termdd.sys is causing problems
#16

 Posted 20 January 2011 - 12:06 AM
Posted 20 January 2011 - 12:06 AM

#17

 Posted 20 January 2011 - 01:10 AM
Posted 20 January 2011 - 01:10 AM

C:\System Volume Information\_restore{8F16AE75-B0A2-467D-BE94-DC58ABE28F43}\RP1\A0012658.ini Win32/Adware.AntimalwareDoctor.AE.Gen application cleaned by deleting - quarantined
C:\System Volume Information\_restore{8F16AE75-B0A2-467D-BE94-DC58ABE28F43}\RP3\A0014293.exe a variant of Win32/Kryptik.JMR trojan cleaned by deleting - quarantined
C:\WINDOWS\awurizevuladiw.dll a variant of Win32/Cimag.FK trojan cleaned by deleting - quarantined
C:\WINDOWS\debugcacheobj.exe a variant of Win32/Kryptik.JMR trojan cleaned by deleting - quarantined
C:\_OTL\MovedFiles\01192011_165838\C_Documents and Settings\All Users\Documents\Server\hlp.dat Win32/Bamital.DZ trojan cleaned by deleting - quarantined
Edited by Log2, 20 January 2011 - 01:10 AM.
#18

 Posted 20 January 2011 - 01:27 AM
Posted 20 January 2011 - 01:27 AM

#19

 Posted 20 January 2011 - 02:19 AM
Posted 20 January 2011 - 02:19 AM

OTL logfile created on: 1/20/2011 3:16:53 AM - Run 4
OTL by OldTimer - Version 3.2.20.2 Folder = C:\Documents and Settings\Computer\My Documents\Downloads
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.00 Gb Total Physical Memory | 2.00 Gb Available Physical Memory | 81.00% Memory free
4.00 Gb Paging File | 4.00 Gb Available in Paging File | 91.00% Paging File free
Paging file location(s): C:\pagefile.sys 1344 2688 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 74.52 Gb Total Space | 3.91 Gb Free Space | 5.25% Space Free | Partition Type: NTFS
Computer Name: B | User Name: Computer | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - C:\Documents and Settings\Computer\My Documents\Downloads\OTL.exe (OldTimer Tools)
PRC - C:\Program Files\Mozilla Firefox\firefox.exe (Mozilla Corporation)
PRC - C:\Program Files\uTorrent\uTorrent.exe (BitTorrent, Inc.)
PRC - C:\Program Files\Common Files\Real\Update_OB\realsched.exe (RealNetworks, Inc.)
PRC - C:\Program Files\DivX\DivX Update\DivXUpdate.exe ()
PRC - C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe (Apple Inc.)
PRC - C:\WINDOWS\explorer.exe (Microsoft Corporation)
========== Modules (SafeList) ==========
MOD - C:\Documents and Settings\Computer\My Documents\Downloads\OTL.exe (OldTimer Tools)
MOD - C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\Chrome\Hook\rpchromebrowserrecordhelper.dll ()
========== Win32 Services (SafeList) ==========
SRV - (wuauserv) -- File not found
SRV - (Apple Mobile Device) -- C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe (Apple Inc.)
========== Driver Services (SafeList) ==========
DRV - (TermDD) -- C:\WINDOWS\system32\drivers\termdd.sys ()
DRV - (nv) -- C:\WINDOWS\system32\drivers\nv4_mini.sys (NVIDIA Corporation)
DRV - (nvnnio) -- C:\WINDOWS\system32\drivers\nvnnio.sys (Novation Digital Music Systems Ltd.)
DRV - (IntcAzAudAddService) Service for Realtek HD Audio (WDM) -- C:\WINDOWS\system32\drivers\RtkHDAud.sys (Realtek Semiconductor Corp.)
DRV - (usbaudio) USB Audio Driver (WDM) -- C:\WINDOWS\system32\drivers\USBAUDIO.sys (Microsoft Corporation)
DRV - (HDAudBus) -- C:\WINDOWS\system32\drivers\hdaudbus.sys (Windows ® Server 2003 DDK provider)
DRV - (nvnetbus) -- C:\WINDOWS\system32\drivers\nvnetbus.sys (NVIDIA Corporation)
DRV - (NVENETFD) -- C:\WINDOWS\system32\drivers\NVENETFD.sys (NVIDIA Corporation)
DRV - (SBKUPNT) -- C:\WINDOWS\system32\drivers\SBKUPNT.SYS ()
DRV - (RVIEGVST) -- C:\Program Files\Roland\Virtual Sound Canvas VST\RVIEg01VST.sys (Roland)
DRV - (RVIEG01) -- C:\Program Files\Roland\Virtual Sound Canvas DXi\RVIEg01.sys (Roland)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.msn.com/
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://home.sweetim.com
IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyOverride" = *.local
========== FireFox ==========
FF - prefs.js..extensions.enabledItems: [email protected]:1.0
FF - prefs.js..extensions.enabledItems: {ABDE892B-13A8-4d1b-88E6-365A6E755758}:1.1.3
FF - HKLM\software\mozilla\Firefox\extensions\\{ABDE892B-13A8-4d1b-88E6-365A6E755758}: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\Firefox\Ext [2010/04/19 15:36:13 | 000,000,000 | ---D | M]
FF - HKLM\software\mozilla\Mozilla Firefox 3.6.13\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2010/12/30 23:56:21 | 000,000,000 | ---D | M]
FF - HKLM\software\mozilla\Mozilla Firefox 3.6.13\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins [2010/12/20 16:10:49 | 000,000,000 | ---D | M]
[2009/10/28 14:50:46 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Computer\Application Data\Mozilla\Extensions
[2011/01/19 17:37:59 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Computer\Application Data\Mozilla\Firefox\Profiles\ecxhcidf.default\extensions
[2010/04/29 22:08:47 | 000,000,000 | ---D | M] (Microsoft .NET Framework Assistant) -- C:\Documents and Settings\Computer\Application Data\Mozilla\Firefox\Profiles\ecxhcidf.default\extensions\{20a82645-c095-46ed-80e3-08825760534b}
[2011/01/19 17:37:59 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2010/04/19 15:36:13 | 000,000,000 | ---D | M] (RealPlayer Browser Record Plugin) -- C:\DOCUMENTS AND SETTINGS\ALL USERS\APPLICATION DATA\REAL\REALPLAYER\BROWSERRECORDPLUGIN\FIREFOX\EXT
[2009/10/28 14:12:20 | 000,000,000 | ---D | M] (Java Quick Starter) -- C:\PROGRAM FILES\JAVA\JRE6\LIB\DEPLOY\JQS\FF
O1 HOSTS File: ([2011/01/19 17:24:09 | 000,000,027 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (RealPlayer Download and Record Plugin for Internet Explorer) - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll (RealPlayer)
O4 - HKLM..\Run: [AppleSyncNotifier] C:\Program Files\Common Files\Apple\Mobile Device Support\AppleSyncNotifier.exe (Apple Inc.)
O4 - HKLM..\Run: [DivXUpdate] C:\Program Files\DivX\DivX Update\DivXUpdate.exe ()
O4 - HKLM..\Run: [NvCplDaemon] C:\WINDOWS\System32\NvCpl.DLL (NVIDIA Corporation)
O4 - HKLM..\Run: [TkBellExe] C:\Program Files\Common Files\Real\Update_OB\realsched.exe (RealNetworks, Inc.)
O4 - HKCU..\Run: [uTorrent] C:\Program Files\uTorrent\uTorrent.exe (BitTorrent, Inc.)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O10 - NameSpace_Catalog5\Catalog_Entries\000000000004 [] - C:\Program Files\Bonjour\mdnsNSP.dll (Apple Inc.)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_16)
O16 - DPF: {CAFEEFAC-0016-0000-0016-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_16)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_16)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.2.1
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O24 - Desktop WallPaper: C:\Documents and Settings\Computer\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O24 - Desktop BackupWallPaper: C:\Documents and Settings\Computer\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2009/10/28 13:16:05 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *) - File not found
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2011/01/20 01:02:12 | 000,000,000 | -HSD | C] -- C:\RECYCLER
[2011/01/19 18:20:57 | 000,000,000 | ---D | C] -- C:\Program Files\ESET
[2011/01/19 17:20:18 | 000,000,000 | RHSD | C] -- C:\cmdcons
[2011/01/19 17:18:28 | 000,212,480 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWXCACLS.exe
[2011/01/19 17:18:28 | 000,161,792 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWREG.exe
[2011/01/19 17:18:28 | 000,136,704 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWSC.exe
[2011/01/19 17:18:28 | 000,031,232 | ---- | C] (NirSoft) -- C:\WINDOWS\NIRCMD.exe
[2011/01/19 17:14:32 | 000,000,000 | ---D | C] -- C:\WINDOWS\ERDNT
[2011/01/19 17:11:33 | 000,000,000 | ---D | C] -- C:\Qoobox
[2011/01/19 17:06:26 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Computer\Desktop\New Folder
[2011/01/19 16:58:38 | 000,000,000 | ---D | C] -- C:\_OTL
[2011/01/18 17:23:06 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Computer\Application Data\SUPERAntiSpyware.com
[2011/01/18 17:23:06 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\SUPERAntiSpyware.com
[2011/01/18 17:16:04 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Computer\New Folder
[2011/01/18 16:39:03 | 000,038,224 | ---- | C] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbamswissarmy.sys
[2011/01/18 16:39:03 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Malwarebytes' Anti-Malware
[2011/01/18 16:39:00 | 000,020,952 | ---- | C] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbam.sys
[2011/01/18 16:39:00 | 000,000,000 | ---D | C] -- C:\Program Files\Malwarebytes' Anti-Malware2
[2011/01/18 16:27:40 | 000,000,000 | ---D | C] -- C:\WINDOWS\System32\CatRoot2
[2011/01/18 15:53:36 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\Motive
[2011/01/18 15:50:05 | 000,000,000 | ---D | C] -- C:\WINDOWS\System32\appmgmt
[2011/01/18 15:10:46 | 000,000,000 | -HSD | C] -- C:\WINDOWS\CSC
[2011/01/18 09:34:52 | 001,349,208 | ---- | C] (Kaspersky Lab ZAO) -- C:\Documents and Settings\Computer\Desktop\TDSSKiller.exe
[2010/12/21 20:05:55 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Computer\Start Menu\Programs\Disk Repair
[2010/12/21 18:49:29 | 000,000,000 | ---D | C] -- C:\Program Files\SweetIM
[2010/12/21 18:49:29 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\SweetIM
========== Files - Modified Within 30 Days ==========
[2011/01/20 02:48:00 | 000,000,890 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineUA.job
[2011/01/19 20:54:55 | 000,236,466 | ---- | M] () -- C:\WINDOWS\System32\NvApps.xml
[2011/01/19 20:54:43 | 000,001,374 | ---- | M] () -- C:\WINDOWS\System32\wpa.dbl
[2011/01/19 20:54:43 | 000,000,284 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeLogonTaskS-1-5-21-527237240-1960408961-725345543-1003.job
[2011/01/19 20:54:42 | 000,000,886 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineCore.job
[2011/01/19 20:43:40 | 000,002,048 | --S- | M] () -- C:\WINDOWS\bootstat.dat
[2011/01/19 19:31:17 | 000,000,292 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeScheduledTaskS-1-5-21-527237240-1960408961-725345543-1003.job
[2011/01/19 17:24:09 | 000,000,027 | ---- | M] () -- C:\WINDOWS\System32\drivers\etc\hosts
[2011/01/19 17:20:22 | 000,000,327 | RHS- | M] () -- C:\boot.ini
[2011/01/19 17:07:46 | 000,040,840 | ---- | M] () -- C:\WINDOWS\System32\drivers\termdd.sys
[2011/01/19 08:32:00 | 000,000,284 | ---- | M] () -- C:\WINDOWS\tasks\AppleSoftwareUpdate.job
[2011/01/18 18:44:22 | 000,000,211 | ---- | M] () -- C:\Boot.bak
[2011/01/18 18:05:34 | 000,000,664 | ---- | M] () -- C:\WINDOWS\System32\d3d9caps.dat
[2011/01/18 18:02:51 | 000,000,791 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\Malwarebytes' Anti-Malware.lnk
[2011/01/18 09:34:52 | 001,349,208 | ---- | M] (Kaspersky Lab ZAO) -- C:\Documents and Settings\Computer\Desktop\TDSSKiller.exe
[2011/01/08 19:07:48 | 000,441,124 | ---- | M] () -- C:\WINDOWS\System32\perfh009.dat
[2011/01/08 19:07:47 | 000,071,060 | ---- | M] () -- C:\WINDOWS\System32\perfc009.dat
[2010/12/31 00:14:48 | 000,130,048 | ---- | M] () -- C:\Documents and Settings\Computer\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
========== Files Created - No Company Name ==========
[2011/01/19 17:20:22 | 000,000,211 | ---- | C] () -- C:\Boot.bak
[2011/01/19 17:20:21 | 000,260,272 | RHS- | C] () -- C:\cmldr
[2011/01/19 17:18:28 | 000,256,512 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2011/01/19 17:18:28 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2011/01/19 17:18:28 | 000,089,088 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2011/01/19 17:18:28 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2011/01/19 17:18:28 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2011/01/18 16:39:46 | 000,000,284 | ---- | C] () -- C:\WINDOWS\tasks\RealUpgradeLogonTaskS-1-5-21-527237240-1960408961-725345543-1003.job
[2011/01/18 16:39:03 | 000,000,791 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\Malwarebytes' Anti-Malware.lnk
[2010/12/30 23:58:11 | 000,000,664 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2010/09/03 11:22:54 | 000,025,600 | ---- | C] () -- C:\WINDOWS\System32\AVSredirect.dll
[2010/07/23 18:04:04 | 000,000,077 | ---- | C] () -- C:\WINDOWS\BBW_INFO.INI
[2010/05/25 22:50:23 | 000,014,976 | ---- | C] () -- C:\WINDOWS\System32\drivers\SBKUPNT.SYS
[2010/04/17 21:34:59 | 000,000,088 | RHS- | C] () -- C:\Documents and Settings\All Users\Application Data\7FA21157EA.sys
[2010/04/17 21:34:58 | 000,001,682 | -HS- | C] () -- C:\Documents and Settings\All Users\Application Data\KGyGaAvL.sys
[2010/03/14 22:54:24 | 000,354,816 | ---- | C] () -- C:\WINDOWS\System32\psisdecd.dll
[2009/11/04 11:58:41 | 000,217,088 | ---- | C] () -- C:\WINDOWS\System32\avformat-50.dll
[2009/11/04 11:58:41 | 000,018,432 | ---- | C] () -- C:\WINDOWS\System32\avutil-49.dll
[2009/11/04 11:58:40 | 001,984,512 | ---- | C] () -- C:\WINDOWS\System32\avcodec-51.dll
[2009/10/28 19:45:44 | 000,130,048 | ---- | C] () -- C:\Documents and Settings\Computer\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2009/10/28 14:11:48 | 000,168,448 | ---- | C] () -- C:\WINDOWS\System32\unrar.dll
[2009/10/28 14:11:45 | 003,596,288 | ---- | C] () -- C:\WINDOWS\System32\qt-dx331.dll
[2009/10/28 14:11:45 | 000,795,648 | ---- | C] () -- C:\WINDOWS\System32\xvidcore.dll
[2009/10/28 14:11:45 | 000,130,048 | ---- | C] () -- C:\WINDOWS\System32\xvidvfw.dll
[2009/10/28 14:11:43 | 000,057,344 | ---- | C] () -- C:\WINDOWS\System32\ff_vfw.dll
[2009/10/28 14:08:58 | 000,286,720 | R--- | C] () -- C:\WINDOWS\System32\nvnt4cpl.dll
[2009/10/28 13:12:01 | 000,040,840 | ---- | C] () -- C:\WINDOWS\System32\drivers\termdd.sys
[2009/10/28 08:05:20 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2009/07/08 10:58:18 | 001,724,416 | ---- | C] () -- C:\WINDOWS\System32\nvwdmcpl.dll
[2009/07/08 10:58:18 | 001,507,328 | ---- | C] () -- C:\WINDOWS\System32\nview.dll
[2009/07/08 10:58:18 | 001,101,824 | ---- | C] () -- C:\WINDOWS\System32\nvwimg.dll
[2009/07/08 10:58:18 | 000,466,944 | ---- | C] () -- C:\WINDOWS\System32\nvshell.dll
========== LOP Check ==========
[2009/11/02 19:37:47 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Acoustica
[2009/11/12 12:54:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Bell
[2010/02/22 20:53:46 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\PopCap Games
[2010/12/21 18:49:29 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\SweetIM
[2011/01/18 15:49:40 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\TEMP
[2009/12/10 00:19:26 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\WinZip
[2010/04/01 19:24:35 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\{429CAD59-35B1-4DBC-BB6D-1DB246563521}
[2009/11/23 14:55:09 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\{755AC846-7372-4AC8-8550-C52491DAA8BD}
[2009/11/02 19:50:15 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\Acoustica
[2009/11/12 12:54:59 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\Bell
[2010/09/03 10:47:03 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\HamsterSoft
[2010/10/13 14:19:02 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\MtStudio
[2009/11/09 13:23:41 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\Novation
[2010/09/03 10:43:37 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\OpenOffice.org
[2011/01/20 03:15:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Computer\Application Data\uTorrent
========== Purity Check ==========
========== Alternate Data Streams ==========
@Alternate Data Stream - 132 bytes -> C:\Documents and Settings\All Users\Application Data\TEMP:3AEA6AF9
< End of report >
I also ran MBAM again and it came up with no infections
EDIT: One thing I do notice right off the bat is that TermDD is still running in the services
Edited by Log2, 20 January 2011 - 02:22 AM.
#20

 Posted 20 January 2011 - 03:41 AM
Posted 20 January 2011 - 03:41 AM

One thing I do notice right off the bat is that TermDD is still running in the services
Termdd.sys is a legit MS system file.
One way to be sure.
Submit a File For Analysis
We need to have the files below Scanned by Uploading them/it to Jotti
Please visit Jotti
Copy/paste the the following file path into the window
C:\WINDOWS\system32\drivers\termdd.sys
Click Submit/Send File
Please post back, to let me know the results.
Next
GMER Rootkit Scanner
 GMER Rootkit Scanner - Download - Homepage
GMER Rootkit Scanner - Download - Homepage- Download GMER
- Extract the contents of the zipped file to desktop.
- Double click GMER.exe.

- If it gives you a warning about rootkit activity and asks if you want to run a full scan...click on NO, then use the following settings for a more complete scan..
- In the right panel, you will see several boxes that have been checked. Ensure the following are UNCHECKED ...
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
NOTE - Not all of the tick boxes will be available if you are running a 64bit Operating System. You may also get an error message display on the screen when using a 64bit Operating System, this is normal, just click on OK and let it carry on.
Click the image to enlarge it
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "ark.txt"
- Save the log where you can easily find it, such as your desktop.
**Caution**Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Please copy and paste the report into your Post.
#21

 Posted 20 January 2011 - 04:44 AM
Posted 20 January 2011 - 04:44 AM

http://virusscan.jotti.org/en/scanresult/7116626879ae0cc550b7071a62b6d29ff6d86642
And here is the GMER Log
GMER 1.0.15.15530 - http://www.gmer.net
Rootkit scan 2011-01-20 05:43:36
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP3T1L0-19 WDC_WD800AAJS-00PSA0 rev.05.06H05
Running: gmer.exe; Driver: C:\DOCUME~1\Computer\LOCALS~1\Temp\pxtdqpow.sys
---- Kernel code sections - GMER 1.0.15 ----
.text C:\WINDOWS\system32\DRIVERS\nv4_mini.sys section is writeable [0xB74A7360, 0x3CDCE5, 0xE8000020]
---- EOF - GMER 1.0.15 ----
Edited by Log2, 20 January 2011 - 04:45 AM.
#22

 Posted 20 January 2011 - 04:52 AM
Posted 20 January 2011 - 04:52 AM

Do you have the installation CD handy?
#23

 Posted 20 January 2011 - 04:53 AM
Posted 20 January 2011 - 04:53 AM

EDIT: Or can I copy it from a windows 7 machine to an XP Machine?
EDIT2: I found a copy of the file online, and ran the Jotti on it, and it doesn't have any viruses, then I searched the MD5 on google to see if it was a real MD5, and it looks legit, how do I go about replacing it? can it be done in safe mode? or do I need to do it a certain way?
Edited by Log2, 20 January 2011 - 05:09 AM.
#24

 Posted 20 January 2011 - 05:45 AM
Posted 20 January 2011 - 05:45 AM

#25

 Posted 20 January 2011 - 03:15 PM
Posted 20 January 2011 - 03:15 PM

I proceeded to run MBAM, here's the log from that:
Malwarebytes' Anti-Malware 1.50.1.1100
www.malwarebytes.org
Database version: 5557
Windows 5.1.2600 Service Pack 3
Internet Explorer 8.0.6001.18702
1/20/2011 8:15:31 AM
mbam-log-2011-01-20 (08-15-31).txt
Scan type: Full scan (C:\|)
Objects scanned: 191392
Time elapsed: 24 minute(s), 29 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Everything seems to be fixed up properly
#26

 Posted 20 January 2011 - 04:49 PM
Posted 20 January 2011 - 04:49 PM

Step One
1. Close any open browsers.
2. Close/disable all anti virus and anti malware programs so they do not interfere with the running of ComboFix.
3. Open notepad and copy/paste the text in the quotebox below into it:
Killall::
File::
FCopy::
C:\termdd.sys | C:\WINDOWS\system32\drivers\termdd.sys
C:\WINDOWS\$NtServicePackUninstall$\regedit.exe | C:\WINDOWS\regedit.exe
Folder::
Registry::
Driver::
Save this as CFScript.txt, in the same location as ComboFix.exe

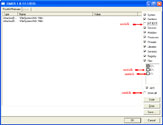
Refering to the picture above, drag CFScript into ComboFix.exe
When finished, it shall produce a log for you at C:\ComboFix.txt which I will require in your next reply.
Step Two
Download AVPTool from Here to your desktop
Run the programme you have just downloaded to your desktop (it will be randomly named )
First we will run a virus scan
On the first tab select all elements down to Computer and then select start scan
Once it has finished select report and post that.

Do not close AVPTool or it will self uninstall, if it does uninstall - then just rerun the setup file on your desktop
Now an analysis scan
Select the Manual Disinfection tab
Press the Gather System Information button
Once done Open the last report saved folder then attach the zip file to your next post zip
The file is located at C:\Users\your name\Desktop\Virus Removal Tool\setup_9.0.0.722_05.01.2011_20-34\LOG\avptool_sysinfo.zip

#27

 Posted 25 January 2011 - 12:43 PM
Posted 25 January 2011 - 12:43 PM

If you need this topic reopened, please contact a staff member. This applies only to the original topic starter. Everyone else please begin a New Topic.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

