Let's see a Process Explorer log with the services and device off per your last post.
slow performance with xp pc
Started by
benny_b
, Jan 25 2012 08:38 PM
#16

 Posted 30 January 2012 - 02:41 PM
Posted 30 January 2012 - 02:41 PM

Let's see a Process Explorer log with the services and device off per your last post.
#17

 Posted 31 January 2012 - 08:52 AM
Posted 31 January 2012 - 08:52 AM

i installed the latest directx last year i think? recently anyways.
that PCIDump driver had a rep as a trojan/backdoor.
i took a few snapshots with process explorer to show you the instability.
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 93.07 0 K 16 K
procexp.exe 2956 2.97 11,176 K 14,664 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
Interrupts n/a 1.98 0 K 0 K Hardware Interrupts
services.exe 776 0.99 1,880 K 3,748 K Services and Controller app Microsoft Corporation
DPCs n/a 0.99 0 K 0 K Deferred Procedure Calls
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,616 K 5,252 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1340 1,748 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1132 15,056 K 22,480 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,636 K 3,772 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,564 K 4,128 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,668 K 4,548 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,880 K 5,756 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,124 K 6,472 K LSA Shell (Export Version) Microsoft Corporation
explorer.exe 120 18,912 K 25,836 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,588 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,208 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,108 K 876 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 91.18 0 K 16 K
Interrupts n/a 2.94 0 K 0 K Hardware Interrupts
DPCs n/a 2.94 0 K 0 K Deferred Procedure Calls
procexp.exe 2956 1.96 11,136 K 14,648 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
services.exe 776 0.98 1,880 K 3,748 K Services and Controller app Microsoft Corporation
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,616 K 5,252 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,056 K 22,544 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,748 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,564 K 4,128 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,668 K 4,548 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,880 K 5,756 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3772 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,052 K 624 K LSA Shell (Export Version) Microsoft Corporation
explorer.exe 120 18,916 K 25,988 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,588 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,216 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,096 K 2,888 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 95.10 0 K 16 K
DPCs n/a 2.94 0 K 0 K Deferred Procedure Calls
services.exe 776 0.98 1,880 K 3,748 K Services and Controller app Microsoft Corporation
procexp.exe 2956 0.98 11,116 K 14,652 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,580 K 5,272 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,028 K 22,532 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,772 K 4,372 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,540 K 4,120 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,644 K 4,536 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,840 K 5,748 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3772 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,020 K 928 K LSA Shell (Export Version) Microsoft Corporation
Interrupts n/a 0 K 0 K Hardware Interrupts
explorer.exe 120 18,920 K 26,012 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,592 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,216 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,096 K 1,136 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 91.09 0 K 16 K
Interrupts n/a 5.94 0 K 0 K Hardware Interrupts
procexp.exe 2928 1.98 11,140 K 14,664 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
services.exe 776 0.99 1,880 K 3,772 K Services and Controller app Microsoft Corporation
wmiprvse.exe 3236 2,584 K 5,280 K WMI Microsoft Corporation
winlogon.exe 732 6,372 K 1,828 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,396 K 25,540 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,728 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,712 K 4,688 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,988 K 4,616 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,556 K 3,860 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,060 K 7,532 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,540 K 4,120 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,720 K 5,720 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 492 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3492 1,228 K 512 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 680 K Notepad Microsoft Corporation
notepad.exe 3772 1,228 K 540 K Notepad Microsoft Corporation
notepad.exe 2396 1,228 K 540 K Notepad Microsoft Corporation
lsass.exe 788 3,920 K 1,144 K LSA Shell (Export Version) Microsoft Corporation
firefox.exe 3932 89,684 K 96,888 K Firefox Mozilla Corporation
explorer.exe 120 20,104 K 28,788 K Windows Explorer Microsoft Corporation
DPCs n/a 0 K 0 K Deferred Procedure Calls
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,424 K 3,424 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,604 K 2,732 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 11,620 K 4,212 K avast! Service AVAST Software
alg.exe 672 1,412 K 3,968 K Application Layer Gateway Service Microsoft Corporation
that PCIDump driver had a rep as a trojan/backdoor.
i took a few snapshots with process explorer to show you the instability.
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 93.07 0 K 16 K
procexp.exe 2956 2.97 11,176 K 14,664 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
Interrupts n/a 1.98 0 K 0 K Hardware Interrupts
services.exe 776 0.99 1,880 K 3,748 K Services and Controller app Microsoft Corporation
DPCs n/a 0.99 0 K 0 K Deferred Procedure Calls
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,616 K 5,252 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1340 1,748 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1132 15,056 K 22,480 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,636 K 3,772 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,564 K 4,128 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,668 K 4,548 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,880 K 5,756 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,124 K 6,472 K LSA Shell (Export Version) Microsoft Corporation
explorer.exe 120 18,912 K 25,836 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,588 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,208 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,108 K 876 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 91.18 0 K 16 K
Interrupts n/a 2.94 0 K 0 K Hardware Interrupts
DPCs n/a 2.94 0 K 0 K Deferred Procedure Calls
procexp.exe 2956 1.96 11,136 K 14,648 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
services.exe 776 0.98 1,880 K 3,748 K Services and Controller app Microsoft Corporation
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,616 K 5,252 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,056 K 22,544 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,748 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,564 K 4,128 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,668 K 4,548 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,880 K 5,756 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3772 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,052 K 624 K LSA Shell (Export Version) Microsoft Corporation
explorer.exe 120 18,916 K 25,988 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,588 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,216 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,096 K 2,888 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 95.10 0 K 16 K
DPCs n/a 2.94 0 K 0 K Deferred Procedure Calls
services.exe 776 0.98 1,880 K 3,748 K Services and Controller app Microsoft Corporation
procexp.exe 2956 0.98 11,116 K 14,652 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
wuauclt.exe 1160 6,752 K 8,164 K Windows Update Microsoft Corporation
wmiprvse.exe 3088 2,580 K 5,272 K WMI Microsoft Corporation
winlogon.exe 732 6,456 K 1,852 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,028 K 22,532 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,772 K 4,372 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,560 K 3,872 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,956 K 4,584 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,020 K 7,476 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,540 K 4,120 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,644 K 4,536 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,840 K 5,748 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 3772 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 512 K Notepad Microsoft Corporation
lsass.exe 788 4,020 K 928 K LSA Shell (Export Version) Microsoft Corporation
Interrupts n/a 0 K 0 K Hardware Interrupts
explorer.exe 120 18,920 K 26,012 K Windows Explorer Microsoft Corporation
dpclat.exe 2472 944 K 3,592 K DPC Latency Checker Thesycon GmbH
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,420 K 3,216 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,628 K 2,572 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 9,096 K 1,136 K avast! Service AVAST Software
alg.exe 672 1,408 K 3,948 K Application Layer Gateway Service Microsoft Corporation
Process PID CPU Private Bytes Working Set Description Company Name
System Idle Process 0 91.09 0 K 16 K
Interrupts n/a 5.94 0 K 0 K Hardware Interrupts
procexp.exe 2928 1.98 11,140 K 14,664 K Sysinternals Process Explorer Sysinternals - www.sysinternals.com
services.exe 776 0.99 1,880 K 3,772 K Services and Controller app Microsoft Corporation
wmiprvse.exe 3236 2,584 K 5,280 K WMI Microsoft Corporation
winlogon.exe 732 6,372 K 1,828 K Windows NT Logon Application Microsoft Corporation
System 4 0 K 228 K
svchost.exe 1132 15,396 K 25,540 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1340 1,728 K 4,364 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 2036 2,712 K 4,688 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1028 1,988 K 4,616 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 944 1,556 K 3,860 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1164 2,612 K 3,764 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1276 5,060 K 7,532 K Generic Host Process for Win32 Services Microsoft Corporation
svchost.exe 1836 1,540 K 4,120 K Generic Host Process for Win32 Services Microsoft Corporation
spoolsv.exe 1484 3,720 K 5,720 K Spooler SubSystem App Microsoft Corporation
smss.exe 440 172 K 416 K Windows NT Session Manager Microsoft Corporation
notepad.exe 492 1,228 K 516 K Notepad Microsoft Corporation
notepad.exe 3492 1,228 K 512 K Notepad Microsoft Corporation
notepad.exe 3320 1,228 K 680 K Notepad Microsoft Corporation
notepad.exe 3772 1,228 K 540 K Notepad Microsoft Corporation
notepad.exe 2396 1,228 K 540 K Notepad Microsoft Corporation
lsass.exe 788 3,920 K 1,144 K LSA Shell (Export Version) Microsoft Corporation
firefox.exe 3932 89,684 K 96,888 K Firefox Mozilla Corporation
explorer.exe 120 20,104 K 28,788 K Windows Explorer Microsoft Corporation
DPCs n/a 0 K 0 K Deferred Procedure Calls
ctfmon.exe 1400 1,140 K 3,584 K CTF Loader Microsoft Corporation
csrss.exe 708 1,424 K 3,424 K Client Server Runtime Process Microsoft Corporation
AvastUI.exe 1192 4,604 K 2,732 K avast! Antivirus AVAST Software
AvastSvc.exe 1924 11,620 K 4,212 K avast! Service AVAST Software
alg.exe 672 1,412 K 3,968 K Application Layer Gateway Service Microsoft Corporation
#18

 Posted 31 January 2012 - 10:00 AM
Posted 31 January 2012 - 10:00 AM

It's the
Interrupts n/a line which is the problem. Is this with or without the battery?
I went back and looked at your thread and I see we never ran Combofix. Let's try again.
First uninstall Malware Bytes Anti-Malware as it can cause problems.
Then tell Avast not to bother us:
Click on the Avast ball. Then click on Additional Protections then on AutoSandbox then on Settings then uncheck Enable AutoSandbox. OK
Right click on the Avast Ball and select Avast! Shields Control and Disable Until Computer is Restarted
Make sure that Combofix.exe is on your desktop. Copy the next line:
C:\Documents and Settings\Mike\Desktop\combofix.exe /uninstall
Start, All Programs, Accessories, right click on Command Prompt and Run as Administrator, Continue. Right click and
select Paste or Edit then Paste and the line should appear. Hit Enter. This will remove Combofix.
reboot into Safe Mode with Networking.
Right click on the Avast Ball and select Avast! Shields Control and Disable Until Computer is Restarted (if you don't have the avast ball in this mode then go into (All) Programs, Avast ..., Avast ... and under Real Time Shields, select each and press the Stop button, and Disable Until Computer is Restarted.
Now download a new copy.
http://subs.geekstogo.com/ComboFix.exe
and save it to your desktop but rename it george.exe
now close all programs including your browser and copy the next line:
C:\Documents and Settings\Mike\Desktop\george.exe /killall
Start, All Programs, Accessories, right click on Command Prompt and Run as Administrator, Continue. Right click and
select Paste or Edit then Paste and the line should appear. Hit Enter.
Ron
Interrupts n/a line which is the problem. Is this with or without the battery?
I went back and looked at your thread and I see we never ran Combofix. Let's try again.
First uninstall Malware Bytes Anti-Malware as it can cause problems.
Then tell Avast not to bother us:
Click on the Avast ball. Then click on Additional Protections then on AutoSandbox then on Settings then uncheck Enable AutoSandbox. OK
Right click on the Avast Ball and select Avast! Shields Control and Disable Until Computer is Restarted
Make sure that Combofix.exe is on your desktop. Copy the next line:
C:\Documents and Settings\Mike\Desktop\combofix.exe /uninstall
Start, All Programs, Accessories, right click on Command Prompt and Run as Administrator, Continue. Right click and
select Paste or Edit then Paste and the line should appear. Hit Enter. This will remove Combofix.
reboot into Safe Mode with Networking.
Right click on the Avast Ball and select Avast! Shields Control and Disable Until Computer is Restarted (if you don't have the avast ball in this mode then go into (All) Programs, Avast ..., Avast ... and under Real Time Shields, select each and press the Stop button, and Disable Until Computer is Restarted.
Now download a new copy.
http://subs.geekstogo.com/ComboFix.exe
and save it to your desktop but rename it george.exe
now close all programs including your browser and copy the next line:
C:\Documents and Settings\Mike\Desktop\george.exe /killall
Start, All Programs, Accessories, right click on Command Prompt and Run as Administrator, Continue. Right click and
select Paste or Edit then Paste and the line should appear. Hit Enter.
Ron
#19

 Posted 31 January 2012 - 12:29 PM
Posted 31 January 2012 - 12:29 PM

that's what i was saying about not being sure if the battery was the culprit as i have been running without my battery since you asked me to remove it on sunday.
perhaps my command prompt has been reconfigured? it comes up with
C:\Documents and Settings\Mike>
when i paste your command it says
'C:\Documents' is not recognized as an internal or external command, operable program or batch file
i'm trying to figure this out. do i need to put quotations around the command?
perhaps my command prompt has been reconfigured? it comes up with
C:\Documents and Settings\Mike>
when i paste your command it says
'C:\Documents' is not recognized as an internal or external command, operable program or batch file
i'm trying to figure this out. do i need to put quotations around the command?
Edited by benny_b, 31 January 2012 - 01:09 PM.
#20

 Posted 31 January 2012 - 01:11 PM
Posted 31 January 2012 - 01:11 PM

Make it say:
"C:\Documents and Settings\Mike\Desktop\combofix.exe" /uninstall
"C:\Documents and Settings\Mike\Desktop\combofix.exe" /uninstall
#21

 Posted 31 January 2012 - 04:10 PM
Posted 31 January 2012 - 04:10 PM

george isn't working either. it gets to the "scanning for infected files..." and after a couple of minutes the hard drive spins down.
i had the avast shields set to turn on after reboot. in safe mode they came up 'status unknown'. after about 90 minutes i forced shutdown, rebooted into normal, permanently disabled the shields, disabled autosandbox again, which had reenabled itself and started george in safe mode again. i don't know if this is the problem, but i'm reading posts about autosandbox behaving this way. maybe i should just uninstall avast.
there's a post on disabling the sandbox, but i have no idea what he's talking about, "...Put the clients into one group in SBC, if not done already, and edit the group settings. Then go to the advanced settings and change this line to '0'"
anyways, i rebooted and the autosandbox was still off, so that doesn't seem to be the problem.
i had the avast shields set to turn on after reboot. in safe mode they came up 'status unknown'. after about 90 minutes i forced shutdown, rebooted into normal, permanently disabled the shields, disabled autosandbox again, which had reenabled itself and started george in safe mode again. i don't know if this is the problem, but i'm reading posts about autosandbox behaving this way. maybe i should just uninstall avast.
there's a post on disabling the sandbox, but i have no idea what he's talking about, "...Put the clients into one group in SBC, if not done already, and edit the group settings. Then go to the advanced settings and change this line to '0'"
anyways, i rebooted and the autosandbox was still off, so that doesn't seem to be the problem.
Edited by benny_b, 31 January 2012 - 04:32 PM.
#22

 Posted 01 February 2012 - 12:45 AM
Posted 01 February 2012 - 12:45 AM

Let's see if DDS will open.
Please download DDS from http://download.blee...om/sUBs/dds.com or http://download.blee...om/sUBs/dds.scr
and save it to your desktop.
* Disable any script blocking protection
* Double click dds.pif to run the tool.
* When done, two DDS.txt's will open.
* Save both reports to your desktop.
---------------------------------------------------
Please include the contents of the following in your next reply:
DDS.txt
Attach.txt.
Please download DDS from http://download.blee...om/sUBs/dds.com or http://download.blee...om/sUBs/dds.scr
and save it to your desktop.
* Disable any script blocking protection
* Double click dds.pif to run the tool.
* When done, two DDS.txt's will open.
* Save both reports to your desktop.
---------------------------------------------------
Please include the contents of the following in your next reply:
DDS.txt
Attach.txt.
#23

 Posted 01 February 2012 - 08:40 AM
Posted 01 February 2012 - 08:40 AM

unfortunately this scan appears to have stopped about 3/4 of the way.
i tried the second download window for dds.scr. when i launch the program it immediately put up a notepad file saying, "this program cannot be run in DOS mode..." followed by script.
i've run the scan in safe mode and it stalls at the 3/4 point as well.
i tried the second download window for dds.scr. when i launch the program it immediately put up a notepad file saying, "this program cannot be run in DOS mode..." followed by script.
i've run the scan in safe mode and it stalls at the 3/4 point as well.
Edited by benny_b, 01 February 2012 - 09:12 AM.
#24

 Posted 01 February 2012 - 10:37 AM
Posted 01 February 2012 - 10:37 AM

This is one I don't use too often but since my usual tools don't work let's try it:
Download AVPTool from Here to your desktop
Run the programme you have just downloaded to your desktop (it will be randomly named )
First we will run a virus scan
Click the cog in the upper right
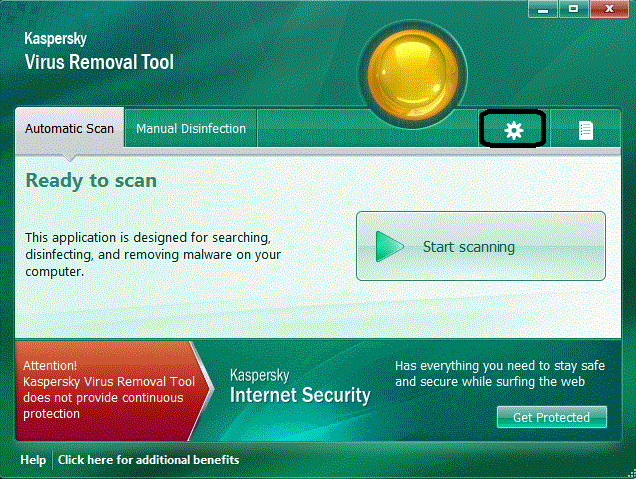
Select down to and including your main drive, once done select the Automatic scan tab and press Start Scan
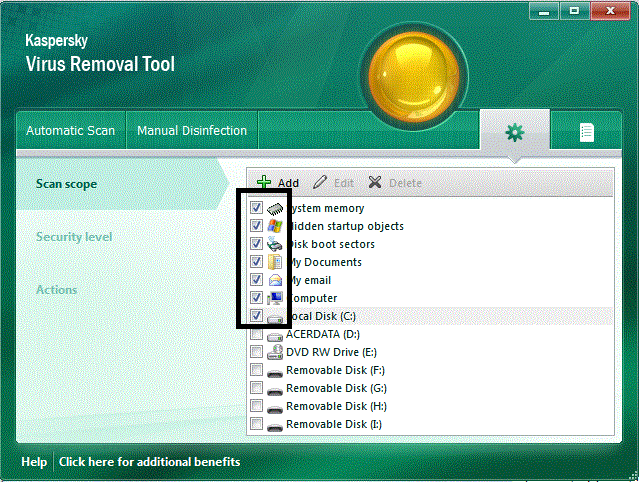
Allow AVP to delete all infections found
Once it has finished select report tab (last tab)
Select Detected threads report from the left and press Save button
Save it to your desktop and attach to your next post
Now the Analysis
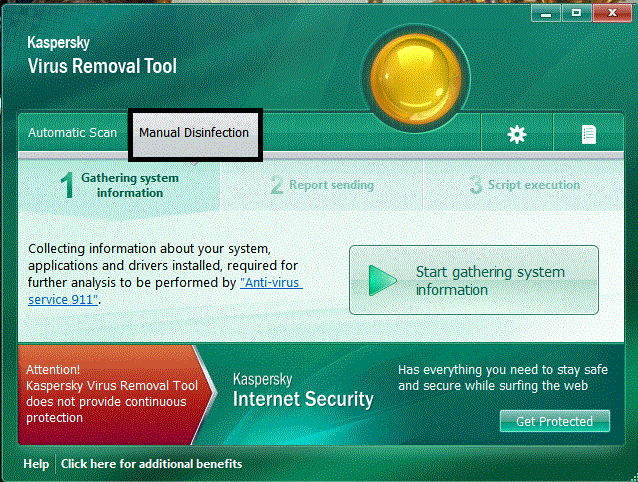
Rerun AVP and select the Manual Disinfection tab and press Start Gathering System Information
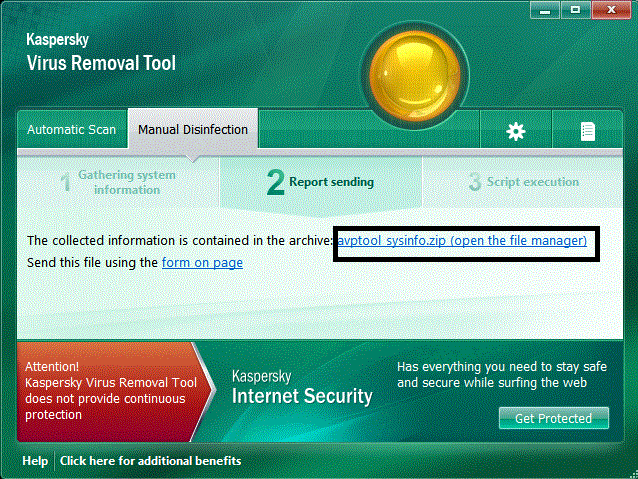
On completion click the link to locate the zip file to upload and attach to your next post
Download AVPTool from Here to your desktop
Run the programme you have just downloaded to your desktop (it will be randomly named )
First we will run a virus scan
Click the cog in the upper right

Select down to and including your main drive, once done select the Automatic scan tab and press Start Scan

Allow AVP to delete all infections found
Once it has finished select report tab (last tab)
Select Detected threads report from the left and press Save button
Save it to your desktop and attach to your next post
Now the Analysis
Rerun AVP and select the Manual Disinfection tab and press Start Gathering System Information

On completion click the link to locate the zip file to upload and attach to your next post

#25

 Posted 01 February 2012 - 02:01 PM
Posted 01 February 2012 - 02:01 PM

i ran the scans and removed one threat, but i wouldn't have thought that would have jammed the other scanners.
there were also a couple of other files that were password protected that it flagged (there's a little pop up window in the lower right), but didn't recognize as threats. i tried to click on one for "more details", but then it just disappeared.
i believe that the autodesk express viewer was previously quarantined by avast. i sent it to their virus analyzer and they told me it was a false positive. maybe i should remove it anyways. i actually did try and it asked for a password, but i have no idea what the password is.
there were also a couple of other files that were password protected that it flagged (there's a little pop up window in the lower right), but didn't recognize as threats. i tried to click on one for "more details", but then it just disappeared.
i believe that the autodesk express viewer was previously quarantined by avast. i sent it to their virus analyzer and they told me it was a false positive. maybe i should remove it anyways. i actually did try and it asked for a password, but i have no idea what the password is.
Attached Files
#26

 Posted 01 February 2012 - 02:40 PM
Posted 01 February 2012 - 02:40 PM

The detected threats were nothing serious. I think the first one is just the install program for autodesk. The second one probably nothing more than one of your 127.0.0.0 entries pointing to some nasty site and that in a backup hosts file so not active.
What does look interesting is the "Hook code blocked" stuff down at the bottom. No details on it unfortunately. As I don't use this program very much I'm not really sure if this is something it always says or if it really found something.
I also see C:\DOCUME~1\Mike\LOCALS~1\Temp\OnlineScanner\Anti-Virus\fsgk.sys
We don't really want this running while we are trying to run CF. No telling what it does. Is there an uninstall for it? If not just delete the file.
Let's see if we can get IceSword to run:
Please download and unzip Icesword to its own folder on your desktop
If you get a lot of "red entries" in an IceSword log, don't panic.
Step 1 : Close all windows and run IceSword. Click the Processes tab and watch for processes displayed in red color. A red colored process in this list indicates that it's hidden. Write down the PathName of any processes in red color. Then click on LOG at the top left. It will prompt you to save the log, call this Processes and save it to your desktop.
Step 2 : Click the Win32 Services tab and look out for red colored entries in the services list. Write down the Module name of any services in red color, you will need to expand out the Module tab to see the full name. Then click on LOG. It will prompt you to save the log, call this Services and save it to your desktop.
Step 3 : Click the Startup tab and look out for red colored entries in the startup list. Write down the Path of any startup entries in red color. Then click on LOG. It will prompt you to save the log, call this Startup and save it to your desktop.
Step 4 : Click the SSDT tab and check for red colored entries. If there are any, write down the KModule name.
Step 5 : Click the Message Hooks tab and check for any entries that are underneath Type and labelled WH_KEYBOARD. Write down the Process Path of these entries if present.
Now post all of the data collected under the headings for :
Processes
Win32 Services
Startup
SSDT
Message Hooks
also try GMER:
Download the GMER Rootkit Scanner. Unzip it to your Desktop.
Before scanning, make sure all other running programs are closed and no other actions like a scheduled antivirus scan will occur while the scan is being performed. Do not use your computer for anything else during the scan.
Double-click gmer.exe. The program will begin to run.
**Caution**
These types of scans can produce false positives. Do NOT take any action on any "<--- ROOKIT" entries unless advised!
If possible rootkit activity is found, you will be asked if you would like to perform a full scan.
What does look interesting is the "Hook code blocked" stuff down at the bottom. No details on it unfortunately. As I don't use this program very much I'm not really sure if this is something it always says or if it really found something.
I also see C:\DOCUME~1\Mike\LOCALS~1\Temp\OnlineScanner\Anti-Virus\fsgk.sys
We don't really want this running while we are trying to run CF. No telling what it does. Is there an uninstall for it? If not just delete the file.
Let's see if we can get IceSword to run:
Please download and unzip Icesword to its own folder on your desktop
If you get a lot of "red entries" in an IceSword log, don't panic.
Step 1 : Close all windows and run IceSword. Click the Processes tab and watch for processes displayed in red color. A red colored process in this list indicates that it's hidden. Write down the PathName of any processes in red color. Then click on LOG at the top left. It will prompt you to save the log, call this Processes and save it to your desktop.
Step 2 : Click the Win32 Services tab and look out for red colored entries in the services list. Write down the Module name of any services in red color, you will need to expand out the Module tab to see the full name. Then click on LOG. It will prompt you to save the log, call this Services and save it to your desktop.
Step 3 : Click the Startup tab and look out for red colored entries in the startup list. Write down the Path of any startup entries in red color. Then click on LOG. It will prompt you to save the log, call this Startup and save it to your desktop.
Step 4 : Click the SSDT tab and check for red colored entries. If there are any, write down the KModule name.
Step 5 : Click the Message Hooks tab and check for any entries that are underneath Type and labelled WH_KEYBOARD. Write down the Process Path of these entries if present.
Now post all of the data collected under the headings for :
Processes
Win32 Services
Startup
SSDT
Message Hooks
also try GMER:
Download the GMER Rootkit Scanner. Unzip it to your Desktop.
Before scanning, make sure all other running programs are closed and no other actions like a scheduled antivirus scan will occur while the scan is being performed. Do not use your computer for anything else during the scan.
Double-click gmer.exe. The program will begin to run.
**Caution**
These types of scans can produce false positives. Do NOT take any action on any "<--- ROOKIT" entries unless advised!
If possible rootkit activity is found, you will be asked if you would like to perform a full scan.
- Click NO
- In the right panel, you will see a bunch of boxes that have been checked ... leave everything checked and ensure the Show all box is un-checked.
- Now click the Scan button.
Once the scan is complete, you may receive another notice about rootkit activity. - Click OK.
- GMER will produce a log. Click on the [Save..] button, and in the File name area, type in "GMER.txt"
- Save it where you can easily find it, such as your desktop.
#27

 Posted 01 February 2012 - 07:52 PM
Posted 01 February 2012 - 07:52 PM

the icesword doesn't appear to have found much. the processes, win32, and start up were totally clean. the SSDT appears to be all avast files. the message hooks,...well you'll have to decide. the gmer log is at the end.
i tried to find
C:\DOCUME~1\Mike\LOCALS~1\Temp\OnlineScanner\Anti-Virus\fsgk.sys
i don't know why but explorer is no longer displaying these folders. i can only see desktop, favorites, my documents, start menu. that is an old file from a F-Secure online virus scan i did about two years ago.
i also reinstalled the battery. please let me know if you need me to remove it again.
SSDT
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
Message Hooks
C:\WINDOWS\explorer.exe
C:\WINDOWS\System32\ctfmon.exe
C:\WINDOWS\explorer.exe
C:\Program Files\AVAST Software\Avast\AvastUI.exe
GMER
GMER 1.0.15.15641 - http://www.gmer.net
Rootkit scan 2012-02-01 20:23:56
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3 IC25N040ATMR04-0 rev.MO2OAD4A
Running: gmer.exe; Driver: C:\DOCUME~1\Mike\LOCALS~1\Temp\fftcrfob.sys
---- System - GMER 1.0.15 ----
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwAddBootEntry [0xF2993FC4]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwAllocateVirtualMemory [0xF2A20510]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwClose [0xF29B76A9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEvent [0xF2996456]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEventPair [0xF29964AE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateIoCompletion [0xF29965C4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateKey [0xF29B705D]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateMutant [0xF29963AC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSection [0xF29964FE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSemaphore [0xF2996400]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateTimer [0xF2996572]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteBootEntry [0xF2993FE8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteKey [0xF29B7D6F]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteValueKey [0xF29B8025]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDuplicateObject [0xF2996848]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateKey [0xF29B7BDA]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateValueKey [0xF29B7A45]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwFreeVirtualMemory [0xF2A205C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwLoadDriver [0xF2993DB2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwModifyBootEntry [0xF299400C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeKey [0xF29969BC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeMultipleKeys [0xF2994AA4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEvent [0xF2996486]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEventPair [0xF29964D6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenIoCompletion [0xF29965EE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenKey [0xF29B73B9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenMutant [0xF29963D8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenProcess [0xF2996680]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSection [0xF299653E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSemaphore [0xF299642E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenThread [0xF2996764]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenTimer [0xF299659C]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwProtectVirtualMemory [0xF2A20658]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryKey [0xF29B78C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryObject [0xF299496A]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryValueKey [0xF29B7712]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwRenameKey [0xF2A289E6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwRestoreKey [0xF29B66D0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootEntryOrder [0xF2994030]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootOptions [0xF2994054]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemInformation [0xF2993E0C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemPowerState [0xF2993F48]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetValueKey [0xF29B7E76]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwShutdownSystem [0xF2993F24]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSystemDebugControl [0xF2993F6C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwVdmControl [0xF2994078]
---- Kernel code sections - GMER 1.0.15 ----
.text ntoskrnl.exe!_abnormal_termination + 140 804E27AC 4 Bytes CALL 9440C0F0
.text ntoskrnl.exe!_abnormal_termination + 271 804E28DD 3 Bytes [06, A2, F2]
PAGE ntoskrnl.exe!ZwReplyWaitReceivePortEx + 3CC 8056BB08 4 Bytes CALL F299500F \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngSetLastError + 79A8 BF8242D4 5 Bytes JMP F2996B9A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!FONTOBJ_pxoGetXform + C2CF BF85198B 5 Bytes JMP F2996AD6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 3581 BF85E514 5 Bytes JMP F2996DE6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 360C BF85E59F 5 Bytes JMP F2996FBC \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreatePalette + 88 BF85F812 5 Bytes JMP F2996ABE \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngGetCurrentCodePage + 4128 BF873F30 5 Bytes JMP F2996F76 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCopyBits + 4DEC BF89DBA0 5 Bytes JMP F2996C0A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngEraseSurface + A9F7 BF8C2130 5 Bytes JMP F2996CA4 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1517 BF8CA592 5 Bytes JMP F2996D14 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1797 BF8CA812 5 Bytes JMP F2996D4E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngDeleteSemaphore + 3B3E BF8EC297 5 Bytes JMP F29969F2 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 19DF BF91348A 5 Bytes JMP F2996B56 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 25B3 BF91405E 5 Bytes JMP F2996C6E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 4F2C BF9169D7 5 Bytes JMP F29970D6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
? System32\Drivers\IsDrv122.sys The system cannot find the path specified. !
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\System32\smss.exe[432] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\alg.exe[608] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\Explorer.EXE[704] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002D0804
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002D0A08
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002D0600
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002D01F8
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002D03FC
.text C:\WINDOWS\system32\csrss.exe[708] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\csrss.exe[708] KERNEL32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000701F8
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000703FC
.text C:\WINDOWS\system32\winlogon.exe[732] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\services.exe[776] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\lsass.exe[788] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[852] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[852] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[936] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1020] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1072] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1112] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1216] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1252] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000A01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000A03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002D0804
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002D0A08
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002D0600
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002D01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002D03FC
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1676] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] kernel32.dll!SetUnhandledExceptionFilter 7C84495D 4 Bytes [C2, 04, 00, 90] {RET 0x4; NOP }
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1856] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 001501F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 001503FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 003E1014
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 003E0804
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 003E0A08
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 003E0C0C
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 003E0E10
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 003E01F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 003E03FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 003E0600
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 003F0804
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 003F0A08
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 003F0600
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 003F01F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 003F03FC
---- User IAT/EAT - GMER 1.0.15 ----
IAT C:\WINDOWS\system32\services.exe[776] @ C:\WINDOWS\system32\services.exe [ADVAPI32.dll!CreateProcessAsUserW] 005E0002
IAT C:\WINDOWS\system32\services.exe[776] @ C:\WINDOWS\system32\services.exe [KERNEL32.dll!CreateProcessW] 005E0000
---- Devices - GMER 1.0.15 ----
AttachedDevice \FileSystem\Ntfs \Ntfs aswMon2.SYS (avast! File System Filter Driver for Windows XP/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Ip aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass0 IsDrv122.sys
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass1 IsDrv122.sys
AttachedDevice \Driver\Tcpip \Device\Tcp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Udp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\RawIp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
---- EOF - GMER 1.0.15 ----
i tried to find
C:\DOCUME~1\Mike\LOCALS~1\Temp\OnlineScanner\Anti-Virus\fsgk.sys
i don't know why but explorer is no longer displaying these folders. i can only see desktop, favorites, my documents, start menu. that is an old file from a F-Secure online virus scan i did about two years ago.
i also reinstalled the battery. please let me know if you need me to remove it again.
SSDT
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSP.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
\SystemRoot\System32\Drivers\aswSnx.SYS
Message Hooks
C:\WINDOWS\explorer.exe
C:\WINDOWS\System32\ctfmon.exe
C:\WINDOWS\explorer.exe
C:\Program Files\AVAST Software\Avast\AvastUI.exe
GMER
GMER 1.0.15.15641 - http://www.gmer.net
Rootkit scan 2012-02-01 20:23:56
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3 IC25N040ATMR04-0 rev.MO2OAD4A
Running: gmer.exe; Driver: C:\DOCUME~1\Mike\LOCALS~1\Temp\fftcrfob.sys
---- System - GMER 1.0.15 ----
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwAddBootEntry [0xF2993FC4]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwAllocateVirtualMemory [0xF2A20510]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwClose [0xF29B76A9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEvent [0xF2996456]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateEventPair [0xF29964AE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateIoCompletion [0xF29965C4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateKey [0xF29B705D]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateMutant [0xF29963AC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSection [0xF29964FE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateSemaphore [0xF2996400]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwCreateTimer [0xF2996572]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteBootEntry [0xF2993FE8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteKey [0xF29B7D6F]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDeleteValueKey [0xF29B8025]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwDuplicateObject [0xF2996848]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateKey [0xF29B7BDA]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwEnumerateValueKey [0xF29B7A45]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwFreeVirtualMemory [0xF2A205C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwLoadDriver [0xF2993DB2]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwModifyBootEntry [0xF299400C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeKey [0xF29969BC]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwNotifyChangeMultipleKeys [0xF2994AA4]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEvent [0xF2996486]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenEventPair [0xF29964D6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenIoCompletion [0xF29965EE]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenKey [0xF29B73B9]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenMutant [0xF29963D8]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenProcess [0xF2996680]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSection [0xF299653E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenSemaphore [0xF299642E]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenThread [0xF2996764]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwOpenTimer [0xF299659C]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwProtectVirtualMemory [0xF2A20658]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryKey [0xF29B78C0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryObject [0xF299496A]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwQueryValueKey [0xF29B7712]
SSDT \SystemRoot\System32\Drivers\aswSP.SYS (avast! self protection module/AVAST Software) ZwRenameKey [0xF2A289E6]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwRestoreKey [0xF29B66D0]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootEntryOrder [0xF2994030]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetBootOptions [0xF2994054]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemInformation [0xF2993E0C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetSystemPowerState [0xF2993F48]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSetValueKey [0xF29B7E76]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwShutdownSystem [0xF2993F24]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwSystemDebugControl [0xF2993F6C]
SSDT \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software) ZwVdmControl [0xF2994078]
---- Kernel code sections - GMER 1.0.15 ----
.text ntoskrnl.exe!_abnormal_termination + 140 804E27AC 4 Bytes CALL 9440C0F0
.text ntoskrnl.exe!_abnormal_termination + 271 804E28DD 3 Bytes [06, A2, F2]
PAGE ntoskrnl.exe!ZwReplyWaitReceivePortEx + 3CC 8056BB08 4 Bytes CALL F299500F \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngSetLastError + 79A8 BF8242D4 5 Bytes JMP F2996B9A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!FONTOBJ_pxoGetXform + C2CF BF85198B 5 Bytes JMP F2996AD6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 3581 BF85E514 5 Bytes JMP F2996DE6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!XLATEOBJ_iXlate + 360C BF85E59F 5 Bytes JMP F2996FBC \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreatePalette + 88 BF85F812 5 Bytes JMP F2996ABE \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngGetCurrentCodePage + 4128 BF873F30 5 Bytes JMP F2996F76 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCopyBits + 4DEC BF89DBA0 5 Bytes JMP F2996C0A \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngEraseSurface + A9F7 BF8C2130 5 Bytes JMP F2996CA4 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1517 BF8CA592 5 Bytes JMP F2996D14 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngFillPath + 1797 BF8CA812 5 Bytes JMP F2996D4E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngDeleteSemaphore + 3B3E BF8EC297 5 Bytes JMP F29969F2 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 19DF BF91348A 5 Bytes JMP F2996B56 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 25B3 BF91405E 5 Bytes JMP F2996C6E \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
.text win32k.sys!EngCreateClip + 4F2C BF9169D7 5 Bytes JMP F29970D6 \SystemRoot\System32\Drivers\aswSnx.SYS (avast! Virtualization Driver/AVAST Software)
? System32\Drivers\IsDrv122.sys The system cannot find the path specified. !
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\System32\smss.exe[432] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\alg.exe[608] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\alg.exe[608] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\alg.exe[608] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[704] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\Explorer.EXE[704] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\Explorer.EXE[704] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002D0804
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002D0A08
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002D0600
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002D01F8
.text C:\WINDOWS\Explorer.EXE[704] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002D03FC
.text C:\WINDOWS\system32\csrss.exe[708] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\csrss.exe[708] KERNEL32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000701F8
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000703FC
.text C:\WINDOWS\system32\winlogon.exe[732] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\winlogon.exe[732] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\winlogon.exe[732] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[776] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\services.exe[776] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\services.exe[776] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\services.exe[776] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[788] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\lsass.exe[788] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\lsass.exe[788] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\lsass.exe[788] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[852] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\avastUI.exe[852] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[936] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[936] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[936] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1020] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1020] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1020] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1020] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1072] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1072] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1072] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1072] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1112] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1112] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1112] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1112] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1216] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1216] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1216] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1216] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1252] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\svchost.exe[1252] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\svchost.exe[1252] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\svchost.exe[1252] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[1392] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\system32\spoolsv.exe[1392] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\spoolsv.exe[1392] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000A01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\system32\ctfmon.exe[1464] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000A03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002C1014
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002C0804
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002C0A08
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002C0C0C
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002C0E10
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002C01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002C03FC
.text C:\WINDOWS\system32\ctfmon.exe[1464] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002C0600
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002D0804
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002D0A08
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002D0600
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002D01F8
.text C:\WINDOWS\system32\ctfmon.exe[1464] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002D03FC
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1676] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1676] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1676] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1676] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] kernel32.dll!SetUnhandledExceptionFilter 7C84495D 4 Bytes [C2, 04, 00, 90] {RET 0x4; NOP }
.text C:\Program Files\AVAST Software\Avast\AvastSvc.exe[1740] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 000901F8
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 000903FC
.text C:\WINDOWS\System32\svchost.exe[1856] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 002B1014
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 002B0804
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 002B0A08
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 002B0C0C
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 002B0E10
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 002B01F8
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 002B03FC
.text C:\WINDOWS\System32\svchost.exe[1856] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 002B0600
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 002C0804
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 002C0A08
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 002C0600
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 002C01F8
.text C:\WINDOWS\System32\svchost.exe[1856] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 002C03FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!LdrLoadDll 7C91632D 5 Bytes JMP 001501F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!RtlDosSearchPath_U + 186 7C916865 1 Byte [62]
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ntdll.dll!LdrUnloadDll 7C9171CD 5 Bytes JMP 001503FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] kernel32.dll!GetBinaryTypeW + 80 7C868D8C 1 Byte [62]
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!SetServiceObjectSecurity 77E36D81 5 Bytes JMP 003E1014
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfigA 77E36E69 5 Bytes JMP 003E0804
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfigW 77E37001 5 Bytes JMP 003E0A08
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfig2A 77E37101 5 Bytes JMP 003E0C0C
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!ChangeServiceConfig2W 77E37189 5 Bytes JMP 003E0E10
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!CreateServiceA 77E37211 5 Bytes JMP 003E01F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!CreateServiceW 77E373A9 5 Bytes JMP 003E03FC
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] ADVAPI32.dll!DeleteService 77E374B1 5 Bytes JMP 003E0600
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 003F0804
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 003F0A08
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWindowsHookExA 7E431211 5 Bytes JMP 003F0600
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!SetWinEventHook 7E4317F7 5 Bytes JMP 003F01F8
.text C:\Documents and Settings\Mike\Desktop\gmer.exe[2096] USER32.dll!UnhookWinEvent 7E4318AC 5 Bytes JMP 003F03FC
---- User IAT/EAT - GMER 1.0.15 ----
IAT C:\WINDOWS\system32\services.exe[776] @ C:\WINDOWS\system32\services.exe [ADVAPI32.dll!CreateProcessAsUserW] 005E0002
IAT C:\WINDOWS\system32\services.exe[776] @ C:\WINDOWS\system32\services.exe [KERNEL32.dll!CreateProcessW] 005E0000
---- Devices - GMER 1.0.15 ----
AttachedDevice \FileSystem\Ntfs \Ntfs aswMon2.SYS (avast! File System Filter Driver for Windows XP/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Ip aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass0 IsDrv122.sys
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass1 IsDrv122.sys
AttachedDevice \Driver\Tcpip \Device\Tcp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\Udp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
AttachedDevice \Driver\Tcpip \Device\RawIp aswTdi.SYS (avast! TDI Filter Driver/AVAST Software)
---- EOF - GMER 1.0.15 ----
#28

 Posted 01 February 2012 - 09:10 PM
Posted 01 February 2012 - 09:10 PM

Close all programs so that you are at your desktop.
Double-click on the My Computer icon.
Select the Tools menu and click Folder Options.
After the new window appears select the View tab.
Put a checkmark in the checkbox labeled Display the contents of system folders.
Under the Hidden files and folders section select the radio button labeled Show hidden files and folders.
Remove the checkmark from the checkbox labeled Hide file extensions for known file types.
Remove the checkmark from the checkbox labeled Hide protected operating system files.
Press the Apply button and then the OK button and exit My Computer.
Now your computer is configured to show all hidden files.
Can you find this file?
C:\windows\System32\Drivers\IsDrv122.sys
If not, Start, Run, cmd, OK then type (with an Enter after each line)
(this creates a folder where the file is supposed to be hiding. If it is still hiding you will get an error.
[*]Extract RootRepeal.exe from the archive.
Right click on rootrepeal.zip and Extract All. Then move to the folder it created and find rootrepeal.exe and run it.
[*]Open on your desktop.
on your desktop.
[*]Click the tab.
tab.
[*]Click the button.
button.
[*]Check all seven boxes:
[*]Push Ok
[*]Check the box for your main system drive (Usually C:), and press Ok.
[*]Allow RootRepeal to run a scan of your system. This may take some time.
[*]Once the scan completes, push the button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your next reply, please.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your next reply, please.
[/list]
Double-click on the My Computer icon.
Select the Tools menu and click Folder Options.
After the new window appears select the View tab.
Put a checkmark in the checkbox labeled Display the contents of system folders.
Under the Hidden files and folders section select the radio button labeled Show hidden files and folders.
Remove the checkmark from the checkbox labeled Hide file extensions for known file types.
Remove the checkmark from the checkbox labeled Hide protected operating system files.
Press the Apply button and then the OK button and exit My Computer.
Now your computer is configured to show all hidden files.
Can you find this file?
C:\windows\System32\Drivers\IsDrv122.sys
If not, Start, Run, cmd, OK then type (with an Enter after each line)
cd \windows\system32\drivers
mkdir IsDrv122.sys
(this creates a folder where the file is supposed to be hiding. If it is still hiding you will get an error.
- Download RootRepeal from the following location and save it to your desktop.
- Zip Mirrors (Recommended)
http://ad13.geekstog.../RootRepeal.zip
http://rootrepeal.ps.../RootRepeal.zip
[*]Extract RootRepeal.exe from the archive.
Right click on rootrepeal.zip and Extract All. Then move to the folder it created and find rootrepeal.exe and run it.
[*]Open
[*]Click the
 tab.
tab.[*]Click the
 button.
button.[*]Check all seven boxes:

[*]Push Ok
[*]Check the box for your main system drive (Usually C:), and press Ok.
[*]Allow RootRepeal to run a scan of your system. This may take some time.
[*]Once the scan completes, push the
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your next reply, please.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your next reply, please.[/list]
#29

 Posted 02 February 2012 - 11:49 AM
Posted 02 February 2012 - 11:49 AM

ok. i changed the folder view profile and at first i could not find that file in the drivers. when i used command prompt i got, "A subdirectory or file IsDrv122.sys already exists". i rescanned the entire driver directory and i found it as a folder sitting at the very bottom of the directory underneath the system file list. however, when i opened the folder it was empty. i went back to the drivers folder and it had moved to the top with the rest of the folders and the date modified had changed to today's date. i read that this might be an icesword driver (although there is no driver as such).
i still am not able to locate the fsgk.sys file
the rootrepeal scan took about 1 sec.
here is the report
ROOTREPEAL © AD, 2007-2009
==================================================
Scan Start Time: 2012/02/02 12:35
Program Version: Version 1.3.5.0
Windows Version: Windows XP SP3
==================================================
Drivers
-------------------
Name: atapi.sys
Image Path: atapi.sys
Address: 0xF75F3000 Size: 96512 File Visible: - Signed: -
Status: Hidden from the Windows API!
Name: giveio.sys
Image Path: giveio.sys
Address: 0xF7C96000 Size: 1664 File Visible: No Signed: -
Status: -
Name: rootrepeal.sys
Image Path: C:\WINDOWS\system32\drivers\rootrepeal.sys
Address: 0xED13C000 Size: 49152 File Visible: No Signed: -
Status: -
Name: speedfan.sys
Image Path: speedfan.sys
Address: 0xF795E000 Size: 16640 File Visible: No Signed: -
Status: -
SSDT
-------------------
#: 009 Function Name: NtAddBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993fc4
#: 017 Function Name: NtAllocateVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a20510
#: 025 Function Name: NtClose
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b76a9
#: 035 Function Name: NtCreateEvent
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996456
#: 036 Function Name: NtCreateEventPair
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964ae
#: 038 Function Name: NtCreateIoCompletion
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29965c4
#: 041 Function Name: NtCreateKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b705d
#: 043 Function Name: NtCreateMutant
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29963ac
#: 050 Function Name: NtCreateSection
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964fe
#: 051 Function Name: NtCreateSemaphore
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996400
#: 054 Function Name: NtCreateTimer
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996572
#: 061 Function Name: NtDeleteBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993fe8
#: 063 Function Name: NtDeleteKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7d6f
#: 065 Function Name: NtDeleteValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b8025
#: 068 Function Name: NtDuplicateObject
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996848
#: 071 Function Name: NtEnumerateKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7bda
#: 073 Function Name: NtEnumerateValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7a45
#: 083 Function Name: NtFreeVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a205c0
#: 097 Function Name: NtLoadDriver
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993db2
#: 109 Function Name: NtModifyBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299400c
#: 111 Function Name: NtNotifyChangeKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29969bc
#: 112 Function Name: NtNotifyChangeMultipleKeys
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994aa4
#: 114 Function Name: NtOpenEvent
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996486
#: 115 Function Name: NtOpenEventPair
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964d6
#: 117 Function Name: NtOpenIoCompletion
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29965ee
#: 119 Function Name: NtOpenKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b73b9
#: 120 Function Name: NtOpenMutant
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29963d8
#: 122 Function Name: NtOpenProcess
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996680
#: 125 Function Name: NtOpenSection
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299653e
#: 126 Function Name: NtOpenSemaphore
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299642e
#: 128 Function Name: NtOpenThread
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996764
#: 131 Function Name: NtOpenTimer
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299659c
#: 137 Function Name: NtProtectVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a20658
#: 160 Function Name: NtQueryKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b78c0
#: 163 Function Name: NtQueryObject
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299496a
#: 177 Function Name: NtQueryValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7712
#: 192 Function Name: NtRenameKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a289e6
#: 204 Function Name: NtRestoreKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b66d0
#: 211 Function Name: NtSetBootEntryOrder
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994030
#: 212 Function Name: NtSetBootOptions
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994054
#: 240 Function Name: NtSetSystemInformation
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993e0c
#: 241 Function Name: NtSetSystemPowerState
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f48
#: 247 Function Name: NtSetValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7e76
#: 249 Function Name: NtShutdownSystem
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f24
#: 255 Function Name: NtSystemDebugControl
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f6c
#: 268 Function Name: NtVdmControl
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994078
==EOF==
i still am not able to locate the fsgk.sys file
the rootrepeal scan took about 1 sec.
here is the report
ROOTREPEAL © AD, 2007-2009
==================================================
Scan Start Time: 2012/02/02 12:35
Program Version: Version 1.3.5.0
Windows Version: Windows XP SP3
==================================================
Drivers
-------------------
Name: atapi.sys
Image Path: atapi.sys
Address: 0xF75F3000 Size: 96512 File Visible: - Signed: -
Status: Hidden from the Windows API!
Name: giveio.sys
Image Path: giveio.sys
Address: 0xF7C96000 Size: 1664 File Visible: No Signed: -
Status: -
Name: rootrepeal.sys
Image Path: C:\WINDOWS\system32\drivers\rootrepeal.sys
Address: 0xED13C000 Size: 49152 File Visible: No Signed: -
Status: -
Name: speedfan.sys
Image Path: speedfan.sys
Address: 0xF795E000 Size: 16640 File Visible: No Signed: -
Status: -
SSDT
-------------------
#: 009 Function Name: NtAddBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993fc4
#: 017 Function Name: NtAllocateVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a20510
#: 025 Function Name: NtClose
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b76a9
#: 035 Function Name: NtCreateEvent
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996456
#: 036 Function Name: NtCreateEventPair
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964ae
#: 038 Function Name: NtCreateIoCompletion
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29965c4
#: 041 Function Name: NtCreateKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b705d
#: 043 Function Name: NtCreateMutant
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29963ac
#: 050 Function Name: NtCreateSection
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964fe
#: 051 Function Name: NtCreateSemaphore
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996400
#: 054 Function Name: NtCreateTimer
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996572
#: 061 Function Name: NtDeleteBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993fe8
#: 063 Function Name: NtDeleteKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7d6f
#: 065 Function Name: NtDeleteValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b8025
#: 068 Function Name: NtDuplicateObject
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996848
#: 071 Function Name: NtEnumerateKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7bda
#: 073 Function Name: NtEnumerateValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7a45
#: 083 Function Name: NtFreeVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a205c0
#: 097 Function Name: NtLoadDriver
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993db2
#: 109 Function Name: NtModifyBootEntry
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299400c
#: 111 Function Name: NtNotifyChangeKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29969bc
#: 112 Function Name: NtNotifyChangeMultipleKeys
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994aa4
#: 114 Function Name: NtOpenEvent
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996486
#: 115 Function Name: NtOpenEventPair
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29964d6
#: 117 Function Name: NtOpenIoCompletion
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29965ee
#: 119 Function Name: NtOpenKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b73b9
#: 120 Function Name: NtOpenMutant
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29963d8
#: 122 Function Name: NtOpenProcess
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996680
#: 125 Function Name: NtOpenSection
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299653e
#: 126 Function Name: NtOpenSemaphore
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299642e
#: 128 Function Name: NtOpenThread
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2996764
#: 131 Function Name: NtOpenTimer
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299659c
#: 137 Function Name: NtProtectVirtualMemory
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a20658
#: 160 Function Name: NtQueryKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b78c0
#: 163 Function Name: NtQueryObject
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf299496a
#: 177 Function Name: NtQueryValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7712
#: 192 Function Name: NtRenameKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSP.SYS" at address 0xf2a289e6
#: 204 Function Name: NtRestoreKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b66d0
#: 211 Function Name: NtSetBootEntryOrder
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994030
#: 212 Function Name: NtSetBootOptions
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994054
#: 240 Function Name: NtSetSystemInformation
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993e0c
#: 241 Function Name: NtSetSystemPowerState
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f48
#: 247 Function Name: NtSetValueKey
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf29b7e76
#: 249 Function Name: NtShutdownSystem
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f24
#: 255 Function Name: NtSystemDebugControl
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2993f6c
#: 268 Function Name: NtVdmControl
Status: Hooked by "C:\WINDOWS\System32\Drivers\aswSnx.SYS" at address 0xf2994078
==EOF==
#30

 Posted 02 February 2012 - 12:33 PM
Posted 02 February 2012 - 12:33 PM

An empty folder is good. That's what we want.
No other sign of any rootkit as far as I can tell. All of the hooks seem to belong to Avast.
About all we can do now to get Combofix to run is to burn a copy of Hiren's CD and boot from it.
http://www.hirensbootcd.org/download/
This a BIG! Zip File so save it. Then right click on it and Extract all. Put a blank CD in the drive and then double click on BurnToCD.cmd. When it finishes you boot off it (you may have to change the boot order in the BIOS in order to get it to boot) and run the MiniXP program. This will give you a fake XP desktop. I think Hirens has a copy of Combofix on it or you can try and find george.exe and run it.
No other sign of any rootkit as far as I can tell. All of the hooks seem to belong to Avast.
About all we can do now to get Combofix to run is to burn a copy of Hiren's CD and boot from it.
http://www.hirensbootcd.org/download/
This a BIG! Zip File so save it. Then right click on it and Extract all. Put a blank CD in the drive and then double click on BurnToCD.cmd. When it finishes you boot off it (you may have to change the boot order in the BIOS in order to get it to boot) and run the MiniXP program. This will give you a fake XP desktop. I think Hirens has a copy of Combofix on it or you can try and find george.exe and run it.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:
















 Sign In
Sign In Create Account
Create Account

