False XP Home Security 2012 Alert [Solved]
#1
![False XP Home Security 2012 Alert [Solved]: post #1](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 19 December 2011 - 02:38 PM
Posted 19 December 2011 - 02:38 PM

#2
![False XP Home Security 2012 Alert [Solved]: post #2](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 December 2011 - 06:44 AM
Posted 20 December 2011 - 06:44 AM

Someone will be along to tell you what steps to take after you post the contents of the scan results.
#3
![False XP Home Security 2012 Alert [Solved]: post #3](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 December 2011 - 10:43 AM
Posted 20 December 2011 - 10:43 AM

OTL logfile created on: 12/20/2011 8:32:04 AM - Run 1
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Documents and Settings\Bob\Desktop
Windows XP Home Edition Service Pack 2 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 7.0.5730.13)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
503.30 Mb Total Physical Memory | 177.36 Mb Available Physical Memory | 35.24% Memory free
1.20 Gb Paging File | 0.88 Gb Available in Paging File | 73.55% Paging File free
Paging file location(s): C:\pagefile.sys 756 1512 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.04 Gb Total Space | 133.52 Gb Free Space | 89.59% Space Free | Partition Type: NTFS
Computer Name: BOB-3CDE5CE5327 | User Name: Bob | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - [2011/12/20 08:29:46 | 000,584,192 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Bob\Desktop\OTL.exe
PRC - [2011/11/28 10:01:24 | 003,744,552 | ---- | M] (AVAST Software) -- C:\Program Files\AVAST Software\Avast\AvastUI.exe
PRC - [2011/11/28 10:01:23 | 000,044,768 | ---- | M] (AVAST Software) -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe
PRC - [2011/11/14 10:07:03 | 000,924,632 | ---- | M] (Mozilla Corporation) -- C:\Program Files\Mozilla Firefox\firefox.exe
PRC - [2009/10/07 00:47:34 | 000,154,136 | ---- | M] (Logitech Inc.) -- C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe
PRC - [2008/10/16 19:35:28 | 000,116,032 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\ramaint.exe
PRC - [2008/10/16 19:35:24 | 000,087,360 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\LMIGuardian.exe
PRC - [2008/08/26 18:02:24 | 000,014,336 | ---- | M] (Agere Systems) -- C:\Program Files\LSI SoftModem\agrsmsvc.exe
PRC - [2008/07/24 17:46:10 | 000,063,040 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\LogMeIn.exe
PRC - [2007/06/13 02:23:07 | 001,033,216 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\explorer.exe
========== Modules (No Company Name) ==========
MOD - [2011/12/20 01:27:21 | 001,650,688 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11122000\algo.dll
MOD - [2011/12/19 15:49:56 | 000,241,528 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11122000\aswRep.dll
MOD - [2011/12/19 13:09:08 | 001,649,152 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11121901\algo.dll
MOD - [2011/12/19 11:03:58 | 000,241,528 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11121901\aswRep.dll
MOD - [2011/11/23 10:44:53 | 008,527,008 | ---- | M] () -- C:\WINDOWS\system32\Macromed\Flash\NPSWF32.dll
MOD - [2011/11/14 10:07:01 | 001,989,592 | ---- | M] () -- C:\Program Files\Mozilla Firefox\mozjs.dll
MOD - [2003/08/02 22:20:57 | 000,126,976 | R--- | M] () -- C:\Program Files\SpywareGuard\spywareguard.dll
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled | Stopped] -- -- (HidServ)
SRV - File not found [On_Demand | Stopped] -- -- (AppMgmt)
SRV - [2011/11/28 10:01:23 | 000,044,768 | ---- | M] (AVAST Software) [Auto | Running] -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe -- (avast! Antivirus)
SRV - [2009/10/07 00:47:34 | 000,154,136 | ---- | M] (Logitech Inc.) [Auto | Running] -- C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe -- (LVPrcSrv)
SRV - [2008/10/16 19:35:28 | 000,116,032 | ---- | M] (LogMeIn, Inc.) [Auto | Running] -- C:\Program Files\LogMeIn\x86\RaMaint.exe -- (LMIMaint)
SRV - [2008/08/26 18:02:24 | 000,014,336 | ---- | M] (Agere Systems) [Auto | Running] -- C:\Program Files\LSI SoftModem\agrsmsvc.exe -- (AgereModemAudio)
SRV - [2008/07/24 17:46:10 | 000,063,040 | ---- | M] (LogMeIn, Inc.) [Auto | Running] -- C:\Program Files\LogMeIn\x86\LogMeIn.exe -- (LogMeIn)
========== Driver Services (SafeList) ==========
DRV - [2011/11/28 09:53:53 | 000,435,032 | ---- | M] (AVAST Software) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\aswSnx.sys -- (aswSnx)
DRV - [2011/11/28 09:53:35 | 000,314,456 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswSP.sys -- (aswSP)
DRV - [2011/11/28 09:52:19 | 000,034,392 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswRdr.sys -- (aswRdr)
DRV - [2011/11/28 09:52:16 | 000,052,952 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswTdi.sys -- (aswTdi)
DRV - [2011/11/28 09:52:02 | 000,111,320 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\WINDOWS\System32\drivers\aswmon2.sys -- (aswMon2)
DRV - [2011/11/28 09:51:50 | 000,020,568 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\WINDOWS\System32\drivers\aswFsBlk.sys -- (aswFsBlk)
DRV - [2011/11/28 09:48:49 | 000,030,808 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aavmker4.sys -- (Aavmker4)
DRV - [2009/10/07 00:49:50 | 000,023,832 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\lvuvcflt.sys -- (FilterService)
DRV - [2009/10/07 00:49:38 | 006,756,632 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvuvc.sys -- (LVUVC) QuickCam Orbit/Sphere AF(UVC)
DRV - [2009/10/07 00:48:18 | 000,066,456 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvselsus.sys -- (lvselsus)
DRV - [2009/10/07 00:47:54 | 000,266,008 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvrs.sys -- (LVRS)
DRV - [2009/10/07 00:46:36 | 000,025,752 | ---- | M] () [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\LVPr2Mon.sys -- (LVPr2Mon)
DRV - [2008/10/29 19:43:44 | 001,204,128 | ---- | M] (Agere Systems) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2008/10/16 19:35:58 | 000,083,288 | ---- | M] (LogMeIn, Inc.) [File_System | Disabled | Stopped] -- C:\WINDOWS\System32\LMIRfsClientNP.dll -- (LMIRfsClientNP)
DRV - [2008/07/24 17:46:12 | 000,012,856 | ---- | M] (LogMeIn, Inc.) [Kernel | Auto | Running] -- C:\Program Files\LogMeIn\x86\rainfo.sys -- (LMIInfo)
DRV - [2008/07/24 17:46:10 | 000,047,640 | ---- | M] (LogMeIn, Inc.) [File_System | Auto | Running] -- C:\WINDOWS\system32\drivers\LMIRfsDriver.sys -- (LMIRfsDriver)
DRV - [2005/01/07 16:07:16 | 000,145,920 | ---- | M] (Windows ® Server 2003 DDK provider) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\Hdaudio.sys -- (HdAudAddService)
DRV - [2001/08/17 14:02:50 | 000,002,688 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\HIDSwvd.sys -- (HIDSwvd)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Local Page = %SystemRoot%\system32\blank.htm
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.msn.com/
IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ==========
FF - prefs.js..browser.search.update: false
FF - prefs.js..browser.startup.homepage: "http://www.google.com/"
FF - prefs.js..extensions.enabledItems: {3f963a5b-e555-4543-90e2-c3908898db71}:9.0.0.872
FF - prefs.js..extensions.enabledItems: [email protected]:1.0
FF - prefs.js..network.proxy.type: 0
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\WINDOWS\system32\Macromed\Flash\NPSWF32.dll ()
FF - HKLM\Software\MozillaPlugins\@Google.com/GoogleEarthPlugin: C:\Program Files\Google\Google Earth\plugin\npgeplugin.dll (Google)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\extensions\\[email protected]: C:\Program Files\AVAST Software\Avast\WebRep\FF [2011/11/30 09:16:48 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 8.0\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2011/11/14 10:07:04 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 8.0\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins [2011/09/26 12:22:49 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Components: C:\Program Files\Mozilla Thunderbird\components [2011/09/26 12:22:49 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Plugins: C:\Program Files\Mozilla Thunderbird\plugins
[2009/08/04 18:55:25 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Extensions
[2010/09/09 19:24:00 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Extensions\{3550f703-e582-4d05-9a08-453d09bdfdc6}
[2010/10/22 07:31:33 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Firefox\Profiles\mtjcp9cv.default\extensions
[2011/05/28 09:19:59 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2011/11/14 10:07:03 | 000,134,104 | ---- | M] (Mozilla Foundation) -- C:\Program Files\mozilla firefox\components\browsercomps.dll
[2011/06/11 08:50:29 | 000,001,919 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing-zugo.xml
[2010/01/01 00:00:00 | 000,002,252 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing.xml
[2011/11/14 10:07:03 | 000,002,040 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\twitter.xml
========== Chrome ==========
Hosts file not found
O2 - BHO: (no name) - {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} - No CLSID value found.
O2 - BHO: (SpywareGuardDLBLOCK.CBrowserHelper) - {4A368E80-174F-4872-96B5-0B27DDD11DB2} - C:\Program Files\SpywareGuard\dlprotect.dll ()
O2 - BHO: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software)
O3 - HKLM\..\Toolbar: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software)
O4 - HKLM..\Run: [avast] C:\Program Files\AVAST Software\Avast\avastUI.exe (AVAST Software)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} http://go.microsoft....k/?linkid=39204 (Windows Genuine Advantage Validation Tool)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_14)
O16 - DPF: {CAFEEFAC-0016-0000-0014-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_14)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_14)
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} http://platformdl.ad...Plus/1.6/gp.cab (Reg Error: Key error.)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.0.1
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{E49FD81C-7274-4F12-A922-7566DE088084}: DhcpNameServer = 192.168.0.1
O20 - HKLM Winlogon: Shell - (Explorer.exe) -C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\WINDOWS\system32\userinit.exe) -C:\WINDOWS\system32\userinit.exe (Microsoft Corporation)
O20 - Winlogon\Notify\LMIinit: DllName - (LMIinit.dll) - C:\WINDOWS\System32\LMIinit.dll (LogMeIn, Inc.)
O24 - Desktop WallPaper: C:\Documents and Settings\Bob\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O24 - Desktop BackupWallPaper: C:\Documents and Settings\Bob\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O28 - HKLM ShellExecuteHooks: {81559C35-8464-49F7-BB0E-07A383BEF910} - C:\Program Files\SpywareGuard\spywareguard.dll ()
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2009/07/28 11:37:18 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2011/12/20 08:29:38 | 000,584,192 | ---- | C] (OldTimer Tools) -- C:\Documents and Settings\Bob\Desktop\OTL.exe
[2011/12/19 20:06:43 | 000,000,000 | RH-D | C] -- C:\Documents and Settings\Bob\Recent
[2011/12/02 20:31:55 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Bob\Application Data\Apple Computer
[2011/11/29 08:55:59 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\SpywareBlaster
[2011/11/29 08:55:57 | 000,000,000 | ---D | C] -- C:\Program Files\SpywareBlaster
========== Files - Modified Within 30 Days ==========
[2011/12/20 08:29:46 | 000,584,192 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Bob\Desktop\OTL.exe
[2011/12/20 07:13:46 | 000,002,048 | --S- | M] () -- C:\WINDOWS\bootstat.dat
[2011/12/20 07:13:39 | 000,000,000 | ---- | M] () -- C:\WINDOWS\System32\drivers\lvuvc.hs
[2011/12/20 07:13:37 | 000,000,000 | ---- | M] () -- C:\WINDOWS\System32\drivers\logiflt.iad
[2011/12/18 16:17:50 | 000,013,646 | ---- | M] () -- C:\WINDOWS\System32\wpa.dbl
[2011/11/30 09:16:49 | 000,002,625 | ---- | M] () -- C:\WINDOWS\System32\CONFIG.NT
[2011/11/29 08:55:59 | 000,000,754 | ---- | M] () -- C:\Documents and Settings\Bob\Desktop\SpywareBlaster.lnk
[2011/11/28 10:17:52 | 000,020,992 | ---- | M] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2011/11/28 10:01:25 | 000,041,184 | ---- | M] (AVAST Software) -- C:\WINDOWS\avastSS.scr
[2011/11/28 10:01:23 | 000,199,816 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\aswBoot.exe
[2011/11/28 09:53:53 | 000,435,032 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswSnx.sys
[2011/11/28 09:53:35 | 000,314,456 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswSP.sys
[2011/11/28 09:52:19 | 000,034,392 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswRdr.sys
[2011/11/28 09:52:16 | 000,052,952 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswTdi.sys
[2011/11/28 09:52:02 | 000,111,320 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswmon2.sys
[2011/11/28 09:51:59 | 000,105,176 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswmon.sys
[2011/11/28 09:51:50 | 000,020,568 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswFsBlk.sys
[2011/11/28 09:48:49 | 000,030,808 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aavmker4.sys
[2011/11/22 19:01:16 | 000,000,270 | ---- | M] () -- C:\Documents and Settings\Bob\My Documents\Flight.lnk
[2011/11/22 13:19:38 | 000,021,840 | ---- | M] () -- C:\WINDOWS\System32\SIntfNT.dll
[2011/11/22 13:19:38 | 000,017,212 | ---- | M] () -- C:\WINDOWS\System32\SIntf32.dll
[2011/11/22 13:19:38 | 000,012,067 | ---- | M] () -- C:\WINDOWS\System32\SIntf16.dll
[2011/11/21 16:26:53 | 000,001,925 | ---- | M] () -- C:\Documents and Settings\Bob\Desktop\majorscale.gif
========== Files Created - No Company Name ==========
[2011/11/29 08:55:59 | 000,000,754 | ---- | C] () -- C:\Documents and Settings\Bob\Desktop\SpywareBlaster.lnk
[2011/11/22 19:01:16 | 000,000,270 | ---- | C] () -- C:\Documents and Settings\Bob\My Documents\Flight.lnk
[2011/11/21 16:26:49 | 000,001,925 | ---- | C] () -- C:\Documents and Settings\Bob\Desktop\majorscale.gif
[2011/06/04 08:20:23 | 000,000,664 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2011/05/28 03:36:47 | 000,000,122 | ---- | C] () -- C:\WINDOWS\wininit.ini
[2011/05/27 20:24:56 | 000,012,058 | -HS- | C] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\5bfpmqtq7mu88r0308hhv1b34gi712fxq1rdw0k76s
[2011/02/19 18:45:33 | 000,021,840 | ---- | C] () -- C:\WINDOWS\System32\SIntfNT.dll
[2011/02/19 18:45:33 | 000,017,212 | ---- | C] () -- C:\WINDOWS\System32\SIntf32.dll
[2011/02/19 18:45:33 | 000,012,067 | ---- | C] () -- C:\WINDOWS\System32\SIntf16.dll
[2011/02/19 18:37:59 | 000,034,115 | ---- | C] () -- C:\WINDOWS\DIIUnin.dat
[2010/10/09 12:48:19 | 000,020,992 | ---- | C] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/07/24 13:11:28 | 000,082,289 | ---- | C] () -- C:\WINDOWS\System32\lvcoinst.ini
[2009/10/07 00:46:36 | 000,025,752 | ---- | C] () -- C:\WINDOWS\System32\drivers\LVPr2Mon.sys
[2009/10/07 00:23:08 | 000,013,584 | ---- | C] () -- C:\WINDOWS\System32\drivers\iKeyLFT2.dll
[2009/08/24 11:02:00 | 000,000,376 | ---- | C] () -- C:\WINDOWS\ODBC.INI
[2009/08/04 18:55:15 | 000,000,000 | ---- | C] () -- C:\WINDOWS\nsreg.dat
[2009/07/28 16:55:54 | 000,204,800 | ---- | C] () -- C:\WINDOWS\System32\igfxCoIn_v4764.dll
[2009/07/28 11:39:33 | 000,002,048 | --S- | C] () -- C:\WINDOWS\bootstat.dat
[2009/07/28 11:34:46 | 000,021,640 | ---- | C] () -- C:\WINDOWS\System32\emptyregdb.dat
[2009/07/28 04:27:47 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2009/07/28 04:26:27 | 000,189,792 | ---- | C] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2005/03/22 10:48:43 | 013,107,200 | ---- | C] () -- C:\WINDOWS\System32\oembios.bin
[2005/03/22 10:48:43 | 000,004,627 | ---- | C] () -- C:\WINDOWS\System32\oembios.dat
[2004/08/04 02:00:00 | 000,673,088 | ---- | C] () -- C:\WINDOWS\System32\mlang.dat
[2004/08/04 02:00:00 | 000,314,838 | ---- | C] () -- C:\WINDOWS\System32\perfh009.dat
[2004/08/04 02:00:00 | 000,272,128 | ---- | C] () -- C:\WINDOWS\System32\perfi009.dat
[2004/08/04 02:00:00 | 000,218,003 | ---- | C] () -- C:\WINDOWS\System32\dssec.dat
[2004/08/04 02:00:00 | 000,046,258 | ---- | C] () -- C:\WINDOWS\System32\mib.bin
[2004/08/04 02:00:00 | 000,041,040 | ---- | C] () -- C:\WINDOWS\System32\perfc009.dat
[2004/08/04 02:00:00 | 000,028,626 | ---- | C] () -- C:\WINDOWS\System32\perfd009.dat
[2004/08/04 02:00:00 | 000,004,569 | ---- | C] () -- C:\WINDOWS\System32\secupd.dat
[2004/08/04 02:00:00 | 000,001,788 | ---- | C] () -- C:\WINDOWS\System32\Dcache.bin
[2004/08/04 02:00:00 | 000,000,741 | ---- | C] () -- C:\WINDOWS\System32\noise.dat
[2003/01/07 14:05:08 | 000,002,695 | ---- | C] () -- C:\WINDOWS\System32\OUTLPERF.INI
========== LOP Check ==========
[2011/06/15 19:01:00 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\AVAST Software
[2011/06/15 06:14:51 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\avg9
[2011/03/14 06:30:57 | 000,000,000 | -H-D | M] -- C:\Documents and Settings\All Users\Application Data\Common Files
[2009/07/29 11:45:55 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\LogMeIn
[2011/08/02 11:22:22 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\MFAData
[2011/12/19 12:59:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\TEMP
[2010/07/24 13:12:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\Leadertech
[2010/09/09 19:23:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\Thunderbird
[2010/02/02 21:36:54 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\W Photo Studio Viewer
========== Purity Check ==========
========== Alternate Data Streams ==========
@Alternate Data Stream - 104 bytes -> C:\Documents and Settings\All Users\Application Data\TEMP:5C321E34
< End of report >
#4
![False XP Home Security 2012 Alert [Solved]: post #4](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 06:48 AM
Posted 21 December 2011 - 06:48 AM

Hi and welcome to Geeks to Go.Please note that all instructions given are customised for this computer only, the tools used may cause damage if used on a computer with different infections.
If you think you have similar problems, please post the appropriate logs in the Malware Removal forum and wait for help.
I'm Dakeyras and I am going to try to assist you with your problem. Please take note of the below:
- I will start working on your Malware issues, this may or may not, solve other issues you have with your machine.
- The fixes are specific to your problem and should only be used for this issue on this machine!
- The process is not instant. Please continue to review my answers until I tell you your machine is clear. Absence of symptoms does not mean that everything is clear.
- If you don't know, stop and ask! Don't keep going on.
- Please reply to this thread. Do not start a new topic.
- Refrain from running self fixes as this will hinder the malware removal process.
- It may prove beneficial if you print of the following instructions or save them to notepad as I post them.
- Your security programs may give warnings for some of the tools I will ask you to use. Be assured, any links I give are safe.
Please be aware that removing Malware is a potentially hazardous undertaking. I will take care not to knowingly suggest courses of action that might damage your computer. However it is impossible for me to foresee all interactions that may happen between the software on your computer and those we'll use to clear you of infection, and I cannot guarantee the safety of your system. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system, or to necessitate you taking your computer to a repair shop.
Because of this, I advise you to backup any personal files and folders before you start.
Next:
You're welcome and thanks for the update...I see your machine only has XP Service Pack 2 installed, if I may bring to attention the below:-Thank you for your reply. My computer seems to be running ok but the red security center warning still sits in my tray next to my clock. It indicates problems with automatic updates and firewall monitoring. I won't touch those at this point. Here's the OTL log:
Source.Support for Windows XP with Service Pack 2 (SP2) ended on July 13, 2010. To continue support, make sure you've installed Windows XP Service Pack 3 (SP3).
As soon as I deem your machine is malware free we will install Service Pack 3 as this will increase both the overall security and stability of your machine. Do not attempt to install it yourself untill I advise so. As trying to install a Service Pack on a infected machine will result in all kinds of dire problems.
Next:
Could you post the OTL Extras Log please, it should be on the desktop. Also run the below scan and post that log as well, thank you.
Scan with GMER:
Please download GMER Rootkit Scanner from here.
- Double click the .exe file. If asked to allow gmer.sys driver to load, please consent
- If it gives you a warning about rootkit activity and asks if you want to run scan...click on NO
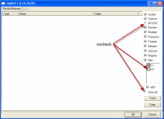
Click the image to enlarge it
- In the right panel, you will see several boxes that have been checked. Uncheck the following ...
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
- Then click the Scan button & wait for it to finish
- Once done click on the [Save..] button, and in the File name area, type in "Gmer.txt" or it will save as a .log file
- Save it where you can easily find it, such as your desktop, and post it in reply
Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Note: Do not run any programs while Gmer is running.
#5
![False XP Home Security 2012 Alert [Solved]: post #5](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 01:00 PM
Posted 21 December 2011 - 01:00 PM

OTL Extras logfile created on: 12/20/2011 8:32:04 AM - Run 1
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Documents and Settings\Bob\Desktop
Windows XP Home Edition Service Pack 2 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 7.0.5730.13)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
503.30 Mb Total Physical Memory | 177.36 Mb Available Physical Memory | 35.24% Memory free
1.20 Gb Paging File | 0.88 Gb Available in Paging File | 73.55% Paging File free
Paging file location(s): C:\pagefile.sys 756 1512 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.04 Gb Total Space | 133.52 Gb Free Space | 89.59% Space Free | Partition Type: NTFS
Computer Name: BOB-3CDE5CE5327 | User Name: Bob | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Extra Registry (SafeList) ==========
========== File Associations ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<extension>]
.cpl [@ = cplfile] -- rundll32.exe shell32.dll,Control_RunDLL "%1",%*
.html [@ = Reg Error: Key error.] -- Reg Error: Key error. File not found
.url [@ = InternetShortcut] -- rundll32.exe ieframe.dll,OpenURL %l
[HKEY_CURRENT_USER\SOFTWARE\Classes\<extension>]
.html [@ = FirefoxHTML] -- C:\Program Files\Mozilla Firefox\firefox.exe (Mozilla Corporation)
========== Shell Spawning ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<key>\shell\[command]\command]
batfile [open] -- "%1" %*
cmdfile [open] -- "%1" %*
comfile [open] -- "%1" %*
cplfile [cplopen] -- rundll32.exe shell32.dll,Control_RunDLL "%1",%*
exefile [open] -- "%1" %*
http [open] -- Reg Error: Key error.
https [open] -- Reg Error: Key error.
InternetShortcut [open] -- rundll32.exe ieframe.dll,OpenURL %l
piffile [open] -- "%1" %*
regfile [merge] -- Reg Error: Key error.
scrfile [config] -- "%1"
scrfile [install] -- rundll32.exe desk.cpl,InstallScreenSaver %l
scrfile [open] -- "%1" /S
txtfile [edit] -- Reg Error: Key error.
Unknown [openas] -- %SystemRoot%\system32\rundll32.exe %SystemRoot%\system32\shell32.dll,OpenAs_RunDLL %1
Directory [AddToPlaylistVLC] -- "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file --playlist-enqueue "%1" ()
Directory [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Directory [PlayWithVLC] -- "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file --no-playlist-enqueue "%1" ()
Folder [open] -- %SystemRoot%\Explorer.exe /idlist,%I,%L (Microsoft Corporation)
Folder [explore] -- %SystemRoot%\Explorer.exe /e,/idlist,%I,%L (Microsoft Corporation)
Drive [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
========== Security Center Settings ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"FirstRunDisabled" = 1
"AntiVirusDisableNotify" = 0
"FirewallDisableNotify" = 0
"UpdatesDisableNotify" = 0
"AntiVirusOverride" = 1
"FirewallOverride" = 1
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\AhnlabAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\ComputerAssociatesAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\KasperskyAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\McAfeeAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\McAfeeFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\PandaAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\PandaFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SophosAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SymantecAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SymantecFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TinyFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TrendAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TrendFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\ZoneLabsFirewall]
========== System Restore Settings ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore]
"DisableSR" = 0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sr]
"Start" = 0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SrService]
"Start" = 2
========== Firewall Settings ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall\StandardProfile]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile]
"EnableFirewall" = 0
"DoNotAllowExceptions" = 0
"DisableNotifications" = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile]
"EnableFirewall" = 0
"DoNotAllowExceptions" = 0
"DisableNotifications" = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\GloballyOpenPorts\List]
"53:UDP" = 53:UDP:*:Enabled:Promo
"23753:TCP" = 23753:TCP:*:Enabled:spport
"15276:TCP" = 15276:TCP:*:Enabled:spport
"6047:TCP" = 6047:TCP:*:Enabled:spport
"1900:UDP" = 1900:UDP:LocalSubNet:Disabled:@xpsp2res.dll,-22007
"2869:TCP" = 2869:TCP:LocalSubNet:Disabled:@xpsp2res.dll,-22008
========== Authorized Applications List ==========
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List]
"C:\Program Files\Google\Google Earth\plugin\geplugin.exe" = C:\Program Files\Google\Google Earth\plugin\geplugin.exe:*:Enabled:Google Earth -- (Google)
"C:\Program Files\Google\Google Earth\client\googleearth.exe" = C:\Program Files\Google\Google Earth\client\googleearth.exe:*:Enabled:Google Earth -- (Google)
"C:\Program Files\Logitech\Vid HD\Vid.exe" = C:\Program Files\Logitech\Vid HD\Vid.exe:*:Enabled:Logitech Vid HD -- (Logitech Inc.)
========== HKEY_LOCAL_MACHINE Uninstall List ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall]
"{172423F9-522A-483A-AD65-03600CE4CA4F}" = Microsoft Works 6-9 Converter
"{1F1C2DFC-2D24-3E06-BCB8-725134ADF989}" = Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148
"{26A24AE4-039D-4CA4-87B4-2F83216014FF}" = Java™ 6 Update 14
"{350C97B0-3D7C-4EE8-BAA9-00BCB3D54227}" = WebFldrs XP
"{4286E640-B5FB-11DF-AC4B-005056C00008}" = Google Earth
"{7F831576-6246-42C7-B523-55B3F96509CC}" = LogMeIn
"{837b34e3-7c30-493c-8f6a-2b0f04e2912c}" = Microsoft Visual C++ 2005 Redistributable
"{90260409-6000-11D3-8CFE-0150048383C9}" = Microsoft Office XP Web Components
"{91110409-6000-11D3-8CFE-0150048383C9}" = Microsoft Office Professional Edition 2003
"{AC76BA86-7AD7-1033-7B44-A93000000001}" = Adobe Reader 9.3.4
"{C27BC2A2-30DD-4014-B22E-63EB0DB572F9}" = Logitech Webcam Software
"{C9E14402-3631-4182-B377-6B0DFB1C0339}" = QuickTime
"Adobe Flash Player ActiveX" = Adobe Flash Player 10 ActiveX
"Adobe Flash Player Plugin" = Adobe Flash Player 11 Plugin
"avast" = avast! Free Antivirus
"CCleaner" = CCleaner
"Combat Flight Simulator 1.00" = Microsoft Combat Flight Simulator
"Diablo II" = Diablo II
"HDMI" = Intel® Graphics Media Accelerator Driver
"HijackThis" = HijackThis 2.0.2
"IDNMitigationAPIs" = Microsoft Internationalized Domain Names Mitigation APIs
"ie7" = Windows Internet Explorer 7
"Logitech Vid" = Logitech Vid HD
"lvdrivers_12.10" = Logitech Webcam Software Driver Package
"Malwarebytes' Anti-Malware_is1" = Malwarebytes' Anti-Malware version 1.51.2.1300
"Mozilla Firefox 8.0 (x86 en-US)" = Mozilla Firefox 8.0 (x86 en-US)
"Mozilla Thunderbird (8.0)" = Mozilla Thunderbird (8.0)
"MRU-Blaster_is1" = MRU-Blaster v1.5 (Database 3/28/2004)
"NLSDownlevelMapping" = Microsoft National Language Support Downlevel APIs
"PROSet" = Intel® PRO Network Connections Drivers
"SpywareBlaster_is1" = SpywareBlaster 4.5
"SpywareGuard_is1" = SpywareGuard v2.2
"VLC media player" = VLC media player 1.0.1
"WinRAR archiver" = WinRAR archiver
========== Last 10 Event Log Errors ==========
[ Application Events ]
Error - 6/19/2011 3:55:53 PM | Computer Name = BOB-3CDE5CE5327 | Source = ESENT | ID = 489
Description = wuauclt (3756) An attempt to open the file "C:\WINDOWS\SoftwareDistribution\DataStore\Logs\edb.log"
for read only access failed with system error 32 (0x00000020): "The process cannot
access the file because it is being used by another process. ". The open file
operation will fail with error -1032 (0xfffffbf8).
Error - 6/19/2011 3:55:53 PM | Computer Name = BOB-3CDE5CE5327 | Source = ESENT | ID = 455
Description = wuaueng.dll (3756) SUS20ClientDataStore: Error -1032 (0xfffffbf8)
occurred while opening logfile C:\WINDOWS\SoftwareDistribution\DataStore\Logs\edb.log.
Error - 6/19/2011 6:06:02 PM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: The connection with the server was terminated abnormally
Error - 6/19/2011 6:06:02 PM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 6/19/2011 10:09:07 PM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: The connection with the server was terminated abnormally
Error - 6/19/2011 10:09:08 PM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 6/20/2011 11:56:22 AM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: The connection with the server was terminated abnormally
Error - 6/20/2011 11:56:22 AM | Computer Name = BOB-3CDE5CE5327 | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 7/7/2011 12:06:08 PM | Computer Name = BOB-3CDE5CE5327 | Source = Application Hang | ID = 1002
Description = Hanging application firefox.exe, version 5.0.0.4183, hang module hungapp,
version 0.0.0.0, hang address 0x00000000.
Error - 7/7/2011 12:06:12 PM | Computer Name = BOB-3CDE5CE5327 | Source = Application Error | ID = 1000
Description = Faulting application plugin-container.exe, version 5.0.0.4183, faulting
module mozalloc.dll, version 5.0.0.4183, fault address 0x00001a39.
[ System Events ]
Error - 12/19/2011 7:57:53 PM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The LogMeIn Maintenance Service service terminated unexpectedly.
It has done this 1 time(s).
Error - 12/19/2011 7:57:53 PM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The LogMeIn service terminated unexpectedly. It has done this 1 time(s).
Error - 12/19/2011 7:57:53 PM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The Process Monitor service terminated unexpectedly. It has done
this 1 time(s).
Error - 12/19/2011 8:04:32 PM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7023
Description = The Computer Browser service terminated with the following error:
%%1460
Error - 12/20/2011 12:07:47 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The Agere Modem Call Progress Audio service terminated unexpectedly.
It has done this 1 time(s).
Error - 12/20/2011 12:07:47 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The Java Quick Starter service terminated unexpectedly. It has done
this 1 time(s).
Error - 12/20/2011 12:07:47 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The LogMeIn Maintenance Service service terminated unexpectedly.
It has done this 1 time(s).
Error - 12/20/2011 12:07:48 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The LogMeIn service terminated unexpectedly. It has done this 1 time(s).
Error - 12/20/2011 12:07:48 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7034
Description = The Process Monitor service terminated unexpectedly. It has done
this 1 time(s).
Error - 12/20/2011 11:19:13 AM | Computer Name = BOB-3CDE5CE5327 | Source = Service Control Manager | ID = 7023
Description = The Computer Browser service terminated with the following error:
%%1460
< End of report >
GMER 1.0.15.15641 - http://www.gmer.net
Rootkit scan 2011-12-21 10:53:19
Windows 5.1.2600 Service Pack 2 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP2T0L0-e ST3160815AS rev.4.AAB
Running: dolbge1o.exe; Driver: C:\DOCUME~1\Bob\LOCALS~1\Temp\kwqcifoc.sys
---- System - GMER 1.0.15 ----
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwAddBootEntry [0xA9198FC4]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwAllocateVirtualMemory [0xA91FD510]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwClose [0xA91BC6A9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEvent [0xA919B456]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEventPair [0xA919B4AE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateIoCompletion [0xA919B5C4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateKey [0xA91BC05D]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateMutant [0xA919B3AC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSection [0xA919B4FE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSemaphore [0xA919B400]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateTimer [0xA919B572]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteBootEntry [0xA9198FE8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteKey [0xA91BCD6F]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteValueKey [0xA91BD025]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDuplicateObject [0xA919B848]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateKey [0xA91BCBDA]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateValueKey [0xA91BCA45]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwFreeVirtualMemory [0xA91FD5C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwLoadDriver [0xA9198DB2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwModifyBootEntry [0xA919900C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeKey [0xA919B9BC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeMultipleKeys [0xA9199AA4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEvent [0xA919B486]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEventPair [0xA919B4D6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenIoCompletion [0xA919B5EE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenKey [0xA91BC3B9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenMutant [0xA919B3D8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenProcess [0xA919B680]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSection [0xA919B53E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSemaphore [0xA919B42E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenThread [0xA919B764]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenTimer [0xA919B59C]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwProtectVirtualMemory [0xA91FD658]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryKey [0xA91BC8C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryObject [0xA919996A]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryValueKey [0xA91BC712]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwRenameKey [0xA92059E6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwRestoreKey [0xA91BB6D0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootEntryOrder [0xA9199030]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootOptions [0xA9199054]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemInformation [0xA9198E0C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemPowerState [0xA9198F48]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetValueKey [0xA91BCE76]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwShutdownSystem [0xA9198F24]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSystemDebugControl [0xA9198F6C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwVdmControl [0xA9199078]
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwCreateProcessEx [0xA92117A2]
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ObInsertObject
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ObMakeTemporaryObject
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwCallbackReturn + 2460 80501C58 4 Bytes [E8, 8F, 19, A9]
PAGE ntkrnlpa.exe!ZwReplyWaitReceivePortEx + 5EC 8059B4F4 4 Bytes CALL A919A00F \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
PAGE ntkrnlpa.exe!ObMakeTemporaryObject 805B192A 5 Bytes JMP A920E69C \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ObInsertObject 805B8618 5 Bytes JMP A921015C \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ZwCreateProcessEx 805C6EFC 7 Bytes JMP A92117A6 \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
.text win32k.sys!EngPaint + 4EF BF8255ED 5 Bytes JMP A919BB9A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngUnmapFontFileFD + EE3F BF841181 5 Bytes JMP A919BC0A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!FONTOBJ_pxoGetXform + DE42 BF85AD4E 5 Bytes JMP A919BAD6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 3474 BF87111B 5 Bytes JMP A919BDE6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 34FF BF8711A6 4 Bytes JMP A919BFBC \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngGetCurrentCodePage + 411E BF894CB8 5 Bytes JMP A919BF76 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngStretchBltROP + 34B7 BF8BA260 5 Bytes JMP A919BABE \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngAlphaBlend + 3E8 BF8C333C 4 Bytes JMP A919BCA4 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1517 BF8EB97D 3 Bytes JMP A919BD14 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 151B BF8EB981 1 Byte [E9]
.text win32k.sys!EngFillPath + 1797 BF8EBBFD 5 Bytes JMP A919BD4E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!PATHOBJ_bCloseFigure + 19EF BF8F9A43 5 Bytes JMP A919B9F2 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 19C1 BF913245 5 Bytes JMP A919BB56 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 2595 BF913E19 5 Bytes JMP A919BC6E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 4EF4 BF916778 5 Bytes JMP A919C0D6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\system32\spoolsv.exe[312] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\spoolsv.exe[312] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[312] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\spoolsv.exe[312] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\spoolsv.exe[312] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\spoolsv.exe[312] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\spoolsv.exe[312] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\spoolsv.exe[312] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\spoolsv.exe[312] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\spoolsv.exe[312] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 003D1014
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 003D0804
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 003D0A08
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 003D0C0C
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 003D0E10
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003D01F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003D03FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 003D0600
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 003E0A08
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 003E0804
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 003E0600
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003E01F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[404] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003E03FC
.text C:\WINDOWS\system32\svchost.exe[520] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[520] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[520] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[520] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[520] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[520] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[520] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[520] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[520] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[520] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002C1014
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002C0804
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002C0A08
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002C0C0C
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 3 Bytes JMP 002C0E10
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!ChangeServiceConfig2W + 4 77E372D5 1 Byte [88]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002C01F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002C03FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002C0600
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002D0A08
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002D0804
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002D0600
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002D01F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[556] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002D03FC
.text C:\WINDOWS\System32\smss.exe[616] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[628] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\system32\csrss.exe[688] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\csrss.exe[688] KERNEL32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[712] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000701F8
.text C:\WINDOWS\system32\winlogon.exe[712] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[712] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000703FC
.text C:\WINDOWS\system32\winlogon.exe[712] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\winlogon.exe[712] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\winlogon.exe[712] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\winlogon.exe[712] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\winlogon.exe[712] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\winlogon.exe[712] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\winlogon.exe[712] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\services.exe[756] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\services.exe[756] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[756] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\services.exe[756] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\services.exe[756] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\services.exe[756] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\services.exe[756] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\services.exe[756] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\services.exe[756] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\services.exe[756] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\lsass.exe[768] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\lsass.exe[768] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[768] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\lsass.exe[768] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\lsass.exe[768] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\lsass.exe[768] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\lsass.exe[768] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\lsass.exe[768] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\lsass.exe[768] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\lsass.exe[768] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[832] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[928] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[992] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[992] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[992] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[992] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[992] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[992] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[992] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[992] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[992] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[992] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 003A0A08
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 003A0804
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 003A0600
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003A01F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003A03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 003B1014
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 003B0804
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 003B0A08
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 003B0C0C
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 003B0E10
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003B01F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003B03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[1040] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 003B0600
.text C:\WINDOWS\System32\svchost.exe[1088] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1088] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1088] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1088] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\System32\svchost.exe[1088] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\System32\svchost.exe[1088] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1088] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1088] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1088] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1088] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1112] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1112] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1112] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1112] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1148] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1172] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1232] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1232] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1232] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1232] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1232] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1232] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1232] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1232] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1232] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1232] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1304] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1304] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1304] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1304] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1304] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1304] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1304] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1304] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1304] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1304] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1572] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1572] kernel32.dll!SetUnhandledExceptionFilter 7C8447ED 4 Bytes [C2, 04, 00, 90] {RET 0x4; NOP }
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1572] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1676] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\Explorer.EXE[1676] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1676] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\Explorer.EXE[1676] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002B1014
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002B0804
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002B0A08
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002B0E10
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002B01F8
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002B03FC
.text C:\WINDOWS\Explorer.EXE[1676] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002B0600
.text C:\WINDOWS\Explorer.EXE[1676] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002C0A08
.text C:\WINDOWS\Explorer.EXE[1676] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002C0804
.text C:\WINDOWS\Explorer.EXE[1676] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[1676] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\Explorer.EXE[1676] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[1780] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[1780] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2564] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\wscntfy.exe[2564] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2564] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\wscntfy.exe[2564] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2564] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\wscntfy.exe[2564] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\wscntfy.exe[2564] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\wscntfy.exe[2564] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\wscntfy.exe[2564] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002D1014
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002D0804
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002D0A08
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002D0C0C
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002D0E10
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002D01F8
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002D03FC
.text C:\WINDOWS\system32\wscntfy.exe[2564] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002D0600
.text C:\WINDOWS\System32\svchost.exe[2716] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[2716] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[2716] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[2716] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\System32\svchost.exe[2716] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\System32\svchost.exe[2716] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[2716] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[2716] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[2716] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[2716] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs aswSP.SYS (avast! self protection module/AVAST Software)
AttachedDevice \FileSystem\Ntfs \Ntfs aswMon2.SYS (avast! File System Filter Driver for Windows XP/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Ip aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Tcp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Udp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\RawIp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \FileSystem\Fastfat \Fat fltMgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
AttachedDevice \FileSystem\Fastfat \Fat aswMon2.SYS (avast! File System Filter Driver for Windows XP/AVAST Software)
---- EOF - GMER 1.0.15 ----
#6
![False XP Home Security 2012 Alert [Solved]: post #6](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 07:06 PM
Posted 21 December 2011 - 07:06 PM

GMER 1.0.15.15641 - http://www.gmer.net
Rootkit scan 2011-12-21 17:02:55
Windows 5.1.2600 Service Pack 2 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP2T0L0-e ST3160815AS rev.4.AAB
Running: dolbge1o.exe; Driver: C:\DOCUME~1\Bob\LOCALS~1\Temp\kwqcifoc.sys
---- System - GMER 1.0.15 ----
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwAddBootEntry [0xA9808FC4]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwAllocateVirtualMemory [0xA986D510]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwClose [0xA982C6A9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEvent [0xA980B456]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEventPair [0xA980B4AE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateIoCompletion [0xA980B5C4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateKey [0xA982C05D]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateMutant [0xA980B3AC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSection [0xA980B4FE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSemaphore [0xA980B400]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateTimer [0xA980B572]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteBootEntry [0xA9808FE8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteKey [0xA982CD6F]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteValueKey [0xA982D025]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDuplicateObject [0xA980B848]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateKey [0xA982CBDA]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateValueKey [0xA982CA45]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwFreeVirtualMemory [0xA986D5C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwLoadDriver [0xA9808DB2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwModifyBootEntry [0xA980900C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeKey [0xA980B9BC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeMultipleKeys [0xA9809AA4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEvent [0xA980B486]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEventPair [0xA980B4D6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenIoCompletion [0xA980B5EE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenKey [0xA982C3B9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenMutant [0xA980B3D8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenProcess [0xA980B680]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSection [0xA980B53E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSemaphore [0xA980B42E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenThread [0xA980B764]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenTimer [0xA980B59C]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwProtectVirtualMemory [0xA986D658]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryKey [0xA982C8C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryObject [0xA980996A]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryValueKey [0xA982C712]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwRenameKey [0xA98759E6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwRestoreKey [0xA982B6D0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootEntryOrder [0xA9809030]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootOptions [0xA9809054]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemInformation [0xA9808E0C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemPowerState [0xA9808F48]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetValueKey [0xA982CE76]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwShutdownSystem [0xA9808F24]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSystemDebugControl [0xA9808F6C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwVdmControl [0xA9809078]
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwCreateProcessEx [0xA98817A2]
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ObInsertObject
Code \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ObMakeTemporaryObject
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwCallbackReturn + 2460 80501C58 4 Bytes [E8, 8F, 80, A9]
PAGE ntkrnlpa.exe!ZwReplyWaitReceivePortEx + 5EC 8059B4F4 4 Bytes CALL A980A00F \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
PAGE ntkrnlpa.exe!ObMakeTemporaryObject 805B192A 5 Bytes JMP A987E69C \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ObInsertObject 805B8618 5 Bytes JMP A988015C \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
PAGE ntkrnlpa.exe!ZwCreateProcessEx 805C6EFC 7 Bytes JMP A98817A6 \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software)
.text win32k.sys!EngPaint + 4EF BF8255ED 5 Bytes JMP A980BB9A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngUnmapFontFileFD + EE3F BF841181 5 Bytes JMP A980BC0A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!FONTOBJ_pxoGetXform + DE42 BF85AD4E 5 Bytes JMP A980BAD6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 3474 BF87111B 5 Bytes JMP A980BDE6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 34FF BF8711A6 4 Bytes JMP A980BFBC \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngGetCurrentCodePage + 411E BF894CB8 5 Bytes JMP A980BF76 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngStretchBltROP + 34B7 BF8BA260 5 Bytes JMP A980BABE \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngAlphaBlend + 3E8 BF8C333C 4 Bytes JMP A980BCA4 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1517 BF8EB97D 5 Bytes JMP A980BD14 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1797 BF8EBBFD 5 Bytes JMP A980BD4E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!PATHOBJ_bCloseFigure + 19EF BF8F9A43 5 Bytes JMP A980B9F2 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 19C1 BF913245 5 Bytes JMP A980BB56 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 2595 BF913E19 5 Bytes JMP A980BC6E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 4EF4 BF916778 5 Bytes JMP A980C0D6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\system32\spoolsv.exe[248] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\spoolsv.exe[248] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[248] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\spoolsv.exe[248] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\spoolsv.exe[248] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\spoolsv.exe[248] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\spoolsv.exe[248] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\spoolsv.exe[248] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\spoolsv.exe[248] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\spoolsv.exe[248] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[488] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[488] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[488] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[488] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[488] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[488] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[488] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[488] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[488] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[488] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002C1014
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002C0804
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002C0A08
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002C0C0C
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 3 Bytes JMP 002C0E10
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!ChangeServiceConfig2W + 4 77E372D5 1 Byte [88]
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002C01F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002C03FC
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002C0600
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002D0A08
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002D0804
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002D0600
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002D01F8
.text C:\Program Files\LSI SoftModem\agrsmsvc.exe[524] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002D03FC
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\Java\jre6\bin\jqs.exe[548] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\System32\smss.exe[616] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\LogMeIn\x86\RaMaint.exe[632] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\system32\csrss.exe[692] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\csrss.exe[692] KERNEL32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[716] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000701F8
.text C:\WINDOWS\system32\winlogon.exe[716] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[716] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000703FC
.text C:\WINDOWS\system32\winlogon.exe[716] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\winlogon.exe[716] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\winlogon.exe[716] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\winlogon.exe[716] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\winlogon.exe[716] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\winlogon.exe[716] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\winlogon.exe[716] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\services.exe[760] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\services.exe[760] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[760] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\services.exe[760] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\services.exe[760] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\services.exe[760] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\services.exe[760] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\services.exe[760] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\services.exe[760] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\services.exe[760] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\lsass.exe[772] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\lsass.exe[772] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[772] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\lsass.exe[772] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\lsass.exe[772] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\lsass.exe[772] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\lsass.exe[772] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\lsass.exe[772] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\lsass.exe[772] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\lsass.exe[772] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[928] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[928] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[928] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[928] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 003A0A08
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 003A0804
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 003A0600
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003A01F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003A03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 003B1014
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 003B0804
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 003B0A08
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 003B0C0C
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 003B0E10
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003B01F8
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003B03FC
.text C:\Program Files\LogMeIn\x86\LogMeIn.exe[948] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 003B0600
.text C:\WINDOWS\system32\svchost.exe[996] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[996] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[996] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[996] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[996] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[996] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[996] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[996] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[996] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[996] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1056] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1056] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1056] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\LogMeIn\x86\LMIGuardian.exe[1056] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 00381014
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 00380804
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 00380A08
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 00380C0C
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 00380E10
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003801F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003803FC
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 00380600
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 00390A08
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 00390804
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 00390600
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003901F8
.text C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe[1080] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003903FC
.text C:\WINDOWS\System32\svchost.exe[1092] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1092] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1092] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1092] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\System32\svchost.exe[1092] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\System32\svchost.exe[1092] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1092] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1092] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1092] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1092] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1172] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1172] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1172] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1172] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1216] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1216] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1216] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1216] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1216] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1216] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1216] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1216] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1216] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1216] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1296] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1296] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1296] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1296] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\system32\svchost.exe[1296] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\system32\svchost.exe[1296] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1296] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1296] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1296] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1296] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1548] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1548] kernel32.dll!SetUnhandledExceptionFilter 7C8447ED 4 Bytes [C2, 04, 00, 90] {RET 0x4; NOP }
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1548] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1684] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\Explorer.EXE[1684] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1684] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\Explorer.EXE[1684] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002B1014
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002B0804
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002B0A08
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002B0E10
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002B01F8
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002B03FC
.text C:\WINDOWS\Explorer.EXE[1684] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002B0600
.text C:\WINDOWS\Explorer.EXE[1684] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002C0A08
.text C:\WINDOWS\Explorer.EXE[1684] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002C0804
.text C:\WINDOWS\Explorer.EXE[1684] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[1684] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\Explorer.EXE[1684] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[1780] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[1780] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2612] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\wscntfy.exe[2612] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2612] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\wscntfy.exe[2612] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\system32\wscntfy.exe[2612] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\wscntfy.exe[2612] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\wscntfy.exe[2612] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\wscntfy.exe[2612] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\wscntfy.exe[2612] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002D1014
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002D0804
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002D0A08
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002D0C0C
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002D0E10
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002D01F8
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002D03FC
.text C:\WINDOWS\system32\wscntfy.exe[2612] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002D0600
.text C:\WINDOWS\System32\svchost.exe[2772] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[2772] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[2772] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[2772] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 002A1014
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 002A0804
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 002A0A08
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 002A0C0C
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 002A0E10
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 002A01F8
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 002A03FC
.text C:\WINDOWS\System32\svchost.exe[2772] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 002A0600
.text C:\WINDOWS\System32\svchost.exe[2772] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[2772] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[2772] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[2772] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[2772] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 002B03FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ntdll.dll!LdrLoadDll 7C915CD3 5 Bytes JMP 001501F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ntdll.dll!RtlDosSearchPath_U + 1D1 7C916ADA 1 Byte [62]
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ntdll.dll!LdrUnloadDll 7C916C9B 5 Bytes JMP 001503FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] kernel32.dll!GetBinaryTypeW + 80 7C867E3C 1 Byte [62]
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!SetServiceObjectSecurity 77E36EC9 5 Bytes JMP 003D1014
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!ChangeServiceConfigA 77E36FB1 5 Bytes JMP 003D0804
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!ChangeServiceConfigW 77E37149 5 Bytes JMP 003D0A08
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!ChangeServiceConfig2A 77E37249 5 Bytes JMP 003D0C0C
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!ChangeServiceConfig2W 77E372D1 5 Bytes JMP 003D0E10
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!CreateServiceA 77E37359 5 Bytes JMP 003D01F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!CreateServiceW 77E374F1 5 Bytes JMP 003D03FC
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] ADVAPI32.dll!DeleteService 77E375F9 5 Bytes JMP 003D0600
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] USER32.dll!UnhookWindowsHookEx 7E41F21E 5 Bytes JMP 003E0A08
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] USER32.dll!SetWindowsHookExW 7E42DDB5 5 Bytes JMP 003E0804
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] USER32.dll!SetWindowsHookExA 7E4311D1 5 Bytes JMP 003E0600
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] USER32.dll!SetWinEventHook 7E4317B7 5 Bytes JMP 003E01F8
.text C:\Documents and Settings\Bob\Desktop\dolbge1o.exe[3880] USER32.dll!UnhookWinEvent 7E43186C 5 Bytes JMP 003E03FC
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs aswSP.SYS (avast! self protection module/AVAST Software)
AttachedDevice \FileSystem\Ntfs \Ntfs aswMon2.SYS (avast! File System Filter Driver for Windows XP/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Ip aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Tcp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Udp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\RawIp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
---- EOF - GMER 1.0.15 ----
#7
![False XP Home Security 2012 Alert [Solved]: post #7](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 07:12 PM
Posted 21 December 2011 - 07:12 PM

You're welcome and not a problem with the Gmer scan and or the need to re-run it as you did again. Anyway lets proceed as follows shall we...Thank you. Gmer didn't leave any message that it had ended its scan, so I wonder if the scan was completed. I waited for a while and no activity was showing in its "dialogue box". Should I scan again to be sure? Or is it obvious to you if it completed or not? Attached will be 1st the " extras" and then 2nd, the Gmer log.
Now please go to Start >> Control Panel >> Add/Remove Programs and remove the following (if present):
Adobe Reader 9.3.4 <-- Out of date versions are/can exploited by malware, we will update this in due course.
HijackThis 2.0.2 <-- Out of date version, plus nigh on ineffective with detecting modern malware now.
Java™ 6 Update 14 <-- Out of date versions are/can exploited by malware, we will update this in due course.
Optional/advised uninstalltions, the below are not the best these days in my humble opinion and I can advise when I give the all clear more up-to date secure solutions if you so wish.
SpywareBlaster 4.5
SpywareGuard v2.2
To do so, click once on each of the above in turn to highlight and then click on the Remove button.
Download/Run ComboFix:
Please visit this webpage for download links, and instructions for running the tool:
http://www.bleepingc...to-use-combofix
* Ensure you have disabled all anti virus and anti malware programs so they do not interfere with the running of ComboFix.
Please include the C:\ComboFix.txt in your next reply for further review.How To Temporarily Disable Your Anti-virus, Firewall And Anti-malware Programs <-- Click on this link.
Note: If ComboFix detects Rootkit activity and asks to reboot the system, please allow this to be done.
If you receive an error "Illegal operation attempted on a registry key that has been marked for deletion." after ComboFix has run merely reboot your machine.
A word of warning: Neither I nor sUBs are responsible for any damage you may have caused your machine by running ComboFix on your own.
This tool is not a toy and not for everyday use. ComboFix Should Not be used unless requested by a forum helper
When completed the above, please post back the following in the order asked for:
- How is your computer performing now, any other symptoms and or problems encountered?
- ComboFix Log.
#8
![False XP Home Security 2012 Alert [Solved]: post #8](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 11:25 PM
Posted 21 December 2011 - 11:25 PM

Thank you for sticking with this. Computer runs well enough. I always wish it could be faster, but it runs normally. No new symptoms. The red Security Center warning is still in the tray. It warns of automatic updates being turned off (I used to have it set let me know when updates were available and I would do them manually). Also, the firewall is listed as "not monitored". This red security center icon appeared at the time of what I assumed was a false warning of the "XP Home Security Alert 2012". Maybe some of this is legit? Were there any issues? Also, I did uninstall: adobe reader, java, hijack this, spyware blaster and spywareguard. Here's the combofix log:
ComboFix 11-12-21.02 - Bob 12/21/2011 20:56:34.2.1 - x86
Microsoft Windows XP Home Edition 5.1.2600.2.1252.1.1033.18.503.262 [GMT -8:00]
Running from: c:\documents and settings\Bob\Desktop\ComboFix.exe
AV: avast! Antivirus *Disabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
AV: AVG Anti-Virus Free *Disabled/Outdated* {17DDD097-36FF-435F-9E1B-52D74245D6BF}
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\TEMP
c:\windows\system32\oobe\isperror
c:\windows\system32\oobe\isperror\ispcnerr.htm
c:\windows\system32\oobe\isperror\ispdtone.htm
c:\windows\system32\oobe\isperror\isphdshk.htm
c:\windows\system32\oobe\isperror\ispins.htm
c:\windows\system32\oobe\isperror\ispnoanw.htm
c:\windows\system32\oobe\isperror\isppberr.htm
c:\windows\system32\oobe\isperror\ispphbsy.htm
c:\windows\system32\oobe\isperror\ispsbusy.htm
.
.
((((((((((((((((((((((((( Files Created from 2011-11-22 to 2011-12-22 )))))))))))))))))))))))))))))))
.
.
2011-12-03 04:31 . 2011-12-03 04:48 -------- d-----w- c:\documents and settings\Bob\Application Data\Apple Computer
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2011-11-28 18:01 . 2011-06-16 03:01 41184 ----a-w- c:\windows\avastSS.scr
2011-11-28 18:01 . 2011-06-16 03:01 199816 ----a-w- c:\windows\system32\aswBoot.exe
2011-11-28 17:53 . 2011-06-16 03:01 435032 ----a-w- c:\windows\system32\drivers\aswSnx.sys
2011-11-28 17:53 . 2011-06-16 03:01 314456 ----a-w- c:\windows\system32\drivers\aswSP.sys
2011-11-28 17:52 . 2011-06-16 03:01 34392 ----a-w- c:\windows\system32\drivers\aswRdr.sys
2011-11-28 17:52 . 2011-06-16 03:01 52952 ----a-w- c:\windows\system32\drivers\aswTdi.sys
2011-11-28 17:52 . 2011-06-16 03:01 111320 ----a-w- c:\windows\system32\drivers\aswmon2.sys
2011-11-28 17:51 . 2011-06-16 03:01 105176 ----a-w- c:\windows\system32\drivers\aswmon.sys
2011-11-28 17:51 . 2011-06-16 03:01 20568 ----a-w- c:\windows\system32\drivers\aswFsBlk.sys
2011-11-28 17:48 . 2011-06-16 03:01 30808 ----a-w- c:\windows\system32\drivers\aavmker4.sys
2011-11-23 18:44 . 2011-05-17 02:42 414368 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2011-11-22 21:19 . 2011-02-20 02:45 21840 ----atw- c:\windows\system32\SIntfNT.dll
2011-11-22 21:19 . 2011-02-20 02:45 17212 ----atw- c:\windows\system32\SIntf32.dll
2011-11-22 21:19 . 2011-02-20 02:45 12067 ----atw- c:\windows\system32\SIntf16.dll
2011-11-14 18:07 . 2011-05-28 17:19 134104 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\00avast]
@="{472083B0-C522-11CF-8763-00608CC02F24}"
[HKEY_CLASSES_ROOT\CLSID\{472083B0-C522-11CF-8763-00608CC02F24}]
2011-11-28 18:01 122512 ----a-w- c:\program files\AVAST Software\Avast\ashShell.dll
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"avast"="c:\program files\AVAST Software\Avast\avastUI.exe" [2011-11-28 3744552]
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\LMIinit]
2008-10-17 03:35 87352 ----a-w- c:\windows\system32\LMIinit.dll
.
[HKLM\~\startupfolder\C:^Documents and Settings^Bob^Start Menu^Programs^Startup^Logitech . Product Registration.lnk]
path=c:\documents and settings\Bob\Start Menu\Programs\Startup\Logitech . Product Registration.lnk
backup=c:\windows\pss\Logitech . Product Registration.lnkStartup
.
[HKLM\~\startupfolder\C:^Documents and Settings^Bob^Start Menu^Programs^Startup^SpywareGuard.lnk]
path=c:\documents and settings\Bob\Start Menu\Programs\Startup\SpywareGuard.lnk
backup=c:\windows\pss\SpywareGuard.lnkStartup
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\ctfmon.exe]
2004-08-04 10:00 15360 ----a-w- c:\windows\system32\ctfmon.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2011-07-06 01:36 421888 ----a-w- c:\program files\QuickTime\QTTask.exe
.
[HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run-]
"MSMSGS"="c:\program files\Messenger\msmsgs.exe" /background
"ctfmon.exe"=c:\windows\system32\ctfmon.exe
"Messenger (Yahoo!)"="c:\progra~1\Yahoo!\Messenger\YahooMessenger.exe" -quiet
"Logitech Vid"="c:\program files\Logitech\Logitech Vid\vid.exe" -bootmode
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run-]
"High Definition Audio Property Page Shortcut"=HDAShCut.exe
"LogMeIn GUI"="c:\program files\LogMeIn\x86\LogMeInSystray.exe"
"IgfxTray"=c:\windows\system32\igfxtray.exe
"Persistence"=c:\windows\system32\igfxpers.exe
"HotKeysCmds"=c:\windows\system32\hkcmd.exe
"LogitechQuickCamRibbon"="c:\program files\Logitech\Logitech WebCam Software\LWS.exe" /hide
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
"FirewallOverride"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Google\\Google Earth\\plugin\\geplugin.exe"=
"c:\\Program Files\\Google\\Google Earth\\client\\googleearth.exe"=
"c:\\Program Files\\Logitech\\Vid HD\\Vid.exe"=
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"53:UDP"= 53:UDP:Promo
"23753:TCP"= 23753:TCP:spport
"15276:TCP"= 15276:TCP:spport
"6047:TCP"= 6047:TCP:spport
.
R1 aswSnx;aswSnx;c:\windows\system32\drivers\aswSnx.sys [6/15/2011 7:01 PM 435032]
R1 aswSP;aswSP;c:\windows\system32\drivers\aswSP.sys [6/15/2011 7:01 PM 314456]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [6/15/2011 7:01 PM 20568]
R2 LMIInfo;LogMeIn Kernel Information Provider;c:\program files\LogMeIn\x86\rainfo.sys [7/24/2008 5:46 PM 12856]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;\??\c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys --> c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys [?]
.
--- Other Services/Drivers In Memory ---
.
*Deregistered* - kwqcifoc
.
.
------- Supplementary Scan -------
.
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
TCP: DhcpNameServer = 192.168.0.1
FF - ProfilePath - c:\documents and settings\Bob\Application Data\Mozilla\Firefox\Profiles\mtjcp9cv.default\
FF - prefs.js: browser.startup.homepage - hxxp://www.google.com/
FF - prefs.js: network.proxy.type - 0
.
- - - - ORPHANS REMOVED - - - -
.
MSConfigStartUp-FlashPlayerUpdate - c:\windows\system32\Macromed\Flash\FlashUtil10q_Plugin.exe
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2011-12-21 21:02
Windows 5.1.2600 Service Pack 2 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'winlogon.exe'(716)
c:\windows\system32\LMIinit.dll
c:\windows\system32\LMIRfsClientNP.dll
.
Completion time: 2011-12-21 21:05:53
ComboFix-quarantined-files.txt 2011-12-22 05:05
.
Pre-Run: 143,513,944,064 bytes free
Post-Run: 143,503,953,920 bytes free
.
- - End Of File - - 86531FADBAAA17CACC09F111E87BA1AB
#9
![False XP Home Security 2012 Alert [Solved]: post #9](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 December 2011 - 11:46 PM
Posted 21 December 2011 - 11:46 PM

#10
![False XP Home Security 2012 Alert [Solved]: post #10](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 22 December 2011 - 04:38 PM
Posted 22 December 2011 - 04:38 PM

You're welcome and thanks for the update also.Thank you for sticking with this. Computer runs well enough. I always wish it could be faster, but it runs normally
Everything you have also mentioned I have taken into account and I will provide the appropriate advice in due course if required...
Custom ComboFix-Script:
A word of warning: Please do not run ComboFix on your own. This tool is not a toy and not for everyday use.
- Please open Notepad (Start -> Run -> type notepad in the Open field -> OK) and copy and paste the text present inside the code box below:
KillAll:: SecCenter:: AV: AVG Anti-Virus Free *Disabled/Outdated* {17DDD097-36FF-435F-9E1B-52D74245D6BF} Registry:: [-HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\ctfmon.exe] [-HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task] [HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List] "53:UDP"=- "23753:TCP"=- "15276:TCP"=- "6047:TCP"=- ReBoot:: - Save this as CFScript.txt and change the "Save as type" to "All Files" and place it on your desktop.

- Very Important! Temporarily disable your anti-virus, script blocking and any anti-malware real-time protection before following the steps below. They can interfere with ComboFix or remove some of its embedded files which may cause "unpredictable results".
- Referring to the screenshot above, drag CFScript.txt into ComboFix.exe.
- ComboFix will now run a scan on your system. It may reboot your system when it finishes. This is normal.
- When finished, it shall produce a log for you. Copy and paste the contents of the log in your next reply.
Malwarebytes Anti-Malware:
- Launch the application, Check for Updates >> Perform quick scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply.
When completed the above, please post back the following in the order asked for:
- How is your computer performing now, any further symptoms and or problems encountered?
- ComboFix Log.
- Malwarebytes Anti-Malware Log.
- A new OTL Log.
#11
![False XP Home Security 2012 Alert [Solved]: post #11](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 22 December 2011 - 06:53 PM
Posted 22 December 2011 - 06:53 PM

1) After I dragged your script onto ComboFix and it ran, I was asked if I wanted an update that was available. I clicked no...just because I was unsure. 2)Even though my avast! antivirus was turned off, it updated itself during the log preparation stage of ComboFix 3)MalwareBytes found no harmful threats 4)no red security center warning is in the tray (good!) and when opening the security center via control panel, I see that the firewall is still "unmonitored" (is this because I have a router?) and see that both automatic updates and virus protection are shown to be "on". (Is it good to keep updates on automatic?) 5)an IE icon has appeared on my desktop even though I use a different browser 6) THANKS
Finally, things are humming pretty smoothly with the computer. Nothing to notice really. About like it was before the weirdness. I'd be curious what malware, if any, was still on my computer when I opened this strand in the forum. Here are the logs in the order you asked:
ComboFix 11-12-21.02 - Bob 12/22/2011 15:56:12.3.1 - x86
Microsoft Windows XP Home Edition 5.1.2600.2.1252.1.1033.18.503.310 [GMT -8:00]
Running from: c:\documents and settings\Bob\Desktop\ComboFix.exe
Command switches used :: c:\documents and settings\Bob\Desktop\CFScript.txt
AV: avast! Antivirus *Disabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
.
.
((((((((((((((((((((((((( Files Created from 2011-11-23 to 2011-12-23 )))))))))))))))))))))))))))))))
.
.
2011-12-03 04:31 . 2011-12-03 04:48 -------- d-----w- c:\documents and settings\Bob\Application Data\Apple Computer
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2011-11-28 18:01 . 2011-06-16 03:01 41184 ----a-w- c:\windows\avastSS.scr
2011-11-28 18:01 . 2011-06-16 03:01 199816 ----a-w- c:\windows\system32\aswBoot.exe
2011-11-28 17:53 . 2011-06-16 03:01 435032 ----a-w- c:\windows\system32\drivers\aswSnx.sys
2011-11-28 17:53 . 2011-06-16 03:01 314456 ----a-w- c:\windows\system32\drivers\aswSP.sys
2011-11-28 17:52 . 2011-06-16 03:01 34392 ----a-w- c:\windows\system32\drivers\aswRdr.sys
2011-11-28 17:52 . 2011-06-16 03:01 52952 ----a-w- c:\windows\system32\drivers\aswTdi.sys
2011-11-28 17:52 . 2011-06-16 03:01 111320 ----a-w- c:\windows\system32\drivers\aswmon2.sys
2011-11-28 17:51 . 2011-06-16 03:01 105176 ----a-w- c:\windows\system32\drivers\aswmon.sys
2011-11-28 17:51 . 2011-06-16 03:01 20568 ----a-w- c:\windows\system32\drivers\aswFsBlk.sys
2011-11-28 17:48 . 2011-06-16 03:01 30808 ----a-w- c:\windows\system32\drivers\aavmker4.sys
2011-11-23 18:44 . 2011-05-17 02:42 414368 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2011-11-22 21:19 . 2011-02-20 02:45 21840 ----atw- c:\windows\system32\SIntfNT.dll
2011-11-22 21:19 . 2011-02-20 02:45 17212 ----atw- c:\windows\system32\SIntf32.dll
2011-11-22 21:19 . 2011-02-20 02:45 12067 ----atw- c:\windows\system32\SIntf16.dll
2011-11-14 18:07 . 2011-05-28 17:19 134104 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
.
.
((((((((((((((((((((((((((((( SnapShot@2011-12-22_05.03.01 )))))))))))))))))))))))))))))))))))))))))
.
+ 2011-12-23 00:03 . 2009-10-07 08:47 109080 c:\windows\temp\logishrd\LVPrcInj01.dll
+ 2011-12-23 00:04 . 2011-12-23 00:04 502217 c:\windows\temp\_asw_aisI.tm~a03776\sig.bin
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\00avast]
@="{472083B0-C522-11CF-8763-00608CC02F24}"
[HKEY_CLASSES_ROOT\CLSID\{472083B0-C522-11CF-8763-00608CC02F24}]
2011-11-28 18:01 122512 ----a-w- c:\program files\AVAST Software\Avast\ashShell.dll
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"avast"="c:\program files\AVAST Software\Avast\avastUI.exe" [2011-11-28 3744552]
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\LMIinit]
2008-10-17 03:35 87352 ----a-w- c:\windows\system32\LMIinit.dll
.
[HKLM\~\startupfolder\C:^Documents and Settings^Bob^Start Menu^Programs^Startup^Logitech . Product Registration.lnk]
path=c:\documents and settings\Bob\Start Menu\Programs\Startup\Logitech . Product Registration.lnk
backup=c:\windows\pss\Logitech . Product Registration.lnkStartup
.
[HKLM\~\startupfolder\C:^Documents and Settings^Bob^Start Menu^Programs^Startup^SpywareGuard.lnk]
path=c:\documents and settings\Bob\Start Menu\Programs\Startup\SpywareGuard.lnk
backup=c:\windows\pss\SpywareGuard.lnkStartup
.
[HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run-]
"MSMSGS"="c:\program files\Messenger\msmsgs.exe" /background
"ctfmon.exe"=c:\windows\system32\ctfmon.exe
"Messenger (Yahoo!)"="c:\progra~1\Yahoo!\Messenger\YahooMessenger.exe" -quiet
"Logitech Vid"="c:\program files\Logitech\Logitech Vid\vid.exe" -bootmode
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run-]
"High Definition Audio Property Page Shortcut"=HDAShCut.exe
"LogMeIn GUI"="c:\program files\LogMeIn\x86\LogMeInSystray.exe"
"IgfxTray"=c:\windows\system32\igfxtray.exe
"Persistence"=c:\windows\system32\igfxpers.exe
"HotKeysCmds"=c:\windows\system32\hkcmd.exe
"LogitechQuickCamRibbon"="c:\program files\Logitech\Logitech WebCam Software\LWS.exe" /hide
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
"FirewallOverride"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Google\\Google Earth\\plugin\\geplugin.exe"=
"c:\\Program Files\\Google\\Google Earth\\client\\googleearth.exe"=
"c:\\Program Files\\Logitech\\Vid HD\\Vid.exe"=
.
R1 aswSnx;aswSnx;c:\windows\system32\drivers\aswSnx.sys [6/15/2011 7:01 PM 435032]
R1 aswSP;aswSP;c:\windows\system32\drivers\aswSP.sys [6/15/2011 7:01 PM 314456]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [6/15/2011 7:01 PM 20568]
R2 LMIInfo;LogMeIn Kernel Information Provider;c:\program files\LogMeIn\x86\rainfo.sys [7/24/2008 5:46 PM 12856]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;\??\c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys --> c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys [?]
.
.
------- Supplementary Scan -------
.
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
TCP: DhcpNameServer = 192.168.0.1
FF - ProfilePath - c:\documents and settings\Bob\Application Data\Mozilla\Firefox\Profiles\mtjcp9cv.default\
FF - prefs.js: browser.startup.homepage - hxxp://www.google.com/
FF - prefs.js: network.proxy.type - 0
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2011-12-22 16:04
Windows 5.1.2600 Service Pack 2 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'winlogon.exe'(712)
c:\windows\system32\LMIinit.dll
c:\windows\system32\LMIRfsClientNP.dll
.
- - - - - - - > 'explorer.exe'(3424)
c:\windows\system32\WININET.dll
c:\windows\TEMP\logishrd\LVPrcInj01.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\LMIRfsClientNP.dll
.
------------------------ Other Running Processes ------------------------
.
c:\program files\AVAST Software\Avast\AvastSvc.exe
c:\program files\LSI SoftModem\agrsmsvc.exe
c:\program files\LogMeIn\x86\RaMaint.exe
c:\program files\LogMeIn\x86\LogMeIn.exe
c:\program files\LogMeIn\x86\LMIGuardian.exe
c:\program files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe
.
**************************************************************************
.
Completion time: 2011-12-22 16:07:53 - machine was rebooted
ComboFix-quarantined-files.txt 2011-12-23 00:07
ComboFix2.txt 2011-12-22 05:05
.
Pre-Run: 143,671,447,552 bytes free
Post-Run: 143,529,345,024 bytes free
.
- - End Of File - - BE4141F74ECE4A2B53886CBD7EC0E8C3
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122205
Windows 5.1.2600 Service Pack 2
Internet Explorer 7.0.5730.13
12/22/2011 4:13:33 PM
mbam-log-2011-12-22 (16-13-33).txt
Scan type: Quick scan
Objects scanned: 150254
Time elapsed: 3 minute(s), 1 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
OTL logfile created on: 12/22/2011 4:20:07 PM - Run 2
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Documents and Settings\Bob\Desktop\geeks to go
Windows XP Home Edition Service Pack 2 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 7.0.5730.13)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
503.30 Mb Total Physical Memory | 213.09 Mb Available Physical Memory | 42.34% Memory free
1.20 Gb Paging File | 0.99 Gb Available in Paging File | 82.38% Paging File free
Paging file location(s): C:\pagefile.sys 756 1512 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 149.04 Gb Total Space | 133.75 Gb Free Space | 89.74% Space Free | Partition Type: NTFS
Computer Name: BOB-3CDE5CE5327 | User Name: Bob | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - [2011/12/20 08:29:46 | 000,584,192 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Bob\Desktop\geeks to go\OTL.exe
PRC - [2011/11/28 10:01:24 | 003,744,552 | ---- | M] (AVAST Software) -- C:\Program Files\AVAST Software\Avast\AvastUI.exe
PRC - [2011/11/28 10:01:23 | 000,044,768 | ---- | M] (AVAST Software) -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe
PRC - [2009/10/07 00:47:34 | 000,154,136 | ---- | M] (Logitech Inc.) -- C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe
PRC - [2008/10/16 19:35:28 | 000,116,032 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\ramaint.exe
PRC - [2008/10/16 19:35:24 | 000,087,360 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\LMIGuardian.exe
PRC - [2008/08/26 18:02:24 | 000,014,336 | ---- | M] (Agere Systems) -- C:\Program Files\LSI SoftModem\agrsmsvc.exe
PRC - [2008/07/24 17:46:10 | 000,063,040 | ---- | M] (LogMeIn, Inc.) -- C:\Program Files\LogMeIn\x86\LogMeIn.exe
PRC - [2007/06/13 02:23:07 | 001,033,216 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\explorer.exe
========== Modules (No Company Name) ==========
MOD - [2011/12/22 14:41:57 | 001,656,320 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11122201\algo.dll
MOD - [2011/12/19 15:49:56 | 000,241,528 | ---- | M] () -- C:\Program Files\AVAST Software\Avast\defs\11122201\aswRep.dll
========== Win32 Services (SafeList) ==========
SRV - File not found [Disabled | Stopped] -- -- (HidServ)
SRV - File not found [On_Demand | Stopped] -- -- (AppMgmt)
SRV - [2011/11/28 10:01:23 | 000,044,768 | ---- | M] (AVAST Software) [Auto | Running] -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe -- (avast! Antivirus)
SRV - [2009/10/07 00:47:34 | 000,154,136 | ---- | M] (Logitech Inc.) [Auto | Running] -- C:\Program Files\Common Files\LogiShrd\LVMVFM\LVPrcSrv.exe -- (LVPrcSrv)
SRV - [2008/10/16 19:35:28 | 000,116,032 | ---- | M] (LogMeIn, Inc.) [Auto | Running] -- C:\Program Files\LogMeIn\x86\RaMaint.exe -- (LMIMaint)
SRV - [2008/08/26 18:02:24 | 000,014,336 | ---- | M] (Agere Systems) [Auto | Running] -- C:\Program Files\LSI SoftModem\agrsmsvc.exe -- (AgereModemAudio)
SRV - [2008/07/24 17:46:10 | 000,063,040 | ---- | M] (LogMeIn, Inc.) [Auto | Running] -- C:\Program Files\LogMeIn\x86\LogMeIn.exe -- (LogMeIn)
========== Driver Services (SafeList) ==========
DRV - [2011/11/28 09:53:53 | 000,435,032 | ---- | M] (AVAST Software) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\aswSnx.sys -- (aswSnx)
DRV - [2011/11/28 09:53:35 | 000,314,456 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswSP.sys -- (aswSP)
DRV - [2011/11/28 09:52:19 | 000,034,392 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswRdr.sys -- (aswRdr)
DRV - [2011/11/28 09:52:16 | 000,052,952 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aswTdi.sys -- (aswTdi)
DRV - [2011/11/28 09:52:02 | 000,111,320 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\WINDOWS\System32\drivers\aswmon2.sys -- (aswMon2)
DRV - [2011/11/28 09:51:50 | 000,020,568 | ---- | M] (AVAST Software) [File_System | Auto | Running] -- C:\WINDOWS\System32\drivers\aswFsBlk.sys -- (aswFsBlk)
DRV - [2011/11/28 09:48:49 | 000,030,808 | ---- | M] (AVAST Software) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\aavmker4.sys -- (Aavmker4)
DRV - [2009/10/07 00:49:50 | 000,023,832 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\lvuvcflt.sys -- (FilterService)
DRV - [2009/10/07 00:49:38 | 006,756,632 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvuvc.sys -- (LVUVC) QuickCam Orbit/Sphere AF(UVC)
DRV - [2009/10/07 00:48:18 | 000,066,456 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvselsus.sys -- (lvselsus)
DRV - [2009/10/07 00:47:54 | 000,266,008 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\lvrs.sys -- (LVRS)
DRV - [2009/10/07 00:46:36 | 000,025,752 | ---- | M] () [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\LVPr2Mon.sys -- (LVPr2Mon)
DRV - [2008/10/29 19:43:44 | 001,204,128 | ---- | M] (Agere Systems) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\AGRSM.sys -- (AgereSoftModem)
DRV - [2008/10/16 19:35:58 | 000,083,288 | ---- | M] (LogMeIn, Inc.) [File_System | Disabled | Stopped] -- C:\WINDOWS\System32\LMIRfsClientNP.dll -- (LMIRfsClientNP)
DRV - [2008/07/24 17:46:12 | 000,012,856 | ---- | M] (LogMeIn, Inc.) [Kernel | Auto | Running] -- C:\Program Files\LogMeIn\x86\rainfo.sys -- (LMIInfo)
DRV - [2008/07/24 17:46:10 | 000,047,640 | ---- | M] (LogMeIn, Inc.) [File_System | Auto | Running] -- C:\WINDOWS\system32\drivers\LMIRfsDriver.sys -- (LMIRfsDriver)
DRV - [2005/01/07 16:07:16 | 000,145,920 | ---- | M] (Windows ® Server 2003 DDK provider) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\Hdaudio.sys -- (HdAudAddService)
DRV - [2001/08/17 14:02:50 | 000,002,688 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\HIDSwvd.sys -- (HIDSwvd)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Local Page = %SystemRoot%\system32\blank.htm
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.msn.com/
IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ==========
FF - prefs.js..browser.search.update: false
FF - prefs.js..browser.startup.homepage: "http://www.google.com/"
FF - prefs.js..extensions.enabledItems: {3f963a5b-e555-4543-90e2-c3908898db71}:9.0.0.872
FF - prefs.js..extensions.enabledItems: [email protected]:1.0
FF - prefs.js..network.proxy.type: 0
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\WINDOWS\system32\Macromed\Flash\NPSWF32.dll ()
FF - HKLM\Software\MozillaPlugins\@Google.com/GoogleEarthPlugin: C:\Program Files\Google\Google Earth\plugin\npgeplugin.dll (Google)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\extensions\\[email protected]: C:\Program Files\AVAST Software\Avast\WebRep\FF [2011/11/30 09:16:48 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 8.0\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2011/11/14 10:07:04 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 8.0\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins [2011/12/21 20:46:34 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Components: C:\Program Files\Mozilla Thunderbird\components [2011/09/26 12:22:49 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Thunderbird 8.0\extensions\\Plugins: C:\Program Files\Mozilla Thunderbird\plugins
[2009/08/04 18:55:25 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Extensions
[2010/09/09 19:24:00 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Extensions\{3550f703-e582-4d05-9a08-453d09bdfdc6}
[2010/10/22 07:31:33 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\Bob\Application Data\Mozilla\Firefox\Profiles\mtjcp9cv.default\extensions
[2011/05/28 09:19:59 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2011/11/14 10:07:03 | 000,134,104 | ---- | M] (Mozilla Foundation) -- C:\Program Files\mozilla firefox\components\browsercomps.dll
[2011/06/11 08:50:29 | 000,001,919 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing-zugo.xml
[2010/01/01 00:00:00 | 000,002,252 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing.xml
[2011/11/14 10:07:03 | 000,002,040 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\twitter.xml
========== Chrome ==========
O1 HOSTS File: ([2011/12/22 16:03:37 | 000,000,027 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (no name) - {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} - No CLSID value found.
O2 - BHO: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software)
O2 - BHO: (Java™ Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll File not found
O3 - HKLM\..\Toolbar: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software)
O4 - HKLM..\Run: [avast] C:\Program Files\AVAST Software\Avast\avastUI.exe (AVAST Software)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} http://go.microsoft....k/?linkid=39204 (Windows Genuine Advantage Validation Tool)
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} http://platformdl.ad...Plus/1.6/gp.cab (Reg Error: Key error.)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.0.1
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{E49FD81C-7274-4F12-A922-7566DE088084}: DhcpNameServer = 192.168.0.1
O20 - HKLM Winlogon: Shell - (Explorer.exe) -C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\WINDOWS\system32\userinit.exe) -C:\WINDOWS\system32\userinit.exe (Microsoft Corporation)
O20 - Winlogon\Notify\LMIinit: DllName - (LMIinit.dll) - C:\WINDOWS\System32\LMIinit.dll (LogMeIn, Inc.)
O24 - Desktop WallPaper: C:\Documents and Settings\Bob\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O24 - Desktop BackupWallPaper: C:\Documents and Settings\Bob\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2009/07/28 11:37:18 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2011/12/22 16:02:03 | 000,000,000 | ---D | C] -- C:\WINDOWS\temp
[2011/12/21 21:37:10 | 000,000,000 | RH-D | C] -- C:\Documents and Settings\Bob\Recent
[2011/12/21 21:33:05 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Bob\Desktop\geeks to go
[2011/12/21 20:54:47 | 000,518,144 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWREG.exe
[2011/12/21 20:54:47 | 000,406,528 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWSC.exe
[2011/12/21 20:54:47 | 000,212,480 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWXCACLS.exe
[2011/12/21 20:54:47 | 000,060,416 | ---- | C] (NirSoft) -- C:\WINDOWS\NIRCMD.exe
[2011/12/21 20:54:31 | 000,000,000 | ---D | C] -- C:\Qoobox
[2011/12/21 20:51:03 | 004,347,226 | R--- | C] (Swearware) -- C:\Documents and Settings\Bob\Desktop\ComboFix.exe
[2011/12/21 20:46:27 | 000,000,000 | ---D | C] -- C:\Config.Msi
[2011/12/02 20:31:55 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Bob\Application Data\Apple Computer
========== Files - Modified Within 30 Days ==========
[2011/12/22 16:15:22 | 000,002,048 | --S- | M] () -- C:\WINDOWS\bootstat.dat
[2011/12/22 16:15:20 | 000,000,000 | ---- | M] () -- C:\WINDOWS\System32\drivers\lvuvc.hs
[2011/12/22 16:15:18 | 000,000,000 | ---- | M] () -- C:\WINDOWS\System32\drivers\logiflt.iad
[2011/12/22 16:03:37 | 000,000,027 | ---- | M] () -- C:\WINDOWS\System32\drivers\etc\hosts
[2011/12/22 15:33:51 | 000,002,497 | ---- | M] () -- C:\Documents and Settings\Bob\Desktop\Word.lnk
[2011/12/21 20:51:09 | 004,347,226 | R--- | M] (Swearware) -- C:\Documents and Settings\Bob\Desktop\ComboFix.exe
[2011/12/21 09:15:09 | 000,013,646 | ---- | M] () -- C:\WINDOWS\System32\wpa.dbl
[2011/11/30 09:16:49 | 000,002,625 | ---- | M] () -- C:\WINDOWS\System32\CONFIG.NT
[2011/11/28 10:17:52 | 000,020,992 | ---- | M] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2011/11/28 10:01:25 | 000,041,184 | ---- | M] (AVAST Software) -- C:\WINDOWS\avastSS.scr
[2011/11/28 10:01:23 | 000,199,816 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\aswBoot.exe
[2011/11/28 09:53:53 | 000,435,032 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswSnx.sys
[2011/11/28 09:53:35 | 000,314,456 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswSP.sys
[2011/11/28 09:52:19 | 000,034,392 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswRdr.sys
[2011/11/28 09:52:16 | 000,052,952 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswTdi.sys
[2011/11/28 09:52:02 | 000,111,320 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswmon2.sys
[2011/11/28 09:51:59 | 000,105,176 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswmon.sys
[2011/11/28 09:51:50 | 000,020,568 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aswFsBlk.sys
[2011/11/28 09:48:49 | 000,030,808 | ---- | M] (AVAST Software) -- C:\WINDOWS\System32\drivers\aavmker4.sys
[2011/11/22 19:01:16 | 000,000,270 | ---- | M] () -- C:\Documents and Settings\Bob\My Documents\Flight.lnk
========== Files Created - No Company Name ==========
[2011/12/21 20:54:47 | 000,256,000 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2011/12/21 20:54:47 | 000,208,896 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2011/12/21 20:54:47 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2011/12/21 20:54:47 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2011/12/21 20:54:47 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2011/11/22 19:01:16 | 000,000,270 | ---- | C] () -- C:\Documents and Settings\Bob\My Documents\Flight.lnk
[2011/06/04 08:20:23 | 000,000,664 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2011/05/28 03:36:47 | 000,000,122 | ---- | C] () -- C:\WINDOWS\wininit.ini
[2011/05/27 20:24:56 | 000,012,058 | -HS- | C] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\5bfpmqtq7mu88r0308hhv1b34gi712fxq1rdw0k76s
[2011/02/19 18:45:33 | 000,021,840 | ---- | C] () -- C:\WINDOWS\System32\SIntfNT.dll
[2011/02/19 18:45:33 | 000,017,212 | ---- | C] () -- C:\WINDOWS\System32\SIntf32.dll
[2011/02/19 18:45:33 | 000,012,067 | ---- | C] () -- C:\WINDOWS\System32\SIntf16.dll
[2011/02/19 18:37:59 | 000,034,115 | ---- | C] () -- C:\WINDOWS\DIIUnin.dat
[2010/10/09 12:48:19 | 000,020,992 | ---- | C] () -- C:\Documents and Settings\Bob\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/07/24 13:11:28 | 000,082,289 | ---- | C] () -- C:\WINDOWS\System32\lvcoinst.ini
[2009/10/07 00:46:36 | 000,025,752 | ---- | C] () -- C:\WINDOWS\System32\drivers\LVPr2Mon.sys
[2009/10/07 00:23:08 | 000,013,584 | ---- | C] () -- C:\WINDOWS\System32\drivers\iKeyLFT2.dll
[2009/08/24 11:02:00 | 000,000,376 | ---- | C] () -- C:\WINDOWS\ODBC.INI
[2009/08/04 18:55:15 | 000,000,000 | ---- | C] () -- C:\WINDOWS\nsreg.dat
[2009/07/28 16:55:54 | 000,204,800 | ---- | C] () -- C:\WINDOWS\System32\igfxCoIn_v4764.dll
[2009/07/28 11:39:33 | 000,002,048 | --S- | C] () -- C:\WINDOWS\bootstat.dat
[2009/07/28 11:34:46 | 000,021,640 | ---- | C] () -- C:\WINDOWS\System32\emptyregdb.dat
[2009/07/28 04:27:47 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2009/07/28 04:26:27 | 000,189,792 | ---- | C] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2005/03/22 10:48:43 | 013,107,200 | ---- | C] () -- C:\WINDOWS\System32\oembios.bin
[2005/03/22 10:48:43 | 000,004,627 | ---- | C] () -- C:\WINDOWS\System32\oembios.dat
[2004/08/04 02:00:00 | 000,673,088 | ---- | C] () -- C:\WINDOWS\System32\mlang.dat
[2004/08/04 02:00:00 | 000,314,838 | ---- | C] () -- C:\WINDOWS\System32\perfh009.dat
[2004/08/04 02:00:00 | 000,272,128 | ---- | C] () -- C:\WINDOWS\System32\perfi009.dat
[2004/08/04 02:00:00 | 000,218,003 | ---- | C] () -- C:\WINDOWS\System32\dssec.dat
[2004/08/04 02:00:00 | 000,046,258 | ---- | C] () -- C:\WINDOWS\System32\mib.bin
[2004/08/04 02:00:00 | 000,041,040 | ---- | C] () -- C:\WINDOWS\System32\perfc009.dat
[2004/08/04 02:00:00 | 000,028,626 | ---- | C] () -- C:\WINDOWS\System32\perfd009.dat
[2004/08/04 02:00:00 | 000,004,569 | ---- | C] () -- C:\WINDOWS\System32\secupd.dat
[2004/08/04 02:00:00 | 000,001,788 | ---- | C] () -- C:\WINDOWS\System32\Dcache.bin
[2004/08/04 02:00:00 | 000,000,741 | ---- | C] () -- C:\WINDOWS\System32\noise.dat
[2003/01/07 14:05:08 | 000,002,695 | ---- | C] () -- C:\WINDOWS\System32\OUTLPERF.INI
========== LOP Check ==========
[2011/06/15 19:01:00 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\AVAST Software
[2011/06/15 06:14:51 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\avg9
[2011/03/14 06:30:57 | 000,000,000 | -H-D | M] -- C:\Documents and Settings\All Users\Application Data\Common Files
[2009/07/29 11:45:55 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\LogMeIn
[2011/08/02 11:22:22 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\MFAData
[2010/07/24 13:12:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\Leadertech
[2010/09/09 19:23:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\Thunderbird
[2010/02/02 21:36:54 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Bob\Application Data\W Photo Studio Viewer
========== Purity Check ==========
< End of report >
#12
![False XP Home Security 2012 Alert [Solved]: post #12](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 December 2011 - 02:44 PM
Posted 23 December 2011 - 02:44 PM

Actually it would have been perfectly safe to allow the update but not a problem. If in the event we do use it again merely allow the update.1) After I dragged your script onto ComboFix and it ran, I was asked if I wanted an update that was available. I clicked no...just because I was unsure
Not a problem.2)Even though my avast! antivirus was turned off, it updated itself during the log preparation stage of ComboFix
No, this has probably been caused by the malware that has been removed so far. We will reset it and see if that cures this particular issue.I see that the firewall is still "unmonitored" (is this because I have a router?)
Aye it is prudent however since at present your machine only has Service Pack 2 installed it will not be a issue/interfere with the malware removal process.(Is it good to keep updates on automatic?)
That is normal and will have been placed on the desktop by ComboFix as part of its routine. You can delete the icon if you so wish.5)an IE icon has appeared on my desktop even though I use a different browser
It appears to myself we have been dealing with what is known as a rogue anti-malware application.I'd be curious what malware, if any, was still on my computer when I opened this strand in the forum.
Reset SP2 Firewall:
Click on Start >> Run... and cut/paste in the following and click on OK
firewall.cplClick on the Advanced tab >> Restore Defaults >> At the prompt click on Yes >> OK
Now click on the General tab >> select On(recommended) >> OK.
Custom OTL Script:
- Double-click OTL.exeto start the program.
- Copy the lines from the quote-box(do not copy the word quote) to the clipboard by highlighting ALL of them and pressing CTRL + C (or, after highlighting, right-click and choose Copy):
:OTL
SRV - File not found [Disabled | Stopped] -- -- (HidServ)
SRV - File not found [On_Demand | Stopped] -- -- (AppMgmt)
O2 - BHO: (no name) - {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} - No CLSID value found.
O2 - BHO: (Java™ Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll File not found
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} http://platformdl.ad...Plus/1.6/gp.cab (Reg Error: Key error.)
:Files
ipconfig /flushdns /c
:Commands
[EmptyTemp]
[CreateRestorePoint]
[Reboot]
- Return to OTL, right-click in the Custom Scans/Fixes window (under the cyan bar) and choose Paste.
- Then click the red Run Fix button.
- Let the program run unhindered.
- If OTL asks to reboot your computer, allow it to do so. The report should appear in Notepad after the reboot.
ESET Online Scanner:
Note: You can use either Internet Explorer or Mozilla FireFox for this scan. You will however need to disable your current installed Anti-Virus, how to do so can be read here.
- Please go here to run the scan...Click on Scan Now
Note: If using Mozilla Firefox you will need to download esetsmartinstaller_enu.exe when prompted then double click on it to install.
All of the below instructions are compatible with either Internet Explorer or Mozilla FireFox. - Select the option YES, I accept the Terms of Use then click on:

- When prompted allow the Add-On/Active X to install.
- Make sure that the option Remove found threats is Not checked, and the option Scan archives is checked.
- Now click on Advanced Settings and select the following:
- Scan for potentially unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Now click on:

- The virus signature database... will begin to download. Be patient this make take some time depending on the speed of your Internet Connection.
- When completed the Online Scan will begin automatically.
- Do not touch either the Mouse or keyboard during the scan otherwise it may stall.
- When completed select Uninstall application on close if you so wish, make sure you copy the logfile first!
- Now click on:

- Use notepad to open the logfile located at C:\Program Files\ESET\EsetOnlineScanner\log.txt.
- Copy and paste that log as a reply to this topic.
When completed the above, please post back the following in the order asked for:
- How is your computer performing now, any further symptoms and or problems encountered?
- OTL Log from the Custom Script.
- Eset Log.
#13
![False XP Home Security 2012 Alert [Solved]: post #13](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 December 2011 - 06:12 PM
Posted 23 December 2011 - 06:12 PM

All processes killed
========== OTL ==========
Service HidServ stopped successfully!
Service HidServ deleted successfully!
Service AppMgmt stopped successfully!
Service AppMgmt deleted successfully!
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{3CA2F312-6F6E-4B53-A66E-4E65E497C8C0}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3CA2F312-6F6E-4B53-A66E-4E65E497C8C0}\ not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{DBC80044-A445-435b-BC74-9C25C1C588A9}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{DBC80044-A445-435b-BC74-9C25C1C588A9}\ deleted successfully.
Starting removal of ActiveX control {E2883E8F-472F-4FB0-9522-AC9BF37916A7}
C:\WINDOWS\Downloaded Program Files\gp.inf not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{E2883E8F-472F-4FB0-9522-AC9BF37916A7}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E2883E8F-472F-4FB0-9522-AC9BF37916A7}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{E2883E8F-472F-4FB0-9522-AC9BF37916A7}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E2883E8F-472F-4FB0-9522-AC9BF37916A7}\ not found.
========== FILES ==========
< ipconfig /flushdns /c >
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
C:\Documents and Settings\Bob\Desktop\geeks to go\cmd.bat deleted successfully.
C:\Documents and Settings\Bob\Desktop\geeks to go\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Bob
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 39858 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 37082497 bytes
->Flash cache emptied: 456 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: LocalService
->Temp folder emptied: 65748 bytes
->Temporary Internet Files folder emptied: 32902 bytes
->Flash cache emptied: 0 bytes
User: NetworkService
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 32902 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32\dllcache .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 109080 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 0 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temporary Internet Files folder emptied: 0 bytes
RecycleBin emptied: 0 bytes
Total Files Cleaned = 36.00 mb
Restore point Set: OTL Restore Point (0)
OTL by OldTimer - Version 3.2.31.0 log created on 12232011_145827
Files\Folders moved on Reboot...
File move failed. C:\WINDOWS\temp\_avast_\Webshlock.txt scheduled to be moved on reboot.
Registry entries deleted on Reboot...
ESETSmartInstaller@High as downloader log:
all ok
# version=7
# OnlineScannerApp.exe=1.0.0.1
# OnlineScanner.ocx=1.0.0.6583
# api_version=3.0.2
# EOSSerial=71cbab19d435a043893046c717bf6c90
# end=finished
# remove_checked=false
# archives_checked=true
# unwanted_checked=true
# unsafe_checked=true
# antistealth_checked=true
# utc_time=2011-12-23 11:37:10
# local_time=2011-12-23 03:37:10 (-0800, Pacific Standard Time)
# country="United States"
# lang=1033
# osver=5.1.2600 NT Service Pack 2
# compatibility_mode=512 16777215 100 0 66932820 66932820 0 0
# compatibility_mode=1026 16777214 0 2 65330464 65330464 0 0
# compatibility_mode=8192 67108863 100 0 0 0 0 0
# scanned=35802
# found=2
# cleaned=0
# scan_time=1603
C:\Documents and Settings\All Users\Application Data\Spybot - Search & Destroy\Recovery\WinFakeAlertttam.zip Win32/Bagle.gen.zip worm (unable to clean) 00000000000000000000000000000000 I
C:\Documents and Settings\All Users\Application Data\Spybot - Search & Destroy\Recovery\WinPalevo1.zip Win32/Bagle.gen.zip worm (unable to clean) 00000000000000000000000000000000 I
#14
![False XP Home Security 2012 Alert [Solved]: post #14](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 December 2011 - 07:38 AM
Posted 24 December 2011 - 07:38 AM

Good and you're welcome!Thank you again. Mostly the computer runs fine. I say mostly only because I have simply browsed a few websites, opened a couple of my own Word documents and restarted.
The below Ram advice would probably make some difference plus when I give the all clear I will provide some advice about system maintenance.The restart seemed slower, but sometimes it does that too
It appears to be a folder left behind after uninstalltion and the actual detections are false positives. However we will delete the folder anyway as it is not required.I did notice that the eset scan found a couple of threats which the log says it couldn't clean. Those appear to be associated with a spybot search and destroy which I no longer have. Or maybe they are simply masked with an innocent sounding "spybot" name. I
Random Access Memory Advice:
Though Microsoft claims XP will run with a mere 128 MB installed in my humble opinion a minimum of 1 GB is far better.503.30 Mb Total Physical Memory | 213.09 Mb Available Physical Memory | 42.34% Memory free
If you wish to upgrade the installed memory, Crucial have a small scanner(CrucialScan.exe)which is perfectly safe to download and run. Which will advise if your system can support any upgraded memory modules. They cater for the US/UK and Europe.
Next:
Using Windows Explorer (to get there right-click your Start button and go to "Explore"), please delete this folder (if present):
C:\Documents and Settings\All Users\Application Data\Spybot - Search & Destroy
Then empty the Recycle Bin.
Install Service Pack 3:
The download can be found here.
Please read this Microsoft article before actually installing the aforementioned Service Pack.
Next:
Let myself know when completed the above and post a new OTL log please and we will go from there, thank you.
#15
![False XP Home Security 2012 Alert [Solved]: post #15](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 December 2011 - 01:59 PM
Posted 24 December 2011 - 01:59 PM

http://www.microsoft...aylang=en&id=24
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

