Message alleges to be from the West Yorkshire Police and says that I have been looking at illegal content and that I need to pay £100 With Ukash vouchers.I am able to start the computer in Safe mode.I have seen other recent posts with a similar problem.I managed to carry out a virus scan in safe mode but it found no threats. Please help!
Ukash Police virus [Closed] [Solved]
Started by
chucknorrisno1
, May 29 2012 11:40 AM
#1
![Ukash Police virus [Closed] [Solved]: post #1](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 29 May 2012 - 11:40 AM
Posted 29 May 2012 - 11:40 AM

Message alleges to be from the West Yorkshire Police and says that I have been looking at illegal content and that I need to pay £100 With Ukash vouchers.I am able to start the computer in Safe mode.I have seen other recent posts with a similar problem.I managed to carry out a virus scan in safe mode but it found no threats. Please help!
#2
![Ukash Police virus [Closed] [Solved]: post #2](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 May 2012 - 06:42 PM
Posted 31 May 2012 - 06:42 PM

Hi, chucknorrisno1!  My nick name is CompCav and I will be assisting you with your Malware/Security problems. Please make sure you read all of the instructions and fixes thoroughly before continuing with them. If you have any questions or you are unsure about anything, just ask and I will help you out.
My nick name is CompCav and I will be assisting you with your Malware/Security problems. Please make sure you read all of the instructions and fixes thoroughly before continuing with them. If you have any questions or you are unsure about anything, just ask and I will help you out. 
If you have resolved the issues you were originally experiencing, or have received help elsewhere, please let me know so that this topic can be closed.
Please make sure you are saving and printing the instructions out prior to each fix, this way you will have them on hand just in case you are unable to access this site. One of the steps I will be asking you to do requires you to boot into Safe Mode and this process will be much easier for you to perform if the instructions are printed out for you to follow.
If you are ready to get started, please review and follow these guidelines so that we resolve your issues in a timely and effective manner:
Since you can run in safe mode please do this first step in safe mode:
Step 1.
Please post:
All RKreport.txt text files located on your desktop.
One you have completed step 1 reboot into normal mode and complete the remaining steps.
Step 2.
Download aswMBR.exe ( 1.8mb ) to your desktop.
Double click the aswMBR.exe to run it Click the "Scan" button to start scan
On completion of the scan click save log, save it to your desktop and post in your next reply
If it does not run rename it iexplore.exe and try it again.
Step 3.
Download OTL to your Desktop
Step 4.
Please post:
RkReport.txt logs
aswMBR log
OTL.txt
Extras.txt
Give me an update on your computer's issues.
If you have resolved the issues you were originally experiencing, or have received help elsewhere, please let me know so that this topic can be closed.
Please make sure you are saving and printing the instructions out prior to each fix, this way you will have them on hand just in case you are unable to access this site. One of the steps I will be asking you to do requires you to boot into Safe Mode and this process will be much easier for you to perform if the instructions are printed out for you to follow.
If you are ready to get started, please review and follow these guidelines so that we resolve your issues in a timely and effective manner:
- Logs from malware removal programs (OTL is one of them) can take some time to analyze. I need you to be patient while I analyze any logs you post.
- Please make sure to carefully read any instructions that I give you. Since I cannot see or directly interact with your computer I am dependent on you to "be my eyes" and provide as much information as you can regarding the current state of your computer.
- If you're not sure, or if something unexpected happens, do NOT continue! Stop and ask!
- These instructions have been specifically tailored to your computer and the issues you are experiencing with your computer. These instructions are not suitable for any other computer, even if the issues are fairly similar.
- Do not do things I do not ask for, such as running a spyware scan on your computer. However, the one thing that you should always do, is to make sure your anti-virus definitions are up-to-date!
- Please do not use the Attachment feature for any log file. Just do a Copy/Paste of the entire contents of the log file inside your post and submit.
- You must reply within four days failure to reply will result in the topic being closed!
- Please do not PM me directly for help. If you have any questions, post them in this topic. PM me only if I have not responded to your last post in 2 days.
- Lastly, I am no magician. I will try very hard to fix your issues, but no promises can be made. Also be aware that some infections are so severe that you might need to ultimately reformat your hard drive and reinstall the operating system.
Don't worry, this only happens in severe cases, but it sadly does happen. Please have the software and storage media for backing up your data available.
Since you can run in safe mode please do this first step in safe mode:
Step 1.
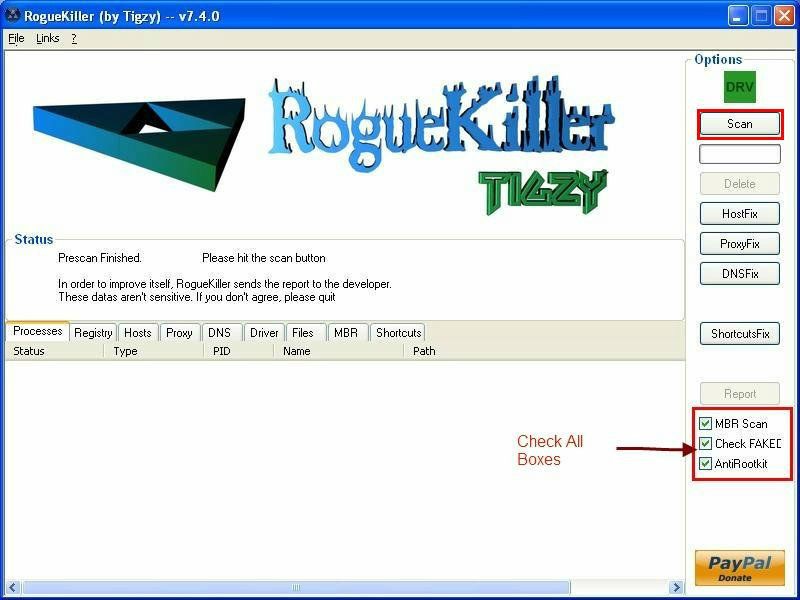
- Download RogueKiller and save it on your desktop.
- Quit all programs
- Start RogueKiller.exe.
- Wait until Prescan has finished ...
- Click on Scan
- Note: If RogueKiller will not run please try it several times, if it still does not run rename it winlogon.com and try it several times.

- Wait for the end of the scan.
- The report has been created on the desktop.
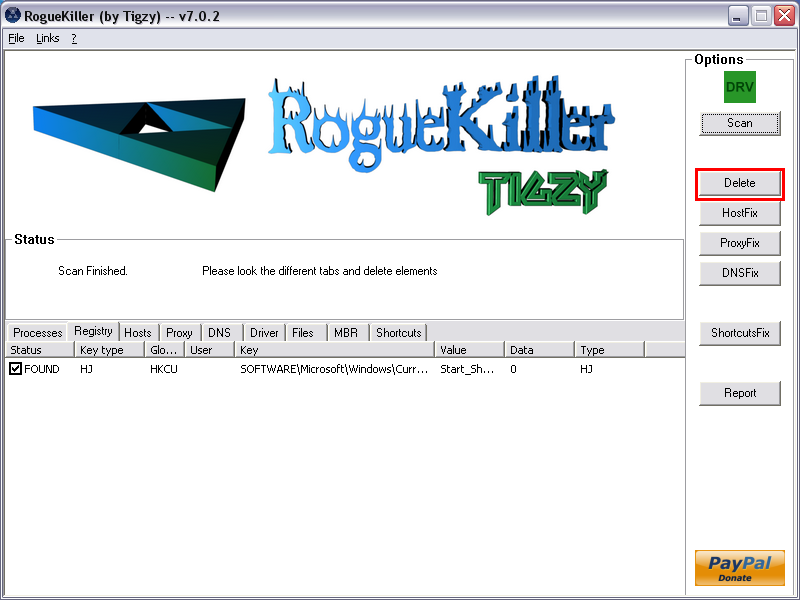
- Click on the Delete button.

- The report has been created on the desktop.
- Next click on ShortcutsFix
- The report has been created on the desktop.
Please post:
All RKreport.txt text files located on your desktop.
One you have completed step 1 reboot into normal mode and complete the remaining steps.
Step 2.
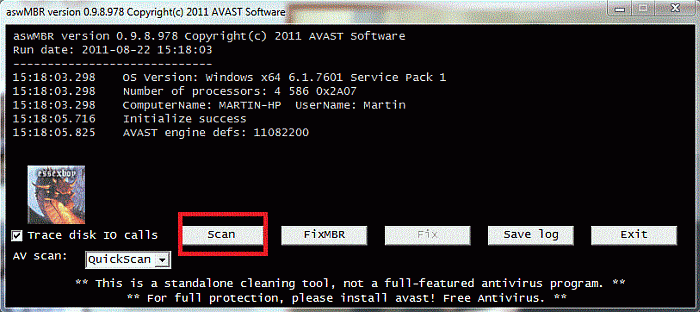
Download aswMBR.exe ( 1.8mb ) to your desktop.
Double click the aswMBR.exe to run it Click the "Scan" button to start scan

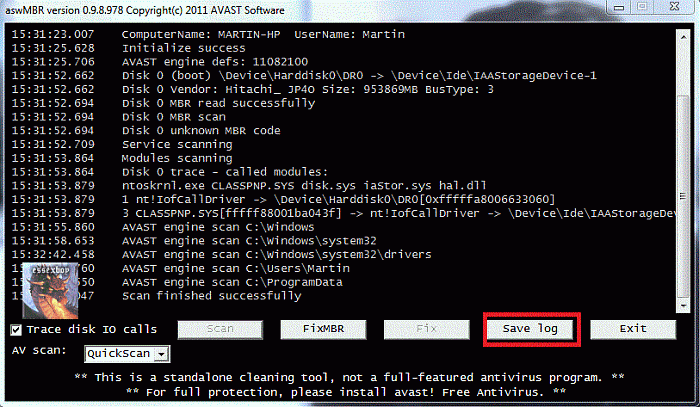
On completion of the scan click save log, save it to your desktop and post in your next reply

If it does not run rename it iexplore.exe and try it again.
Step 3.
Download OTL to your Desktop
- Double click on the icon to run it. Make sure all other windows are closed and to let it run uninterrupted.
- Select Scan All Users
- Select Lop Check and Purity Check
- Under the Custom Scan box paste this in
netsvcs
%SYSTEMDRIVE%\*.exe
/md5start
consrv.dll
explorer.exe
winlogon.exe
Userinit.exe
svchost.exe
/md5stop
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NetBT /s
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NetBIOS /s
hklm\software\clients\startmenuinternet|command /rs
hklm\software\clients\startmenuinternet|command /64 /rs
C:\Windows\assembly\tmp\U\*.* /s
C:\Program Files\Common Files\ComObjects\*.* /s
C:\windows\*. /RP /s
%Temp%\smtmp\1\*.*
%Temp%\smtmp\2\*.*
%Temp%\smtmp\3\*.*
%Temp%\smtmp\4\*.*
>C:\commands.txt echo list vol /raw /hide /c
/wait
>C:\DiskReport.txt diskpart /s C:\commands.txt /raw /hide /c
/wait
type c:\diskreport.txt /c
/wait
erase c:\commands.txt /hide /c
/wait
erase c:\diskreport.txt /hide /c
CREATERESTOREPOINT - Click the Quick Scan button. Do not change any settings unless otherwise told to do so. The scan wont take long.
- When the scan completes, it will open two notepad windows. OTL.Txt and Extras.Txt. These are saved in the same location as OTL.
- Post both logs
Step 4.
Please post:
RkReport.txt logs
aswMBR log
OTL.txt
Extras.txt
Give me an update on your computer's issues.
#3
![Ukash Police virus [Closed] [Solved]: post #3](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 09:29 AM
Posted 01 June 2012 - 09:29 AM

Hi CompCav
Thanks for getting back to me.
I am just about to do what you asked but for your info when I restarted my laptop it stated "Checking file system on C: The type of the file system is NTFS. Volume label is OS." And then it carried out a scan of the C:
Also my laptop uses Windows 7 OS.
Regards
Thanks for getting back to me.
I am just about to do what you asked but for your info when I restarted my laptop it stated "Checking file system on C: The type of the file system is NTFS. Volume label is OS." And then it carried out a scan of the C:
Also my laptop uses Windows 7 OS.
Regards
#4
![Ukash Police virus [Closed] [Solved]: post #4](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 09:31 AM
Posted 01 June 2012 - 09:31 AM

Thanks for the update, the check disk is OK you can run the tools when it finishes 
#5
![Ukash Police virus [Closed] [Solved]: post #5](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 10:12 AM
Posted 01 June 2012 - 10:12 AM

Hi again
I am having problems connecting to the internet whilst in safe mode. Do you know how to resolve this or can I use the laptop I am on to download the above programs, save them to a USB and plug it into my infected laptop?
I use a wireless router and connections box states "Not connected. No connections are available." When I open the Network and Sharing centre it says "The dependency service or group failed to start".

I am having problems connecting to the internet whilst in safe mode. Do you know how to resolve this or can I use the laptop I am on to download the above programs, save them to a USB and plug it into my infected laptop?
I use a wireless router and connections box states "Not connected. No connections are available." When I open the Network and Sharing centre it says "The dependency service or group failed to start".
#6
![Ukash Police virus [Closed] [Solved]: post #6](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 10:16 AM
Posted 01 June 2012 - 10:16 AM

can I use the laptop I am on to download the above programs, save them to a USB and plug it into my infected laptop?
This is a good way to get files onto the infected computer. But first install this:
Panda Vaccine
- Please download Panda USB Vaccine (you must provide valid e-mail and they will send you download link to this e-mail address) to your desktop.
- Install and run the program.
- Double-click on the file USBVaccine.zip located on your desktop.
- A file viewer will open. Double-click on the file USBVaccineSetup.exe. Please select Yes if you are asked if you want to allow the program to make changes to the computer.
- Follow the steps on screen to install the program on your computer.
- Plug in your USB drive and click on Vaccinate USB and Vaccinate Computer.
Then after this download the files you need, copy them onto the vaccinated USB drive, and then plug it in your infected computer and copy onto the desktop.
#7
![Ukash Police virus [Closed] [Solved]: post #7](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 10:27 AM
Posted 01 June 2012 - 10:27 AM

Thanks. Vaccinated and downloading files now
#8
![Ukash Police virus [Closed] [Solved]: post #8](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 11:26 AM
Posted 01 June 2012 - 11:26 AM

USB is not being detected on the infected laptop and I still cannot get it to connect to the internet to download direct to load the files.
I tried to add a picture from my phone to show whats on the screen but needs a url address.
I tried to add a picture from my phone to show whats on the screen but needs a url address.
#9
![Ukash Police virus [Closed] [Solved]: post #9](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:02 PM
Posted 01 June 2012 - 01:02 PM

I believe my CDrom will work so I will try using that to transfer the files.
#10
![Ukash Police virus [Closed] [Solved]: post #10](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:22 PM
Posted 01 June 2012 - 01:22 PM

Yes try the CD and if it does not work let me know and we will work outside of windows.
#11
![Ukash Police virus [Closed] [Solved]: post #11](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:38 PM
Posted 01 June 2012 - 01:38 PM

Using the cdrom seemed to work so for RK -
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Scan -- Date: 06/01/2012 20:11:45
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 4 ¤¤¤
[SUSP PATH] HKCU\[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> FOUND
[SUSP PATH] HKUS\S-1-5-21-42006818-769000053-1479337117-1002[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 9d490dd7e6adfb6a473e12293cc8b6b4
[BSP] dea9defa67a18cc486b8c709b2ee22f0 : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] DELL-UTIL (0xde) [VISIBLE] Offset (sectors): 63 | Size: 101 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 212992 | Size: 20000 Mo
2 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 41172992 | Size: 456835 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[1].txt >>
RKreport[1].txt
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Scan -- Date: 06/01/2012 20:11:45
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 4 ¤¤¤
[SUSP PATH] HKCU\[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> FOUND
[SUSP PATH] HKUS\S-1-5-21-42006818-769000053-1479337117-1002[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 9d490dd7e6adfb6a473e12293cc8b6b4
[BSP] dea9defa67a18cc486b8c709b2ee22f0 : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] DELL-UTIL (0xde) [VISIBLE] Offset (sectors): 63 | Size: 101 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 212992 | Size: 20000 Mo
2 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 41172992 | Size: 456835 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[1].txt >>
RKreport[1].txt
#12
![Ukash Police virus [Closed] [Solved]: post #12](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:40 PM
Posted 01 June 2012 - 01:40 PM

Next RK report -
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Remove -- Date: 06/01/2012 20:12:23
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 3 ¤¤¤
[SUSP PATH] HKCU\[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> DELETED
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 9d490dd7e6adfb6a473e12293cc8b6b4
[BSP] dea9defa67a18cc486b8c709b2ee22f0 : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] DELL-UTIL (0xde) [VISIBLE] Offset (sectors): 63 | Size: 101 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 212992 | Size: 20000 Mo
2 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 41172992 | Size: 456835 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2].txt >>
RKreport[1].txt ; RKreport[2].txt
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Remove -- Date: 06/01/2012 20:12:23
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 3 ¤¤¤
[SUSP PATH] HKCU\[...]\Run : {3C1B74A1-014D-A2FA-884B-7B24C588DD9E} (C:\Users\Al and Claire\AppData\Roaming\xkpoe\start.exe) -> DELETED
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ Infection : ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: +++++
--- User ---
[MBR] 9d490dd7e6adfb6a473e12293cc8b6b4
[BSP] dea9defa67a18cc486b8c709b2ee22f0 : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] DELL-UTIL (0xde) [VISIBLE] Offset (sectors): 63 | Size: 101 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 212992 | Size: 20000 Mo
2 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 41172992 | Size: 456835 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2].txt >>
RKreport[1].txt ; RKreport[2].txt
#13
![Ukash Police virus [Closed] [Solved]: post #13](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:40 PM
Posted 01 June 2012 - 01:40 PM

Last RK report -
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Shortcuts HJfix -- Date: 06/01/2012 20:13:43
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ File attributes restored: ¤¤¤
Desktop: Success 2 / Fail 0
Quick launch: Success 1 / Fail 0
Programs: Success 5 / Fail 0
Start menu: Success 1 / Fail 0
User folder: Success 96 / Fail 0
My documents: Success 0 / Fail 0
My favorites: Success 0 / Fail 0
My pictures: Success 0 / Fail 0
My music: Success 0 / Fail 0
My videos: Success 0 / Fail 0
Local drives: Success 89 / Fail 0
Backup: [NOT FOUND]
Drives:
[C:] \Device\HarddiskVolume3 -- 0x3 --> Restored
[D:] \Device\CdRom0 -- 0x5 --> Skipped
¤¤¤ Infection : ¤¤¤
Finished : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
RogueKiller V7.5.2 [05/30/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows 7 (6.1.7601 Service Pack 1) 64 bits version
Started in : Safe mode
User: Al and Claire [Admin rights]
Mode: Shortcuts HJfix -- Date: 06/01/2012 20:13:43
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Driver: [NOT LOADED] ¤¤¤
¤¤¤ File attributes restored: ¤¤¤
Desktop: Success 2 / Fail 0
Quick launch: Success 1 / Fail 0
Programs: Success 5 / Fail 0
Start menu: Success 1 / Fail 0
User folder: Success 96 / Fail 0
My documents: Success 0 / Fail 0
My favorites: Success 0 / Fail 0
My pictures: Success 0 / Fail 0
My music: Success 0 / Fail 0
My videos: Success 0 / Fail 0
Local drives: Success 89 / Fail 0
Backup: [NOT FOUND]
Drives:
[C:] \Device\HarddiskVolume3 -- 0x3 --> Restored
[D:] \Device\CdRom0 -- 0x5 --> Skipped
¤¤¤ Infection : ¤¤¤
Finished : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
#14
![Ukash Police virus [Closed] [Solved]: post #14](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:41 PM
Posted 01 June 2012 - 01:41 PM

Then the aswMBR report -
aswMBR version 0.9.9.1665 Copyright© 2011 AVAST Software
Run date: 2012-06-01 20:19:30
-----------------------------
20:19:30.391 OS Version: Windows x64 6.1.7601 Service Pack 1
20:19:30.391 Number of processors: 4 586 0x2A07
20:19:30.392 ComputerName: ALANDCLAIRE-PC UserName: Al and Claire
20:19:36.712 Initialize success
20:19:51.612 AVAST engine download error: 0
20:19:51.614 AVAST engine error: 11003
20:21:58.615 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IAAStorageDevice-1
20:21:58.621 Disk 0 Vendor: ST950042 0002 Size: 476940MB BusType: 3
20:21:58.643 Disk 0 MBR read successfully
20:21:58.655 Disk 0 MBR scan
20:21:58.662 Disk 0 Windows VISTA default MBR code
20:21:58.669 Disk 0 Partition 1 00 DE Dell Utility Dell 8.0 101 MB offset 63
20:21:58.687 Disk 0 Partition 2 80 (A) 07 HPFS/NTFS NTFS 20000 MB offset 212992
20:21:58.709 Disk 0 Partition 3 00 07 HPFS/NTFS NTFS 456835 MB offset 41172992
20:21:58.727 Disk 0 scanning C:\Windows\system32\drivers
20:22:05.200 Service scanning
20:22:21.265 Modules scanning
20:22:21.288 Disk 0 trace - called modules:
20:22:21.300
20:22:21.323 Scan finished successfully
20:22:48.358 Disk 0 MBR has been saved successfully to "C:\Users\Al and Claire\Desktop\MBR.dat"
20:22:48.362 The log file has been saved successfully to "C:\Users\Al and Claire\Desktop\aswMBR.txt"
aswMBR version 0.9.9.1665 Copyright© 2011 AVAST Software
Run date: 2012-06-01 20:19:30
-----------------------------
20:19:30.391 OS Version: Windows x64 6.1.7601 Service Pack 1
20:19:30.391 Number of processors: 4 586 0x2A07
20:19:30.392 ComputerName: ALANDCLAIRE-PC UserName: Al and Claire
20:19:36.712 Initialize success
20:19:51.612 AVAST engine download error: 0
20:19:51.614 AVAST engine error: 11003
20:21:58.615 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IAAStorageDevice-1
20:21:58.621 Disk 0 Vendor: ST950042 0002 Size: 476940MB BusType: 3
20:21:58.643 Disk 0 MBR read successfully
20:21:58.655 Disk 0 MBR scan
20:21:58.662 Disk 0 Windows VISTA default MBR code
20:21:58.669 Disk 0 Partition 1 00 DE Dell Utility Dell 8.0 101 MB offset 63
20:21:58.687 Disk 0 Partition 2 80 (A) 07 HPFS/NTFS NTFS 20000 MB offset 212992
20:21:58.709 Disk 0 Partition 3 00 07 HPFS/NTFS NTFS 456835 MB offset 41172992
20:21:58.727 Disk 0 scanning C:\Windows\system32\drivers
20:22:05.200 Service scanning
20:22:21.265 Modules scanning
20:22:21.288 Disk 0 trace - called modules:
20:22:21.300
20:22:21.323 Scan finished successfully
20:22:48.358 Disk 0 MBR has been saved successfully to "C:\Users\Al and Claire\Desktop\MBR.dat"
20:22:48.362 The log file has been saved successfully to "C:\Users\Al and Claire\Desktop\aswMBR.txt"
#15
![Ukash Police virus [Closed] [Solved]: post #15](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 June 2012 - 01:51 PM
Posted 01 June 2012 - 01:51 PM

Good results so far!
Did you run aswMBR in normal mode?
How is OTL running?
CompCav
Did you run aswMBR in normal mode?
How is OTL running?
CompCav
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

