Netbook won't load Windows - Bootloader doesn't work
Started by
cwalter
, May 03 2011 03:25 PM
#1

 Posted 03 May 2011 - 03:25 PM
Posted 03 May 2011 - 03:25 PM

#2

 Posted 06 June 2011 - 12:47 AM
Posted 06 June 2011 - 12:47 AM

Hello cwalter and welcome to G2G! 
My nick is maliprog and I'll will be your technical support on this issue. Before we start please read my notes carefully:
NOTE:
Step 1
Step 2
Please print these instruction out so that you know what you are doing
My nick is maliprog and I'll will be your technical support on this issue. Before we start please read my notes carefully:
NOTE:
- Malware removal is NOT instantaneous, most infections require several courses of action to completely eradicate.
- Absence of symptoms does not always mean the computer is clean
- Kindly follow my instructions in the order posted. Order is crucial in cleaning process.
- Please DO NOT run any scans or fix on your own without my direction.
- Please read all of my response through at least once before attempting to follow the procedures described.
- If there's anything you don't understand or isn't totally clear, please come back to me for clarification.
- Please do not attach any log files to your replies unless I specifically ask you. Instead please copy and paste so as to include the log in your reply.
- You must reply within 3 days or your topic will be closed
Step 1
- Does this notebook have Recovery partition?
- Do you have your Windows installation disk?
Step 2
Please print these instruction out so that you know what you are doing
- Download OTLPEStd.exe to your desktop
- Ensure that you have a blank CD in the drive
- Double click OTLPENet.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
Note : If you do not know how to set your computer to boot from CD follow the steps here - As the CD needs to detect your hardware and load the operating system, I would recommend a nice cup of tea whilst it loads

- Your system should now display a Reatogo desktop.
Note : as you are running from CD it is not exactly speedy - Double-click on the OTLPE icon.
- Select the Windows folder of the infected drive if it asks for a location
- When asked "Do you wish to load the remote registry", select Yes
- When asked "Do you wish to load remote user profile(s) for scanning", select Yes
- Ensure the box "Automatically Load All Remaining Users" is checked and press OK
- OTL should now start.
- Press Run Scan to start the scan.
- When finished, the file will be saved in drive C:\\OTL.txt
- Copy this file to your USB drive if you do not have internet connection on this system.
- Right click the file and select send to : select the USB drive.
- Confirm that it has copied to the USB drive by selecting it
- You can backup any files that you wish from this OS
- Please post the contents of the C:\\OTL.txt file in your reply.
#3

 Posted 07 June 2011 - 09:41 AM
Posted 07 June 2011 - 09:41 AM

Hi maliprog.
Thank you for helping me.
I do have a few questions/problems:
Step 1
1. Does this notebook have Recovery partition? - I don't know.
2. Do you have your Windows installation disk? - no. This is a netbook and there is no disk drive. The only thing I have are USB ports. In the past, I created a bootloader to bypass startup from the netbook itself and read from a flashdrive, but now it won't do that. It recognizes the flash drive and I can select it to load windows from it, but then I am left with a blank screen.
Which brings me to Step 2.
I can't even get the netbook working to load anything and since there is not a cd drive, I can not continue.
Is there another solution?
Thank you!
Thank you for helping me.
I do have a few questions/problems:
Step 1
1. Does this notebook have Recovery partition? - I don't know.
2. Do you have your Windows installation disk? - no. This is a netbook and there is no disk drive. The only thing I have are USB ports. In the past, I created a bootloader to bypass startup from the netbook itself and read from a flashdrive, but now it won't do that. It recognizes the flash drive and I can select it to load windows from it, but then I am left with a blank screen.
Which brings me to Step 2.
I can't even get the netbook working to load anything and since there is not a cd drive, I can not continue.
Is there another solution?
Thank you!
#4

 Posted 07 June 2011 - 02:20 PM
Posted 07 June 2011 - 02:20 PM

Hi cwalter,
There is also USB version we can use
IMPORTANT:
You will need a flash drive with a size of 512 Mb or bigger. Make sure that you do not leave anything important on the flash drive, as all data on it will be deleted during the following steps.
Try to boot it now and follow all step from my previous post and post OTL log here for me.
There is also USB version we can use
IMPORTANT:
You will need a flash drive with a size of 512 Mb or bigger. Make sure that you do not leave anything important on the flash drive, as all data on it will be deleted during the following steps.
- Download OTLPEStd.exe from the following link and save it to your Desktop: mirror1.
- Download eeepcfr.zip from the following link and save it to your Desktop: the mirror
- Finally, if you do not have a file archiver like 7-zip or Winrar installed, please download 7-zip from the following link and install it: the mirror
- Download OTLPEStd.exe from the following link and save it to your Desktop: mirror1.
- Once you have 7-zip install, decompress OTLPEStd.exe by rightclicking on the folder and choosing the options shown in the picture below. Please use a dedicated folder, for example OTLPE, on your Desktop
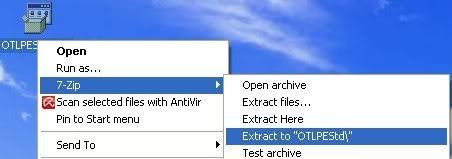
- Open the folder OTLPEStd which will be created in the same location as OTLPEStd.exe and right-click OTLPE_New_Std.iso. Select 7-Zip and from the submenu select Extract files... and extract the content onto your Desktop in a OTLPE folder:
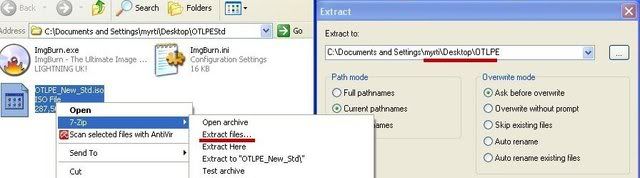
- Please also decompress eeepcfr to your systemroot (usually C:\).
- Empty the flash drive you want to install OTLPE on.
- Go to C:\eeecpfr and double-click usb_prep8.cmd to launch it.
- Press any key when asked to in the black window that opens.
- As indicated in the image, make sure you have selected the correct flash drive, before proceeding.
For Drive Label: type in OTLPE.
Under Source Path to built BartPE/WinPE Files click ... and select the folder OTLPE that you created on your Desktop.
Finally check Enable File Copy.
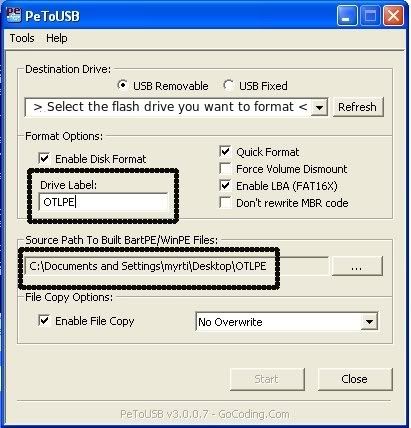
- Click on Start, accept the disclaimers and wait for the program to finish.
Try to boot it now and follow all step from my previous post and post OTL log here for me.
#5

 Posted 11 June 2011 - 02:31 PM
Posted 11 June 2011 - 02:31 PM

Maliprog,
I'm just posting to say I will performing the steps as you described and I will be posting the results this afternoon. Thank you for your help!
I'm just posting to say I will performing the steps as you described and I will be posting the results this afternoon. Thank you for your help!
#6

 Posted 12 June 2011 - 08:07 AM
Posted 12 June 2011 - 08:07 AM

OTL logfile created on: 6/12/2011 6:22:36 AM - Run
OTLPE by OldTimer - Version 3.1.46.0 Folder = X:\Programs\OTLPE
Microsoft Windows XP Service Pack 3 (Version = 5.1.2600) - Type = SYSTEM
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
1,014.00 Mb Total Physical Memory | 835.00 Mb Available Physical Memory | 82.00% Memory free
902.00 Mb Paging File | 839.00 Mb Available in Paging File | 93.00% Paging File free
Paging file location(s): C:\pagefile.sys 1524 3048 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 139.66 Gb Total Space | 128.36 Gb Free Space | 91.91% Space Free | Partition Type: NTFS
Drive X: | 1.86 Gb Total Space | 1.52 Gb Free Space | 81.68% Space Free | Partition Type: FAT
Computer Name: REATOGO | User Name: SYSTEM
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
Using ControlSet: ControlSet001
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled] -- -- (HidServ)
SRV - File not found [On_Demand] -- -- (AppMgmt)
SRV - [2009/08/22 03:25:16 | 000,117,640 | R--- | M] (Symantec Corporation) [Auto] -- C:\Program Files\Norton Internet Security\Engine\16.8.0.41\ccSvcHst.exe -- (Norton Internet Security)
SRV - [2009/06/10 09:13:54 | 000,499,796 | ---- | M] (Atheros) [Auto] -- C:\WINDOWS\system32\acs.exe -- (ACS)
SRV - [2009/05/22 14:02:20 | 000,250,616 | ---- | M] (WildTangent, Inc.) [On_Demand] -- C:\Program Files\TOSHIBA Games\TOSHIBA Game Console\GameConsoleService.exe -- (GameConsoleService)
SRV - [2008/08/22 13:26:38 | 000,523,320 | ---- | M] (TOSHIBA Corporation) [Auto] -- C:\WINDOWS\system32\ThpSrv.exe -- (Thpsrv)
SRV - [2008/05/21 17:07:00 | 000,111,984 | ---- | M] () [Auto] -- C:\TOSHIBA\IVP\swupdate\swupdtmr.exe -- (Swupdtmr)
SRV - [2007/11/21 20:23:32 | 000,129,632 | ---- | M] (TOSHIBA Corporation) [Auto] -- C:\WINDOWS\system32\TODDSrv.exe -- (TODDSrv)
SRV - [2007/01/25 21:47:50 | 000,136,816 | ---- | M] () [Auto] -- C:\TOSHIBA\IVP\ISM\pinger.exe -- (pinger)
SRV - [2005/01/17 19:38:00 | 000,040,960 | ---- | M] (TOSHIBA CORPORATION) [Auto] -- C:\Program Files\TOSHIBA\ConfigFree\CFSvcs.exe -- (CFSvcs)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand] -- -- (USBCCID)
DRV - File not found [Kernel | On_Demand] -- -- (SYMNDIS)
DRV - File not found [Kernel | On_Demand] -- -- (SYMIDS)
DRV - File not found [Kernel | On_Demand] -- -- (SYMFW)
DRV - File not found [Kernel | On_Demand] -- -- (RtsUIR)
DRV - File not found [Kernel | On_Demand] -- -- (RSUSBSTOR)
DRV - File not found [Kernel | On_Demand] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDCOMP)
DRV - File not found [Kernel | System] -- -- (PCIDump)
DRV - File not found [Kernel | System] -- -- (lbrtfdc)
DRV - File not found [Kernel | System] -- -- (i2omgmt)
DRV - File not found [Kernel | System] -- -- (Changer)
DRV - File not found [Kernel | On_Demand] -- -- (catchme)
DRV - [2011/01/07 22:56:04 | 000,763,904 | ---- | M] (Windows ® Codename Longhorn DDK provider) [Kernel | Boot] -- C:\WINDOWS\System32\drivers\atlebtzc.sys -- (atlebtzc)
DRV - [2010/02/04 21:52:05 | 000,482,432 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\ccHPx86.sys -- (ccHP)
DRV - [2009/12/28 07:02:32 | 001,323,568 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\VirusDefs\20100122.048\NAVEX15.SYS -- (NAVEX15)
DRV - [2009/12/28 07:02:32 | 000,371,248 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\Program Files\Common Files\Symantec Shared\EENGINE\eeCtrl.sys -- (eeCtrl)
DRV - [2009/12/28 07:02:32 | 000,102,448 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Program Files\Common Files\Symantec Shared\EENGINE\EraserUtilRebootDrv.sys -- (EraserUtilRebootDrv)
DRV - [2009/12/28 07:02:32 | 000,084,912 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\VirusDefs\20100122.048\NAVENG.SYS -- (NAVENG)
DRV - [2009/12/26 09:39:39 | 000,124,976 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SYMEVENT.SYS -- (SymEvent)
DRV - [2009/10/28 18:37:22 | 000,329,592 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\IPSDefs\20100119.001\IDSXpx86.sys -- (IDSxpx86)
DRV - [2009/10/27 23:08:05 | 000,036,400 | R--- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SymIM.sys -- (SymIMMP)
DRV - [2009/10/27 23:08:05 | 000,036,400 | R--- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SymIM.sys -- (SymIM)
DRV - [2009/08/22 03:25:17 | 000,310,320 | ---- | M] (Symantec Corporation) [File_System | Boot] -- C:\WINDOWS\system32\drivers\NIS\1008000.029\SymEFA.sys -- (SymEFA)
DRV - [2009/08/22 03:25:17 | 000,308,272 | ---- | M] (Symantec Corporation) [File_System | On_Demand] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\SRTSP.SYS -- (SRTSP)
DRV - [2009/08/22 03:25:17 | 000,259,632 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\BHDrvx86.sys -- (BHDrvx86)
DRV - [2009/08/22 03:25:17 | 000,217,136 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\SYMTDI.SYS -- (SYMTDI)
DRV - [2009/08/22 03:25:17 | 000,043,696 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\system32\drivers\NIS\1008000.029\SRTSPX.SYS -- (SRTSPX) Symantec Real Time Storage Protection (PEL)
DRV - [2009/07/29 00:06:24 | 005,870,080 | ---- | M] (Realtek Semiconductor Corp.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\RtkHDAud.sys -- (IntcAzAudAddService) Service for Realtek HD Audio (WDM)
DRV - [2009/06/22 15:59:26 | 001,574,112 | ---- | M] (Atheros Communications, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\athw.sys -- (AR5416)
DRV - [2009/04/10 20:09:44 | 000,017,960 | ---- | M] (Chicony Electronics Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\UVCFTR_S.SYS -- (UVCFTR)
DRV - [2009/04/10 20:09:42 | 000,048,176 | ---- | M] (Chicony Electronics Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\cec_uvc.sys -- (cecnuvc)
DRV - [2009/03/17 02:19:44 | 000,058,208 | ---- | M] (Atheros Communications, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\wsimd.sys -- (WSIMD)
DRV - [2009/03/12 18:09:54 | 000,023,512 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\TVALZ_O.SYS -- (TVALZ)
DRV - [2009/01/22 20:25:26 | 000,120,064 | ---- | M] (Realtek Semiconductor Corporation ) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Rtenicxp.sys -- (RTLE8023xp)
DRV - [2008/08/21 13:35:24 | 000,028,536 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\thpdrv.sys -- (Thpdrv)
DRV - [2008/08/05 23:10:12 | 001,684,736 | ---- | M] (Creative) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Ambfilt.sys -- (Ambfilt)
DRV - [2008/07/24 17:40:58 | 000,017,192 | ---- | M] (TOSHIBA ) [Kernel | System] -- C:\WINDOWS\system32\drivers\TPwSav.sys -- (TPwSav)
DRV - [2008/02/07 03:23:46 | 000,166,448 | ---- | M] (Alps Electric Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Apfiltr.sys -- (ApfiltrService)
DRV - [2007/09/04 13:14:06 | 000,006,528 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\Thpevm.sys -- (Thpevm)
DRV - [2007/03/26 15:22:18 | 000,105,856 | ---- | M] (TOSHIBA Corporation) [File_System | Auto] -- C:\WINDOWS\system32\drivers\tdudf.sys -- (tdudf)
DRV - [2007/02/22 18:10:30 | 000,016,128 | ---- | M] (TOSHIBA Corporation.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\tdcmdpst.sys -- (tdcmdpst)
DRV - [2007/02/19 15:15:32 | 000,134,016 | ---- | M] (TOSHIBA Corporation) [File_System | Auto] -- C:\WINDOWS\system32\drivers\trudf.sys -- (trudf)
DRV - [2006/01/04 18:41:48 | 001,389,056 | ---- | M] (Creative Technology Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Monfilt.sys -- (Monfilt)
DRV - [2003/01/29 17:35:00 | 000,012,032 | ---- | M] (TOSHIBA Corporation.) [Kernel | Auto] -- C:\WINDOWS\system32\drivers\Netdevio.sys -- (Netdevio)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.google.co...=TSNB&bmod=TSNB
IE - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.google.co...=TSNB&bmod=TSNB
IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.google.co...=TSNB&bmod=TSNB
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,SearchDefaultBranded = 1
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.yahoo.com/
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Start Page Restore = http://www.yahoo.com/
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 1
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyOverride" = <local>
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyServer" = http=127.0.0.1:8074
IE - HKU\LocalService_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
FF - HKLM\software\mozilla\Firefox\extensions\\{7BA52691-1876-45ce-9EE6-54BCB3B04BBC}: C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\coFFPlgn\ [2010/04/26 17:27:03 | 000,000,000 | ---D | M]
FF - HKLM\software\mozilla\Firefox\extensions\\{29D3A363-23BD-41A6-9EB2-3D563ED266DA}: C:\Documents and Settings\Cori Walter\Local Settings\Application Data\{29D3A363-23BD-41A6-9EB2-3D563ED266DA}
FF - HKLM\software\mozilla\Firefox\extensions\\{6ADCDFE6-44E7-4A0C-A4CB-7DD7C43BE630}: C:\Documents and Settings\Cori Walter\Local Settings\Application Data\{6ADCDFE6-44E7-4A0C-A4CB-7DD7C43BE630} [2010/12/13 21:20:15 | 000,000,000 | ---D | M]
O1 HOSTS File: ([2010/12/13 21:14:27 | 000,000,098 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\Hosts
O1 - Hosts: 127.0.0.1 localhost
O1 - Hosts: ::1 localhost
O2 - BHO: (Symantec NCO BHO) - {602ADB0E-4AFF-4217-8AA1-95DAC4DFA408} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O2 - BHO: (Symantec Intrusion Prevention) - {6D53EC84-6AAE-4787-AEEE-F4628F01010C} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\IPSBHO.dll (Symantec Corporation)
O3 - HKLM\..\Toolbar: (Norton Toolbar) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O3 - HKU\Cori_Walter_ON_C\..\Toolbar\WebBrowser: (Norton Toolbar) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O4 - HKLM..\Run: [ACU] C:\Program Files\Atheros\ACU.exe (Atheros Communications, Inc.)
O4 - HKLM..\Run: [Camera Assistant Software] C:\Program Files\Camera Assistant Software for Toshiba\traybar.exe (Chicony)
O4 - HKLM..\Run: [CeEKEY] C:\Program Files\TOSHIBA\E-KEY\CeEKey.exe (COMPAL ELECTRONIC INC.)
O4 - HKLM..\Run: [DDWMon] C:\Program Files\TOSHIBA\TOSHIBA Direct Disc Writer\\ddwmon.exe ()
O4 - HKLM..\Run: [HWSetup] C:\Program Files\TOSHIBA\TOSHIBA Applet\HWSetup.exe (TOSHIBA CO.,LTD.)
O4 - HKLM..\Run: [Ltucaveca] C:\WINDOWS\oyubeyeyo.dll (CyberLink Corp.)
O4 - HKLM..\Run: [NortonOnlineBackupReminder] C:\Program Files\TOSHIBA\Toshiba Online Backup\Activation\TobuActivation.exe (Toshiba)
O4 - HKLM..\Run: [Pinger] C:\toshiba\ivp\ism\pinger.exe ()
O4 - HKLM..\Run: [SmoothView] C:\Program Files\TOSHIBA\TOSHIBA Zooming Utility\SmoothView.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TAccessibility] C:\Program Files\TOSHIBA\Accessibility\TAccessibility.exe ()
O4 - HKLM..\Run: [TDispVol] C:\WINDOWS\System32\TDispVol.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [ThpSrv] C:\WINDOWS\System32\thpsrv.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TPNF] C:\Program Files\TOSHIBA\TouchPad\TPTray.exe (COMPAL ELECTRONIC INC.)
O4 - HKLM..\Run: [TPSMain] C:\WINDOWS\System32\TPSMain.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TUSBSleepChargeSrv] C:\Program Files\TOSHIBA\TOSHIBA USB Sleep and Charge Utility\TUSBSleepChargeSrv.exe (TOSHIBA)
O4 - HKLM..\Run: [ZoomingHook] C:\WINDOWS\System32\ZoomingHook.exe (TOSHIBA)
O4 - HKU\Cori_Walter_ON_C..\Run: [dgnikqbr] C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe ()
O4 - HKU\Cori_Walter_ON_C..\Run: [ndkwrsdg] C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe ()
O4 - HKLM..\RunOnce: [*packbootmsg.exe] C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe (It Systems)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\Cori_Walter_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\Cori_Walter_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\LocalService_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\NetworkService_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O16 - DPF: {CAFEEFAC-0016-0000-0011-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.2.1
O18 - Protocol\Handler\symres {AA1061FE-6C41-421f-9344-69640C9732AB} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O24 - Desktop WallPaper: C:\WINDOWS\Web\Wallpaper\Bliss.bmp
O24 - Desktop BackupWallPaper: C:\WINDOWS\Web\Wallpaper\Bliss.bmp
O32 - Unable to read "AutoRun" value or value not present!
O32 - AutoRun File - [2009/09/08 09:23:30 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O32 - AutoRun File - [2006/03/24 06:06:42 | 000,000,053 | ---- | M] () - X:\AUTORUN.INF -- [ FAT ]
O34 - HKLM BootExecute: (autocheck autochk *) - File not found
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = comfile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2010/12/13 21:14:26 | 000,148,992 | ---- | C] (It Systems) -- C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe
========== Files - Modified Within 30 Days ==========
========== Files Created - No Company Name ==========
[2011/01/04 19:40:42 | 000,256,512 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2011/01/04 19:40:42 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2011/01/04 19:40:42 | 000,089,088 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2011/01/04 19:40:42 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2011/01/04 19:40:42 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2011/01/04 19:24:11 | 000,000,120 | ---- | C] () -- C:\WINDOWS\Rgubo.dat
[2011/01/04 19:24:11 | 000,000,000 | ---- | C] () -- C:\WINDOWS\Tlacigejimi.bin
[2010/08/01 13:44:32 | 000,003,584 | ---- | C] () -- C:\Documents and Settings\Cori Walter\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/03/17 20:37:00 | 000,000,754 | ---- | C] () -- C:\WINDOWS\WORDPAD.INI
[2010/01/09 17:01:06 | 000,000,000 | ---- | C] () -- C:\WINDOWS\TPTray.INI
[2009/12/25 11:54:05 | 000,003,242 | ---- | C] () -- C:\Documents and Settings\Cori Walter\Application Data\wklnhst.dat
[2009/12/25 10:41:00 | 000,000,013 | RHS- | C] () -- C:\WINDOWS\System32\drivers\fbd.sys
[2009/10/27 23:12:05 | 000,000,061 | ---- | C] () -- C:\WINDOWS\smscfg.ini
[2009/10/27 22:59:26 | 000,262,216 | ---- | C] () -- C:\WINDOWS\System32\IPTests.dll
[2009/09/08 10:03:35 | 000,000,000 | ---- | C] () -- C:\WINDOWS\NDSTray.INI
[2009/09/08 10:02:50 | 000,000,353 | ---- | C] () -- C:\WINDOWS\System32\OEMINFO.INI
[2009/09/08 09:58:10 | 000,004,569 | ---- | C] () -- C:\WINDOWS\System32\secupd.dat
[2009/09/08 09:58:00 | 000,434,266 | ---- | C] () -- C:\WINDOWS\System32\perfh009.dat
[2009/09/08 09:58:00 | 000,272,128 | ---- | C] () -- C:\WINDOWS\System32\perfi009.dat
[2009/09/08 09:58:00 | 000,068,386 | ---- | C] () -- C:\WINDOWS\System32\perfc009.dat
[2009/09/08 09:58:00 | 000,028,626 | ---- | C] () -- C:\WINDOWS\System32\perfd009.dat
[2009/09/08 09:57:57 | 000,004,631 | ---- | C] () -- C:\WINDOWS\System32\oembios.dat
[2009/09/08 09:57:55 | 013,107,200 | ---- | C] () -- C:\WINDOWS\System32\oembios.bin
[2009/09/08 09:57:51 | 000,040,960 | ---- | C] () -- C:\WINDOWS\System32\EBLib.DLL
[2009/09/08 09:57:51 | 000,000,741 | ---- | C] () -- C:\WINDOWS\System32\noise.dat
[2009/09/08 09:57:41 | 000,045,056 | ---- | C] () -- C:\WINDOWS\System32\TDispVol.dll
[2009/09/08 09:57:37 | 000,673,088 | ---- | C] () -- C:\WINDOWS\System32\mlang.dat
[2009/09/08 09:57:36 | 000,046,258 | ---- | C] () -- C:\WINDOWS\System32\mib.bin
[2009/09/08 09:57:08 | 000,218,003 | ---- | C] () -- C:\WINDOWS\System32\dssec.dat
[2009/09/08 09:56:57 | 000,001,804 | ---- | C] () -- C:\WINDOWS\System32\Dcache.bin
[2009/09/08 09:52:23 | 000,147,456 | ---- | C] () -- C:\WINDOWS\System32\igfxCoIn_v4926.dll
[2009/09/08 09:25:35 | 000,002,048 | --S- | C] () -- C:\WINDOWS\bootstat.dat
[2009/09/08 09:21:34 | 000,021,640 | ---- | C] () -- C:\WINDOWS\System32\emptyregdb.dat
[2009/09/08 09:20:45 | 000,001,793 | ---- | C] () -- C:\WINDOWS\System32\fxsperf.ini
[2009/09/08 02:18:25 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2009/09/08 02:17:40 | 000,167,504 | ---- | C] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2009/06/06 04:42:40 | 000,028,672 | ---- | C] () -- C:\WINDOWS\System32\TPeculiarity.dll
[2009/04/02 12:35:18 | 000,024,576 | ---- | C] () -- C:\WINDOWS\System32\EKECioCtl.dll
[2009/03/31 14:13:20 | 000,045,056 | ---- | C] () -- C:\WINDOWS\System32\HWS_Ctrl.dll
[2005/03/26 00:00:00 | 000,101,376 | ---- | C] () -- C:\WINDOWS\System32\FORMATUFD.EXE
========== LOP Check ==========
[2009/09/08 10:00:59 | 000,000,000 | ---D | M] -- C:\WINDOWS\system32\config\systemprofile\Application Data\toshiba
[2009/09/08 09:28:04 | 000,000,000 | ---D | M] -- C:\WINDOWS\system32\config\systemprofile\Application Data\WinBatch
[2009/12/25 11:54:05 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\Template
[2009/09/08 10:00:59 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\toshiba
[2009/09/08 09:28:04 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\WinBatch
[2010/01/18 08:16:39 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Partner
[2009/09/08 10:02:33 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Toshiba
[2009/09/08 09:57:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Vista32
[2009/09/08 09:57:51 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Vista64
[2009/09/08 10:19:11 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\WildTangent
========== Purity Check ==========
< End of report >
OTLPE by OldTimer - Version 3.1.46.0 Folder = X:\Programs\OTLPE
Microsoft Windows XP Service Pack 3 (Version = 5.1.2600) - Type = SYSTEM
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
1,014.00 Mb Total Physical Memory | 835.00 Mb Available Physical Memory | 82.00% Memory free
902.00 Mb Paging File | 839.00 Mb Available in Paging File | 93.00% Paging File free
Paging file location(s): C:\pagefile.sys 1524 3048 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 139.66 Gb Total Space | 128.36 Gb Free Space | 91.91% Space Free | Partition Type: NTFS
Drive X: | 1.86 Gb Total Space | 1.52 Gb Free Space | 81.68% Space Free | Partition Type: FAT
Computer Name: REATOGO | User Name: SYSTEM
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
Using ControlSet: ControlSet001
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled] -- -- (HidServ)
SRV - File not found [On_Demand] -- -- (AppMgmt)
SRV - [2009/08/22 03:25:16 | 000,117,640 | R--- | M] (Symantec Corporation) [Auto] -- C:\Program Files\Norton Internet Security\Engine\16.8.0.41\ccSvcHst.exe -- (Norton Internet Security)
SRV - [2009/06/10 09:13:54 | 000,499,796 | ---- | M] (Atheros) [Auto] -- C:\WINDOWS\system32\acs.exe -- (ACS)
SRV - [2009/05/22 14:02:20 | 000,250,616 | ---- | M] (WildTangent, Inc.) [On_Demand] -- C:\Program Files\TOSHIBA Games\TOSHIBA Game Console\GameConsoleService.exe -- (GameConsoleService)
SRV - [2008/08/22 13:26:38 | 000,523,320 | ---- | M] (TOSHIBA Corporation) [Auto] -- C:\WINDOWS\system32\ThpSrv.exe -- (Thpsrv)
SRV - [2008/05/21 17:07:00 | 000,111,984 | ---- | M] () [Auto] -- C:\TOSHIBA\IVP\swupdate\swupdtmr.exe -- (Swupdtmr)
SRV - [2007/11/21 20:23:32 | 000,129,632 | ---- | M] (TOSHIBA Corporation) [Auto] -- C:\WINDOWS\system32\TODDSrv.exe -- (TODDSrv)
SRV - [2007/01/25 21:47:50 | 000,136,816 | ---- | M] () [Auto] -- C:\TOSHIBA\IVP\ISM\pinger.exe -- (pinger)
SRV - [2005/01/17 19:38:00 | 000,040,960 | ---- | M] (TOSHIBA CORPORATION) [Auto] -- C:\Program Files\TOSHIBA\ConfigFree\CFSvcs.exe -- (CFSvcs)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand] -- -- (USBCCID)
DRV - File not found [Kernel | On_Demand] -- -- (SYMNDIS)
DRV - File not found [Kernel | On_Demand] -- -- (SYMIDS)
DRV - File not found [Kernel | On_Demand] -- -- (SYMFW)
DRV - File not found [Kernel | On_Demand] -- -- (RtsUIR)
DRV - File not found [Kernel | On_Demand] -- -- (RSUSBSTOR)
DRV - File not found [Kernel | On_Demand] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand] -- -- (PDCOMP)
DRV - File not found [Kernel | System] -- -- (PCIDump)
DRV - File not found [Kernel | System] -- -- (lbrtfdc)
DRV - File not found [Kernel | System] -- -- (i2omgmt)
DRV - File not found [Kernel | System] -- -- (Changer)
DRV - File not found [Kernel | On_Demand] -- -- (catchme)
DRV - [2011/01/07 22:56:04 | 000,763,904 | ---- | M] (Windows ® Codename Longhorn DDK provider) [Kernel | Boot] -- C:\WINDOWS\System32\drivers\atlebtzc.sys -- (atlebtzc)
DRV - [2010/02/04 21:52:05 | 000,482,432 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\ccHPx86.sys -- (ccHP)
DRV - [2009/12/28 07:02:32 | 001,323,568 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\VirusDefs\20100122.048\NAVEX15.SYS -- (NAVEX15)
DRV - [2009/12/28 07:02:32 | 000,371,248 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\Program Files\Common Files\Symantec Shared\EENGINE\eeCtrl.sys -- (eeCtrl)
DRV - [2009/12/28 07:02:32 | 000,102,448 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Program Files\Common Files\Symantec Shared\EENGINE\EraserUtilRebootDrv.sys -- (EraserUtilRebootDrv)
DRV - [2009/12/28 07:02:32 | 000,084,912 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\VirusDefs\20100122.048\NAVENG.SYS -- (NAVENG)
DRV - [2009/12/26 09:39:39 | 000,124,976 | ---- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SYMEVENT.SYS -- (SymEvent)
DRV - [2009/10/28 18:37:22 | 000,329,592 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\Definitions\IPSDefs\20100119.001\IDSXpx86.sys -- (IDSxpx86)
DRV - [2009/10/27 23:08:05 | 000,036,400 | R--- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SymIM.sys -- (SymIMMP)
DRV - [2009/10/27 23:08:05 | 000,036,400 | R--- | M] (Symantec Corporation) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\SymIM.sys -- (SymIM)
DRV - [2009/08/22 03:25:17 | 000,310,320 | ---- | M] (Symantec Corporation) [File_System | Boot] -- C:\WINDOWS\system32\drivers\NIS\1008000.029\SymEFA.sys -- (SymEFA)
DRV - [2009/08/22 03:25:17 | 000,308,272 | ---- | M] (Symantec Corporation) [File_System | On_Demand] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\SRTSP.SYS -- (SRTSP)
DRV - [2009/08/22 03:25:17 | 000,259,632 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\BHDrvx86.sys -- (BHDrvx86)
DRV - [2009/08/22 03:25:17 | 000,217,136 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\System32\Drivers\NIS\1008000.029\SYMTDI.SYS -- (SYMTDI)
DRV - [2009/08/22 03:25:17 | 000,043,696 | ---- | M] (Symantec Corporation) [Kernel | System] -- C:\WINDOWS\system32\drivers\NIS\1008000.029\SRTSPX.SYS -- (SRTSPX) Symantec Real Time Storage Protection (PEL)
DRV - [2009/07/29 00:06:24 | 005,870,080 | ---- | M] (Realtek Semiconductor Corp.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\RtkHDAud.sys -- (IntcAzAudAddService) Service for Realtek HD Audio (WDM)
DRV - [2009/06/22 15:59:26 | 001,574,112 | ---- | M] (Atheros Communications, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\athw.sys -- (AR5416)
DRV - [2009/04/10 20:09:44 | 000,017,960 | ---- | M] (Chicony Electronics Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\UVCFTR_S.SYS -- (UVCFTR)
DRV - [2009/04/10 20:09:42 | 000,048,176 | ---- | M] (Chicony Electronics Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\cec_uvc.sys -- (cecnuvc)
DRV - [2009/03/17 02:19:44 | 000,058,208 | ---- | M] (Atheros Communications, Inc.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\wsimd.sys -- (WSIMD)
DRV - [2009/03/12 18:09:54 | 000,023,512 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\TVALZ_O.SYS -- (TVALZ)
DRV - [2009/01/22 20:25:26 | 000,120,064 | ---- | M] (Realtek Semiconductor Corporation ) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Rtenicxp.sys -- (RTLE8023xp)
DRV - [2008/08/21 13:35:24 | 000,028,536 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\thpdrv.sys -- (Thpdrv)
DRV - [2008/08/05 23:10:12 | 001,684,736 | ---- | M] (Creative) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Ambfilt.sys -- (Ambfilt)
DRV - [2008/07/24 17:40:58 | 000,017,192 | ---- | M] (TOSHIBA ) [Kernel | System] -- C:\WINDOWS\system32\drivers\TPwSav.sys -- (TPwSav)
DRV - [2008/02/07 03:23:46 | 000,166,448 | ---- | M] (Alps Electric Co., Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Apfiltr.sys -- (ApfiltrService)
DRV - [2007/09/04 13:14:06 | 000,006,528 | ---- | M] (TOSHIBA Corporation) [Kernel | Boot] -- C:\WINDOWS\system32\drivers\Thpevm.sys -- (Thpevm)
DRV - [2007/03/26 15:22:18 | 000,105,856 | ---- | M] (TOSHIBA Corporation) [File_System | Auto] -- C:\WINDOWS\system32\drivers\tdudf.sys -- (tdudf)
DRV - [2007/02/22 18:10:30 | 000,016,128 | ---- | M] (TOSHIBA Corporation.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\tdcmdpst.sys -- (tdcmdpst)
DRV - [2007/02/19 15:15:32 | 000,134,016 | ---- | M] (TOSHIBA Corporation) [File_System | Auto] -- C:\WINDOWS\system32\drivers\trudf.sys -- (trudf)
DRV - [2006/01/04 18:41:48 | 001,389,056 | ---- | M] (Creative Technology Ltd.) [Kernel | On_Demand] -- C:\WINDOWS\system32\drivers\Monfilt.sys -- (Monfilt)
DRV - [2003/01/29 17:35:00 | 000,012,032 | ---- | M] (TOSHIBA Corporation.) [Kernel | Auto] -- C:\WINDOWS\system32\drivers\Netdevio.sys -- (Netdevio)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.google.co...=TSNB&bmod=TSNB
IE - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.google.co...=TSNB&bmod=TSNB
IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.google.co...=TSNB&bmod=TSNB
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,SearchDefaultBranded = 1
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.yahoo.com/
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Internet Explorer\Main,Start Page Restore = http://www.yahoo.com/
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 1
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyOverride" = <local>
IE - HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyServer" = http=127.0.0.1:8074
IE - HKU\LocalService_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
FF - HKLM\software\mozilla\Firefox\extensions\\{7BA52691-1876-45ce-9EE6-54BCB3B04BBC}: C:\Documents and Settings\All Users\Application Data\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\Norton\coFFPlgn\ [2010/04/26 17:27:03 | 000,000,000 | ---D | M]
FF - HKLM\software\mozilla\Firefox\extensions\\{29D3A363-23BD-41A6-9EB2-3D563ED266DA}: C:\Documents and Settings\Cori Walter\Local Settings\Application Data\{29D3A363-23BD-41A6-9EB2-3D563ED266DA}
FF - HKLM\software\mozilla\Firefox\extensions\\{6ADCDFE6-44E7-4A0C-A4CB-7DD7C43BE630}: C:\Documents and Settings\Cori Walter\Local Settings\Application Data\{6ADCDFE6-44E7-4A0C-A4CB-7DD7C43BE630} [2010/12/13 21:20:15 | 000,000,000 | ---D | M]
O1 HOSTS File: ([2010/12/13 21:14:27 | 000,000,098 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\Hosts
O1 - Hosts: 127.0.0.1 localhost
O1 - Hosts: ::1 localhost
O2 - BHO: (Symantec NCO BHO) - {602ADB0E-4AFF-4217-8AA1-95DAC4DFA408} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O2 - BHO: (Symantec Intrusion Prevention) - {6D53EC84-6AAE-4787-AEEE-F4628F01010C} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\IPSBHO.dll (Symantec Corporation)
O3 - HKLM\..\Toolbar: (Norton Toolbar) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O3 - HKU\Cori_Walter_ON_C\..\Toolbar\WebBrowser: (Norton Toolbar) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O4 - HKLM..\Run: [ACU] C:\Program Files\Atheros\ACU.exe (Atheros Communications, Inc.)
O4 - HKLM..\Run: [Camera Assistant Software] C:\Program Files\Camera Assistant Software for Toshiba\traybar.exe (Chicony)
O4 - HKLM..\Run: [CeEKEY] C:\Program Files\TOSHIBA\E-KEY\CeEKey.exe (COMPAL ELECTRONIC INC.)
O4 - HKLM..\Run: [DDWMon] C:\Program Files\TOSHIBA\TOSHIBA Direct Disc Writer\\ddwmon.exe ()
O4 - HKLM..\Run: [HWSetup] C:\Program Files\TOSHIBA\TOSHIBA Applet\HWSetup.exe (TOSHIBA CO.,LTD.)
O4 - HKLM..\Run: [Ltucaveca] C:\WINDOWS\oyubeyeyo.dll (CyberLink Corp.)
O4 - HKLM..\Run: [NortonOnlineBackupReminder] C:\Program Files\TOSHIBA\Toshiba Online Backup\Activation\TobuActivation.exe (Toshiba)
O4 - HKLM..\Run: [Pinger] C:\toshiba\ivp\ism\pinger.exe ()
O4 - HKLM..\Run: [SmoothView] C:\Program Files\TOSHIBA\TOSHIBA Zooming Utility\SmoothView.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TAccessibility] C:\Program Files\TOSHIBA\Accessibility\TAccessibility.exe ()
O4 - HKLM..\Run: [TDispVol] C:\WINDOWS\System32\TDispVol.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [ThpSrv] C:\WINDOWS\System32\thpsrv.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TPNF] C:\Program Files\TOSHIBA\TouchPad\TPTray.exe (COMPAL ELECTRONIC INC.)
O4 - HKLM..\Run: [TPSMain] C:\WINDOWS\System32\TPSMain.exe (TOSHIBA Corporation)
O4 - HKLM..\Run: [TUSBSleepChargeSrv] C:\Program Files\TOSHIBA\TOSHIBA USB Sleep and Charge Utility\TUSBSleepChargeSrv.exe (TOSHIBA)
O4 - HKLM..\Run: [ZoomingHook] C:\WINDOWS\System32\ZoomingHook.exe (TOSHIBA)
O4 - HKU\Cori_Walter_ON_C..\Run: [dgnikqbr] C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe ()
O4 - HKU\Cori_Walter_ON_C..\Run: [ndkwrsdg] C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe ()
O4 - HKLM..\RunOnce: [*packbootmsg.exe] C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe (It Systems)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\Cori_Walter_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\Cori_Walter_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\LocalService_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\NetworkService_ON_C\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O16 - DPF: {CAFEEFAC-0016-0000-0011-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_11)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.2.1
O18 - Protocol\Handler\symres {AA1061FE-6C41-421f-9344-69640C9732AB} - C:\Program Files\Norton Internet Security\Engine\16.8.0.41\CoIEPlg.dll (Symantec Corporation)
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O24 - Desktop WallPaper: C:\WINDOWS\Web\Wallpaper\Bliss.bmp
O24 - Desktop BackupWallPaper: C:\WINDOWS\Web\Wallpaper\Bliss.bmp
O32 - Unable to read "AutoRun" value or value not present!
O32 - AutoRun File - [2009/09/08 09:23:30 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O32 - AutoRun File - [2006/03/24 06:06:42 | 000,000,053 | ---- | M] () - X:\AUTORUN.INF -- [ FAT ]
O34 - HKLM BootExecute: (autocheck autochk *) - File not found
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = comfile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2010/12/13 21:14:26 | 000,148,992 | ---- | C] (It Systems) -- C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe
========== Files - Modified Within 30 Days ==========
========== Files Created - No Company Name ==========
[2011/01/04 19:40:42 | 000,256,512 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2011/01/04 19:40:42 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2011/01/04 19:40:42 | 000,089,088 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2011/01/04 19:40:42 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2011/01/04 19:40:42 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2011/01/04 19:24:11 | 000,000,120 | ---- | C] () -- C:\WINDOWS\Rgubo.dat
[2011/01/04 19:24:11 | 000,000,000 | ---- | C] () -- C:\WINDOWS\Tlacigejimi.bin
[2010/08/01 13:44:32 | 000,003,584 | ---- | C] () -- C:\Documents and Settings\Cori Walter\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/03/17 20:37:00 | 000,000,754 | ---- | C] () -- C:\WINDOWS\WORDPAD.INI
[2010/01/09 17:01:06 | 000,000,000 | ---- | C] () -- C:\WINDOWS\TPTray.INI
[2009/12/25 11:54:05 | 000,003,242 | ---- | C] () -- C:\Documents and Settings\Cori Walter\Application Data\wklnhst.dat
[2009/12/25 10:41:00 | 000,000,013 | RHS- | C] () -- C:\WINDOWS\System32\drivers\fbd.sys
[2009/10/27 23:12:05 | 000,000,061 | ---- | C] () -- C:\WINDOWS\smscfg.ini
[2009/10/27 22:59:26 | 000,262,216 | ---- | C] () -- C:\WINDOWS\System32\IPTests.dll
[2009/09/08 10:03:35 | 000,000,000 | ---- | C] () -- C:\WINDOWS\NDSTray.INI
[2009/09/08 10:02:50 | 000,000,353 | ---- | C] () -- C:\WINDOWS\System32\OEMINFO.INI
[2009/09/08 09:58:10 | 000,004,569 | ---- | C] () -- C:\WINDOWS\System32\secupd.dat
[2009/09/08 09:58:00 | 000,434,266 | ---- | C] () -- C:\WINDOWS\System32\perfh009.dat
[2009/09/08 09:58:00 | 000,272,128 | ---- | C] () -- C:\WINDOWS\System32\perfi009.dat
[2009/09/08 09:58:00 | 000,068,386 | ---- | C] () -- C:\WINDOWS\System32\perfc009.dat
[2009/09/08 09:58:00 | 000,028,626 | ---- | C] () -- C:\WINDOWS\System32\perfd009.dat
[2009/09/08 09:57:57 | 000,004,631 | ---- | C] () -- C:\WINDOWS\System32\oembios.dat
[2009/09/08 09:57:55 | 013,107,200 | ---- | C] () -- C:\WINDOWS\System32\oembios.bin
[2009/09/08 09:57:51 | 000,040,960 | ---- | C] () -- C:\WINDOWS\System32\EBLib.DLL
[2009/09/08 09:57:51 | 000,000,741 | ---- | C] () -- C:\WINDOWS\System32\noise.dat
[2009/09/08 09:57:41 | 000,045,056 | ---- | C] () -- C:\WINDOWS\System32\TDispVol.dll
[2009/09/08 09:57:37 | 000,673,088 | ---- | C] () -- C:\WINDOWS\System32\mlang.dat
[2009/09/08 09:57:36 | 000,046,258 | ---- | C] () -- C:\WINDOWS\System32\mib.bin
[2009/09/08 09:57:08 | 000,218,003 | ---- | C] () -- C:\WINDOWS\System32\dssec.dat
[2009/09/08 09:56:57 | 000,001,804 | ---- | C] () -- C:\WINDOWS\System32\Dcache.bin
[2009/09/08 09:52:23 | 000,147,456 | ---- | C] () -- C:\WINDOWS\System32\igfxCoIn_v4926.dll
[2009/09/08 09:25:35 | 000,002,048 | --S- | C] () -- C:\WINDOWS\bootstat.dat
[2009/09/08 09:21:34 | 000,021,640 | ---- | C] () -- C:\WINDOWS\System32\emptyregdb.dat
[2009/09/08 09:20:45 | 000,001,793 | ---- | C] () -- C:\WINDOWS\System32\fxsperf.ini
[2009/09/08 02:18:25 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2009/09/08 02:17:40 | 000,167,504 | ---- | C] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2009/06/06 04:42:40 | 000,028,672 | ---- | C] () -- C:\WINDOWS\System32\TPeculiarity.dll
[2009/04/02 12:35:18 | 000,024,576 | ---- | C] () -- C:\WINDOWS\System32\EKECioCtl.dll
[2009/03/31 14:13:20 | 000,045,056 | ---- | C] () -- C:\WINDOWS\System32\HWS_Ctrl.dll
[2005/03/26 00:00:00 | 000,101,376 | ---- | C] () -- C:\WINDOWS\System32\FORMATUFD.EXE
========== LOP Check ==========
[2009/09/08 10:00:59 | 000,000,000 | ---D | M] -- C:\WINDOWS\system32\config\systemprofile\Application Data\toshiba
[2009/09/08 09:28:04 | 000,000,000 | ---D | M] -- C:\WINDOWS\system32\config\systemprofile\Application Data\WinBatch
[2009/12/25 11:54:05 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\Template
[2009/09/08 10:00:59 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\toshiba
[2009/09/08 09:28:04 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Cori Walter\Application Data\WinBatch
[2010/01/18 08:16:39 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Partner
[2009/09/08 10:02:33 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Toshiba
[2009/09/08 09:57:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Vista32
[2009/09/08 09:57:51 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Vista64
[2009/09/08 10:19:11 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\WildTangent
========== Purity Check ==========
< End of report >
#7

 Posted 13 June 2011 - 01:08 PM
Posted 13 June 2011 - 01:08 PM

Hi cwalter,
Try to start your system normaly after this step and let me know.
Start OTLPE as you did previously
Copy the attached Fix.txt to a USB
Try to start your system normaly after this step and let me know.
Start OTLPE as you did previously
Copy the attached Fix.txt to a USB
- Insert your USB drive with fix.txt on it
- Start OTLPE
- Drag and drop fix.txt into the Custom scans and fixes box
- If you cannot drag and drop for some reason. Then press the Run Fix button and a dialogue box will pop up asking for the location - select the file on your USB drive
- Then click the Run Fix button at the top
- Let the program run unhindered, reboot when it is done to normal mode if possible
Attached Files
#8

 Posted 25 June 2011 - 10:47 AM
Posted 25 June 2011 - 10:47 AM

I'm sorry for the delay. I appreciate your helping me with this.
I ran the step as you described and the netbook won't load on normal mode by itself. When I restarted it, I get a blinking cursor on a black screen.
Here is the log that displayed after I ran the custom fix:
========== OTL ==========
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyEnable|dword:0 /E : value set successfully!
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyOverride| /E : value set successfully!
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyServer| /E : value set successfully!
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\\Ltucaveca deleted successfully.
C:\WINDOWS\oyubeyeyo.dll moved successfully.
Registry value HKEY_USERS\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Run\\dgnikqbr deleted successfully.
C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe moved successfully.
Registry value HKEY_USERS\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Run\\ndkwrsdg deleted successfully.
C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe moved successfully.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce\\*packbootmsg.exe deleted successfully.
Invalid CLSID key: *packbootmsg.exe
C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe moved successfully.
File C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe not found.
========== FILES ==========
File\Folder C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe not found.
File\Folder C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe not found.
OTLPE by OldTimer - Version 3.1.46.0 log created on 06252011_104113
I ran the step as you described and the netbook won't load on normal mode by itself. When I restarted it, I get a blinking cursor on a black screen.
Here is the log that displayed after I ran the custom fix:
========== OTL ==========
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyEnable|dword:0 /E : value set successfully!
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyOverride| /E : value set successfully!
HKU\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Internet Settings\\ProxyServer| /E : value set successfully!
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\\Ltucaveca deleted successfully.
C:\WINDOWS\oyubeyeyo.dll moved successfully.
Registry value HKEY_USERS\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Run\\dgnikqbr deleted successfully.
C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe moved successfully.
Registry value HKEY_USERS\Cori_Walter_ON_C\Software\Microsoft\Windows\CurrentVersion\Run\\ndkwrsdg deleted successfully.
C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe moved successfully.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce\\*packbootmsg.exe deleted successfully.
Invalid CLSID key: *packbootmsg.exe
C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe moved successfully.
File C:\Documents and Settings\LocalService\Local Settings\Application Data\packbootmsg.exe not found.
========== FILES ==========
File\Folder C:\Documents and Settings\Cori Walter\Local Settings\Temp\nrhmgssbi\fjqjagklajb.exe not found.
File\Folder C:\Documents and Settings\Cori Walter\Local Settings\Temp\rrrmgjsrg\fsowkaflajb.exe not found.
OTLPE by OldTimer - Version 3.1.46.0 log created on 06252011_104113
#9

 Posted 27 June 2011 - 11:44 PM
Posted 27 June 2011 - 11:44 PM

Hi cwalter,
Start OTLPE as you did previously from CD
Step 1
Step 2
Restart your system now and see if you can boot it now.
Start OTLPE as you did previously from CD
Step 1
- Start OTLPE and in the custom scans box copy this command
SAVEMBR:0
- Run the quick scan
Step 2
- From OTLPE Desktop start MBRFix by double click
- Please enter this command in Command Prompt
mbrfix /drive 0 fixmbr /yes
- press Enter and if all goes fine you wont see any error messages.
Restart your system now and see if you can boot it now.
#10

 Posted 28 June 2011 - 05:39 PM
Posted 28 June 2011 - 05:39 PM

Yes! It loaded on it's own!
Everything went smoothly.
I have zipped the file and attached it.
Thank you so far!!
Everything went smoothly.
I have zipped the file and attached it.
Thank you so far!!
Attached Files
#11

 Posted 28 June 2011 - 11:02 PM
Posted 28 June 2011 - 11:02 PM

Hi cwalter,
Great news for this morning
What problems do you have now?
Please download Malwarebytes' Anti-Malware
Double Click mbam-setup.exe to install the application.
If MBAM encounters a file that is difficult to remove, you will be presented with 1 of 2 prompts, click OK to either and let MBAM proceed with the disinfection process, if asked to restart the computer, please do so immediately.
Great news for this morning
What problems do you have now?
Please download Malwarebytes' Anti-Malware
Double Click mbam-setup.exe to install the application.
- Make sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select "Perform Quick Scan", then click Scan.
- The scan may take some time to finish, so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected.
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.(See Extra Note)
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy&Paste the entire report in your next reply.
If MBAM encounters a file that is difficult to remove, you will be presented with 1 of 2 prompts, click OK to either and let MBAM proceed with the disinfection process, if asked to restart the computer, please do so immediately.
#12

 Posted 30 June 2011 - 06:05 PM
Posted 30 June 2011 - 06:05 PM

I'm not noticing anything too severe anymore. It does seem to running slower than it used to. Here is the log that saved when I ran anti-malware:
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6989
Windows 5.1.2600 Service Pack 3
Internet Explorer 8.0.6001.18702
6/30/2011 4:54:37 PM
mbam-log-2011-06-30 (16-54-37).txt
Scan type: Quick scan
Objects scanned: 143608
Time elapsed: 3 minute(s), 48 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 1
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 3
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_CURRENT_USER\Software\qni8hj710fdl (Malware.Trace) -> Quarantined and deleted successfully.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\WINDOWS\system32\drivers\atlebtzc.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
c:\documents and settings\cori walter\local settings\Temp\0.17654275996786206.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
c:\documents and settings\cori walter\local settings\Temp\0.7597338067602282.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6989
Windows 5.1.2600 Service Pack 3
Internet Explorer 8.0.6001.18702
6/30/2011 4:54:37 PM
mbam-log-2011-06-30 (16-54-37).txt
Scan type: Quick scan
Objects scanned: 143608
Time elapsed: 3 minute(s), 48 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 1
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 3
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_CURRENT_USER\Software\qni8hj710fdl (Malware.Trace) -> Quarantined and deleted successfully.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\WINDOWS\system32\drivers\atlebtzc.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
c:\documents and settings\cori walter\local settings\Temp\0.17654275996786206.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
c:\documents and settings\cori walter\local settings\Temp\0.7597338067602282.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
#13

 Posted 30 June 2011 - 11:30 PM
Posted 30 June 2011 - 11:30 PM

Hi cwalter,
Nice. Let's try do clean thing up.
Step 1
Download AVPTool from Here to your desktop
Run the programme you have just downloaded to your desktop (it will be randomly named )
First we will run a virus scan
On the first tab select all elements down to Computer and then select start scan
Confirm deletion to all infection AVP finds
Once it has finished select report and post that.
Do not close AVPTool or it will self uninstall, if it does uninstall - then just rerun the setup file on your desktop
Step 2
Step 3
Download and run Puran Disc Defragmenter
For the first run I would recommend a boot defrag and disk check

Step 4
Please don't forget to include these items in your reply:
Nice. Let's try do clean thing up.
Step 1
Download AVPTool from Here to your desktop
Run the programme you have just downloaded to your desktop (it will be randomly named )
First we will run a virus scan
On the first tab select all elements down to Computer and then select start scan
Confirm deletion to all infection AVP finds
Once it has finished select report and post that.
Do not close AVPTool or it will self uninstall, if it does uninstall - then just rerun the setup file on your desktop
Step 2
- Go to Start -> My Computer
- Right click on C: disk and clik on Properties
- Click on tab Tools and click on Check now... button
- Check Automatically fix system errors and Scan for and attempt recovery of bad sectors
- Click Start button
- Confirm schedule disk check next time computer starts with Yes button
- Restart your system and wait while system checks your disk for errors
Step 3
Download and run Puran Disc Defragmenter
For the first run I would recommend a boot defrag and disk check

Step 4
Please don't forget to include these items in your reply:
- AVPTool log
#14

 Posted 02 July 2011 - 08:41 AM
Posted 02 July 2011 - 08:41 AM

So I ran averything...
The only thing is...I think I screwed up the log for the AVPTool. I ran the AVP Tool a first time and thought I did something wrong with removing things. So I ran it again, but as I later discovered, it didn't remove anything because it removed it the first time (and I didn't save the log...).
So I sucked at this step...I'm sorry. But I did everything else as instructed.
The only thing is...I think I screwed up the log for the AVPTool. I ran the AVP Tool a first time and thought I did something wrong with removing things. So I ran it again, but as I later discovered, it didn't remove anything because it removed it the first time (and I didn't save the log...).
So I sucked at this step...I'm sorry. But I did everything else as instructed.
#15

 Posted 03 July 2011 - 01:56 AM
Posted 03 July 2011 - 01:56 AM

Hi cwalter,
How is your system now? Any problems?
How is your system now? Any problems?
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked







 Sign In
Sign In Create Account
Create Account

