Did the repair.bat
Log below
Reset the router as instructed, retyped the various things for connection, rebooted.
Exact same attempted redirection as soon as the connection was made
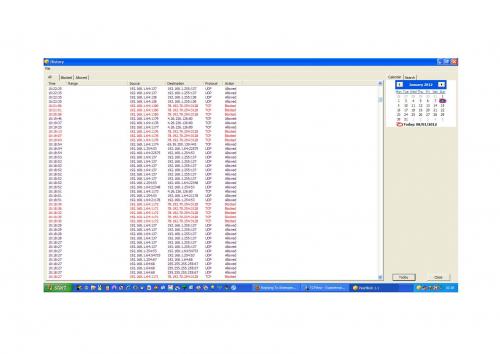
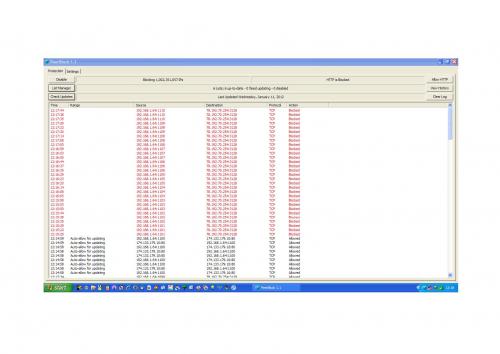
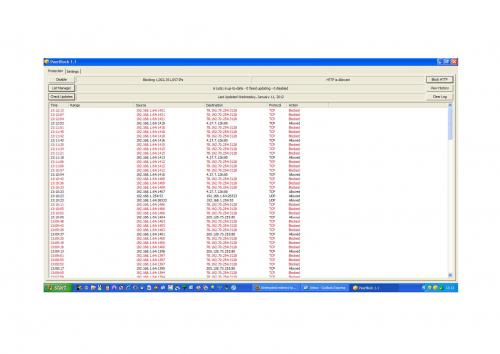
Screendump attached "malware.pdf" (wouldn't let me upload as .docx file)
Reset.txt log:
deleted SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\CacheHashTableBucketSize
deleted SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\CacheHashTableSize
deleted SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\MaxCacheEntryTtlLimit
deleted SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\MaxSoaCacheEntryTtlLimit
reset SYSTEM\CurrentControlSet\Services\Netbt\Parameters\Interfaces\Tcpip_{8814F931-AC3A-428D-889F-6D5AE0FFBB8F}\NameServerList
old REG_MULTI_SZ =
<empty>
added SYSTEM\CurrentControlSet\Services\Netbt\Parameters\Interfaces\Tcpip_{8814F931-AC3A-428D-889F-6D5AE0FFBB8F}\NetbiosOptions
deleted SYSTEM\CurrentControlSet\Services\Netbt\Parameters\EnableLmhosts
deleted SYSTEM\CurrentControlSet\Services\Netbt\Parameters\EnableProxy
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1C89B43F-6880-488C-9C16-DC305AE88D85}\IpAutoconfigurationAddress
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1C89B43F-6880-488C-9C16-DC305AE88D85}\IpAutoconfigurationMask
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1C89B43F-6880-488C-9C16-DC305AE88D85}\IpAutoconfigurationSeed
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1C89B43F-6880-488C-9C16-DC305AE88D85}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1C89B43F-6880-488C-9C16-DC305AE88D85}\TcpWindowSize
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\AddressType
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\Mtu
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{3D154A7C-2857-4DE6-8194-2693FDC33DAD}\UdpAllowedPorts
old REG_MULTI_SZ =
0
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{414E9E6F-D709-45FE-B999-6DE2A936BE84}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{414E9E6F-D709-45FE-B999-6DE2A936BE84}\TcpWindowSize
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\AddressType
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\Mtu
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{455DCAC7-772F-44A5-A724-0859A6853F1C}\UdpAllowedPorts
old REG_MULTI_SZ =
0
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\IpAutoconfigurationAddress
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\IpAutoconfigurationMask
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\IpAutoconfigurationSeed
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\Mtu
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{6A1D0A68-C5F2-401A-81CD-EB6210573F1F}\UdpAllowedPorts
old REG_MULTI_SZ =
0
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\IpAutoconfigurationAddress
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\IpAutoconfigurationMask
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\IpAutoconfigurationSeed
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{70CD94B5-9D8C-486E-B8E8-3D3AFB6444E7}\UdpAllowedPorts
old REG_MULTI_SZ =
0
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A545EDF-3EBE-41C5-B268-01AB4F12860F}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A545EDF-3EBE-41C5-B268-01AB4F12860F}\TcpWindowSize
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\AddressType
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\Mtu
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7A8F0683-4D03-4AFE-919F-D6ED856F8F67}\UdpAllowedPorts
old REG_MULTI_SZ =
0
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7B48EE6F-0AC9-4D66-BFD6-E287EAFDDF41}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{7B48EE6F-0AC9-4D66-BFD6-E287EAFDDF41}\TcpWindowSize
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{8814F931-AC3A-428D-889F-6D5AE0FFBB8F}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{8814F931-AC3A-428D-889F-6D5AE0FFBB8F}\NameServer
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{8814F931-AC3A-428D-889F-6D5AE0FFBB8F}\TcpWindowSize
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{93AC5D81-74F9-4571-B409-C7870CD9B12D}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{93AC5D81-74F9-4571-B409-C7870CD9B12D}\TcpWindowSize
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\AddressType
added SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\DisableDynamicUpdate
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\Mtu
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\RawIpAllowedProtocols
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\TcpAllowedPorts
old REG_MULTI_SZ =
0
reset SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{99DF8FB4-AFD3-4B43-8321-504213A3102F}\UdpAllowedPorts
old REG_MULTI_SZ =
0
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B8CA05A4-E231-4FBE-A782-B4D8DD27F3EE}\IpAutoconfigurationAddress
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B8CA05A4-E231-4FBE-A782-B4D8DD27F3EE}\IpAutoconfigurationMask
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B8CA05A4-E231-4FBE-A782-B4D8DD27F3EE}\IpAutoconfigurationSeed
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B8CA05A4-E231-4FBE-A782-B4D8DD27F3EE}\Mtu
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B8CA05A4-E231-4FBE-A782-B4D8DD27F3EE}\TcpWindowSize
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DefaultTtl
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DisableTaskOffload
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DontAddDefaultGatewayDefault
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnableIcmpRedirect
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnablePmtuBhDetect
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnablePmtuDiscovery
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnableSecurityFilters
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\GlobalMaxTcpWindowSize
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\MaxUserPort
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\SackOpts
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\SearchList
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\SynAttackProtect
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Tcp1323Opts
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\TcpMaxDupAcks
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\TcpTimedWaitDelay
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\TcpWindowSize
deleted SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\UseDomainNameDevolution
reset Linkage\UpperBind for USB\VID_0BDA&PID_8187\6&301DA863&0&4. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8189\6&301DA863&0&1. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8187\6&301DA863&0&1. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8187\6&AAA4719&0&1. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8187\6&1D63F7BE&0&1. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8187\5&2E60703B&0&5. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for USB\VID_0BDA&PID_8189\00E04C000001. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for ROOT\MS_NDISWANBH\0000. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for PCI\VEN_8086&DEV_27DC&SUBSYS_2A22103C&REV_01\4&1AF1648C&0&40F0. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for ROOT\MS_NDISWANIP\0000. bad value was:
REG_MULTI_SZ =
PSched
reset Linkage\UpperBind for PCI\VEN_10EC&DEV_8139&SUBSYS_577C1462&REV_10\4&1A671D0C&0&60F0. bad value was:
REG_MULTI_SZ =
PSched
<completed>

 This topic is locked
This topic is locked















 Sign In
Sign In Create Account
Create Account

