selected button.
[/list]If you use Firefox browserClick Firefox at the top and choose: Select All
Click the Empty Selected button.
NOTE: If you would like to keep your saved passwords, please click No at the prompt.
If you use Opera browserClick Opera at the top and choose: Select All
Click the Empty Selected button.
NOTE: If you would like to keep your saved passwords, please click No at the prompt.
Click Exit on the Main menu to close the program.
It's normal after running ATF cleaner that the PC will be slower to boot the first time.
Next:
Download ComboFix from one of these locations:
Link 1
Link 2 If using this link, Right Click and select Save As.
* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. Note: If you are having difficulty properly disabling your protective programs, or are unsure as to what programs need to be disabled, please refer to the information available through this link : Protective Programs
- Double click on ComboFix.exe & follow the prompts.
Notes: Combofix will run without the Recovery Console installed. Skip the Recovery Console part if you're running Vista or Windows 7.
Note: If you have SP3, use the SP2 package.If Vista or Windows 7, skip the Recovery Console part
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.

Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply.
Notes:
1.Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. ComboFix may reset a number of Internet Explorer's settings, including making I-E the default browser.
3. Combofix prevents autorun of ALL CD, floppy and USB devices to assist with malware removal & increase security. If this is an issue or makes it difficult for you -- please tell your helper.
4. CF disconnects your machine from the internet. The connection is automatically restored before CF completes its run. If CF runs into difficulty and terminates prematurely, the connection can be manually restored by restarting your machine.
Give it atleast 20-30 minutes to finish if needed.
Also please describe how your computer behaves at the moment.
#4
![XP Internet Security 2010 [Solved]: post #4](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 06 March 2010 - 04:33 PM
Posted 06 March 2010 - 04:33 PM

Microsoft Windows XP Home Edition 5.1.2600.2.1252.1.1033.18.1278.971 [GMT -6:00]
Running from: c:\documents and settings\Owner\Desktop\ComboFix.exe
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\recycler\S-1-5-21-1229272821-796845957-682003330-1003
c:\recycler\S-1-5-21-1229272821-796845957-682003330-1004
c:\windows\system32\_000110_.tmp.dll
.
original MBR restored successfully !
.
((((((((((((((((((((((((( Files Created from 2010-02-06 to 2010-03-06 )))))))))))))))))))))))))))))))
.
2010-03-06 01:35 . 2010-03-06 01:35 -------- d-----w- c:\documents and settings\Owner\Application Data\Malwarebytes
2010-03-06 01:35 . 2010-01-07 22:07 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2010-03-06 01:35 . 2010-03-06 01:35 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2010-03-06 01:35 . 2010-01-07 22:07 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2010-03-06 01:33 . 2010-03-06 01:34 -------- d-----w- c:\program files\ERUNT
2010-03-06 01:29 . 2010-03-06 01:29 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\VS Revo Group
2010-03-06 01:13 . 2010-03-06 01:13 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2010-03-06 00:45 . 2009-12-30 17:20 27064 ----a-w- c:\windows\system32\drivers\revoflt.sys
2010-03-04 19:04 . 2010-03-04 19:04 -------- d-----w- c:\documents and settings\Owner\Application Data\com.onebyonedesign.warbler.34E56A3B2F1D475AD2DBF2E6A17E88EEAA906703.1
2010-03-04 19:04 . 2010-03-04 19:04 -------- d-----w- c:\program files\Warbler
2010-02-20 20:00 . 2010-02-20 20:00 -------- d-----w- c:\program files\iPod
2010-02-20 19:52 . 2010-02-20 19:52 72488 ----a-w- c:\documents and settings\All Users\Application Data\Apple Computer\Installer Cache\iTunes 9.0.3.15\SetupAdmin.exe
2010-02-15 11:35 . 2010-02-15 11:41 -------- d---a-w- c:\documents and settings\All Users\Application Data\TEMP
2010-02-15 08:18 . 2010-02-21 10:16 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\Google
2010-02-15 08:17 . 2010-02-15 08:18 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\Deployment
2010-02-09 08:51 . 2010-01-30 16:48 266552 ----a-w- c:\windows\system32\HMIPCore.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2010-03-06 00:49 . 2009-02-27 23:36 -------- d-----w- c:\documents and settings\All Users\Application Data\Viewpoint
2010-03-06 00:45 . 2009-02-27 11:30 -------- d-----w- c:\program files\VS Revo Group
2010-03-04 19:59 . 2009-03-10 05:03 -------- d-----w- c:\program files\Common Files\Adobe AIR
2010-02-20 20:01 . 2009-10-14 22:19 -------- d-----w- c:\program files\iTunes
2010-02-20 20:00 . 2009-10-14 22:17 -------- d-----w- c:\program files\Common Files\Apple
2010-02-11 01:21 . 2009-09-24 08:13 78952 ---ha-w- c:\windows\system32\mlfcache.dat
2010-02-11 01:20 . 2009-10-14 22:20 -------- d-----w- c:\documents and settings\Owner\Application Data\Apple Computer
2010-02-06 23:31 . 2009-02-27 10:53 103344 -c--a-w- c:\documents and settings\Owner\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2010-01-17 20:29 . 2010-01-15 18:03 -------- d-----w- c:\program files\Common Files\AVSMedia
2010-01-15 17:39 . 2010-01-15 17:39 34 ---ha-w- c:\windows\system32\DVDRippper_sysquict.dat
2010-01-15 01:12 . 2010-01-15 01:09 -------- d-----w- c:\program files\Common Files\DVDVideoSoft
2010-01-12 18:25 . 2010-01-12 18:24 -------- d-----w- c:\documents and settings\Owner\Application Data\acccore
2010-01-12 18:23 . 2010-01-12 18:23 -------- d-----w- c:\documents and settings\All Users\Application Data\AIM
2010-01-12 18:23 . 2009-10-25 21:08 -------- d-----w- c:\program files\AIM
2010-01-12 18:23 . 2010-01-12 18:23 -------- d-----w- c:\program files\Common Files\AOL
2010-01-12 00:09 . 2010-01-12 00:09 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstWA\unins000.exe
2010-01-12 00:09 . 2010-01-11 22:21 275 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\uninst2.bat
2010-01-11 22:21 . 2010-01-11 22:21 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstWMP\unins000.exe
2010-01-11 22:21 . 2010-01-11 22:21 -------- d-----w- c:\documents and settings\All Users\Application Data\Last.fm
2010-01-11 22:21 . 2010-01-11 22:21 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstITW\unins000.exe
2010-01-11 22:21 . 2010-01-11 22:21 -------- d-----w- c:\program files\Last.fm
2010-01-02 18:28 . 2010-01-02 18:28 56 ---ha-w- c:\windows\system32\ezsidmv.dat
2009-12-31 16:14 . 2004-08-04 12:00 352640 ----a-w- c:\windows\system32\drivers\srv.sys
2009-12-22 05:42 . 2004-08-04 12:00 662016 ----a-w- c:\windows\system32\wininet.dll
2009-12-22 05:42 . 2009-03-19 18:13 81920 ----a-w- c:\windows\system32\ieencode.dll
2009-12-16 12:58 . 2009-12-01 16:19 343040 ----a-w- c:\windows\system32\mspaint.exe
2009-12-14 07:35 . 2004-08-04 12:00 33280 ----a-w- c:\windows\system32\csrsrv.dll
2009-12-08 18:55 . 2004-08-04 12:00 2180352 ----a-w- c:\windows\system32\ntoskrnl.exe
2009-12-08 18:19 . 2004-08-03 22:59 2057728 ----a-w- c:\windows\system32\ntkrnlpa.exe
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SoundMAXPnP"="c:\program files\Analog Devices\Core\smax4pnp.exe" [2004-10-14 1404928]
"Persistence"="c:\windows\system32\igfxpers.exe" [2005-04-05 114688]
"IgfxTray"="c:\windows\system32\igfxtray.exe" [2005-04-05 94208]
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\AdobeCS4ServiceManager]
2008-08-14 15:58 611712 ----a-w- c:\program files\Common Files\Adobe\CS4ServiceManager\CS4ServiceManager.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Google Update]
2010-02-21 10:15 135664 ----atw- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\HotKeysCmds]
2005-04-05 22:19 77824 ----a-w- c:\windows\system32\hkcmd.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\iTunesHelper]
2010-02-16 00:07 141608 ----a-w- c:\program files\iTunes\iTunesHelper.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2009-11-11 05:08 417792 ----a-w- c:\program files\QuickTime\QTTask.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched]
2009-07-25 10:23 149280 ----a-w- c:\program files\Java\jre6\bin\jusched.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\services]
"Themes"=2 (0x2)
"seclogon"=2 (0x2)
"Schedule"=2 (0x2)
"iPod Service"=3 (0x3)
"Apple Mobile Device"=2 (0x2)
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
"FirewallOverride"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"c:\\Program Files\\AIM\\aim.exe"=
"c:\\Program Files\\QuickTime\\QuickTimePlayer.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"5353:TCP"= 5353:TCP:Adobe CSI CS4
"65533:TCP"= 65533:TCP:Services
"52344:TCP"= 52344:TCP:Services
"2479:TCP"= 2479:TCP:Services
"7408:TCP"= 7408:TCP:Services
"3389:TCP"= 3389:TCP:Remote Desktop
"4286:TCP"= 4286:TCP:Services
"9957:TCP"= 9957:TCP:Services
"7833:TCP"= 7833:TCP:Services
"9613:TCP"= 9613:TCP:Services
"1848:TCP"= 1848:TCP:Services
"9519:TCP"= 9519:TCP:Services
"3246:TCP"= 3246:TCP:Services
"3817:TCP"= 3817:TCP:Services
"4036:TCP"= 4036:TCP:Services
"4426:TCP"= 4426:TCP:Services
"5536:TCP"= 5536:TCP:Services
"6020:TCP"= 6020:TCP:Services
"4348:TCP"= 4348:TCP:Services
S0 sptd;sptd;c:\windows\system32\drivers\sptd.sys [4/1/2009 3:10 AM 717296]
S3 ManyCam;ManyCam Virtual Webcam, WDM Video Capture Driver;c:\windows\system32\DRIVERS\ManyCam.sys --> c:\windows\system32\DRIVERS\ManyCam.sys [?]
S3 Revoflt;Revoflt;c:\windows\system32\drivers\revoflt.sys [3/5/2010 6:45 PM 27064]
.
Contents of the 'Scheduled Tasks' folder
2010-02-21 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1715567821-1284227242-725345543-1003Core.job
- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2010-02-21 10:15]
2010-02-21 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1715567821-1284227242-725345543-1003UA.job
- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2010-02-21 10:15]
.
.
------- Supplementary Scan -------
.
uStart Page = about:blank
uInternet Connection Wizard,ShellNext = iexplore
uInternet Settings,ProxyServer = 218.247.198.99:80
uInternet Settings,ProxyOverride = plimus.com,www.plimus.com,regnow.com,www.regnow.com,
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\Office12\EXCEL.EXE/3000
FF - ProfilePath - c:\documents and settings\Owner\Application Data\Mozilla\Firefox\Profiles\ciox11z7.default\
FF - prefs.js: browser.search.selectedEngine - Ask.com
FF - prefs.js: browser.startup.homepage - google.com
FF - prefs.js: keyword.URL - hxxp://www.google.com/search?ie=UTF-8&oe=UTF-8&sourceid=navclient&gfns=1&q=
FF - prefs.js: network.proxy.socks - 127.0.0.1
FF - prefs.js: network.proxy.socks_port - 7070
FF - prefs.js: network.proxy.type - 4
FF - plugin: c:\documents and settings\Owner\Application Data\Move Networks\plugins\npqmp071505000010.dll
FF - plugin: c:\documents and settings\Owner\Application Data\Move Networks\plugins\npqmp071505000011.dll
FF - plugin: c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\1.2.183.13\npGoogleOneClick8.dll
.
- - - - ORPHANS REMOVED - - - -
Toolbar-{D4027C7F-154A-4066-A1AD-4243D8127440} - (no file)
WebBrowser-{D4027C7F-154A-4066-A1AD-4243D8127440} - (no file)
HKCU-Run-AdobeBridge - (no file)
AddRemove-Adobe ConnectNow Add-in - c:\documents and settings\Owner\Application Data\Macromedia\Flash Player\www.macromedia.com\bin\acaddin\acaddin.exe
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2010-03-06 16:26
Windows 5.1.2600 Service Pack 2 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
called modules: ntoskrnl.exe catchme.sys CLASSPNP.SYS disk.sys >>UNKNOWN [0x8922E4A0]<<
kernel: MBR read successfully
detected MBR rootkit hooks:
\Driver\Disk -> CLASSPNP.SYS @ 0xf763bfc3
\Driver\ACPI -> ACPI.sys @ 0xf75aecb8
\Driver\atapi -> 0x8922e4a0
IoDeviceObjectType -> DeleteProcedure -> ntoskrnl.exe @ 0x805a0084
ParseProcedure -> ntoskrnl.exe @ 0x8056f07e
\Device\Harddisk0\DR0 -> DeleteProcedure -> ntoskrnl.exe @ 0x805a0084
ParseProcedure -> ntoskrnl.exe @ 0x8056f07e
NDIS: Intel® PRO/100 VE Network Connection -> SendCompleteHandler -> 0x892b3330
PacketIndicateHandler -> NDIS.sys @ 0xf7454b21
SendHandler -> NDIS.sys @ 0xf743287b
Warning: possible MBR rootkit infection !
copy of MBR has been found in sector 0x03940F59
malicious code @ sector 0x03940F5C !
PE file found in sector at 0x03940F72 !
MBR rootkit infection detected ! Use: "mbr.exe -f" to fix.
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-1715567821-1284227242-725345543-1003\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{8A2887A0-D974-9904-9A73-1D7B66BD3A58}*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
"nahljpifgieeajennmhhjkgmgpoh"=hex:6b,61,6b,64,6f,6c,69,63,6b,69,63,6c,62,64,
69,62,61,6f,6c,6e,6a,6c,00,00
"mablpnjmfdginknafgopomjfak"=hex:6b,61,6d,64,62,6b,6c,61,63,6d,64,6b,6a,6a,70,
70,63,64,6b,6b,6e,6c,00,00
.
Completion time: 2010-03-06 16:29:17
ComboFix-quarantined-files.txt 2010-03-06 22:29
Pre-Run: 7,408,095,232 bytes free
Post-Run: 7,374,704,640 bytes free
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Home Edition" /noexecute=optin /fastdetect
- - End Of File - - FAF4DD69430BEBE47FFCC5830D833EE8
And at the moment, I'm not getting any of the fake virus scan pop-ups that I would get before I scanned it with MBAM.
Edited by kelisjunky, 06 March 2010 - 04:34 PM.
#5
![XP Internet Security 2010 [Solved]: post #5](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 06 March 2010 - 08:14 PM
Posted 06 March 2010 - 08:14 PM

Please download HelpAsst_mebroot_fix.exe and save it to your desktop.
Close out all other open programs and windows.
Double click the file to run it and follow any prompts.
If the tool detects an mbr infection, please allow it to run mbr -f and shutdown your computer.
Upon restarting, please wait about 5 minutes, click Start>Run and type the following bolded command, then hit Enter.
helpasst -mbrt
Make sure you leave a space between helpasst and -mbrt !
When it completes, a log will open.
Please post the contents of that log.
In the event the tool does not detect an mbr infection and completes, click Start>Run and type the following bolded command, then hit Enter.
mbr -f
Now, please do the Start>Run>mbr -f command a second time.
Now shut down the computer (do not restart, but shut it down), wait a few minutes then start it back up.
Give it about 5 minutes, then click Start>Run and type the following bolded command, then hit Enter.
helpasst -mbrt
Make sure you leave a space between helpasst and -mbrt !
When it completes, a log will open.
Please post the contents of that log.
**Important note to Dell users - fixing the mbr may prevent access the the Dell Restore Utility, which allows you to press a key on startup and revert your computer to a factory delivered state. There are a couple of known fixes for said condition, though the methods are somewhat advanced. If you are unwilling to take such a risk, you should not allow the tool to execute mbr -f nor execute the command manually, and you will either need to restore your computer to a factory state or allow your computer to remain having an infected mbr (the latter not recommended).
Edited by ldtate, 06 March 2010 - 09:32 PM.
#6
![XP Internet Security 2010 [Solved]: post #6](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 06 March 2010 - 11:45 PM
Posted 06 March 2010 - 11:45 PM

Sat 03/06/2010 at 23:23:03.23
HelpAssistant account was found to be Active ~ attempting to de-activate
Full Name Remote Desktop Help Assistant Account
Account active Yes
Local Group Memberships *Administrators
The command completed successfully.
HelpAssistant account successfully set inactive
termsrv32.dll found ~ attempting to remove
HelpAssistant profile found in registry ~ backing up and removing S-1-5-21-1715567821-1284227242-725345543-1000
HelpAssistant profile directory exists at C:\Documents and Settings\HelpAssistant ~ attempting to remove
Remove on reboot: C:\WINDOWS\system32\termsrv32.dll
~ All C:\Documents and Settings\HelpAssistant files successfully removed ~
~~ Checking mbr ~~
mbr infection detected! ~ running mbr -f
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
kernel: MBR read successfully
detected MBR rootkit hooks:
\Driver\atapi -> 0x8922e4a0
NDIS: Intel® PRO/100 VE Network Connection -> SendCompleteHandler -> 0x892b3330
Warning: possible MBR rootkit infection !
copy of MBR has been found in sector 0x03940F59
malicious code @ sector 0x03940F5C !
PE file found in sector at 0x03940F72 !
MBR rootkit infection detected ! Use: "mbr.exe -f" to fix.
original MBR restored successfully !
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
kernel: MBR read successfully
detected MBR rootkit hooks:
\Driver\atapi -> 0x8922e4a0
NDIS: Intel® PRO/100 VE Network Connection -> SendCompleteHandler -> 0x892b3330
Warning: possible MBR rootkit infection !
user & kernel MBR OK
copy of MBR has been found in sector 0x03940F59
malicious code @ sector 0x03940F5C !
PE file found in sector at 0x03940F72 !
Use "Recovery Console" command "fixmbr" to clear infection !
user & kernel MBR OK
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Status check on Sat 03/06/2010 at 23:42:35.93
Full Name Remote Desktop Help Assistant Account
Account active No
Local Group Memberships
The command completed successfully.
~~ Checking mbr ~~
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
called modules: ntoskrnl.exe CLASSPNP.SYS disk.sys >>UNKNOWN [0x8972C1F8]<<
kernel: MBR read successfully
detected MBR rootkit hooks:
\Driver\atapi -> 0x8972c1f8
Warning: possible MBR rootkit infection !
user & kernel MBR OK
copy of MBR has been found in sector 0x03940F59
malicious code @ sector 0x03940F5C !
PE file found in sector at 0x03940F72 !
Use "Recovery Console" command "fixmbr" to clear infection !
~~ Checking for termsrv32.dll ~~
termsrv32.dll was not found
HKEY_LOCAL_MACHINE\system\currentcontrolset\services\termservice\parameters
ServiceDll REG_EXPAND_SZ %systemroot%\System32\termsrv.dll
~~ Checking for HelpAssistant directories ~~
none found
~~ Checking firewall ports ~~
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"65533:TCP"=65533:TCP:*:Enabled:Services
"52344:TCP"=52344:TCP:*:Enabled:Services
"2479:TCP"=2479:TCP:*:Enabled:Services
"7408:TCP"=7408:TCP:*:Enabled:Services
"3389:TCP"=3389:TCP:*:Enabled:Remote Desktop
"4286:TCP"=4286:TCP:*:Enabled:Services
"9957:TCP"=9957:TCP:*:Enabled:Services
"7833:TCP"=7833:TCP:*:Enabled:Services
"9613:TCP"=9613:TCP:*:Enabled:Services
"1848:TCP"=1848:TCP:*:Enabled:Services
"9519:TCP"=9519:TCP:*:Enabled:Services
"3246:TCP"=3246:TCP:*:Enabled:Services
"3817:TCP"=3817:TCP:*:Enabled:Services
"4036:TCP"=4036:TCP:*:Enabled:Services
"4426:TCP"=4426:TCP:*:Enabled:Services
"5536:TCP"=5536:TCP:*:Enabled:Services
"6020:TCP"=6020:TCP:*:Enabled:Services
"4348:TCP"=4348:TCP:*:Enabled:Services
~~ EOF ~~
#7
![XP Internet Security 2010 [Solved]: post #7](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 07:15 AM
Posted 07 March 2010 - 07:15 AM

Here's how to do that:
Click Start > Run type Notepad click OK.
This will open an empty notepad file:
Take your mouse, and place your cursor at the beginning of the text in the box below, then click and hold the left mouse button, while pulling your mouse over the text. This should highlight the text. Now release the left mouse button. Now, with the cursor over the highlighted text, right click the mouse for options, and select 'copy'. Now over the empty Notepad box, right click your mouse again, and select 'paste' and you will have copied and pasted the text.
Registry:: [HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List] "65533:TCP"=- "52344:TCP"=- "2479:TCP"=- "7408:TCP"=- "3389:TCP"=- "4286:TCP"=- "9957:TCP"=- "7833:TCP"=- "9613:TCP"=- "1848:TCP"=- "9519:TCP"=- "3246:TCP"=- "3817:TCP"=- "4036:TCP"=- "4426:TCP"=- "5536:TCP"=- "6020:TCP"=- "4348:TCP"=-
Save this file to your desktop, Save this as "CFScript"
Here's how to do that:
1.Click File;
2.Click Save As... Change the directory to your desktop;
3.Change the Save as type to "All Files";
4.Type in the file name: CFScript
5.Click Save ...

Drag CFScript.txt into ComboFix.exe
Then post the results log using Copy / Paste
Also please describe how your computer behaves at the moment.
#8
![XP Internet Security 2010 [Solved]: post #8](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 08:58 AM
Posted 07 March 2010 - 08:58 AM

Microsoft Windows XP Home Edition 5.1.2600.2.1252.1.1033.18.1278.983 [GMT -6:00]
Running from: c:\documents and settings\Owner\Desktop\ComboFix.exe
Command switches used :: c:\documents and settings\Owner\Desktop\CFScript.txt
.
((((((((((((((((((((((((( Files Created from 2010-02-07 to 2010-03-07 )))))))))))))))))))))))))))))))
.
2010-03-07 05:23 . 2010-03-07 05:23 -------- d-----w- C:\HelpAsst_backup
2010-03-06 01:35 . 2010-03-06 01:35 -------- d-----w- c:\documents and settings\Owner\Application Data\Malwarebytes
2010-03-06 01:35 . 2010-01-07 22:07 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2010-03-06 01:35 . 2010-03-06 01:35 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2010-03-06 01:35 . 2010-01-07 22:07 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2010-03-06 01:33 . 2010-03-06 01:34 -------- d-----w- c:\program files\ERUNT
2010-03-06 01:29 . 2010-03-06 01:29 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\VS Revo Group
2010-03-06 01:13 . 2010-03-06 01:13 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2010-03-06 00:45 . 2009-12-30 17:20 27064 ----a-w- c:\windows\system32\drivers\revoflt.sys
2010-03-04 19:04 . 2010-03-04 19:04 -------- d-----w- c:\documents and settings\Owner\Application Data\com.onebyonedesign.warbler.34E56A3B2F1D475AD2DBF2E6A17E88EEAA906703.1
2010-03-04 19:04 . 2010-03-04 19:04 -------- d-----w- c:\program files\Warbler
2010-02-20 20:00 . 2010-02-20 20:00 -------- d-----w- c:\program files\iPod
2010-02-20 19:52 . 2010-02-20 19:52 72488 ----a-w- c:\documents and settings\All Users\Application Data\Apple Computer\Installer Cache\iTunes 9.0.3.15\SetupAdmin.exe
2010-02-15 11:35 . 2010-02-15 11:41 -------- d---a-w- c:\documents and settings\All Users\Application Data\TEMP
2010-02-15 08:18 . 2010-02-21 10:16 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\Google
2010-02-15 08:17 . 2010-02-15 08:18 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\Deployment
2010-02-09 08:51 . 2010-01-30 16:48 266552 ----a-w- c:\windows\system32\HMIPCore.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2010-03-06 00:49 . 2009-02-27 23:36 -------- d-----w- c:\documents and settings\All Users\Application Data\Viewpoint
2010-03-06 00:45 . 2009-02-27 11:30 -------- d-----w- c:\program files\VS Revo Group
2010-03-04 19:59 . 2009-03-10 05:03 -------- d-----w- c:\program files\Common Files\Adobe AIR
2010-02-20 20:01 . 2009-10-14 22:19 -------- d-----w- c:\program files\iTunes
2010-02-20 20:00 . 2009-10-14 22:17 -------- d-----w- c:\program files\Common Files\Apple
2010-02-11 01:21 . 2009-09-24 08:13 78952 ---ha-w- c:\windows\system32\mlfcache.dat
2010-02-11 01:20 . 2009-10-14 22:20 -------- d-----w- c:\documents and settings\Owner\Application Data\Apple Computer
2010-02-06 23:31 . 2009-02-27 10:53 103344 -c--a-w- c:\documents and settings\Owner\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2010-01-17 20:29 . 2010-01-15 18:03 -------- d-----w- c:\program files\Common Files\AVSMedia
2010-01-15 17:39 . 2010-01-15 17:39 34 ---ha-w- c:\windows\system32\DVDRippper_sysquict.dat
2010-01-15 01:12 . 2010-01-15 01:09 -------- d-----w- c:\program files\Common Files\DVDVideoSoft
2010-01-12 18:25 . 2010-01-12 18:24 -------- d-----w- c:\documents and settings\Owner\Application Data\acccore
2010-01-12 18:23 . 2010-01-12 18:23 -------- d-----w- c:\documents and settings\All Users\Application Data\AIM
2010-01-12 18:23 . 2009-10-25 21:08 -------- d-----w- c:\program files\AIM
2010-01-12 18:23 . 2010-01-12 18:23 -------- d-----w- c:\program files\Common Files\AOL
2010-01-12 00:09 . 2010-01-12 00:09 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstWA\unins000.exe
2010-01-12 00:09 . 2010-01-11 22:21 275 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\uninst2.bat
2010-01-11 22:21 . 2010-01-11 22:21 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstWMP\unins000.exe
2010-01-11 22:21 . 2010-01-11 22:21 -------- d-----w- c:\documents and settings\All Users\Application Data\Last.fm
2010-01-11 22:21 . 2010-01-11 22:21 683801 ----a-w- c:\documents and settings\All Users\Application Data\Last.fm\Client\UninstITW\unins000.exe
2010-01-11 22:21 . 2010-01-11 22:21 -------- d-----w- c:\program files\Last.fm
2010-01-02 18:28 . 2010-01-02 18:28 56 ---ha-w- c:\windows\system32\ezsidmv.dat
2009-12-31 16:14 . 2004-08-04 12:00 352640 ----a-w- c:\windows\system32\drivers\srv.sys
2009-12-22 05:42 . 2004-08-04 12:00 662016 ------w- c:\windows\system32\wininet.dll
2009-12-22 05:42 . 2009-03-19 18:13 81920 ----a-w- c:\windows\system32\ieencode.dll
2009-12-16 12:58 . 2009-12-01 16:19 343040 ----a-w- c:\windows\system32\mspaint.exe
2009-12-14 07:35 . 2004-08-04 12:00 33280 ----a-w- c:\windows\system32\csrsrv.dll
2009-12-08 18:55 . 2004-08-04 12:00 2180352 ------w- c:\windows\system32\ntoskrnl.exe
2009-12-08 18:19 . 2004-08-03 22:59 2057728 ------w- c:\windows\system32\ntkrnlpa.exe
.
((((((((((((((((((((((((((((( SnapShot@2010-03-06_22.26.46 )))))))))))))))))))))))))))))))))))))))))
.
+ 2010-03-07 14:42 . 2010-03-07 14:42 16384 c:\windows\Temp\Perflib_Perfdata_770.dat
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SoundMAXPnP"="c:\program files\Analog Devices\Core\smax4pnp.exe" [2004-10-14 1404928]
"Persistence"="c:\windows\system32\igfxpers.exe" [2005-04-05 114688]
"IgfxTray"="c:\windows\system32\igfxtray.exe" [2005-04-05 94208]
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\AdobeCS4ServiceManager]
2008-08-14 15:58 611712 ----a-w- c:\program files\Common Files\Adobe\CS4ServiceManager\CS4ServiceManager.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Google Update]
2010-02-21 10:15 135664 ----atw- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\HotKeysCmds]
2005-04-05 22:19 77824 ----a-w- c:\windows\system32\hkcmd.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\iTunesHelper]
2010-02-16 00:07 141608 ----a-w- c:\program files\iTunes\iTunesHelper.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2009-11-11 05:08 417792 ----a-w- c:\program files\QuickTime\QTTask.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched]
2009-07-25 10:23 149280 ----a-w- c:\program files\Java\jre6\bin\jusched.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\services]
"Themes"=2 (0x2)
"seclogon"=2 (0x2)
"Schedule"=2 (0x2)
"iPod Service"=3 (0x3)
"Apple Mobile Device"=2 (0x2)
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
"FirewallOverride"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"c:\\Program Files\\AIM\\aim.exe"=
"c:\\Program Files\\QuickTime\\QuickTimePlayer.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"5353:TCP"= 5353:TCP:Adobe CSI CS4
S0 sptd;sptd;c:\windows\system32\drivers\sptd.sys [4/1/2009 3:10 AM 717296]
S3 ManyCam;ManyCam Virtual Webcam, WDM Video Capture Driver;c:\windows\system32\DRIVERS\ManyCam.sys --> c:\windows\system32\DRIVERS\ManyCam.sys [?]
S3 Revoflt;Revoflt;c:\windows\system32\drivers\revoflt.sys [3/5/2010 6:45 PM 27064]
.
Contents of the 'Scheduled Tasks' folder
2010-02-21 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1715567821-1284227242-725345543-1003Core.job
- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2010-02-21 10:15]
2010-02-21 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1715567821-1284227242-725345543-1003UA.job
- c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2010-02-21 10:15]
.
.
------- Supplementary Scan -------
.
uStart Page = about:blank
uInternet Connection Wizard,ShellNext = iexplore
uInternet Settings,ProxyServer = 218.247.198.99:80
uInternet Settings,ProxyOverride = plimus.com,www.plimus.com,regnow.com,www.regnow.com,
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\Office12\EXCEL.EXE/3000
FF - ProfilePath - c:\documents and settings\Owner\Application Data\Mozilla\Firefox\Profiles\ciox11z7.default\
FF - prefs.js: browser.search.selectedEngine - Ask.com
FF - prefs.js: browser.startup.homepage - google.com
FF - prefs.js: keyword.URL - hxxp://www.google.com/search?ie=UTF-8&oe=UTF-8&sourceid=navclient&gfns=1&q=
FF - prefs.js: network.proxy.socks - 127.0.0.1
FF - prefs.js: network.proxy.socks_port - 7070
FF - prefs.js: network.proxy.type - 4
FF - plugin: c:\documents and settings\Owner\Application Data\Move Networks\plugins\npqmp071505000010.dll
FF - plugin: c:\documents and settings\Owner\Application Data\Move Networks\plugins\npqmp071505000011.dll
FF - plugin: c:\documents and settings\Owner\Local Settings\Application Data\Google\Update\1.2.183.13\npGoogleOneClick8.dll
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2010-03-07 08:52
Windows 5.1.2600 Service Pack 2 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-1715567821-1284227242-725345543-1003\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{8A2887A0-D974-9904-9A73-1D7B66BD3A58}*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
"nahljpifgieeajennmhhjkgmgpoh"=hex:6b,61,6b,64,6f,6c,69,63,6b,69,63,6c,62,64,
69,62,61,6f,6c,6e,6a,6c,00,00
"mablpnjmfdginknafgopomjfak"=hex:6b,61,6d,64,62,6b,6c,61,63,6d,64,6b,6a,6a,70,
70,63,64,6b,6b,6e,6c,00,00
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'explorer.exe'(400)
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
Completion time: 2010-03-07 08:54:32
ComboFix-quarantined-files.txt 2010-03-07 14:54
ComboFix2.txt 2010-03-06 22:29
Pre-Run: 7,360,028,672 bytes free
Post-Run: 7,329,714,176 bytes free
- - End Of File - - 1D637361BE714CFF0A82366839C43D4D
My computer is behaving very well. It's runny faster and smoother than it has for the past month!
#9
![XP Internet Security 2010 [Solved]: post #9](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 09:07 AM
Posted 07 March 2010 - 09:07 AM

Please click Start>Run and type (or copy and paste it) the following bolded command then hit Enter.
helpasst -cleanup
Next:
click Start>Run and type (or copy and paste it) the following bolded command then hit Enter.
helpasst -mbrt
Post the log results
#10
![XP Internet Security 2010 [Solved]: post #10](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 09:37 AM
Posted 07 March 2010 - 09:37 AM

~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Status check on Sun 03/07/2010 at 9:36:13.59
Full Name Remote Desktop Help Assistant Account
Account active No
Local Group Memberships
The command completed successfully.
~~ Checking mbr ~~
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
called modules: ntoskrnl.exe catchme.sys CLASSPNP.SYS disk.sys atapi.sys hal.dll pciide.sys PCIIDEX.SYS
kernel: MBR read successfully
user & kernel MBR OK
copy of MBR has been found in sector 0x03940F59
malicious code @ sector 0x03940F5C !
PE file found in sector at 0x03940F72 !
~~ Checking for termsrv32.dll ~~
termsrv32.dll was not found
HKEY_LOCAL_MACHINE\system\currentcontrolset\services\termservice\parameters
ServiceDll REG_EXPAND_SZ %SystemRoot%\System32\termsrv.dll
~~ Checking for HelpAssistant directories ~~
none found
~~ Checking firewall ports ~~
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
~~ EOF ~~
#11
![XP Internet Security 2010 [Solved]: post #11](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 10:52 AM
Posted 07 March 2010 - 10:52 AM

The following will implement some cleanup procedures as well as reset System Restore points:
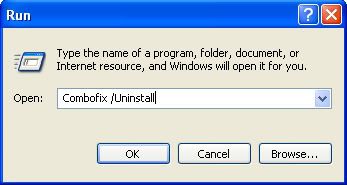
- Click START then RUN
- Now type ComboFix /Uninstall in the runbox and click OK. Note the space between the X and the U, it needs to be there.
If you used DeFogger
You must remember to re-enable your Emulation drivers once we are finished, double click DeFogger to run the tool.
- The application window will appear
- Click the Re-enable button to re-enable your CD Emulation drivers
- Click Yes to continue
- A 'Finished!' message will appear
- Click OK
- DeFogger will now ask to reboot the machine - click OK
Your Emulation drivers are now re-enabled.
To be on the safe side, I would also change all my passwords.
Here's my usual all clean post
Log looks good
- Make your Internet Explorer more secure - This can be done by following these simple instructions:
- From within Internet Explorer click on the Tools menu and then click on Options.
- Click once on the Security tab
- Click once on the Internet icon so it becomes highlighted.
- Click once on the Custom Level button.
- Change the Download signed ActiveX controls to Prompt
- Change the Download unsigned ActiveX controls to Disable
- Change the Initialize and script ActiveX controls not marked as safe to Disable
- Change the Installation of desktop items to Prompt
- Change the Launching programs and files in an IFRAME to Prompt
- Change the Navigate sub-frames across different domains to Prompt
- When all these settings have been made, click on the OK button.
- If it prompts you as to whether or not you want to save the settings, press the Yes button.
- Next press the Apply button and then the OK to exit the Internet Properties page.
- Update your AntiVirus Software - It is imperative that you update your Antivirus software at least once a week
(Even more if you wish). If you do not update your antivirus software then it will not be able to catch any of the new variants that may come out.
- Use a Firewall - I can not stress how important it is that you use a Firewall on your computer.
Without a firewall your computer is succeptible to being hacked and taken over.
I am very serious about this and see it happen almost every day with my clients.
Simply using a Firewall in its default configuration can lower your risk greatly.
- Visit Microsoft's Windows Update Site Frequently - It is important that you visit http://www.windowsupdate.com regularly.
This will ensure your computer has always the latest security updates available installed on your computer.
If there are new updates to install, install them immediately, reboot your computer, and revisit the site
until there are no more critical updates.
- Update all these programs regularly - Make sure you update all the programs I have listed regularly.
Without regular updates you WILL NOT be protected when new malicious programs are released.
Only run one Anti-Virus and Firewall program.
I would suggest you read How to Prevent Malware:
#12
![XP Internet Security 2010 [Solved]: post #12](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 11:48 AM
Posted 07 March 2010 - 11:48 AM

Is it okay if I uninstall ERUNT and at C: to delete the ComboFix and HelpAsst text document?
#13
![XP Internet Security 2010 [Solved]: post #13](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 11:50 AM
Posted 07 March 2010 - 11:50 AM

Yes.THANKS A TON!

Is it okay if I uninstall ERUNT and at C: to delete the ComboFix and HelpAsst text document?
You're more then welcome.
Glad we were able to help
Peace be with you
#14
![XP Internet Security 2010 [Solved]: post #14](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 07 March 2010 - 11:54 AM
Posted 07 March 2010 - 11:54 AM

If you're the topic starter, and need this topic reopened, please contact a staff member with the address of the thread.
Everyone else please begin a New Topic.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

