Some interesting developments when running RKu?

Need to attach some photos as soon as I figure out how to make some space since I am at my limit of 4 mb. Figured it out and attached files:
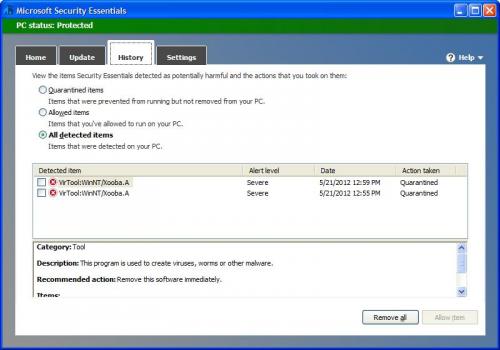
And the reports you requested:
Boot.ini
[boot loader]
timeout=30
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect
RkU
RkU Version: 3.8.389.593, Type LE (SR2)
==============================================
OS Name: Windows XP
Version 5.1.2600 (Service Pack 3)
Number of processors #2
==============================================
>Drivers
==============================================
0xBF0B2000 C:\WINDOWS\System32\ati3duag.dll 2367488 bytes (ATI Technologies Inc. , ati3duag.dll)
0x804D7000 C:\WINDOWS\system32\ntoskrnl.exe 2265088 bytes (Microsoft Corporation, NT Kernel & System)
0x804D7000 PnpManager 2265088 bytes
0x804D7000 RAW 2265088 bytes
0x804D7000 WMIxWDM 2265088 bytes
0xBF800000 Win32k 1863680 bytes
0xBF800000 C:\WINDOWS\System32\win32k.sys 1863680 bytes (Microsoft Corporation, Multi-User Win32 Driver)
0xB9C3B000 C:\WINDOWS\system32\DRIVERS\ati2mtag.sys 1331200 bytes (ATI Technologies Inc., ATI Radeon WindowsNT Miniport Driver)
0xB9A49000 C:\WINDOWS\system32\DRIVERS\smserial.sys 925696 bytes (Motorola Inc., Motorola SM56 Modem WDM Driver)
0xBF2F4000 C:\WINDOWS\System32\ativvaxx.dll 643072 bytes (ATI Technologies Inc. , Radeon Video Acceleration Universal Driver)
0xF7B52000 Ntfs.sys 577536 bytes (Microsoft Corporation, NT File System Driver)
0xB5556000 C:\WINDOWS\system32\DRIVERS\mrxsmb.sys 458752 bytes (Microsoft Corporation, Windows NT SMB Minirdr)
0xB98F3000 C:\WINDOWS\system32\DRIVERS\update.sys 385024 bytes (Microsoft Corporation, Update Driver)
0xB570B000 C:\WINDOWS\system32\DRIVERS\tcpip.sys 364544 bytes (Microsoft Corporation, TCP/IP Protocol Driver)
0xB1FA8000 C:\WINDOWS\system32\DRIVERS\srv.sys 360448 bytes (Microsoft Corporation, Server driver)
0xBF391000 C:\WINDOWS\System32\ATMFD.DLL 290816 bytes (Adobe Systems Incorporated, Windows NT OpenType/Type 1 Font Driver)
0xB9BC2000 C:\WINDOWS\system32\DRIVERS\bcmwl5.sys 266240 bytes (Broadcom Corporation, Broadcom Corporation NDIS 5.0 wireless driver)
0xB1BF4000 C:\WINDOWS\System32\Drivers\HTTP.sys 266240 bytes (Microsoft Corporation, HTTP Protocol Stack)
0xB9B4D000 C:\WINDOWS\system32\drivers\STAC97.sys 253952 bytes (SigmaTel, Inc., SigmaTel Audio Driver (WDM))
0xBF012000 C:\WINDOWS\System32\ati2dvag.dll 225280 bytes (ATI Technologies Inc., ATI Radeon WindowsNT Display Driver)
0xBF07D000 C:\WINDOWS\System32\atikvmag.dll 217088 bytes (ATI Technologies Inc., Virtual Command And Memory Manager)
0xBF049000 C:\WINDOWS\System32\ati2cqag.dll 212992 bytes (ATI Technologies Inc., Central Memory Manager / Queue Server Module)
0xB9951000 C:\WINDOWS\system32\DRIVERS\rdpdr.sys 196608 bytes (Microsoft Corporation, Microsoft RDP Device redirector)
0xF75A8000 ACPI.sys 188416 bytes (Microsoft Corporation, ACPI Driver for NT)
0xB226C000 C:\WINDOWS\system32\DRIVERS\mrxdav.sys 184320 bytes (Microsoft Corporation, Windows NT WebDav Minirdr)
0xF786A000 NDIS.sys 184320 bytes (Microsoft Corporation, NDIS 5.1 wrapper driver)
0xB106D000 C:\WINDOWS\system32\drivers\kmixer.sys 176128 bytes (Microsoft Corporation, Kernel Mode Audio Mixer)
0xB55C6000 C:\WINDOWS\system32\DRIVERS\rdbss.sys 176128 bytes (Microsoft Corporation, Redirected Drive Buffering SubSystem Driver)
0xF7422000 MpFilter.sys 163840 bytes (Microsoft Corporation, Microsoft antimalware file system filter driver)
0xB56D9000 C:\WINDOWS\system32\DRIVERS\netbt.sys 163840 bytes (Microsoft Corporation, MBT Transport driver)
0xF7494000 dmio.sys 155648 bytes (Microsoft Corp., Veritas Software, NT Disk Manager I/O Driver)
0xB56B3000 C:\WINDOWS\system32\DRIVERS\ipnat.sys 155648 bytes (Microsoft Corporation, IP Network Address Translator)
0xB1900000 C:\WINDOWS\System32\Drivers\Fastfat.SYS 147456 bytes (Microsoft Corporation, Fast FAT File System Driver)
0xB9C03000 C:\WINDOWS\system32\DRIVERS\USBPORT.SYS 147456 bytes (Microsoft Corporation, USB 1.1 & 2.0 Port Driver)
0xB9B8B000 C:\WINDOWS\system32\DRIVERS\ks.sys 143360 bytes (Microsoft Corporation, Kernel CSA Library)
0xB5691000 C:\WINDOWS\System32\drivers\afd.sys 139264 bytes (Microsoft Corporation, Ancillary Function Driver for WinSock)
0xB9B2B000 C:\WINDOWS\system32\drivers\portcls.sys 139264 bytes (Microsoft Corporation, Port Class (Class Driver for Port/Miniport Devices))
0x80700000 ACPI_HAL 134400 bytes
0x80700000 C:\WINDOWS\system32\hal.dll 134400 bytes (Microsoft Corporation, Hardware Abstraction Layer DLL)
0xF745C000 fltMgr.sys 131072 bytes (Microsoft Corporation, Microsoft Filesystem Filter Manager)
0xF74BA000 ftdisk.sys 126976 bytes (Microsoft Corporation, FT Disk Driver)
0xF74D9000 pcmcia.sys 122880 bytes (Microsoft Corporation, PCMCIA Bus Driver)
0xF7850000 Mup.sys 106496 bytes (Microsoft Corporation, Multiple UNC Provider driver)
0xF747C000 atapi.sys 98304 bytes (Microsoft Corporation, IDE/ATAPI Port Driver)
0xB46E4000 C:\WINDOWS\System32\Drivers\dump_atapi.sys 98304 bytes
0xB16DE000 C:\WINDOWS\system32\drivers\57028367.sys 94208 bytes (Kaspersky Lab, GERT, Kaspersky Lab Mini Driver)
0xF740B000 KSecDD.sys 94208 bytes (Microsoft Corporation, Kernel Security Support Provider Interface)
0xB9A32000 C:\WINDOWS\system32\DRIVERS\ndiswan.sys 94208 bytes (Microsoft Corporation, MS PPP Framing Driver (Strong Encryption))
0xB23AF000 C:\WINDOWS\system32\drivers\wdmaud.sys 86016 bytes (Microsoft Corporation, MMSYSTEM Wave/Midi API mapper)
0xB9BAE000 C:\WINDOWS\system32\DRIVERS\parport.sys 81920 bytes (Microsoft Corporation, Parallel Port Driver)
0xB9C27000 C:\WINDOWS\system32\DRIVERS\VIDEOPRT.SYS 81920 bytes (Microsoft Corporation, Video Port Driver)
0xB5764000 C:\WINDOWS\system32\DRIVERS\ipsec.sys 77824 bytes (Microsoft Corporation, IPSec Driver)
0xBF000000 C:\WINDOWS\System32\drivers\dxg.sys 73728 bytes (Microsoft Corporation, DirectX Graphics Driver)
0xF744A000 sr.sys 73728 bytes (Microsoft Corporation, System Restore Filesystem Filter Driver)
0xF7597000 pci.sys 69632 bytes (Microsoft Corporation, NT Plug and Play PCI Enumerator)
0xB9981000 C:\WINDOWS\system32\DRIVERS\psched.sys 69632 bytes (Microsoft Corporation, MS QoS Packet Scheduler)
0xB5681000 C:\WINDOWS\System32\Drivers\Cdfs.SYS 65536 bytes (Microsoft Corporation, CD-ROM File System Driver)
0xBA700000 C:\WINDOWS\system32\DRIVERS\cdrom.sys 65536 bytes (Microsoft Corporation, SCSI CD-ROM Driver)
0xF7607000 ohci1394.sys 65536 bytes (Microsoft Corporation, 1394 OpenHCI Port Driver)
0xF7687000 C:\WINDOWS\system32\drivers\drmk.sys 61440 bytes (Microsoft Corporation, Microsoft Kernel DRM Descrambler Filter)
0xBA6F0000 C:\WINDOWS\system32\DRIVERS\redbook.sys 61440 bytes (Microsoft Corporation, Redbook Audio Filter Driver)
0xB5641000 C:\WINDOWS\system32\drivers\sysaudio.sys 61440 bytes (Microsoft Corporation, System Audio WDM Filter)
0xF7557000 C:\WINDOWS\system32\DRIVERS\usbhub.sys 61440 bytes (Microsoft Corporation, Default Hub Driver for USB)
0xF7617000 C:\WINDOWS\system32\DRIVERS\1394BUS.SYS 57344 bytes (Microsoft Corporation, 1394 Bus Device Driver)
0xF7657000 C:\WINDOWS\system32\DRIVERS\CLASSPNP.SYS 53248 bytes (Microsoft Corporation, SCSI Class System Dll)
0xBA720000 C:\WINDOWS\system32\DRIVERS\i8042prt.sys 53248 bytes (Microsoft Corporation, i8042 Port Driver)
0xF7697000 C:\WINDOWS\system32\DRIVERS\rasl2tp.sys 53248 bytes (Microsoft Corporation, RAS L2TP mini-port/call-manager driver)
0xF7637000 VolSnap.sys 53248 bytes (Microsoft Corporation, Volume Shadow Copy Driver)
0xF76B7000 C:\WINDOWS\system32\DRIVERS\raspptp.sys 49152 bytes (Microsoft Corporation, Peer-to-Peer Tunneling Protocol)
0xF7667000 agp440.sys 45056 bytes (Microsoft Corporation, 440 NT AGP Filter)
0xF7527000 C:\WINDOWS\System32\Drivers\Fips.SYS 45056 bytes (Microsoft Corporation, FIPS Crypto Driver)
0xBA710000 C:\WINDOWS\system32\DRIVERS\imapi.sys 45056 bytes (Microsoft Corporation, IMAPI Kernel Driver)
0xF7627000 MountMgr.sys 45056 bytes (Microsoft Corporation, Mount Manager)
0xF76A7000 C:\WINDOWS\system32\DRIVERS\raspppoe.sys 45056 bytes (Microsoft Corporation, RAS PPPoE mini-port/call-manager driver)
0xF75F7000 isapnp.sys 40960 bytes (Microsoft Corporation, PNP ISA Bus Driver)
0xF76F7000 C:\WINDOWS\System32\Drivers\NDProxy.SYS 40960 bytes (Microsoft Corporation, NDIS Proxy)
0xF76D7000 C:\WINDOWS\system32\DRIVERS\termdd.sys 40960 bytes (Microsoft Corporation, Terminal Server Driver)
0xB1248000 C:\WINDOWS\System32\Drivers\BlackBox.SYS 36864 bytes (RKU Driver)
0xF7647000 disk.sys 36864 bytes (Microsoft Corporation, PnP Disk Driver)
0xBA730000 C:\WINDOWS\system32\DRIVERS\intelppm.sys 36864 bytes (Microsoft Corporation, Processor Device Driver)
0xF76C7000 C:\WINDOWS\system32\DRIVERS\msgpc.sys 36864 bytes (Microsoft Corporation, MS General Packet Classifier)
0xF7537000 C:\WINDOWS\system32\DRIVERS\netbios.sys 36864 bytes (Microsoft Corporation, NetBIOS interface driver)
0xF7547000 C:\WINDOWS\system32\DRIVERS\wanarp.sys 36864 bytes (Microsoft Corporation, MS Remote Access and Routing ARP Driver)
0xF77C7000 C:\WINDOWS\System32\Drivers\Modem.SYS 32768 bytes (Microsoft Corporation, Modem Device Driver)
0xF780F000 C:\WINDOWS\System32\Drivers\Npfs.SYS 32768 bytes (Microsoft Corporation, NPFS Driver)
0xF77A7000 C:\WINDOWS\system32\DRIVERS\usbehci.sys 32768 bytes (Microsoft Corporation, EHCI eUSB Miniport Driver)
0xF77BF000 C:\WINDOWS\system32\DRIVERS\fdc.sys 28672 bytes (Microsoft Corporation, Floppy Disk Controller Driver)
0xF7817000 C:\WINDOWS\system32\DRIVERS\HIDPARSE.SYS 28672 bytes (Microsoft Corporation, Hid Parsing Library)
0xF778F000 C:\DOCUME~1\Owner\LOCALS~1\Temp\mbr.sys 28672 bytes
0xF7707000 C:\WINDOWS\System32\Drivers\PCIIDEX.SYS 28672 bytes (Microsoft Corporation, PCI IDE Bus Driver Extension)
0xF77AF000 C:\WINDOWS\system32\DRIVERS\kbdclass.sys 24576 bytes (Microsoft Corporation, Keyboard Class Driver)
0xF77B7000 C:\WINDOWS\system32\DRIVERS\mouclass.sys 24576 bytes (Microsoft Corporation, Mouse Class Driver)
0xF7777000 c:\Documents and Settings\All Users\Application Data\Microsoft\Microsoft Antimalware\Definition Updates\{965E7061-AB6B-4E98-A636-8CE4614BB58D}\MpKsl8ca676ec.sys 24576 bytes (Microsoft Corporation, KSLDriver)
0xF779F000 C:\WINDOWS\system32\DRIVERS\usbuhci.sys 24576 bytes (Microsoft Corporation, UHCI USB Miniport Driver)
0xF77FF000 C:\WINDOWS\System32\drivers\vga.sys 24576 bytes (Microsoft Corporation, VGA/Super VGA Video Driver)
0xF77EF000 C:\WINDOWS\system32\DRIVERS\flpydisk.sys 20480 bytes (Microsoft Corporation, Floppy Driver)
0xF7807000 C:\WINDOWS\System32\Drivers\Msfs.SYS 20480 bytes (Microsoft Corporation, Mailslot driver)
0xF770F000 PartMgr.sys 20480 bytes (Microsoft Corporation, Partition Manager)
0xF77D7000 C:\WINDOWS\system32\DRIVERS\ptilink.sys 20480 bytes (Parallel Technologies, Inc., Parallel Technologies DirectParallel IO Library)
0xF77DF000 C:\WINDOWS\system32\DRIVERS\raspti.sys 20480 bytes (Microsoft Corporation, PTI DirectParallel® mini-port/call-manager driver)
0xF77CF000 C:\WINDOWS\system32\DRIVERS\TDI.SYS 20480 bytes (Microsoft Corporation, TDI Wrapper)
0xB5810000 C:\WINDOWS\System32\watchdog.sys 20480 bytes (Microsoft Corporation, Watchdog Driver)
0xF789F000 C:\WINDOWS\system32\DRIVERS\BATTC.SYS 16384 bytes (Microsoft Corporation, Battery Class Driver)
0xBA7B0000 C:\WINDOWS\system32\DRIVERS\CmBatt.sys 16384 bytes (Microsoft Corporation, Control Method Battery Driver)
0xBA790000 C:\WINDOWS\system32\DRIVERS\mssmbios.sys 16384 bytes (Microsoft Corporation, System Management BIOS Driver)
0xB2648000 C:\WINDOWS\system32\DRIVERS\ndisuio.sys 16384 bytes (Microsoft Corporation, NDIS User mode I/O Driver)
0xF78A3000 ACPIEC.sys 12288 bytes (Microsoft Corporation, ACPI Embedded Controller Driver)
0xF7897000 C:\WINDOWS\system32\BOOTVID.dll 12288 bytes (Microsoft Corporation, VGA Boot Driver)
0xF789B000 compbatt.sys 12288 bytes (Microsoft Corporation, Composite Battery Driver)
0xB5532000 C:\WINDOWS\System32\drivers\Dxapi.sys 12288 bytes (Microsoft Corporation, DirectX API Driver)
0xBA7AC000 C:\WINDOWS\system32\DRIVERS\ndistapi.sys 12288 bytes (Microsoft Corporation, NDIS 3.0 connection wrapper driver)
0xF793F000 C:\WINDOWS\system32\DRIVERS\rasacd.sys 12288 bytes (Microsoft Corporation, RAS Automatic Connection Driver)
0xF79B9000 C:\WINDOWS\System32\Drivers\Beep.SYS 8192 bytes (Microsoft Corporation, BEEP Driver)
0xF798D000 dmload.sys 8192 bytes (Microsoft Corp., Veritas Software., NT Disk Manager Startup Driver)
0xF79EF000 C:\WINDOWS\System32\Drivers\dump_WMILIB.SYS 8192 bytes
0xF79B7000 C:\WINDOWS\System32\Drivers\Fs_Rec.SYS 8192 bytes (Microsoft Corporation, File System Recognizer Driver)
0xF798B000 intelide.sys 8192 bytes (Microsoft Corporation, Intel PCI IDE Driver)
0xF7987000 C:\WINDOWS\system32\KDCOM.DLL 8192 bytes (Microsoft Corporation, Kernel Debugger HW Extension DLL)
0xF79BB000 C:\WINDOWS\System32\Drivers\mnmdd.SYS 8192 bytes (Microsoft Corporation, Frame buffer simulator)
0xF7995000 C:\WINDOWS\System32\Drivers\ParVdm.SYS 8192 bytes (Microsoft Corporation, VDM Parallel Driver)
0xF79BD000 C:\WINDOWS\System32\DRIVERS\RDPCDD.sys 8192 bytes (Microsoft Corporation, RDP Miniport)
0xF79B1000 C:\WINDOWS\system32\DRIVERS\swenum.sys 8192 bytes (Microsoft Corporation, Plug and Play Software Device Enumerator)
0xF79B3000 C:\WINDOWS\system32\DRIVERS\USBD.SYS 8192 bytes (Microsoft Corporation, Universal Serial Bus Driver)
0xF7989000 C:\WINDOWS\system32\DRIVERS\WMILIB.SYS 8192 bytes (Microsoft Corporation, WMILIB WMI support library Dll)
0xF7A56000 C:\WINDOWS\system32\DRIVERS\audstub.sys 4096 bytes (Microsoft Corporation, AudStub Driver)
0xB5868000 C:\WINDOWS\System32\Drivers\BANTExt.sys 4096 bytes
0xB552B000 C:\WINDOWS\System32\drivers\dxgthk.sys 4096 bytes (Microsoft Corporation, DirectX Graphics Driver Thunk)
0xF7A64000 C:\WINDOWS\System32\Drivers\Null.SYS 4096 bytes (Microsoft Corporation, NULL Driver)
0xF7A50000 C:\WINDOWS\system32\DRIVERS\OPRGHDLR.SYS 4096 bytes (Microsoft Corporation, ACPI Operation Registration Driver)
0xF7A4F000 PCIIde.sys 4096 bytes (Microsoft Corporation, Generic PCI IDE Bus Driver)
==============================================
>Stealth
==============================================
==============================================
>Files
==============================================
==============================================
>Hooks
==============================================
ntoskrnl.exe+0x00005B22, Type: Inline - RelativeJump 0x804DCB22-->804DCB29 [ntoskrnl.exe]
[1832]searchindexer.exe-->kernel32.dll-->WriteFile, Type: Inline - RelativeJump 0x7C810E27-->00585C0C [mssrch.dll]
[1832]searchindexer.exe-->kernel32.dll-->WriteFile, Type: Inline - SEH 0x7C810E2C [unknown_code_page]
[1832]searchindexer.exe-->kernel32.dll-->WriteFile, Type: Inline - SEH 0x7C810E2D [unknown_code_page]
[2020]explorer.exe-->advapi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77DD1218-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->crypt32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77A81188-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->gdi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77F110B4-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x01001268-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->mswsock.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71A51178-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->shell32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7C9C15A4-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->user32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7E41133C-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->wininet.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x3D9314B0-->5CB77774 [shimeng.dll]
[2020]explorer.exe-->ws2_32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71AB109C-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->advapi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77DD1218-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77DD1214-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77DD105C-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77DD11E0-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->crypt32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77A81188-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77A81190-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x77A811F8-->715B9F5D [aclayers.dll]
[2264]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77A811FC-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->gdi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77F110B4-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77F11084-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77F11078-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77F110B8-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x0040106C-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x00401098-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x004010E8-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x004010C0-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->mswsock.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71A51178-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71A51184-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x71A511A0-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->shell32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7C9C15A4-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7C9C13E8-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x7C9C163C-->715B9F5D [aclayers.dll]
[2264]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7C9C161C-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7C9C15A0-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->user32.dll-->CallNextHookEx, Type: Inline - RelativeJump 0x7E42B3C6-->3E2DD119 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->CreateWindowExW, Type: Inline - RelativeJump 0x7E42D0A3-->3E2EDB14 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->DialogBoxIndirectParamA, Type: Inline - RelativeJump 0x7E456D7D-->3E3E5412 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->DialogBoxIndirectParamW, Type: Inline - RelativeJump 0x7E432072-->3E3E53AF [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->DialogBoxParamA, Type: Inline - RelativeJump 0x7E43B144-->3E3E534C [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->DialogBoxParamW, Type: Inline - RelativeJump 0x7E4247AB-->3E215505 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7E41133C-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7E4112F4-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7E411208-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7E411340-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->user32.dll-->MessageBoxExA, Type: Inline - RelativeJump 0x7E45085C-->3E3E5214 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->MessageBoxExW, Type: Inline - RelativeJump 0x7E450838-->3E3E51B2 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->MessageBoxIndirectA, Type: Inline - RelativeJump 0x7E43A082-->3E3E52E1 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->MessageBoxIndirectW, Type: Inline - RelativeJump 0x7E4664D5-->3E3E5276 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->SetWindowsHookExW, Type: Inline - RelativeJump 0x7E42820F-->3E2E9AA5 [ieframe.dll]
[2264]iexplore.exe-->user32.dll-->UnhookWindowsHookEx, Type: Inline - RelativeJump 0x7E42D5F3-->3E254686 [ieframe.dll]
[2264]iexplore.exe-->wininet.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x3D9314B0-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x3D9314B4-->715B9E59 [aclayers.dll]
[2264]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x3D931450-->715BA16B [aclayers.dll]
[2264]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x3D931350-->715BA067 [aclayers.dll]
[2264]iexplore.exe-->ws2_32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71AB109C-->5CB77774 [shimeng.dll]
[2264]iexplore.exe-->ws2_32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71AB10A8-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->advapi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77DD1218-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77DD1214-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77DD105C-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77DD11E0-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->crypt32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77A81188-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77A81190-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x77A811F8-->715B9F5D [aclayers.dll]
[2520]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77A811FC-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->gdi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77F110B4-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77F11084-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77F11078-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77F110B8-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x0040106C-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x00401098-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x004010E8-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x004010C0-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->mswsock.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71A51178-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71A51184-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x71A511A0-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->shell32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7C9C15A4-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7C9C13E8-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x7C9C163C-->715B9F5D [aclayers.dll]
[2520]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7C9C161C-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7C9C15A0-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->user32.dll-->CallNextHookEx, Type: Inline - RelativeJump 0x7E42B3C6-->3E2DD119 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->CreateWindowExW, Type: Inline - RelativeJump 0x7E42D0A3-->3E2EDB14 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->DialogBoxIndirectParamA, Type: Inline - RelativeJump 0x7E456D7D-->3E3E5412 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->DialogBoxIndirectParamW, Type: Inline - RelativeJump 0x7E432072-->3E3E53AF [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->DialogBoxParamA, Type: Inline - RelativeJump 0x7E43B144-->3E3E534C [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->DialogBoxParamW, Type: Inline - RelativeJump 0x7E4247AB-->3E215505 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7E41133C-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7E4112F4-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7E411208-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7E411340-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->user32.dll-->MessageBoxExA, Type: Inline - RelativeJump 0x7E45085C-->3E3E5214 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->MessageBoxExW, Type: Inline - RelativeJump 0x7E450838-->3E3E51B2 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->MessageBoxIndirectA, Type: Inline - RelativeJump 0x7E43A082-->3E3E52E1 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->MessageBoxIndirectW, Type: Inline - RelativeJump 0x7E4664D5-->3E3E5276 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->SetWindowsHookExW, Type: Inline - RelativeJump 0x7E42820F-->3E2E9AA5 [ieframe.dll]
[2520]iexplore.exe-->user32.dll-->UnhookWindowsHookEx, Type: Inline - RelativeJump 0x7E42D5F3-->3E254686 [ieframe.dll]
[2520]iexplore.exe-->wininet.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x3D9314B0-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x3D9314B4-->715B9E59 [aclayers.dll]
[2520]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x3D931450-->715BA16B [aclayers.dll]
[2520]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x3D931350-->715BA067 [aclayers.dll]
[2520]iexplore.exe-->ws2_32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71AB109C-->5CB77774 [shimeng.dll]
[2520]iexplore.exe-->ws2_32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71AB10A8-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->advapi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77DD1218-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77DD1214-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77DD105C-->715BA16B [aclayers.dll]
[472]iexplore.exe-->advapi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77DD11E0-->715BA067 [aclayers.dll]
[472]iexplore.exe-->crypt32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77A81188-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77A81190-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x77A811F8-->715B9F5D [aclayers.dll]
[472]iexplore.exe-->crypt32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77A811FC-->715BA16B [aclayers.dll]
[472]iexplore.exe-->gdi32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x77F110B4-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x77F11084-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x77F11078-->715BA16B [aclayers.dll]
[472]iexplore.exe-->gdi32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x77F110B8-->715BA067 [aclayers.dll]
[472]iexplore.exe-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x0040106C-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x00401098-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x004010E8-->715BA16B [aclayers.dll]
[472]iexplore.exe-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x004010C0-->715BA067 [aclayers.dll]
[472]iexplore.exe-->mswsock.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71A51178-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71A51184-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->mswsock.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x71A511A0-->715BA067 [aclayers.dll]
[472]iexplore.exe-->shell32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7C9C15A4-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7C9C13E8-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExA, Type: IAT modification 0x7C9C163C-->715B9F5D [aclayers.dll]
[472]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7C9C161C-->715BA16B [aclayers.dll]
[472]iexplore.exe-->shell32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7C9C15A0-->715BA067 [aclayers.dll]
[472]iexplore.exe-->user32.dll-->CreateWindowExW, Type: Inline - RelativeJump 0x7E42D0A3-->3E2EDB14 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->DialogBoxIndirectParamA, Type: Inline - RelativeJump 0x7E456D7D-->3E3E5412 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->DialogBoxIndirectParamW, Type: Inline - RelativeJump 0x7E432072-->3E3E53AF [ieframe.dll]
[472]iexplore.exe-->user32.dll-->DialogBoxParamA, Type: Inline - RelativeJump 0x7E43B144-->3E3E534C [ieframe.dll]
[472]iexplore.exe-->user32.dll-->DialogBoxParamW, Type: Inline - RelativeJump 0x7E4247AB-->3E215505 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x7E41133C-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x7E4112F4-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x7E411208-->715BA16B [aclayers.dll]
[472]iexplore.exe-->user32.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x7E411340-->715BA067 [aclayers.dll]
[472]iexplore.exe-->user32.dll-->MessageBoxExA, Type: Inline - RelativeJump 0x7E45085C-->3E3E5214 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->MessageBoxExW, Type: Inline - RelativeJump 0x7E450838-->3E3E51B2 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->MessageBoxIndirectA, Type: Inline - RelativeJump 0x7E43A082-->3E3E52E1 [ieframe.dll]
[472]iexplore.exe-->user32.dll-->MessageBoxIndirectW, Type: Inline - RelativeJump 0x7E4664D5-->3E3E5276 [ieframe.dll]
[472]iexplore.exe-->wininet.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x3D9314B0-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x3D9314B4-->715B9E59 [aclayers.dll]
[472]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryExW, Type: IAT modification 0x3D931450-->715BA16B [aclayers.dll]
[472]iexplore.exe-->wininet.dll-->kernel32.dll-->LoadLibraryW, Type: IAT modification 0x3D931350-->715BA067 [aclayers.dll]
[472]iexplore.exe-->ws2_32.dll-->kernel32.dll-->GetProcAddress, Type: IAT modification 0x71AB109C-->5CB77774 [shimeng.dll]
[472]iexplore.exe-->ws2_32.dll-->kernel32.dll-->LoadLibraryA, Type: IAT modification 0x71AB10A8-->715B9E59 [aclayers.dll]
Edited by joseph456, 21 May 2012 - 11:41 AM.


 This topic is locked
This topic is locked














 Sign In
Sign In Create Account
Create Account

