By other user do you mean the new user account or did you run javara under the original user account?
Win 7 security virus, removal help needed! [Closed] [Solved]
Started by
pa.pete
, Jan 27 2012 11:33 AM
#76
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #76](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 16 March 2012 - 10:31 AM
Posted 16 March 2012 - 10:31 AM

By other user do you mean the new user account or did you run javara under the original user account?
#77
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #77](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 16 March 2012 - 02:48 PM
Posted 16 March 2012 - 02:48 PM

I mean the new user logon I created on my computer.
Pete
Pete
#78
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #78](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 March 2012 - 07:46 AM
Posted 17 March 2012 - 07:46 AM

Hello Pete,
There are some folders I want to take a look inside. Also it appears that the permissions for the Event logs weren't the only permissions that the malware messed with. You will probably continue to have issues where the old user account won't be able to run something, like the JavaRa.exe file that you had to run from the new account. There is a registry fix that you can merge into the registry that will will put a "Take Ownership" option on the right click menu so that when you can't run a file, you can right click on it and click the "Take Ownership" option and run the file that way.
But to get all of the permissions reset, the easiest thing would probably be to transfer all of your files from the old user account to the new one, then delete the old user account. Let me know what you want to do.
The last OTL log showed some new folders that I want to look in.
Step-1.
 OTL Custom Scan
OTL Custom Scan
1. Please copy the text in the code box below and paste it in the box in OTL. To do that:
box in OTL. To do that:
2. Re-open OTL on the desktop. To do that:
Step-2.
Run Revo Uninstaller
Run Revo Uninstaller again.
Step-3.
Things For Your Next Post:
1. The OTL.txt log
There are some folders I want to take a look inside. Also it appears that the permissions for the Event logs weren't the only permissions that the malware messed with. You will probably continue to have issues where the old user account won't be able to run something, like the JavaRa.exe file that you had to run from the new account. There is a registry fix that you can merge into the registry that will will put a "Take Ownership" option on the right click menu so that when you can't run a file, you can right click on it and click the "Take Ownership" option and run the file that way.
But to get all of the permissions reset, the easiest thing would probably be to transfer all of your files from the old user account to the new one, then delete the old user account. Let me know what you want to do.
The last OTL log showed some new folders that I want to look in.
Step-1.
1. Please copy the text in the code box below and paste it in the
 box in OTL. To do that:
box in OTL. To do that:- Highlight everything inside the code box, right click the mouse and click Copy.
C:\1dfe74114c20be64c80762d23588 C:\1376ce827bcf38df0a3b331e C:\73c51549210326fc41cf70d0 C:\4d2becf2886af8a0f6a48fa2f285 C:\d37e51664a70a5aa217a0fe5 C:\5e446f905e7c4252a90e8751bf1cb7
2. Re-open OTL on the desktop. To do that:
- Double click on the
 OTL icon to run it. Make sure all other windows are closed.
OTL icon to run it. Make sure all other windows are closed. - You will see a console like the one below:
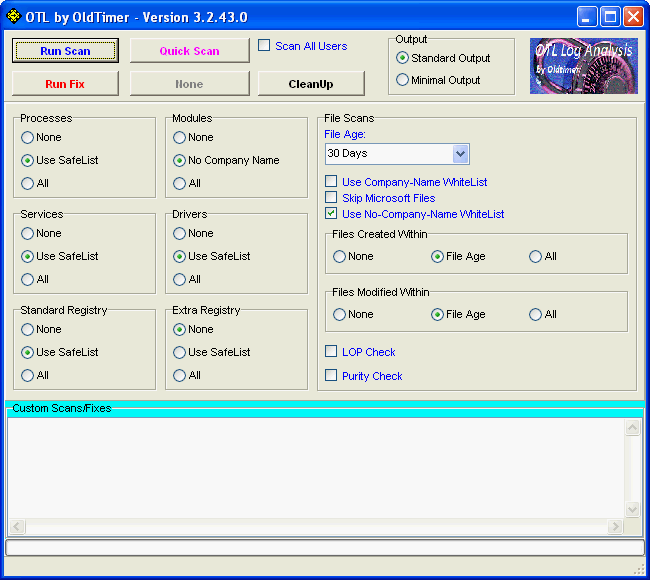
- Click the greyed out None button at the top of the console.<---Important
- Place the mouse pointer inside the
 box, right click and click Paste. This will put the above script inside OTL
box, right click and click Paste. This will put the above script inside OTL - Click the
 button. Do not change any settings unless otherwise told to do so.
button. Do not change any settings unless otherwise told to do so. - Let the scan run uninterrupted. The scan won't take long.
- When the scan completes, it will open OTL.Txt. This file is also saved in the same location as OTL (it should be on your desktop).
- Please copy the contents of this file and paste it into your reply.
Step-2.
Run Revo Uninstaller
Run Revo Uninstaller again.
- Double click ( Vista/7 users may need to right click the file and click Run as Administrator) the Revo Uninstaller Icon on the desktop to start the program.
You will now see a list of installed programs that Revo Uninstaller can remove.
- Locate the program you are uninstalling
Java6 Update 26
Java6 Update 3 - Right Click the program Icon then choose Uninstall.
- Click yes to the warning and choose the Uninstall Mode
- Choose the Advanced option and then click Next.
- This will launch the programs built in uninstaller. Be patient it can take several seconds.
- Once the Uninstaller is done click Next.
- Revo Uninstaller will now scan for leftover information. Be patient it can take several seconds.
- Once this scan is done click Next.
- You will then be presented with the leftover entries found by Revo Uninstaller
- Click any bolded boxes that relate to the programs above.
- Look at ALL of the entries to ensure they relate to the uninstall.
- Next click Delete to remove the entries.
- Click Next.
- If there are any program file folders left over you will be presented with a list to be removed.
- Again look at ALL of the entries to ensure they are related to the uninstall.
- Click Select All > Delete to remove the entries.
- Click Finish to go back to the uninstall list.
- Close the program
Step-3.
Things For Your Next Post:
1. The OTL.txt log
#79
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #79](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 19 March 2012 - 12:13 PM
Posted 19 March 2012 - 12:13 PM

godawgs,
If the easiest thing to do is to delete the old logon that is fine with me. I am not sure how to transfer the files though?
Pete
OTL logfile created on: 3/19/2012 1:45:20 PM - Run 12
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Users\Radwick\Desktop
64bit- Home Premium Edition (Version = 6.1.7600) - Type = NTWorkstation
Internet Explorer (Version = 9.0.8112.16421)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.75 Gb Total Physical Memory | 2.39 Gb Available Physical Memory | 63.78% Memory free
7.49 Gb Paging File | 5.12 Gb Available in Paging File | 68.26% Paging File free
Paging file location(s): ?:\pagefile.sys [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\Windows | %ProgramFiles% = C:\Program Files (x86)
Drive C: | 453.94 Gb Total Space | 277.98 Gb Free Space | 61.24% Space Free | Partition Type: NTFS
Computer Name: RADWICK-PC | User Name: Radwick | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Include 64bit Scans
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: Off | File Age = 30 Days
========== Custom Scans ==========
< C:\1dfe74114c20be64c80762d23588 >
< C:\1376ce827bcf38df0a3b331e >
< C:\73c51549210326fc41cf70d0 >
< C:\4d2becf2886af8a0f6a48fa2f285 >
< C:\d37e51664a70a5aa217a0fe5 >
< C:\5e446f905e7c4252a90e8751bf1cb7 >
< End of report >
If the easiest thing to do is to delete the old logon that is fine with me. I am not sure how to transfer the files though?
Pete
OTL logfile created on: 3/19/2012 1:45:20 PM - Run 12
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Users\Radwick\Desktop
64bit- Home Premium Edition (Version = 6.1.7600) - Type = NTWorkstation
Internet Explorer (Version = 9.0.8112.16421)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
3.75 Gb Total Physical Memory | 2.39 Gb Available Physical Memory | 63.78% Memory free
7.49 Gb Paging File | 5.12 Gb Available in Paging File | 68.26% Paging File free
Paging file location(s): ?:\pagefile.sys [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\Windows | %ProgramFiles% = C:\Program Files (x86)
Drive C: | 453.94 Gb Total Space | 277.98 Gb Free Space | 61.24% Space Free | Partition Type: NTFS
Computer Name: RADWICK-PC | User Name: Radwick | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Include 64bit Scans
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: Off | File Age = 30 Days
========== Custom Scans ==========
< C:\1dfe74114c20be64c80762d23588 >
< C:\1376ce827bcf38df0a3b331e >
< C:\73c51549210326fc41cf70d0 >
< C:\4d2becf2886af8a0f6a48fa2f285 >
< C:\d37e51664a70a5aa217a0fe5 >
< C:\5e446f905e7c4252a90e8751bf1cb7 >
< End of report >
#80
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #80](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 March 2012 - 05:08 PM
Posted 20 March 2012 - 05:08 PM

Hi Pete,
Below are instructions for transferring the data from one user profile to another. After this is done, we are going to leave both profiles on the system until after cleanup. Then you can remove the old profile.
If you don't understand something or have any questions ask them Before beginning
You should print these instructions out before starting so you will have them to refer to.
Instructions for transferring data to the new user account.
Create a New User Account
Transfer Corrupted User's Files
Below are instructions for transferring the data from one user profile to another. After this is done, we are going to leave both profiles on the system until after cleanup. Then you can remove the old profile.
If you don't understand something or have any questions ask them Before beginning
You should print these instructions out before starting so you will have them to refer to.
Instructions for transferring data to the new user account.
Create a New User Account
- Log in to Windows with your administrator account or as a user who has been given administrator privileges.
- Click the Start button (the Windows logo button in Windows 7). Click Control Panel.
- In Windows 7, click User Accounts and Family Safety,then Add or remove user accounts and click Create a new account.
- Type Test as the name for the new user account. Select the account type--"Administrator". Click Create Account
Transfer Corrupted User's Files
- Log in to Windows with the Test user account.
- Click the Start Orb. Click Computer
- On the Computer page click Tools at the top of the page and click Folder Options.
- On the Folder Options page click the View tab.
- In the Advanced Settings box under Files and Folders click the button beside Show Hidden Files and Folders and clear the Hide protected operating system files (Recommended) check box. Click Yes in the confirmation message and then click OK.
- Back on the Computer window, double-click the primary drive of your computer (usually the "C:" drive).
- Double-click Users folder.
- Double-click the corrupted Windows user's folder,(This should be the C:\Usesr\Radwick folder),to show its contents in the right side of the window.
- NOTE: If you get a warning that you don't have permissions to access that page, click Continue and you will be given access.
- Click the first file or folder listed at the top of the list in the corrupted user's folder. Press and hold the Shift keyboard key. Scroll to the bottom of the corrupted user's folder. Click the last file or folder in the list to simultaneously select it and all the rest of the files. Release the Shift key.
- Press and hold the Ctrl keyboard key. Click on the Ntuser.dat, Ntuser.dat.log and Ntuser.ini files to deselect them. Release the Ctrl button. Right-click the selected and highlighted files. Click Copy.
- NOTE: There may be more than one Ntuser.dat.log file. Deselect them all.
- At the top of the Computer window, click the back arrow. Right-click the new user's name,(This should be peteradwick),
- NOTE: If you get a warning that you don't have permissions to access that page, click Continue and you will be given access.
- NOTE: When you get the warning asking if you want to overwrite the file or folder, check the box to allow all files/folders to be overwritten.
- Log off of the Windows Test account. Log onto Windows as the new user (peteradwick).
- Open the Control Panel and under User Accounts and Family Safety click Add or remove user accounts.
- Click the Test account and click Delete the account from the list on the left.
#81
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #81](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 March 2012 - 10:47 AM
Posted 23 March 2012 - 10:47 AM

godawgs,
I should be able to get to this tonight.
Sorry for the delay,
Pete
I should be able to get to this tonight.
Sorry for the delay,
Pete
#82
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #82](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 March 2012 - 11:05 AM
Posted 23 March 2012 - 11:05 AM

#83
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #83](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2012 - 09:19 AM
Posted 24 March 2012 - 09:19 AM

godawgs,
I followed your instructions to transfer everything and it seems to work fine, but it didn't transfer everything on the desktop.
One thing I did notice on the desktop is something called Dailybiblebak, I have no idea what that is so I didn't click on it.
Pete
I followed your instructions to transfer everything and it seems to work fine, but it didn't transfer everything on the desktop.
One thing I did notice on the desktop is something called Dailybiblebak, I have no idea what that is so I didn't click on it.
Pete
#84
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #84](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2012 - 09:36 AM
Posted 24 March 2012 - 09:36 AM

One thing I did notice on the desktop is something called Dailybiblebak, I have no idea what that is so I didn't click on it.
Which desktop? The old one or the new one?
What didn't it transfer from the old desktop?
Edited by godawgs, 24 March 2012 - 09:39 AM.
#85
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #85](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2012 - 09:58 AM
Posted 24 March 2012 - 09:58 AM

The new desktop, I think it is mostly files that I had save to the desktop that are missing.
#86
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #86](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2012 - 10:39 AM
Posted 24 March 2012 - 10:39 AM

OK. We're going to have to do a cleanup for both users. It should remove all of that. After that is done and everything is still working OK you can delete the old user account. I will be back with those instructions. Right now I gotta go bush hog and rake sweetgum balls....such fun!!!
#87
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #87](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2012 - 03:52 PM
Posted 24 March 2012 - 03:52 PM

When ever you get time is fine with me. I have to do Trig homework and study for a test anyway, I think I would rather bush hog and rake sweet gum balls!
Pete
Pete
#88
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #88](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2012 - 12:17 PM
Posted 25 March 2012 - 12:17 PM

Hey Pete,
I think we have reached the point you were looking for.
OK! Well done. Here is the best part of the process! The mullygrubs are gone! That's a technical term for your log(s) appear to be clean! If you have no further issues with your computer, please proceed with the housekeeping procedures outlined below.
Here is the best part of the process! The mullygrubs are gone! That's a technical term for your log(s) appear to be clean! If you have no further issues with your computer, please proceed with the housekeeping procedures outlined below.
The first thing we need to do is to remove all the tools that we have used. This is so that should you ever be re-infected, you will download updated versions.
Please log into the Radwick user account
Step-1.
We need to uninstall some programs.
Program Uninstalls
1. Click the Start Orb, click Control Panel. Under the Programs heading click Uninstall a program
2. In the list of programs installed, locate the following program(s):
ESET Online Scanner
Revo Uninstaller
3. Click on each program to highlight it and click Uninstall
4. After the program(s) have been uninstalled, close the Installed Programs window and the Control Panel.
5. Reboot the computer.
Delete the folders associated with the uninstalled programs.
1. Using Windows Explorer (to get there right-click your Start button and click "Explore"), please delete the following folders(s) in red (if present):
C:\Program Files (x86)\ESET
C:\Program Files (x86)\Revo Uninstaller
2. Close Windows Explorer.
Step-2.
OTL Cleanup
1. Please copy all of the text in the code box below. To do this, highlight everything inside the code box , right click and click Copy. on your desktop.
on your desktop.
Now log into the peteradwick user account.
Step-1.
Unhide File Extensions
Delete the following files from the desktop (if present):
javara.zip
javara folder
java_files.jpg
JavaRa.zip.asaq8lr.partial
JavaRa.zip.1yujzdi.partial
RogueKiller.htm
aswmbr.exe
mbr.dat
gooredfix.exe
gooredfix.txt
gooredfix backups
mbam--setup-1.60.1.1000.exe
dailybiblebak.reg
Delete any other .bat, .log, .reg, .txt, and any other files created during this process, and left on the desktop and empty the Recycle Bin.
When this is done, please use the computer for another day or two and if everything is OK you can delete the Radwick user account.
Preventing Re-Infection
Below, I have included a number of recommendations for how to protect your computer against future malware infections.
:Keep Windows Updated:-Windows Updates are constantly being revised to combat the newest hacks and threats, Microsoft releases security updates that help your computer from becoming vulnerable. It is best if you have these set to download automatically.
Vista and Windows 7 Users:
1. Click Start> All Programs, from the list find Windows Update and click it.
:Turn On Automatic Updates:
Vista and Windows 7
1. Click Start> Control Panel. Click Security. Under Windows Update, Click Turn automatic on or off.
2. On the next page, under Important Updates, Click the Drop down arrow on the right side of the box and Click Install Updates Automatically(recommended).
If you click this setting, click to select the day and time for scheduled updates to occur. You can schedule Automatic Updates for any time of day. Remember, your computer must be on at the scheduled time for updates to be installed. After you set this option, Windows recognizes when you are online and uses your Internet connection to find updates on the Windows Update Web site or on the Microsoft Update Web site that apply to your computer. Updates are downloaded automatically in the background, and you are not notified or interrupted during this process. An icon appears in the notification area of your task bar when the updates are being downloaded. You can point to the icon to view the download status. To pause or to resume the download, right-click the icon, and then click Pause or Resume. When the download is completed, another message appears in the notification area so that you can review the updates that are scheduled for installation. If you choose not to install at that time, Windows starts the installation on your set schedule.
: Keep Java Updated :
:Web Browsers:
:Make your Internet Explorer more secure:
1. From within Internet Explorer click on the Tools menu and then click on Options.
2. Click once on the Security tab
3. Click once on the Internet icon so it becomes highlighted.
4. Click once on the Custom Level button.
5. Change the Download signed ActiveX controls to "Prompt"
6. Change the Download unsigned ActiveX controls to "Disable"
7. Change the Initialise and script ActiveX controls not marked as safe to "Disable"
8. Change the Installation of desktop items to "Prompt"
9. Change the Launching programs and files in an IFRAME to "Prompt"
10. When all these settings have been made, click on the OK button.
11. If it prompts you as to whether or not you want to save the settings, click the Yes button.
12. Next press the Apply button and then the OK to exit the Internet Properties page.
:Alternate Browsers:
Using an alternative web browser can help protect your PC from infections which exploit security holes within Internet Explorer. They can also be quicker to load pages and offer more tools and features such as Firefox's huge addon list.
Mozilla's Firefox browser is fantastic; it is much more secure than Internet Explorer, immune to almost all known browser hijackers, and also has a great built-in pop up blocker. If you are interested, Click Here To Download Firefox
If you choose to use Firefox, I highly recommend these add-ons to keep your PC even more secure.
Preventative programs that will help to keep the nasties away! We will start with Anti Spyware programs. I would advise getting a couple of them at least, and running a full scan at least once a month. Run Quick Scans at least once a week. Download the Free versions. And update the definitions before running scans.
========Anti Spyware========
It's a good idea to clear out all your temp files every now and again. This will help your computer from bogging down and slowing. It also can assist in getting rid of files that may contain malicious code that could re-infect your computer.
========TEMP File Cleaners========
:Keep Installed Programs Up to Date:
Secunia Software Inspector-It is also possible for other programs on your computer to have security vulnerability that can allow malware to infect you. Therefore, it is also a good idea to check for the latest versions of commonly installed applications that are regularly patched to fix vulnerabilities.
Finally, please read How did I Get Infected in the First Place(by Mr. Tony Klein and dvk01)
I'd be grateful if you could reply to this post so that I know you have read it and, if you've no other questions, the thread can then be closed.
I Will Keep This Open For About Four Days, If Anything Comes Up - Just Come Back And Let Me Know
godawgs
I think we have reached the point you were looking for.
OK! Well done.
The first thing we need to do is to remove all the tools that we have used. This is so that should you ever be re-infected, you will download updated versions.
Please log into the Radwick user account
Step-1.
We need to uninstall some programs.
Program Uninstalls
1. Click the Start Orb, click Control Panel. Under the Programs heading click Uninstall a program
2. In the list of programs installed, locate the following program(s):
ESET Online Scanner
Revo Uninstaller
3. Click on each program to highlight it and click Uninstall
4. After the program(s) have been uninstalled, close the Installed Programs window and the Control Panel.
5. Reboot the computer.
Delete the folders associated with the uninstalled programs.
1. Using Windows Explorer (to get there right-click your Start button and click "Explore"), please delete the following folders(s) in red (if present):
C:\Program Files (x86)\ESET
C:\Program Files (x86)\Revo Uninstaller
2. Close Windows Explorer.
Step-2.
OTL Cleanup
1. Please copy all of the text in the code box below. To do this, highlight everything inside the code box , right click and click Copy.
:COMMANDS [EMPTYTEMP] [CLEARALLRESTOREPOINTS]
- Please re-open
 on your desktop.
on your desktop. - Place the mouse pointer inside the
 textbox, right click and click Paste. This will put the above script inside the textbox.
textbox, right click and click Paste. This will put the above script inside the textbox. - Click the
 button.
button. - Let the program run unhindered. When finished click the OK button and close the log that appears.
- NOTE: I do not need to review the log produced.
- OTL may ask to reboot the machine. Please do so if asked.
- Be sure all other programs are closed as this step will require a reboot.
- Click on

- You will be prompted to reboot your system. Please do so.
Now log into the peteradwick user account.
Step-1.
Unhide File Extensions
- Click the Start Orb. Click Computer.
- On the next window, at the top of the window, click Tools then click Folder Options.
- On the Folder Options window click the View tab.
- Under the Files and Folders section:
- Make sure the Hide extensions for known file types box is un-checked.

Delete the following files from the desktop (if present):
javara.zip
javara folder
java_files.jpg
JavaRa.zip.asaq8lr.partial
JavaRa.zip.1yujzdi.partial
RogueKiller.htm
aswmbr.exe
mbr.dat
gooredfix.exe
gooredfix.txt
gooredfix backups
mbam--setup-1.60.1.1000.exe
dailybiblebak.reg
Delete any other .bat, .log, .reg, .txt, and any other files created during this process, and left on the desktop and empty the Recycle Bin.
When this is done, please use the computer for another day or two and if everything is OK you can delete the Radwick user account.
Preventing Re-Infection
Below, I have included a number of recommendations for how to protect your computer against future malware infections.
:Keep Windows Updated:-Windows Updates are constantly being revised to combat the newest hacks and threats, Microsoft releases security updates that help your computer from becoming vulnerable. It is best if you have these set to download automatically.
Vista and Windows 7 Users:
1. Click Start> All Programs, from the list find Windows Update and click it.
:Turn On Automatic Updates:
Vista and Windows 7
1. Click Start> Control Panel. Click Security. Under Windows Update, Click Turn automatic on or off.
2. On the next page, under Important Updates, Click the Drop down arrow on the right side of the box and Click Install Updates Automatically(recommended).
If you click this setting, click to select the day and time for scheduled updates to occur. You can schedule Automatic Updates for any time of day. Remember, your computer must be on at the scheduled time for updates to be installed. After you set this option, Windows recognizes when you are online and uses your Internet connection to find updates on the Windows Update Web site or on the Microsoft Update Web site that apply to your computer. Updates are downloaded automatically in the background, and you are not notified or interrupted during this process. An icon appears in the notification area of your task bar when the updates are being downloaded. You can point to the icon to view the download status. To pause or to resume the download, right-click the icon, and then click Pause or Resume. When the download is completed, another message appears in the notification area so that you can review the updates that are scheduled for installation. If you choose not to install at that time, Windows starts the installation on your set schedule.
: Keep Java Updated :
- Click the Start button
- Click Control Panel
- Double Click Java - Looks like a coffee cup. You may have to switch to Classical View on the upper left of the Control Panel to see it.
- Click the Update tab
- Click Update Now
- Allow any updates to be downloaded and installed
- Open Adobe Reader
- Click Help on the menu at the top
- Click Check for Updates
- Allow any updates to be downloaded and installed
:Web Browsers:
:Make your Internet Explorer more secure:
1. From within Internet Explorer click on the Tools menu and then click on Options.
2. Click once on the Security tab
3. Click once on the Internet icon so it becomes highlighted.
4. Click once on the Custom Level button.
5. Change the Download signed ActiveX controls to "Prompt"
6. Change the Download unsigned ActiveX controls to "Disable"
7. Change the Initialise and script ActiveX controls not marked as safe to "Disable"
8. Change the Installation of desktop items to "Prompt"
9. Change the Launching programs and files in an IFRAME to "Prompt"
10. When all these settings have been made, click on the OK button.
11. If it prompts you as to whether or not you want to save the settings, click the Yes button.
12. Next press the Apply button and then the OK to exit the Internet Properties page.
:Alternate Browsers:
Using an alternative web browser can help protect your PC from infections which exploit security holes within Internet Explorer. They can also be quicker to load pages and offer more tools and features such as Firefox's huge addon list.
Mozilla's Firefox browser is fantastic; it is much more secure than Internet Explorer, immune to almost all known browser hijackers, and also has a great built-in pop up blocker. If you are interested, Click Here To Download Firefox
If you choose to use Firefox, I highly recommend these add-ons to keep your PC even more secure.
- NoScript - for blocking ads and other potential website attacks
- WebOfTrust - a safe surfing tool for your browser. Traffic-light rating symbols show which websites you can trust when you search, shop and surf on the Web.
- McAfee SiteAdvisor - this tells you whether the sites you are about to visit are safe or not. A must if you do a lot of Googling
- MVPS Hosts file-replaces your current HOSTS file with one containing well known ad sites and other bad sites. Basically, this prevents your computer from connecting to those sites by redirecting them to 127.0.0.1 which is your local computer, meaning it will be difficult to infect yourself in the future.
Preventative programs that will help to keep the nasties away! We will start with Anti Spyware programs. I would advise getting a couple of them at least, and running a full scan at least once a month. Run Quick Scans at least once a week. Download the Free versions. And update the definitions before running scans.
========Anti Spyware========
- Malwarebytes-Free Version- a powerful tool to search for and eliminate malware found on your computer.
- SpywareBlaster-to help prevent spyware from installing in the first place. A tutorial can be found here.
- SpywareGuard-to catch and block spyware before it can execute. A tutorial can be found here.
- WinPatrol - will alert you to hijackings, malware attacks and critical changes made to your computer without your permission. Help file and tutorial can be found here.
- IESpy-Ad-to block access to malicious websites so you cannot be redirected to them from an infected site or email. A tutorial can be found here.
It's a good idea to clear out all your temp files every now and again. This will help your computer from bogging down and slowing. It also can assist in getting rid of files that may contain malicious code that could re-infect your computer.
========TEMP File Cleaners========
- TFC by OldTimer-A very powerful cleaning program for 32 and 64 bit OS. Note: You may have this already as part of the fixes you have run.
- CleanUP-Click the Download CleanUP! link. There is also a Learn how to use CleanUP! link on this page.
- Keep a backup of your important files.-Now, more than ever, it's especially important to protect your digital files and memories. This article is full of good information on alternatives for home backup solutions.
- ERUNT-(Emergency Recovery Utility NT) allows you to keep a complete backup of your registry and restore it when needed. The standard registry backup options that come with Windows back up most of the registry but not all of it. ERUNT however creates a complete backup set, including the Security hive and user related sections. ERUNT is easy to use and since it creates a full backup, there are no options or choices other than to select the location of the backup files. The backup set includes a small executable that will launch the registry restore if needed.
:Keep Installed Programs Up to Date:
Secunia Software Inspector-It is also possible for other programs on your computer to have security vulnerability that can allow malware to infect you. Therefore, it is also a good idea to check for the latest versions of commonly installed applications that are regularly patched to fix vulnerabilities.
Finally, please read How did I Get Infected in the First Place(by Mr. Tony Klein and dvk01)
I'd be grateful if you could reply to this post so that I know you have read it and, if you've no other questions, the thread can then be closed.
I Will Keep This Open For About Four Days, If Anything Comes Up - Just Come Back And Let Me Know
godawgs
#89
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #89](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 26 March 2012 - 04:58 PM
Posted 26 March 2012 - 04:58 PM

godawgs,
I might need a couple of extra days to finish this.
Pete
I might need a couple of extra days to finish this.
Pete
#90
![Win 7 security virus, removal help needed! [Closed] [Solved]: post #90](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 26 March 2012 - 09:10 PM
Posted 26 March 2012 - 09:10 PM

Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

