Sorry i took so long to reply but i have been a way for the weekend. Here is a coppy of the scans you asked me to do.
Thank you
OTL logfile created on: 12/5/2011 11:07:56 AM - Run 1
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Users\Paul\Downloads
Home Premium Edition Service Pack 1 (Version = 6.1.7601) - Type = NTWorkstation
Internet Explorer (Version = 9.0.8112.16421)
Locale: 00000409 | Country: United Kingdom | Language: ENG | Date Format: dd/MM/yyyy
2.93 Gb Total Physical Memory | 2.06 Gb Available Physical Memory | 70.16% Memory free
5.93 Gb Paging File | 4.97 Gb Available in Paging File | 83.87% Paging File free
Paging file location(s): C:\pagefile.sys 3070 3070 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\Windows | %ProgramFiles% = C:\Program Files
Drive C: | 149.05 Gb Total Space | 111.19 Gb Free Space | 74.60% Space Free | Partition Type: NTFS
Drive E: | 44.81 Mb Total Space | 0.00 Mb Free Space | 0.00% Space Free | Partition Type: CDFS
Computer Name: PAUL-PC | User Name: Paul | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ========== PRC - [2011/12/04 18:11:23 | 000,584,192 | ---- | M] (OldTimer Tools) -- C:\Users\Paul\Downloads\OTL.exe
PRC - [2011/11/28 18:01:24 | 003,744,552 | ---- | M] (AVAST Software) -- C:\Program Files\Alwil Software\Avast5\AvastUI.exe
PRC - [2011/11/28 18:01:23 | 000,044,768 | ---- | M] (AVAST Software) -- C:\Program Files\Alwil Software\Avast5\AvastSvc.exe
PRC - [2011/11/07 21:28:26 | 001,652,536 | ---- | M] (Trusteer Ltd.) -- C:\Program Files\Trusteer\Rapport\bin\RapportService.exe
PRC - [2011/11/07 21:28:26 | 000,931,640 | ---- | M] (Trusteer Ltd.) -- C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe
PRC - [2011/11/03 14:44:28 | 000,497,280 | ---- | M] (Check Point Software Technologies) -- C:\Program Files\CheckPoint\ZAForceField\ISWSVC.exe
PRC - [2011/10/19 15:28:18 | 000,025,464 | ---- | M] (Uniblue Systems Limited) -- C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe
PRC - [2011/10/05 20:18:50 | 001,051,760 | ---- | M] (Badoo) -- C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe
PRC - [2011/02/25 05:30:54 | 002,616,320 | ---- | M] (Microsoft Corporation) -- C:\Windows\explorer.exe
PRC - [2010/11/20 12:17:47 | 000,049,152 | ---- | M] (Microsoft Corporation) -- C:\Windows\System32\taskhost.exe
PRC - [2009/01/26 14:31:10 | 001,153,368 | ---- | M] (Safer Networking Ltd.) -- C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe
========== Modules (No Company Name) ========== MOD - [2011/10/30 20:57:06 | 000,557,056 | ---- | M] () -- C:\Program Files\Trusteer\Rapport\bin\js32.dll
MOD - [2011/09/21 18:27:18 | 000,516,368 | ---- | M] () -- C:\ProgramData\Trusteer\Rapport\store\exts\RapportMS\28896\RapportMS.dll
========== Win32 Services (SafeList) ========== SRV - [2011/11/28 18:01:23 | 000,044,768 | ---- | M] (AVAST Software) [Auto | Running] -- C:\Program Files\Alwil Software\Avast5\AvastSvc.exe -- (avast! Antivirus)
SRV - [2011/11/09 20:05:42 | 002,420,616 | ---- | M] (Check Point Software Technologies LTD) [Auto | Stopped] -- C:\Program Files\CheckPoint\ZoneAlarm\vsmon.exe -- (vsmon)
SRV - [2011/11/07 21:28:26 | 000,931,640 | ---- | M] (Trusteer Ltd.) [Auto | Running] -- C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe -- (RapportMgmtService)
SRV - [2011/11/03 14:44:28 | 000,497,280 | ---- | M] (Check Point Software Technologies) [Auto | Running] -- C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe -- (IswSvc)
SRV - [2011/08/31 16:00:48 | 000,366,152 | ---- | M] (Malwarebytes Corporation) [Disabled | Stopped] -- C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe -- (MBAMService)
SRV - [2011/06/06 11:55:28 | 000,064,952 | ---- | M] (Adobe Systems Incorporated) [Disabled | Stopped] -- C:\Program Files\Common Files\Adobe\ARM\1.0\armsvc.exe -- (AdobeARMservice)
SRV - [2011/02/10 14:29:24 | 000,150,528 | ---- | M] (Avanquest Software) [Disabled | Stopped] -- C:\Program Files\Sony Ericsson\Sony Ericsson PC Companion\PCCService.exe -- (Sony Ericsson PCCompanion)
SRV - [2010/10/09 22:24:13 | 001,343,400 | ---- | M] (Microsoft Corporation) [Unknown | Stopped] -- C:\Windows\System32\Wat\WatAdminSvc.exe -- (WatAdminSvc)
SRV - [2010/09/01 15:51:28 | 000,066,112 | ---- | M] (NOS Microsystems Ltd.) [On_Demand | Stopped] -- C:\Program Files\NOS\bin\getPlus_Helper_3004.dll -- (nosGetPlusHelper) getPlus®
SRV - [2009/07/14 01:16:13 | 000,025,088 | ---- | M] (Microsoft Corporation) [On_Demand | Stopped] -- C:\Windows\System32\sensrsvc.dll -- (SensrSvc)
SRV - [2009/07/14 01:15:41 | 000,680,960 | ---- | M] (Microsoft Corporation) [Auto | Running] -- C:\Program Files\Windows Defender\MpSvc.dll -- (WinDefend)
SRV - [2009/01/26 14:31:10 | 001,153,368 | ---- | M] (Safer Networking Ltd.) [Auto | Running] -- C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe -- (SBSDWSCService)
========== Driver Services (SafeList) ========== DRV - [2011/11/28 17:53:53 | 000,435,032 | ---- | M] (AVAST Software) [File_System | System | Running] -- C:\Windows\System32\drivers\aswSnx.sys -- (aswSnx)
DRV - [2011/11/28 17:53:35 | 000,314,456 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\Windows\System32\drivers\aswSP.sys -- (aswSP)
DRV - [2011/11/28 17:52:19 | 000,034,392 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\Windows\System32\drivers\aswRdr.sys -- (aswRdr)
DRV - [2011/11/28 17:52:16 | 000,052,952 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\Windows\System32\drivers\aswTdi.sys -- (aswTdi)
DRV - [2011/11/28 17:52:07 | 000,055,128 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\Windows\System32\drivers\aswMonFlt.sys -- (aswMonFlt)
DRV - [2011/11/28 17:51:50 | 000,020,568 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\Windows\System32\drivers\aswFsBlk.sys -- (aswFsBlk)
DRV - [2011/11/07 21:30:20 | 000,227,312 | ---- | M] () [Kernel | System | Running] -- C:\ProgramData\Trusteer\Rapport\store\exts\RapportCerberus\baseline\RapportCerberus32_32301.sys -- (RapportCerberus_32301)
DRV - [2011/11/07 21:28:40 | 000,071,440 | ---- | M] (Trusteer Ltd.) [Kernel | System | Running] -- C:\Program Files\Trusteer\Rapport\bin\RapportEI.sys -- (RapportEI)
DRV - [2011/11/07 21:28:38 | 000,164,112 | ---- | M] (Trusteer Ltd.) [Kernel | System | Running] -- C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys -- (RapportPG)
DRV - [2011/11/03 14:44:20 | 000,027,016 | ---- | M] (Check Point Software Technologies) [Kernel | Auto | Running] -- C:\Program Files\CheckPoint\ZAForceField\ISWKL.sys -- (ISWKL)
DRV - [2011/10/07 17:13:02 | 000,232,512 | ---- | M] (DT Soft Ltd) [Kernel | System | Running] -- C:\Windows\System32\drivers\dtsoftbus01.sys -- (dtsoftbus01)
DRV - [2011/09/21 18:27:16 | 000,021,520 | ---- | M] (Trusteer Ltd.) [Kernel | On_Demand | Running] -- c:\ProgramData\Trusteer\Rapport\store\exts\RapportMS\28896\RapportIaso.sys -- (RapportIaso)
DRV - [2011/08/31 16:00:50 | 000,022,216 | ---- | M] (Malwarebytes Corporation) [File_System | On_Demand | Stopped] -- C:\Windows\System32\drivers\mbam.sys -- (MBAMProtector)
DRV - [2011/08/04 00:27:18 | 007,517,696 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\NETwNs32.sys -- (NETwNs32) ___ Intel®
DRV - [2011/05/07 17:51:28 | 000,455,256 | ---- | M] (Check Point Software Technologies LTD) [Kernel | System | Running] -- C:\Windows\System32\drivers\vsdatant.sys -- (Vsdatant)
DRV - [2011/03/20 23:31:18 | 000,193,792 | ---- | M] (Huawei Technologies Co., Ltd.) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\ewusbmdm.sys -- (hwdatacard)
DRV - [2011/01/31 15:04:32 | 000,144,472 | ---- | M] (JMicron Technology Corporation) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\jmcr.sys -- (JMCR)
DRV - [2010/11/20 10:24:41 | 000,052,224 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\TsUsbFlt.sys -- (TsUsbFlt)
DRV - [2010/11/20 09:59:44 | 000,035,968 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\winusb.sys -- (WinUsb)
DRV - [2010/03/15 15:44:48 | 000,127,488 | ---- | M] (Intel® Corporation) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\IntcHdmi.sys -- (IntcHdmiAddService) Intel®
DRV - [2010/02/12 15:11:44 | 001,766,784 | ---- | M] () [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\snp2uvc.sys -- (SNP2UVC) USB2.0 PC Camera (SNP2UVC)
DRV - [2009/09/16 02:40:18 | 006,114,816 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\NETw5s32.sys -- (NETw5s32) Intel®
DRV - [2009/07/13 23:52:10 | 000,014,336 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\vwifimp.sys -- (vwifimp)
DRV - [2009/07/13 22:13:48 | 001,035,776 | ---- | M] (LSI Corp) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2009/07/13 22:02:51 | 004,231,168 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\netw5v32.sys -- (netw5v32) Intel®
DRV - [2009/03/25 15:48:00 | 000,114,728 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018mdm.sys -- (s1018mdm)
DRV - [2009/03/25 15:48:00 | 000,109,864 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018unic.sys -- (s1018unic) Sony Ericsson Device 1018 USB Ethernet Emulation (WDM)
DRV - [2009/03/25 15:48:00 | 000,106,208 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018mgmt.sys -- (s1018mgmt) Sony Ericsson Device 1018 USB WMC Device Management Drivers (WDM)
DRV - [2009/03/25 15:48:00 | 000,104,744 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018obex.sys -- (s1018obex)
DRV - [2009/03/25 15:48:00 | 000,086,824 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018bus.sys -- (s1018bus) Sony Ericsson Device 1018 driver (WDM)
DRV - [2009/03/25 15:48:00 | 000,026,024 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018nd5.sys -- (s1018nd5) Sony Ericsson Device 1018 USB Ethernet Emulation (NDIS)
DRV - [2009/03/25 15:48:00 | 000,015,016 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s1018mdfl.sys -- (s1018mdfl)
DRV - [2008/05/16 10:33:14 | 000,115,752 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016unic.sys -- (s0016unic) Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (WDM)
DRV - [2008/05/16 10:33:14 | 000,025,512 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016nd5.sys -- (s0016nd5) Sony Ericsson Device 0016 USB Ethernet Emulation SEMC0016 (NDIS)
DRV - [2008/05/16 10:33:14 | 000,015,016 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016mdfl.sys -- (s0016mdfl)
DRV - [2008/05/16 10:33:12 | 000,120,744 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016mdm.sys -- (s0016mdm)
DRV - [2008/05/16 10:33:12 | 000,114,216 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016mgmt.sys -- (s0016mgmt) Sony Ericsson Device 0016 USB WMC Device Management Drivers (WDM)
DRV - [2008/05/16 10:33:12 | 000,110,632 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016obex.sys -- (s0016obex)
DRV - [2008/05/16 10:33:12 | 000,089,256 | ---- | M] (MCCI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\System32\drivers\s0016bus.sys -- (s0016bus) Sony Ericsson Device 0016 driver (WDM)
DRV - [2007/03/28 14:51:40 | 000,043,008 | ---- | M] (Winbond Electronics Corporation) [Kernel | On_Demand | Running] -- C:\Windows\System32\drivers\winbondcir.sys -- (winbondcir)
========== Standard Registry (SafeList) ========== ========== Internet Explorer ========== IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page =
http://badoo.com/startpage/IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page Redirect Cache =
http://uk.msn.com/?ocid=iehpIE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page Redirect Cache AcceptLangs = en-GB
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page Redirect Cache_TIMESTAMP = 9A 07 59 3A 02 42 CC 01 [binary data]
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\URLSearchHook: {14940384-1ea8-4976-9800-2c1d1c350bf0} - No CLSID value found
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\URLSearchHook: {88c7f2aa-f93f-432c-8f0e-b7d85967a527} - No CLSID value found
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\URLSearchHook: {90b49673-5506-483e-b92b-ca0265bd9ca8} - No CLSID value found
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\URLSearchHook: {91da5e8a-3318-4f8c-b67e-5964de3ab546} - No CLSID value found
IE - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ========== FF - prefs.js..browser.search.defaultenginename: "Search"
FF - prefs.js..browser.search.selectedEngine: "Search"
FF - prefs.js..browser.startup.homepage: "
http://badoo.com/startpage/"FF - prefs.js..extensions.enabledItems: {ABDE892B-13A8-4d1b-88E6-365A6E755758}:14.0.2
FF - prefs.js..extensions.enabledItems: {7b13ec3e-999a-4b70-b9cb-2617b8323822}:2.7.1.3
FF - prefs.js..extensions.enabledItems:
[email protected]:1.6.2
FF - prefs.js..extensions.enabledItems:
[email protected]:0.9.8.0
FF - prefs.js..extensions.enabledItems: {CAFEEFAC-0016-0000-0024-ABCDEFFEDCBA}:6.0.24
FF - prefs.js..extensions.enabledItems:
[email protected]:20110101
FF - prefs.js..keyword.URL: "chrome://browser-region/locale/region.properties"
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\Windows\system32\Macromed\Flash\NPSWF32.dll ()
FF - HKLM\Software\MozillaPlugins\@adobe.com/ShockwavePlayer: C:\Windows\system32\Adobe\Director\np32dsw.dll (Adobe Systems, Inc.)
FF - HKLM\Software\MozillaPlugins\@checkpoint.com/FFApi: C:\Program Files\CheckPoint\ZAForceField\TrustChecker\bin\npFFApi.dll ()
FF - HKLM\Software\MozillaPlugins\@Google.com/GoogleEarthPlugin: C:\Program Files\Google\Google Earth\plugin\npgeplugin.dll (Google)
FF - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin: C:\Program Files\Java\jre7\bin\new_plugin\npjp2.dll (Oracle Corporation)
FF - HKLM\Software\MozillaPlugins\@messenger.yahoo.com/YahooMessengerStatePlugin;version=1.0.0.6: C:\Program Files\Yahoo!\Shared\npYState.dll (Yahoo! Inc.)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/GENUINE: disabled File not found
FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\4.0.60831.0\npctrl.dll ( Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WLPG,version=15.4.3502.0922: C:\Program Files\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WLPG,version=15.4.3508.1109: C:\Program Files\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WLPG,version=15.4.3538.0513: C:\Program Files\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@nosltd.com/getPlus+®,version=1.6.2.91: C:\Program Files\NOS\bin\np_gp.dll (NOS Microsystems Ltd.)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=3: C:\Program Files\Google\Update\1.3.21.79\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=9: C:\Program Files\Google\Update\1.3.21.79\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\Adobe Reader: C:\Program Files\Adobe\Reader 10.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF - HKCU\Software\MozillaPlugins\@tools.google.com/Google Update;version=3: C:\Users\Paul\AppData\Local\Google\Update\1.3.21.79\npGoogleUpdate3.dll (Google Inc.)
FF - HKCU\Software\MozillaPlugins\@tools.google.com/Google Update;version=9: C:\Users\Paul\AppData\Local\Google\Update\1.3.21.79\npGoogleUpdate3.dll (Google Inc.)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\
[email protected]: C:\Program Files\Alwil Software\Avast5\WebRep\FF [2011/11/29 14:38:33 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{FFB96CC1-7EB3-449D-B827-DB661701C6BB}: C:\Program Files\CheckPoint\ZAForceField\TrustChecker [2011/11/12 14:31:42 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 7.0.1\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2011/11/28 13:51:30 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 7.0.1\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins [2011/11/28 13:51:30 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Components: C:\Program Files\Mozilla Thunderbird\components [2011/11/28 13:51:30 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Plugins: C:\Program Files\Mozilla Thunderbird\plugins
[2010/10/09 21:59:18 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Paul\AppData\Roaming\Mozilla\Extensions
[2011/11/16 23:18:06 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Paul\AppData\Roaming\Mozilla\Firefox\Profiles\t3di2n8w.default\extensions
[2011/11/16 23:18:06 | 000,000,000 | ---D | M] (Zynga Community Toolbar) -- C:\Users\Paul\AppData\Roaming\Mozilla\Firefox\Profiles\t3di2n8w.default\extensions\{7b13ec3e-999a-4b70-b9cb-2617b8323822}
[2011/03/16 01:03:03 | 000,000,000 | ---D | M] (Personas) -- C:\Users\Paul\AppData\Roaming\Mozilla\Firefox\Profiles\t3di2n8w.default\extensions\
[email protected][2011/07/14 17:56:49 | 000,002,023 | ---- | M] () -- C:\Users\Paul\AppData\Roaming\Mozilla\Firefox\Profiles\t3di2n8w.default\searchplugins\badoo.xml
[2011/11/16 23:12:30 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2011/08/23 15:41:54 | 000,000,000 | ---D | M] (Click to call with Skype) -- C:\Program Files\Mozilla Firefox\extensions\{82AF8DCA-6DE9-405D-BD5E-43525BDAD38A}
[2011/02/18 16:09:28 | 000,000,000 | ---D | M] (Java Console) -- C:\Program Files\Mozilla Firefox\extensions\{CAFEEFAC-0016-0000-0024-ABCDEFFEDCBA}
[2011/07/07 17:02:53 | 000,000,000 | ---D | M] (Java Console) -- C:\Program Files\Mozilla Firefox\extensions\{CAFEEFAC-0016-0000-0026-ABCDEFFEDCBA}
[2011/08/03 12:18:28 | 000,000,000 | ---D | M] (Java Console) -- C:\Program Files\Mozilla Firefox\extensions\{CAFEEFAC-0017-0000-0000-ABCDEFFEDCBA}
[2011/11/16 23:12:30 | 000,000,000 | ---D | M] (Java Console) -- C:\Program Files\Mozilla Firefox\extensions\{CAFEEFAC-0017-0000-0001-ABCDEFFEDCBA}
[2011/11/29 14:38:33 | 000,000,000 | ---D | M] (avast! WebRep) -- C:\PROGRAM FILES\ALWIL SOFTWARE\AVAST5\WEBREP\FF
() (No name found) -- C:\USERS\PAUL\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\T3DI2N8W.DEFAULT\EXTENSIONS\
[email protected][2011/11/09 11:35:13 | 000,134,104 | ---- | M] (Mozilla Foundation) -- C:\Program Files\mozilla firefox\components\browsercomps.dll
[2011/10/03 02:53:41 | 000,611,224 | ---- | M] (Oracle Corporation) -- C:\Program Files\mozilla firefox\plugins\npdeployJava1.dll
[2011/09/23 01:16:00 | 000,002,252 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing.xml
========== Chrome ========== CHR - default_search_provider: Google (Enabled)
CHR - default_search_provider: search_url = {google:baseURL}search?{google:RLZ}{google:acceptedSuggestion}{google:originalQueryForSuggestion}{google:searchFieldtrialParameter}{google:instantFieldTrialGroupParameter}sourceid=chrome&ie={inputEncoding}&q={searchTerms}
CHR - default_search_provider: suggest_url = {google:baseSuggestURL}search?{google:searchFieldtrialParameter}{google:instantFieldTrialGroupParameter}client=chrome&hl={language}&q={searchTerms}
CHR - plugin: Shockwave Flash (Enabled) = C:\Users\Paul\AppData\Local\Google\Chrome\Application\15.0.874.121\gcswf32.dll
CHR - plugin: Shockwave Flash (Enabled) = C:\Windows\system32\Macromed\Flash\NPSWF32.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin2.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin3.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin4.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin5.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin6.dll
CHR - plugin: QuickTime Plug-in 7.6.9 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\npqtplugin7.dll
CHR - plugin: Java Deployment Toolkit 6.0.240.7 (Enabled) = C:\Program Files\Java\jre6\bin\new_plugin\npdeployJava1.dll
CHR - plugin: Java™ Platform SE 6 U24 (Enabled) = C:\Program Files\Java\jre6\bin\new_plugin\npjp2.dll
CHR - plugin: Adobe Acrobat (Disabled) = C:\Program Files\Adobe\Reader 10.0\Reader\Browser\nppdf32.dll
CHR - plugin: Silverlight Plug-In (Enabled) = c:\Program Files\Microsoft Silverlight\4.0.60531.0\npctrl.dll
CHR - plugin: Shockwave for Director (Enabled) = C:\Windows\system32\Adobe\Director\np32dsw.dll
CHR - plugin: RealPlayer™ G2 LiveConnect-Enabled Plug-In (32-bit) (Enabled) = C:\Program Files\Mozilla Firefox\plugins\nppl3260.dll
CHR - plugin: RealPlayer Version Plugin (Enabled) = C:\Program Files\Mozilla Firefox\plugins\nprpjplug.dll
CHR - plugin: RealNetworks™ RealPlayer Chrome Background Extension Plug-In (32-bit) (Enabled) = C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll
CHR - plugin: RealPlayer™ HTML5VideoShim Plug-In (32-bit) (Enabled) = C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll
CHR - plugin: Chrome NaCl (Enabled) = C:\Users\Paul\AppData\Local\Google\Chrome\Application\15.0.874.121\ppGoogleNaClPluginChrome.dll
CHR - plugin: Chrome PDF Viewer (Enabled) = C:\Users\Paul\AppData\Local\Google\Chrome\Application\15.0.874.121\pdf.dll
CHR - plugin: RealJukebox NS Plugin (Enabled) = C:\Program Files\Mozilla Firefox\plugins\nprjplug.dll
CHR - plugin: getPlusPlus for Adobe 16291 (Enabled) = C:\Program Files\Mozilla Firefox\plugins\np_gp.dll
CHR - plugin: Google Earth Plugin (Enabled) = C:\Program Files\Google\Google Earth\plugin\npgeplugin.dll
CHR - plugin: Google Update (Enabled) = C:\Program Files\Google\Update\1.3.21.57\npGoogleUpdate3.dll
CHR - plugin: Windows Live\u0099 Photo Gallery (Enabled) = C:\Program Files\Windows Live\Photo Gallery\NPWLPG.dll
CHR - plugin: Default Plug-in (Enabled) = default_plugin
CHR - Extension: avast! WebRep = C:\Users\Paul\AppData\Local\Google\Chrome\User Data\Default\Extensions\icmlaeflemplmjndnaapfdbbnpncnbda\6.0.1367_0\
CHR - Extension: Zynga = C:\Users\Paul\AppData\Local\Google\Chrome\User Data\Default\Extensions\ihcgmidjhhnnjikpigolabhacfngibde\2.3.0.15_0\
O1 HOSTS File: ([2011/11/22 01:28:30 | 000,438,702 | R--- | M]) - C:\Windows\System32\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 www.007guard.com
O1 - Hosts: 127.0.0.1 007guard.com
O1 - Hosts: 127.0.0.1 008i.com
O1 - Hosts: 127.0.0.1 www.008k.com
O1 - Hosts: 127.0.0.1 008k.com
O1 - Hosts: 127.0.0.1 www.00hq.com
O1 - Hosts: 127.0.0.1 00hq.com
O1 - Hosts: 127.0.0.1 010402.com
O1 - Hosts: 127.0.0.1 www.032439.com
O1 - Hosts: 127.0.0.1 032439.com
O1 - Hosts: 127.0.0.1 www.0scan.com
O1 - Hosts: 127.0.0.1 0scan.com
O1 - Hosts: 127.0.0.1 1000gratisproben.com
O1 - Hosts: 127.0.0.1 www.1000gratisproben.com
O1 - Hosts: 127.0.0.1 1001namen.com
O1 - Hosts: 127.0.0.1 www.1001namen.com
O1 - Hosts: 127.0.0.1 100888290cs.com
O1 - Hosts: 127.0.0.1 www.100888290cs.com
O1 - Hosts: 127.0.0.1 www.100sexlinks.com
O1 - Hosts: 127.0.0.1 100sexlinks.com
O1 - Hosts: 127.0.0.1 10sek.com
O1 - Hosts: 127.0.0.1 www.10sek.com
O1 - Hosts: 127.0.0.1 www.1-2005-search.com
O1 - Hosts: 127.0.0.1 1-2005-search.com
O1 - Hosts: 127.0.0.1 123fporn.info
O1 - Hosts: 15087 more lines...
O2 - BHO: (no name) - {02478D38-C3F9-4efb-9B51-7695ECA05670} - No CLSID value found.
O2 - BHO: (Shareaza Web Download Hook) - {0EEDB912-C5FA-486F-8334-57288578C627} - C:\Program Files\Shareaza\RazaWebHook32.dll (Shareaza Development Team)
O2 - BHO: (Spybot-S&D IE Protection) - {53707962-6F74-2D53-2644-206D7942484F} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O2 - BHO: (ZoneAlarm Security Engine Registrar) - {8A4A36C2-0535-4D2C-BD3D-496CB7EED6E3} - C:\Program Files\CheckPoint\ZAForceField\Trustchecker\bin\TrustCheckerIEPlugin.dll (Check Point Software Technologies)
O2 - BHO: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\Alwil Software\Avast5\aswWebRepIE.dll (AVAST Software)
O2 - BHO: (Skype Browser Helper) - {AE805869-2E5C-4ED4-8F7B-F1F7851A4497} - C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O2 - BHO: (Java™ Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre7\bin\jp2ssv.dll (Oracle Corporation)
O3 - HKLM\..\Toolbar: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\Alwil Software\Avast5\aswWebRepIE.dll (AVAST Software)
O3 - HKLM\..\Toolbar: (ZoneAlarm Security Engine) - {EE2AC4E5-B0B0-4EC6-88A9-BCA1A32AB107} - C:\Program Files\CheckPoint\ZAForceField\Trustchecker\bin\TrustCheckerIEPlugin.dll (Check Point Software Technologies)
O3 - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\Toolbar\WebBrowser: (no name) - {14940384-1EA8-4976-9800-2C1D1C350BF0} - No CLSID value found.
O3 - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\Toolbar\WebBrowser: (no name) - {D4027C7F-154A-4066-A1AD-4243D8127440} - No CLSID value found.
O3 - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000\..\Toolbar\WebBrowser: (ZoneAlarm Security Engine) - {EE2AC4E5-B0B0-4EC6-88A9-BCA1A32AB107} - C:\Program Files\CheckPoint\ZAForceField\Trustchecker\bin\TrustCheckerIEPlugin.dll (Check Point Software Technologies)
O4 - HKLM..\Run: [avast5] C:\Program Files\Alwil Software\Avast5\avastUI.exe (AVAST Software)
O4 - HKLM..\Run: [ISW] File not found
O4 - HKLM..\Run: [ZoneAlarm] C:\Program Files\CheckPoint\ZoneAlarm\zatray.exe (Check Point Software Technologies LTD)
O4 - HKU\S-1-5-21-1232758047-3035005367-2970806742-1000..\Run: [Badoo Desktop] C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe (Badoo)
O4 - HKU\S-1-5-19..\RunOnce: [mctadmin] C:\Windows\System32\mctadmin.exe (Microsoft Corporation)
O4 - HKU\S-1-5-20..\RunOnce: [mctadmin] C:\Windows\System32\mctadmin.exe (Microsoft Corporation)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorAdmin = 5
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorUser = 3
O8 - Extra context menu item: Download with &Shareaza - C:\Program Files\Shareaza\RazaWebHook32.dll (Shareaza Development Team)
O9 - Extra Button: Click to call with Skype - {898EA8C8-E7FF-479B-8935-AEC46303B9E5} - C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O9 - Extra 'Tools' menuitem : Click to call with Skype - {898EA8C8-E7FF-479B-8935-AEC46303B9E5} - C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O9 - Extra 'Tools' menuitem : Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O13 - gopher Prefix: missing
O16 - DPF: {22945A69-1191-4DCF-9E6F-409BDE94D101}
http://louk.solidwor...elsStandard.cab (Reg Error: Key error.)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93}
http://java.sun.com/...indows-i586.cab (Java Plug-in 10.1.0)
O16 - DPF: {CAFEEFAC-0016-0000-0026-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_26)
O16 - DPF: {CAFEEFAC-0017-0000-0001-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.7.0_01)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.7.0_01)
O18 - Protocol\Handler\skype-ie-addon-data {91774881-D725-4E58-B298-07617B9B86A8} - C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O20 - HKLM Winlogon: Shell - (explorer.exe) -C:\Windows\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\Windows\system32\userinit.exe) -C:\Windows\System32\userinit.exe (Microsoft Corporation)
O20 - HKLM Winlogon: VMApplet - (SystemPropertiesPerformance.exe) -C:\Windows\System32\SystemPropertiesPerformance.exe (Microsoft Corporation)
O20 - HKLM Winlogon: VMApplet - (/pagefile) - File not found
O21 - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found.
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2009/03/22 02:28:05 | 000,005,560 | ---- | M] () - C:\AutoCADConfig.pit -- [ NTFS ]
O32 - AutoRun File - [2009/06/10 21:42:20 | 000,000,024 | ---- | M] () - C:\autoexec.bat -- [ NTFS ]
O32 - AutoRun File - [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.) - E:\AutoRun.exe -- [ CDFS ]
O32 - AutoRun File - [2008/09/12 10:31:22 | 000,025,214 | R--- | M] () - E:\AutoRun.ico -- [ CDFS ]
O32 - AutoRun File - [2008/09/12 10:23:04 | 000,000,045 | R--- | M] () - E:\AUTORUN.INF -- [ CDFS ]
O33 - MountPoints2\{36ed10a4-14de-11e0-9850-806e6f6e6963}\Shell - "" = AutoRun
O33 - MountPoints2\{36ed10a4-14de-11e0-9850-806e6f6e6963}\Shell\AutoRun\command - "" = E:\AutoRun.exe -- [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.)
O33 - MountPoints2\{4fd482be-3b6d-11e0-859e-001e68ebdbd2}\Shell - "" = AutoRun
O33 - MountPoints2\{4fd482be-3b6d-11e0-859e-001e68ebdbd2}\Shell\AutoRun\command - "" = E:\AutoRun.exe -- [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.)
O33 - MountPoints2\{b973ddc7-d3cb-11df-adb3-001e68ebdbd2}\Shell - "" = AutoRun
O33 - MountPoints2\{b973ddc7-d3cb-11df-adb3-001e68ebdbd2}\Shell\AutoRun\command - "" = F:\AUTORUN.EXE
O33 - MountPoints2\{cb641817-d3ed-11df-ae41-001e68ebdbd2}\Shell - "" = AutoRun
O33 - MountPoints2\{cb641817-d3ed-11df-ae41-001e68ebdbd2}\Shell\AutoRun\command - "" = E:\AutoRun.exe -- [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.)
O33 - MountPoints2\{d4bdb772-e1d9-11df-abc8-001e68ebdbd2}\Shell - "" = AutoRun
O33 - MountPoints2\{d4bdb772-e1d9-11df-abc8-001e68ebdbd2}\Shell\AutoRun\command - "" = E:\AutoRun.exe -- [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.)
O33 - MountPoints2\{e57450f2-f103-11e0-af08-001e68ebdbd2}\Shell - "" = AutoRun
O33 - MountPoints2\{e57450f2-f103-11e0-af08-001e68ebdbd2}\Shell\AutoRun\command - "" = G:\setup\rsrc\Autorun.exe
O33 - MountPoints2\{e57450f2-f103-11e0-af08-001e68ebdbd2}\Shell\dinstall\command - "" = G:\Directx\dxsetup.exe
O33 - MountPoints2\E\Shell - "" = AutoRun
O33 - MountPoints2\E\Shell\AutoRun\command - "" = E:\AutoRun.exe -- [2008/06/05 18:46:20 | 000,114,688 | R--- | M] (Huawei Technologies Co., Ltd.)
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = comfile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ========== [2011/12/05 11:03:03 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{6788903F-7CC2-4000-8223-8ADA5CFD7E9C}
[2011/12/04 17:14:51 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{EDEAD475-738A-4267-A1EC-1773B9C1FB86}
[2011/12/04 17:12:59 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{E0C502F1-EE33-476D-9C8C-5C1ACE4B2A5D}
[2011/12/01 19:42:19 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{3E08CFB2-7BC9-453F-A5CA-6A52F232854E}
[2011/12/01 19:40:43 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{5CD701C4-0FB1-430F-A15A-C6FBB55F875A}
[2011/11/30 13:14:52 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\HiJackThis
[2011/11/30 13:14:51 | 000,000,000 | ---D | C] -- C:\Program Files\Trend Micro
[2011/11/30 10:34:53 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{1DDF63A1-1EF5-470D-90C6-03EC45E35AA0}
[2011/11/30 10:33:57 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{78E41F8E-CE69-4E39-9610-0DB5E0B14D3D}
[2011/11/29 15:03:52 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Uniblue
[2011/11/29 14:34:19 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{AF0DBBA9-658F-4CFF-A0D7-DD10E3CAE8C3}
[2011/11/29 14:32:55 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{6088BE91-30BB-4341-BE67-B1B2E090DCE8}
[2011/11/28 23:41:02 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Roaming\Apple Computer
[2011/11/28 13:51:15 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\QuickTime
[2011/11/28 13:50:52 | 000,000,000 | ---D | C] -- C:\Program Files\QuickTime
[2011/11/28 13:50:52 | 000,000,000 | ---D | C] -- C:\ProgramData\Apple Computer
[2011/11/28 13:26:28 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{0B892C16-C66C-47DA-BF14-533557BD8714}
[2011/11/28 13:25:19 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{83C9CF99-46E5-4021-A0FB-4E55FB4A1923}
[2011/11/24 10:28:21 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{CEF7A4FF-A95D-4F96-9939-4FE7E149AD9A}
[2011/11/24 10:27:29 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{69C959B8-49AD-4D6F-9BBE-3BFDE1375FAB}
[2011/11/22 23:54:03 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{2CC2ED3C-4CFC-455B-9EFC-E7A97C6FF09E}
[2011/11/22 23:53:30 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{CF88DB1D-7C8D-4A40-9230-2D67A571CEB7}
[2011/11/21 23:58:47 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{20F7BDCA-2678-48C6-B90E-17453929ED58}
[2011/11/21 23:57:03 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{93198623-6675-44AA-9412-CC6AC2301725}
[2011/11/19 15:55:34 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{0C28AEBA-1872-4B3C-A51C-C0A9CB74AAE5}
[2011/11/19 15:53:45 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{26CC9B9B-0DA6-4E0A-BDD8-4A28B770684B}
[2011/11/17 18:22:53 | 000,000,000 | ---D | C] -- C:\ProgramData\MediaMonkey
[2011/11/17 18:22:49 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Roaming\MediaMonkey
[2011/11/17 17:03:28 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{F9D74E0B-E8FD-44C1-9E1E-B29B8CEDF021}
[2011/11/17 17:02:33 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{6D9B4B19-5465-4558-AD77-9790BB4E89F5}
[2011/11/16 23:12:30 | 000,214,408 | ---- | C] (Oracle Corporation) -- C:\Windows\System32\javaws.exe
[2011/11/16 23:12:30 | 000,173,960 | ---- | C] (Oracle Corporation) -- C:\Windows\System32\javaw.exe
[2011/11/16 23:12:30 | 000,173,960 | ---- | C] (Oracle Corporation) -- C:\Windows\System32\java.exe
[2011/11/16 16:26:40 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{157F280B-22B2-4AA4-B560-A261F42B69BF}
[2011/11/16 16:25:25 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{72EF2F4C-C281-4D44-8F16-BAB16B40CD0C}
[2011/11/15 22:38:37 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{A063C0EF-9EF3-4C44-9D2D-C4839C8F4CFA}
[2011/11/15 22:35:45 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{CC20992F-619B-433E-A7BD-C874265B1033}
[2011/11/12 14:32:40 | 000,000,000 | ---D | C] -- C:\Windows\Internet Logs
[2011/11/12 14:31:10 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Check Point
[2011/11/12 13:54:10 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{A396E6AC-095A-474B-8C56-2324A7DAAA08}
[2011/11/12 13:52:52 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{40FC9EAB-47D2-4AFD-B6F5-E341A2BF81B1}
[2011/11/11 10:46:31 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{94E2C276-2CAE-4A19-B272-4B845FFD3225}
[2011/11/11 10:45:09 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{EE7B0C96-1434-4548-87F5-D683746320A1}
[2011/11/09 23:59:21 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{C4AB8A0E-2AA5-4372-9C2C-9AE2469AEEAE}
[2011/11/09 23:58:30 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{40D7443E-647F-4FB7-A53D-A3693DC03675}
[2011/11/09 11:51:54 | 000,000,000 | ---D | C] -- C:\ProgramData\Badoo
[2011/11/09 11:35:10 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{70ACEF67-AC6F-4254-837F-87B430B6F3F4}
[2011/11/09 11:34:47 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{91CBBF75-C185-436E-85FB-2FEBBA1E91F5}
[2011/11/09 11:34:26 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{63921055-114B-4002-9B3A-68D852FC6989}
[2011/11/09 11:34:05 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{855330BD-A871-465D-BD35-9013BADE19FC}
[2011/11/08 23:38:36 | 002,341,888 | ---- | C] (Microsoft Corporation) -- C:\Windows\System32\win32k.sys
[2011/11/08 23:33:25 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{934BB09D-4C27-43DF-BFC1-DEDDAB1DC05E}
[2011/11/08 23:31:15 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{C3B513B6-65E8-4F76-9DFD-4813CF9CD154}
[2011/11/07 23:54:03 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{8217123A-2947-43AF-8991-BF20B8BC4BDC}
[2011/11/07 23:53:41 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{08B83FA5-E091-4AEE-8410-B1F1B6CB1D36}
[2011/11/07 23:48:34 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{3098081D-6D54-463C-BB57-C3624859B776}
[2011/11/07 21:28:38 | 000,056,208 | ---- | C] (Trusteer Ltd.) -- C:\Windows\System32\drivers\RapportKELL.sys
[2011/11/07 10:10:57 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{3D50451A-44A0-49F0-8BF1-92AEA5AE37A1}
[2011/11/07 10:09:38 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{F14B6545-90C5-443E-8C34-648BD4F7EEB3}
[2011/11/06 12:31:39 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{E3481DD7-ADFC-4CC8-84BA-A66778E14E45}
[2011/11/06 12:29:29 | 000,000,000 | ---D | C] -- C:\Users\Paul\AppData\Local\{9465D97A-4F2E-4FEC-87E3-9693C1DD669C}
[2011/10/13 11:31:48 | 000,004,096 | ---- | C] ( ) -- C:\Windows\System32\IGFXDEVLib.dll
[2011/05/23 23:40:17 | 000,172,032 | ---- | C] ( ) -- C:\Windows\System32\rsnp2uvc.dll
[2011/05/23 23:40:17 | 000,053,248 | ---- | C] ( ) -- C:\Windows\System32\csnp2uvc.dll
[1 C:\*.tmp files -> C:\*.tmp -> ]
========== Files - Modified Within 30 Days ========== [2011/12/05 11:08:14 | 000,014,832 | -H-- | M] () -- C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-5P-1.C7483456-A289-439d-8115-601632D005A0
[2011/12/05 11:08:14 | 000,014,832 | -H-- | M] () -- C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-5P-0.C7483456-A289-439d-8115-601632D005A0
[2011/12/05 11:05:07 | 000,312,170 | ---- | M] () -- C:\Windows\System32\perfh009.dat
[2011/12/05 11:05:07 | 000,041,806 | ---- | M] () -- C:\Windows\System32\perfc009.dat
[2011/12/05 11:02:27 | 000,000,878 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskMachineCore.job
[2011/12/05 11:02:23 | 000,000,322 | ---- | M] () -- C:\Windows\tasks\SpeedUpMyPC.job
[2011/12/05 11:00:57 | 000,065,536 | ---- | M] () -- C:\Windows\System32\Ikeext.etl
[2011/12/05 11:00:35 | 000,067,584 | --S- | M] () -- C:\Windows\bootstat.dat
[2011/12/05 11:00:28 | 2359,980,032 | -HS- | M] () -- C:\hiberfil.sys
[2011/12/04 19:32:03 | 000,000,904 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskUserS-1-5-21-1232758047-3035005367-2970806742-1000UA.job
[2011/12/04 18:57:00 | 000,000,882 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskMachineUA.job
[2011/12/04 18:18:43 | 000,001,417 | ---- | M] () -- C:\Users\Paul\Desktop\aswMBR.exe - Shortcut.lnk
[2011/12/04 18:14:13 | 000,001,437 | ---- | M] () -- C:\Users\Paul\Desktop\7mk9gcz2.exe - Shortcut.lnk
[2011/12/04 18:11:53 | 000,001,382 | ---- | M] () -- C:\Users\Paul\Desktop\OTL.exe - Shortcut.lnk
[2011/11/30 13:24:23 | 000,295,226 | ---- | M] () -- C:\Users\Paul\AppData\Local\census.cache
[2011/11/30 13:24:03 | 000,124,055 | ---- | M] () -- C:\Users\Paul\AppData\Local\ars.cache
[2011/11/30 13:14:52 | 000,002,959 | ---- | M] () -- C:\Users\Paul\Desktop\HiJackThis.lnk
[2011/11/29 15:03:53 | 000,002,016 | ---- | M] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\SpeedUpMyPC.lnk
[2011/11/29 15:03:53 | 000,001,968 | ---- | M] () -- C:\Users\Public\Desktop\SpeedUpMyPC.lnk
[2011/11/29 14:38:35 | 000,002,577 | ---- | M] () -- C:\Windows\System32\config.nt
[2011/11/28 18:01:25 | 000,041,184 | ---- | M] (AVAST Software) -- C:\Windows\avastSS.scr
[2011/11/28 18:01:23 | 000,199,816 | ---- | M] (AVAST Software) -- C:\Windows\System32\aswBoot.exe
[2011/11/28 17:53:53 | 000,435,032 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswSnx.sys
[2011/11/28 17:53:35 | 000,314,456 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswSP.sys
[2011/11/28 17:52:19 | 000,034,392 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswRdr.sys
[2011/11/28 17:52:16 | 000,052,952 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswTdi.sys
[2011/11/28 17:52:07 | 000,055,128 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswMonFlt.sys
[2011/11/28 17:51:50 | 000,020,568 | ---- | M] (AVAST Software) -- C:\Windows\System32\drivers\aswFsBlk.sys
[2011/11/28 16:44:36 | 000,000,852 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskUserS-1-5-21-1232758047-3035005367-2970806742-1000Core.job
[2011/11/28 13:51:15 | 000,001,815 | ---- | M] () -- C:\Users\Public\Desktop\QuickTime Player.lnk
[2011/11/24 11:39:45 | 000,002,060 | ---- | M] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\Mozilla Thunderbird.lnk
[2011/11/22 11:38:01 | 000,001,008 | ---- | M] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\Badoo.Desktop.lnk
[2011/11/22 11:38:01 | 000,000,984 | ---- | M] () -- C:\Users\Paul\Desktop\Badoo.Desktop.lnk
[2011/11/22 01:29:15 | 000,001,274 | ---- | M] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\Spybot - Search & Destroy.lnk
[2011/11/22 01:29:15 | 000,001,250 | ---- | M] () -- C:\Users\Paul\Desktop\Spybot - Search & Destroy.lnk
[2011/11/22 01:28:30 | 000,438,702 | R--- | M] () -- C:\Windows\System32\drivers\etc\hosts
[2011/11/22 00:34:37 | 000,002,395 | ---- | M] () -- C:\Users\Paul\Desktop\Google Chrome.lnk
[2011/11/17 18:23:22 | 000,001,005 | ---- | M] () -- C:\Users\Public\Desktop\MediaMonkey.lnk
[2011/11/17 17:01:38 | 000,015,170 | ---- | M] () -- C:\Windows\System32\results.xml
[2011/11/16 16:28:02 | 000,414,368 | ---- | M] (Adobe Systems Incorporated) -- C:\Windows\System32\FlashPlayerCPLApp.cpl
[2011/11/12 14:32:50 | 000,415,915 | ---- | M] () -- C:\Windows\System32\drivers\vsconfig.xml
[2011/11/12 14:31:10 | 000,000,981 | ---- | M] () -- C:\Users\Paul\Desktop\ZoneAlarm Security.lnk
[2011/11/10 03:00:00 | 000,000,380 | ---- | M] () -- C:\Windows\tasks\ErrorEND.job
[2011/11/09 11:35:37 | 000,002,002 | ---- | M] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\Mozilla Firefox.lnk
[2011/11/09 10:38:53 | 000,293,224 | ---- | M] () -- C:\Windows\System32\FNTCACHE.DAT
[2011/11/07 21:28:38 | 000,056,208 | ---- | M] (Trusteer Ltd.) -- C:\Windows\System32\drivers\RapportKELL.sys
[1 C:\*.tmp files -> C:\*.tmp -> ]
========== Files Created - No Company Name ========== [2011/12/04 18:18:43 | 000,001,417 | ---- | C] () -- C:\Users\Paul\Desktop\aswMBR.exe - Shortcut.lnk
[2011/12/04 18:14:13 | 000,001,437 | ---- | C] () -- C:\Users\Paul\Desktop\7mk9gcz2.exe - Shortcut.lnk
[2011/12/04 18:11:53 | 000,001,382 | ---- | C] () -- C:\Users\Paul\Desktop\OTL.exe - Shortcut.lnk
[2011/11/30 13:24:23 | 000,295,226 | ---- | C] () -- C:\Users\Paul\AppData\Local\census.cache
[2011/11/30 13:24:03 | 000,124,055 | ---- | C] () -- C:\Users\Paul\AppData\Local\ars.cache
[2011/11/30 13:14:52 | 000,002,959 | ---- | C] () -- C:\Users\Paul\Desktop\HiJackThis.lnk
[2011/11/29 15:03:58 | 000,000,322 | ---- | C] () -- C:\Windows\tasks\SpeedUpMyPC.job
[2011/11/29 15:03:53 | 000,002,016 | ---- | C] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\SpeedUpMyPC.lnk
[2011/11/29 15:03:53 | 000,001,968 | ---- | C] () -- C:\Users\Public\Desktop\SpeedUpMyPC.lnk
[2011/11/28 13:51:15 | 000,001,815 | ---- | C] () -- C:\Users\Public\Desktop\QuickTime Player.lnk
[2011/11/12 14:32:15 | 000,415,915 | ---- | C] () -- C:\Windows\System32\drivers\vsconfig.xml
[2011/11/12 14:31:10 | 000,000,981 | ---- | C] () -- C:\Users\Paul\Desktop\ZoneAlarm Security.lnk
[2011/11/09 11:51:55 | 000,001,008 | ---- | C] () -- C:\Users\Paul\Application Data\Microsoft\Internet Explorer\Quick Launch\Badoo.Desktop.lnk
[2011/11/09 11:51:55 | 000,000,984 | ---- | C] () -- C:\Users\Paul\Desktop\Badoo.Desktop.lnk
[2011/10/13 11:30:24 | 000,000,268 | ---- | C] () -- C:\Windows\System32\GfxUI.exe.config
[2011/10/07 17:16:47 | 000,000,848 | ---- | C] () -- C:\Windows\Rtcwplat.INI
[2011/05/27 18:48:24 | 001,766,784 | ---- | C] () -- C:\Windows\System32\drivers\snp2uvc.sys
[2011/05/27 18:48:24 | 000,030,080 | ---- | C] () -- C:\Windows\snuvcdsm.exe
[2011/05/27 18:48:23 | 000,034,048 | ---- | C] () -- C:\Windows\System32\drivers\sncduvc.sys
[2011/05/27 18:48:23 | 000,000,378 | ---- | C] () -- C:\Windows\PidList.ini
[2011/05/26 16:40:04 | 000,626,688 | ---- | C] () -- C:\Windows\Image.dll
[2011/05/26 16:40:04 | 000,200,704 | ---- | C] () -- C:\Windows\PLFSetI.exe
[2011/05/26 16:40:04 | 000,020,480 | ---- | C] () -- C:\Windows\USB_VIDEO_REG.exe
[2011/05/23 23:40:18 | 001,769,984 | ---- | C] () -- C:\Windows\System32\snp2uvc.sys
[2011/05/23 23:40:17 | 000,028,160 | ---- | C] () -- C:\Windows\System32\sncduvc.sys
[2011/05/23 23:40:17 | 000,000,169 | ---- | C] () -- C:\Windows\System32\PidList.ini
[2011/05/12 16:10:29 | 000,000,036 | ---- | C] () -- C:\ProgramData\InstallAlibre.config
[2011/03/23 02:09:53 | 000,000,000 | ---- | C] () -- C:\Windows\eDrawingOfficeAutomator.INI
[2011/01/19 16:00:36 | 000,009,216 | ---- | C] () -- C:\Users\Paul\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/12/29 17:39:51 | 000,000,056 | -H-- | C] () -- C:\ProgramData\ezsidmv.dat
[2010/12/29 16:06:57 | 000,000,017 | ---- | C] () -- C:\Users\Paul\AppData\Local\resmon.resmoncfg
[2010/11/11 18:26:00 | 000,000,059 | ---- | C] () -- C:\Windows\LTDLGFILE14N.INI
[2010/11/05 16:56:32 | 000,000,223 | ---- | C] () -- C:\Windows\System32\MachineSetup.bin
[2010/07/29 04:01:14 | 000,439,308 | ---- | C] () -- C:\Windows\System32\igcompkrng500.bin
[2010/07/29 04:01:12 | 000,092,356 | ---- | C] () -- C:\Windows\System32\igfcg500m.bin
[2010/07/29 04:01:10 | 000,982,240 | ---- | C] () -- C:\Windows\System32\igkrng500.bin
[2010/03/15 15:44:34 | 000,005,120 | ---- | C] () -- C:\Windows\System32\HdmiCoin.dll
[2009/07/14 04:57:37 | 000,067,584 | --S- | C] () -- C:\Windows\bootstat.dat
[2009/07/14 04:33:53 | 000,293,224 | ---- | C] () -- C:\Windows\System32\FNTCACHE.DAT
[2009/07/14 02:05:48 | 000,312,170 | ---- | C] () -- C:\Windows\System32\perfh009.dat
[2009/07/14 02:05:48 | 000,291,294 | ---- | C] () -- C:\Windows\System32\perfi009.dat
[2009/07/14 02:05:48 | 000,041,806 | ---- | C] () -- C:\Windows\System32\perfc009.dat
[2009/07/14 02:05:48 | 000,031,548 | ---- | C] () -- C:\Windows\System32\perfd009.dat
[2009/07/14 02:05:05 | 000,000,741 | ---- | C] () -- C:\Windows\System32\NOISE.DAT
[2009/07/14 02:04:11 | 000,215,943 | ---- | C] () -- C:\Windows\System32\dssec.dat
[2009/07/13 23:55:01 | 000,043,131 | ---- | C] () -- C:\Windows\mib.bin
[2009/07/13 23:51:43 | 000,073,728 | ---- | C] () -- C:\Windows\System32\BthpanContextHandler.dll
[2009/07/13 23:42:10 | 000,064,000 | ---- | C] () -- C:\Windows\System32\BWContextHandler.dll
[2009/07/13 22:09:19 | 000,139,824 | ---- | C] () -- C:\Windows\System32\igfcg500.bin
[2009/06/10 21:26:10 | 000,673,088 | ---- | C] () -- C:\Windows\System32\mlang.dat
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelTraditionalChinese.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelSwedish.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelSpanish.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelSimplifiedChinese.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelPortugese.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelKorean.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelJapanese.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelGerman.dll
[2008/04/28 10:11:16 | 000,053,248 | ---- | C] () -- C:\Windows\System32\AgCPanelFrench.dll
[2007/06/29 10:25:12 | 000,033,664 | ---- | C] () -- C:\Windows\System32\drivers\TsWlan.sys
========== Alternate Data Streams ========== @Alternate Data Stream - 16 bytes -> C:\Users\Paul\Music:Shareaza.GUID
@Alternate Data Stream - 16 bytes -> C:\Users\Paul\Downloads:Shareaza.GUID
< End of report >
GMER 1.0.15.15641 -
http://www.gmer.netRootkit scan 2011-12-05 11:37:31
Windows 6.1.7601 Service Pack 1 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-0 WDC_WD1600BEVT-22ZCT0 rev.11.01A11
Running: 7mk9gcz2.exe; Driver: C:\Users\Paul\AppData\Local\Temp\kxldapod.sys
---- System - GMER 1.0.15 ----
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwAddBootEntry [0x90678FC4]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwAllocateVirtualMemory [0x9441D510]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwAlpcConnectPort [0x940FE914]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwAlpcCreatePort [0x940FF1E2]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwAssignProcessToJobObject [0x941C7080]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwConnectPort [0x940FE36A]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEvent [0x9067B456]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEventPair [0x9067B4AE]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwCreateFile [0x941C7BDE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateIoCompletion [0x9067B5C4]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwCreateKey [0x941195F2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateMutant [0x9067B3AC]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwCreatePort [0x940FEE74]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSection [0x9067B4FE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSemaphore [0x9067B400]
SSDT \??\C:\ProgramData\Trusteer\Rapport\store\exts\RapportCerberus\baseline\RapportCerberus32_32301.sys ZwCreateThreadEx [0x906F77B0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateTimer [0x9067B572]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwCreateWaitablePort [0x940FEFD2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteBootEntry [0x90678FE8]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwDeleteFile [0x941C7DD6]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwDeleteKey [0x941CB5AC]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwDeleteValueKey [0x941CB5DE]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwFreeVirtualMemory [0x9441D5C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwLoadDriver [0x90678DB2]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwLoadKey [0x941CB740]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwLoadKey2 [0x9411BC54]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwLoadKeyEx [0x9411C106]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwModifyBootEntry [0x9067900C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeKey [0x9067B9BC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeMultipleKeys [0x90679AA4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEvent [0x9067B486]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEventPair [0x9067B4D6]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwOpenFile [0x941C7CF6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenIoCompletion [0x9067B5EE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenMutant [0x9067B3D8]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwOpenProcess [0x941C71F6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSection [0x9067B53E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSemaphore [0x9067B42E]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwOpenThread [0x941C73EA]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenTimer [0x9067B59C]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwProtectVirtualMemory [0x9441D658]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryObject [0x9067996A]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwQueryValueKey [0x941CB6B6]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwRenameKey [0x941CB620]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwReplaceKey [0x941CB652]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwRequestWaitReplyPort [0x940FDF0E]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwRestoreKey [0x941CB684]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootEntryOrder [0x90679030]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootOptions [0x90679054]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwSetContextThread [0x941C7026]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwSetInformationFile [0x941C7E7C]
SSDT \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD) ZwSetSecurityObject [0x9411D078]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemInformation [0x90678E0C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemPowerState [0x90678F48]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwSetValueKey [0x941CB544]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwShutdownSystem [0x90678F24]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwSuspendThread [0x941C6FC0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSystemDebugControl [0x90678F6C]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwTerminateProcess [0x941C6EE8]
SSDT \??\C:\Program Files\Trusteer\Rapport\bin\RapportPG.sys ZwTerminateThread [0x941C6F30]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwVdmControl [0x90679078]
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ObMakeTemporaryObject
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwSaveKey + 13D1 82C8D349 1 Byte [06]
.text ntkrnlpa.exe!KiDispatchInterrupt + 5A2 82CC6D52 19 Bytes [E0, 0F, BA, F0, 07, 73, 09, ...] {LOOPNZ 0x11; MOV EDX, 0x97307f0; MOV CR4, EAX; OR AL, 0x80; MOV CR4, EAX; RET ; MOV ECX, CR3}
.text ntkrnlpa.exe!KeRemoveQueueEx + 10CB 82CCDD80 4 Bytes [C4, 8F, 67, 90]
.text ntkrnlpa.exe!KeRemoveQueueEx + 10F3 82CCDDA8 4 Bytes [10, D5, 41, 94] {ADC CH, DL; INC ECX; XCHG ESP, EAX}
.text ntkrnlpa.exe!KeRemoveQueueEx + 10FF 82CCDDB4 8 Bytes [14, E9, 0F, 94, E2, F1, 0F, ...]
.text ntkrnlpa.exe!KeRemoveQueueEx + 1153 82CCDE08 4 Bytes [80, 70, 1C, 94] {XOR BYTE [EAX+0x1c], 0x94}
.text ntkrnlpa.exe!KeRemoveQueueEx + 1193 82CCDE48 4 Bytes [6A, E3, 0F, 94]
.text ...
PAGE ntkrnlpa.exe!ObMakeTemporaryObject 82E5ABE8 5 Bytes JMP 9442E69C \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ObInsertObject + 27 82E731B8 5 Bytes JMP 94430174 \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ZwReplyWaitReceivePortEx + 108 82E882FF 4 Bytes CALL 9067A025 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
PAGE ntkrnlpa.exe!ZwAlpcSendWaitReceivePort + 122 82EA20D1 4 Bytes CALL 9067A03B \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFntCacheLookUp + 8B2E 82430205 5 Bytes JMP 9067BF90 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateRectRgn + 3819 824442D2 5 Bytes JMP 9067C0D6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCTGetGammaTable + 4C63 824654E3 5 Bytes JMP 9067BB9A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngMapFontFileFD + 650 82486345 5 Bytes JMP 9067B9F2 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngMapFontFileFD + 38FE 824895F3 5 Bytes JMP 9067BABE \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngMapFontFileFD + 39BC 824896B1 5 Bytes JMP 9067BAD6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngIsSemaphoreOwnedByCurrentThread + 1EF5 8248DD37 5 Bytes JMP 9067BFBC \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngUnmapFontFileFD + 2AB5 82497708 5 Bytes JMP 9067BDE6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngUnmapFontFileFD + AC45 8249F898 5 Bytes JMP 9067BC0A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngDeleteClip + 480C 824F6C18 5 Bytes JMP 9067BB56 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngEqualRgn + 414D 82504A5B 5 Bytes JMP 9067BD4E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngDeleteRgn + 2198 82522A4F 5 Bytes JMP 9067BD14 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!PATHOBJ_vGetBounds + 3457 8255C100 5 Bytes JMP 9067BC6E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!PATHOBJ_vGetBounds + 968D 82562336 5 Bytes JMP 9067BCA4 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text peauth.sys B3F53C9D 28 Bytes CALL E60DE8FB
.text peauth.sys B3F53CC1 28 Bytes CALL E60DE91F
PAGE peauth.sys B3F59B9B 72 Bytes JMP B37D3E1F
.text kernel32.dll!OpenProcess 76C4549F 5 Bytes [E9, C8, 2F, 07, AA] {JMP 0xffffffffaa072fcd}
.text kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text user32.dll!FindWindowA 768C8FF3 5 Bytes [E9, 97, F2, 3E, AA] {JMP 0xffffffffaa3ef29c}
.text user32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes [E9, 0A, 5C, A7, 89] {JMP 0xffffffff89a75c0f}
.text user32.dll!FindWindowW 768CAE0D 5 Bytes [E9, 48, D4, 3E, AA] {JMP 0xffffffffaa3ed44d}
.text user32.dll!UnhookWinEvent 768CB750 5 Bytes [E9, A7, 4C, A7, 89] {JMP 0xffffffff89a74cac}
.text user32.dll!SetWindowsHookExW 768CE30C 5 Bytes [E9, F3, 24, A7, 89] {JMP 0xffffffff89a724f8}
.text user32.dll!SetWinEventHook 768D24DC 5 Bytes [E9, 17, DD, A6, 89] {JMP 0xffffffff89a6dd1c}
.text user32.dll!SetWindowsHookExA 768F6D0C 5 Bytes [E9, EF, 98, A4, 89] {JMP 0xffffffff89a498f4}
.text advapi32.dll!SetThreadToken 7679C7CE 5 Bytes [E9, 63, C8, 51, AA] {JMP 0xffffffffaa51c868}
.text advapi32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes [E9, EF, 5A, 4E, AA] {JMP 0xffffffffaa4e5af4}
---- User code sections - GMER 1.0.15 ----
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\System32\svchost.exe[148] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\System32\svchost.exe[148] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\System32\svchost.exe[148] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00180A08
.text C:\Windows\System32\svchost.exe[148] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001803FC
.text C:\Windows\System32\svchost.exe[148] USER32.dll!SetWindowsHookExW 768CE30C 3 Bytes JMP 00180804
.text C:\Windows\System32\svchost.exe[148] USER32.dll!SetWindowsHookExW + 4 768CE310 1 Byte [89]
.text C:\Windows\System32\svchost.exe[148] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001801F8
.text C:\Windows\System32\svchost.exe[148] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00180600
.text C:\Windows\System32\svchost.exe[148] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[148] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\System32\spoolsv.exe[344] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\System32\spoolsv.exe[344] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00150A08
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001503FC
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00150804
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001501F8
.text C:\Windows\System32\spoolsv.exe[344] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00150600
.text C:\Windows\System32\spoolsv.exe[344] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\spoolsv.exe[344] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[432] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[432] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[432] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00290A08
.text C:\Windows\system32\svchost.exe[432] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 002903FC
.text C:\Windows\system32\svchost.exe[432] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00290804
.text C:\Windows\system32\svchost.exe[432] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 002901F8
.text C:\Windows\system32\svchost.exe[432] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00290600
.text C:\Windows\system32\svchost.exe[432] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[432] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\csrss.exe[456] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000303FC
.text C:\Windows\system32\wininit.exe[500] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000301F8
.text C:\Windows\system32\wininit.exe[500] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\wininit.exe[500] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00050A08
.text C:\Windows\system32\wininit.exe[500] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000503FC
.text C:\Windows\system32\wininit.exe[500] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00050804
.text C:\Windows\system32\wininit.exe[500] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000501F8
.text C:\Windows\system32\wininit.exe[500] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00050600
.text C:\Windows\system32\wininit.exe[500] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\wininit.exe[500] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\csrss.exe[508] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00100A08
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001003FC
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00100804
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001001F8
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00100600
.text C:\Windows\system32\services.exe[548] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000A03FC
.text C:\Windows\system32\services.exe[548] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000A01F8
.text C:\Windows\system32\services.exe[548] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\services.exe[548] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\services.exe[548] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\lsass.exe[572] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\lsass.exe[572] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\lsass.exe[572] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsass.exe[572] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\lsm.exe[580] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\lsm.exe[580] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\lsm.exe[580] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\lsm.exe[580] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\winlogon.exe[608] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000303FC
.text C:\Windows\system32\winlogon.exe[608] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000301F8
.text C:\Windows\system32\winlogon.exe[608] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\winlogon.exe[608] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00050A08
.text C:\Windows\system32\winlogon.exe[608] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000503FC
.text C:\Windows\system32\winlogon.exe[608] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00050804
.text C:\Windows\system32\winlogon.exe[608] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000501F8
.text C:\Windows\system32\winlogon.exe[608] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00050600
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[740] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[740] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[740] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[740] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[828] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[828] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[828] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] user32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[828] user32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!KiUserApcDispatcher 772A6F58 5 Bytes JMP 00414D50 C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe (RapportMgmtService/Trusteer Ltd.)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00200A08
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 002003FC
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00200804
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 002001F8
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00200600
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] WS2_32.dll!getaddrinfo 76834296 5 Bytes JMP 71A40022
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] WS2_32.dll!gethostbyname 76847673 5 Bytes JMP 71AD0022
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe[876] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\ctfmon.exe[972] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\ctfmon.exe[972] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\System32\svchost.exe[1028] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\System32\svchost.exe[1028] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00520A08
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 005203FC
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00520804
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 005201F8
.text C:\Windows\System32\svchost.exe[1028] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00520600
.text C:\Windows\System32\svchost.exe[1028] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1028] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\System32\svchost.exe[1060] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\System32\svchost.exe[1060] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00490A08
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 004903FC
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00490804
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 004901F8
.text C:\Windows\System32\svchost.exe[1060] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00490600
.text C:\Windows\System32\svchost.exe[1060] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\System32\svchost.exe[1060] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[1088] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[1088] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00F00A08
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 00F003FC
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00F00804
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 00F001F8
.text C:\Windows\system32\svchost.exe[1088] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00F00600
.text C:\Windows\system32\svchost.exe[1088] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1088] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[1204] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[1204] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 006D0A08
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 006D03FC
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 006D0804
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 006D01F8
.text C:\Windows\system32\svchost.exe[1204] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 006D0600
.text C:\Windows\system32\svchost.exe[1204] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1204] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[1264] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[1264] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[1264] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1264] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[1348] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[1348] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 007A0A08
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 007A03FC
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 007A0804
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 007A01F8
.text C:\Windows\system32\svchost.exe[1348] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 007A0600
.text C:\Windows\system32\svchost.exe[1348] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[1348] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!KiUserApcDispatcher 772A6F58 5 Bytes JMP 00445210 C:\Program Files\Trusteer\Rapport\bin\RapportService.exe (RapportService/Trusteer Ltd.)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00290A08
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 002903FC
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00290804
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 002901F8
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00290600
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] WS2_32.dll!getaddrinfo 76834296 5 Bytes JMP 71A50022
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] WS2_32.dll!gethostbyname 76847673 5 Bytes JMP 71AE0022
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Trusteer\Rapport\bin\RapportService.exe[1500] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00100A08
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001003FC
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00100804
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001001F8
.text C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00100600
.text C:\Program Files\Alwil Software\Avast5\AvastSvc.exe[1640] kernel32.dll!SetUnhandledExceptionFilter 76C4F4FB 4 Bytes [C2, 04, 00, 90] {RET 0x4; NOP }
.text C:\Program Files\Alwil Software\Avast5\AvastSvc.exe[1640] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00340A08
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 003403FC
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00340804
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 003401F8
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00340600
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!GetUpdateRect + CF 768CA644 5 Bytes JMP 20CB9270 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001F0A08
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001F03FC
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001F0804
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001F01F8
.text C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001F0600
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001F0A08
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001F03FC
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001F0804
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001F01F8
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001F0600
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] advapi32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] advapi32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\WUDFHost.exe[2356] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\WUDFHost.exe[2356] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\WUDFHost.exe[2356] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00110A08
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001103FC
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00110804
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001101F8
.text C:\Windows\system32\WUDFHost.exe[2356] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00110600
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[2528] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[2528] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[2528] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001D0A08
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001D03FC
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001D0804
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001D01F8
.text C:\Windows\system32\svchost.exe[2528] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001D0600
.text C:\Windows\system32\taskeng.exe[2836] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\taskeng.exe[2836] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\taskeng.exe[2836] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\taskeng.exe[2836] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 000F0A08
.text C:\Windows\system32\taskeng.exe[2836] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000F03FC
.text C:\Windows\system32\taskeng.exe[2836] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 000F0804
.text C:\Windows\system32\taskeng.exe[2836] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000F01F8
.text C:\Windows\system32\taskeng.exe[2836] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 000F0600
.text C:\Windows\system32\Dwm.exe[2892] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\Dwm.exe[2892] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\Dwm.exe[2892] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\Dwm.exe[2892] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00080A08
.text C:\Windows\system32\Dwm.exe[2892] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000803FC
.text C:\Windows\system32\Dwm.exe[2892] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00080804
.text C:\Windows\system32\Dwm.exe[2892] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000801F8
.text C:\Windows\system32\Dwm.exe[2892] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00080600
.text C:\Windows\Explorer.EXE[2928] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\Explorer.EXE[2928] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\Explorer.EXE[2928] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\Explorer.EXE[2928] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00120A08
.text C:\Windows\Explorer.EXE[2928] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001203FC
.text C:\Windows\Explorer.EXE[2928] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00120804
.text C:\Windows\Explorer.EXE[2928] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001201F8
.text C:\Windows\Explorer.EXE[2928] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00120600
.text C:\Windows\system32\taskhost.exe[2956] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000503FC
.text C:\Windows\system32\taskhost.exe[2956] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000501F8
.text C:\Windows\system32\taskhost.exe[2956] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\taskhost.exe[2956] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 000E0A08
.text C:\Windows\system32\taskhost.exe[2956] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000E03FC
.text C:\Windows\system32\taskhost.exe[2956] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 000E0804
.text C:\Windows\system32\taskhost.exe[2956] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000E01F8
.text C:\Windows\system32\taskhost.exe[2956] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 000E0600
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001F0A08
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001F03FC
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001F0804
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001F01F8
.text C:\Program Files\Uniblue\SpeedUpMyPC\spmonitor.exe[3124] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001F0600
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\svchost.exe[3244] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\svchost.exe[3244] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\svchost.exe[3244] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\svchost.exe[3244] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Program Files\Alwil Software\Avast5\AvastUI.exe[3408] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000703FC
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000701F8
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001D0A08
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001D03FC
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001D0804
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001D01F8
.text C:\Program Files\Windows Live\Messenger\msnmsgr.exe[3440] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001D0600
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 001603FC
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 001601F8
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 001F0A08
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 001F03FC
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 001F0804
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 001F01F8
.text C:\ProgramData\Badoo\Badoo Desktop\1.6.48.1082\Badoo.Desktop.exe[3504] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 001F0600
.text C:\Windows\system32\AUDIODG.EXE[3808] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!NtAccessCheckByType 772A51D8 5 Bytes JMP 20CB8791 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!NtAlpcImpersonateClientOfPort 772A53B8 5 Bytes JMP 20CB8DD9 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!NtImpersonateClientOfPort 772A5AC8 5 Bytes JMP 20CB8D58 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!NtSetInformationProcess 772A6678 5 Bytes JMP 20CB89AB C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!LdrUnloadDll 772BC8DE 5 Bytes JMP 000603FC
.text C:\Windows\system32\SearchIndexer.exe[4036] ntdll.dll!LdrLoadDll 772C22B8 5 Bytes JMP 000601F8
.text C:\Windows\system32\SearchIndexer.exe[4036] kernel32.dll!OpenProcess 76C4549F 5 Bytes JMP 20CB846C C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] kernel32.dll!GetBinaryTypeW + 70 76C669F4 1 Byte [62]
.text C:\Windows\system32\SearchIndexer.exe[4036] ADVAPI32.dll!SetThreadToken 7679C7CE 5 Bytes JMP 20CB9036 C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] ADVAPI32.dll!ImpersonateNamedPipeClient 767D3369 5 Bytes JMP 20CB8E5D C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!FindWindowA 768C8FF3 5 Bytes JMP 20CB828F C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!UnhookWindowsHookEx 768CADF9 5 Bytes JMP 00090A08
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!FindWindowW 768CAE0D 5 Bytes JMP 20CB825A C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!UnhookWinEvent 768CB750 5 Bytes JMP 000903FC
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!SetWindowsHookExW 768CE30C 5 Bytes JMP 00090804
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!SetWinEventHook 768D24DC 5 Bytes JMP 000901F8
.text C:\Windows\system32\SearchIndexer.exe[4036] USER32.dll!SetWindowsHookExA 768F6D0C 5 Bytes JMP 00090600
---- Kernel IAT/EAT - GMER 1.0.15 ----
IAT \SystemRoot\system32\DRIVERS\ndiswan.sys[NDIS.SYS!NdisCloseAdapter] [94103E18] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\ndiswan.sys[NDIS.SYS!NdisOpenAdapter] [94103626] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\ndiswan.sys[NDIS.SYS!NdisDeregisterProtocol] [94101D84] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\ndiswan.sys[NDIS.SYS!NdisRegisterProtocol] [941037D0] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\raspppoe.sys[NDIS.SYS!NdisRegisterProtocol] [941037D0] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\raspppoe.sys[NDIS.SYS!NdisCloseAdapter] [94103E18] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\raspppoe.sys[NDIS.SYS!NdisOpenAdapter] [94103626] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\system32\DRIVERS\raspppoe.sys[NDIS.SYS!NdisDeregisterProtocol] [94101D84] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\System32\Drivers\NDProxy.SYS[NDIS.SYS!NdisRegisterProtocol] [941037D0] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\System32\Drivers\NDProxy.SYS[NDIS.SYS!NdisDeregisterProtocol] [94101D84] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\System32\Drivers\NDProxy.SYS[NDIS.SYS!NdisCloseAdapter] [94103E18] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
IAT \SystemRoot\System32\Drivers\NDProxy.SYS[NDIS.SYS!NdisOpenAdapter] [94103626] \SystemRoot\system32\DRIVERS\vsdatant.sys (ZoneAlarm Firewalling Driver/Check Point Software Technologies LTD)
---- User IAT/EAT - GMER 1.0.15 ----
IAT C:\Windows\System32\svchost.exe[148] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\System32\spoolsv.exe[344] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[432] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\wininit.exe[500] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe[540] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\services.exe[548] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\lsass.exe[572] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\lsm.exe[580] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[740] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[828] @ C:\Windows\system32\user32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\ctfmon.exe[972] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\System32\svchost.exe[1028] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\System32\svchost.exe[1060] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[1088] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[1204] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[1264] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[1348] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE[1508] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Users\Paul\Downloads\7mk9gcz2.exe[1700] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\CRYPT32.dll [KERNEL32.dll!RegisterWaitForSingleObject] [71B51F20] C:\Program Files\CheckPoint\ZoneAlarm\vsinit.dll (TrueVector Service/Check Point Software Technologies LTD)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\CRYPT32.dll [KERNEL32.dll!GetProcAddress] [71B520F0] C:\Program Files\CheckPoint\ZoneAlarm\vsinit.dll (TrueVector Service/Check Point Software Technologies LTD)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\WININET.dll [KERNEL32.dll!SetUnhandledExceptionFilter] [76CC5965] C:\Windows\system32\kernel32.dll (Windows NT BASE API Client DLL/Microsoft Corporation)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\WININET.dll [KERNEL32.dll!GetModuleHandleW] [76CC596F] C:\Windows\system32\kernel32.dll (Windows NT BASE API Client DLL/Microsoft Corporation)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\WININET.dll [KERNEL32.dll!CreateThread] [76CC5974] C:\Windows\system32\kernel32.dll (Windows NT BASE API Client DLL/Microsoft Corporation)
IAT C:\Program Files\CheckPoint\ZAForceField\IswSvc.exe[1704] @ C:\Windows\system32\WININET.dll [KERNEL32.dll!GetModuleHandleA] [76CC596A] C:\Windows\system32\kernel32.dll (Windows NT BASE API Client DLL/Microsoft Corporation)
IAT C:\Program Files\Spybot - Search & Destroy\SDWinSec.exe[2068] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\WUDFHost.exe[2356] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[2528] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\svchost.exe[3244] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
IAT C:\Windows\system32\SearchIndexer.exe[4036] @ C:\Windows\system32\USER32.dll [KERNEL32.dll!LoadLibraryExW] [20CB835C] C:\Program Files\CheckPoint\ZAForceField\Plugins\ISWSHEX.dll (ZoneAlarm Browser Security/Check Point Software Technologies)
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs aswSP.SYS (avast! self protection module/AVAST Software)
AttachedDevice \Driver\tdx \Device\Tcp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
Device \Driver\ACPI_HAL \Device\0000004c halmacpi.dll (Hardware Abstraction Layer DLL/Microsoft Corporation)
AttachedDevice \Driver\tdx \Device\Udp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
---- Registry - GMER 1.0.15 ----
Reg HKCU\Software\Microsoft\Windows Live\Companion\
[email protected]@513c89dca2946c1045c6e1d3c01069cd\r\n 0xA7 0x0D 0x74 0x5A ...
---- EOF - GMER 1.0.15 ----




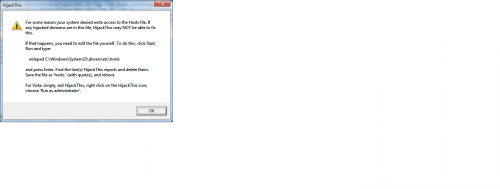











 Sign In
Sign In Create Account
Create Account

