Step 1.Insert the
USB drive into the ailing computer. Run
FRST as you did before,
except that this time around
click on the
Scan button. It will produce a new
FRST.txt log. Please post it in your next reply.
Step 2.Several of your file associations were corrupted by the malware and in order to run our tools we will need to correct the registry.
On the good computer go to this
site.
You will see several file association fixes for Windows 7.
To fix the associations for
EXE,
COM. and
SCR file types:
1. Download the corresponding fix from the table. (Use Right-click – Save as option in your browser to download the fixes.)
2. Unzip the files and extract the .REG files to the Desktop of your good computer.
3. Copy the
three .REG files onto your USB drive.
4. Plug the USB drive in your ailing computer and boot up as you did before but instead of running the FRST64, at the command prompt type:
regedit5. The registry editor will appear on your screen.
6. Click
File >>
Import... 7. An Import Registry File window will open. Click the
down arrow to the
right of the Look in: window
8. Select Removable Disk (what ever drive letter yours is)
9. Click on each file and then the Open button and confirm you want to import the file. Repeat this step for all three .REG files.
10. Close the registry windows. Close the black command prompt window.
11. Restart the ailing computer in normal mode.
Step 2.Insert the USB drive in the ailing computer and copy
RogueKiller to the desktop.
Try to run it. If it does not run post the log above, skip the remaining steps, and let me know.
If it runs do these steps:
- Quit all programs
- Start RogueKiller.exe.
- Wait until Prescan has finished ...
- Click on the Scan button Step 1 in the picture.
- Note: If RogueKiller will not run please try it several times, if it still does not run rename it winlogon.com and try it several times.
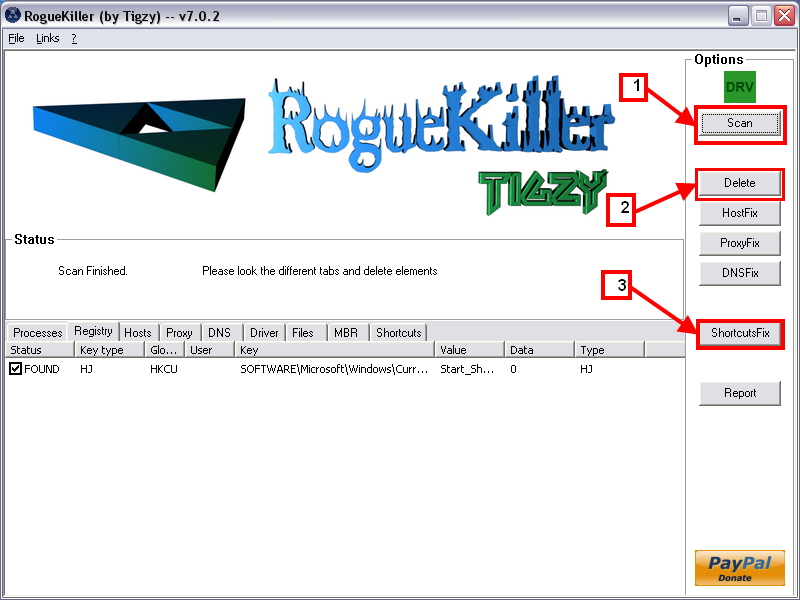
- Wait for the end of the scan.
- The first report will be created on the desktop.
- Click on the Delete button step 2 in the picture.
- The second report will be created on the desktop.
- Next click on ShortcutsFix step 3 in the picture.
- The third report will be created on the desktop.
Please post:
All RKreport.txt text files located on your desktop.
Step 3.Copy Combofix from the USB drive to the ailing computer desktop.
*
IMPORTANT -
Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link
here - Double click on ComboFix.exe & follow the prompts.
- Accept the disclaimer and allow to update if it asks
- When finished, it shall produce a log for you.
- Please include the C:\ComboFix.txt in your next reply.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions.
3. If after the reboot you get errors about programmes being marked for deletion then reboot, that will cure it.
Please make sure you include the Combofix log in your next reply as well as describe how your computer is running nowStep 4.Please post:FRST.txtif they can run post:All RKreport.txt files
ComboFix.txtGive me an update on how the computer is running















 scan.txt 617bytes
468 downloads
scan.txt 617bytes
468 downloads









