
Search Engine re-directs [Closed]
#16
![Search Engine re-directs [Closed]: post #16](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 03:59 PM
Posted 23 July 2012 - 03:59 PM

#17
![Search Engine re-directs [Closed]: post #17](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 04:01 PM
Posted 23 July 2012 - 04:01 PM

========== OTL ==========
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{2fa28606-de77-4029-af96-b231e3b8f827}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2fa28606-de77-4029-af96-b231e3b8f827}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\URLSearchHooks\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ deleted successfully.
C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{2fa28606-de77-4029-af96-b231e3b8f827}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2fa28606-de77-4029-af96-b231e3b8f827}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{4EF9D70C-FC56-C049-5A8E-29ABC30AA288}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{4EF9D70C-FC56-C049-5A8E-29ABC30AA288}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\URLSearchHooks\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
Registry key HKEY_LOCAL_MACHINE\Software\MozillaPlugins\@java.com/JavaPlugin\ deleted successfully.
C:\Program Files (x86)\Java\jre6\bin\new_plugin\npjp2.dll moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\META-INF folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\imgs\flgs folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\imgs folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\images folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected] folder moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{02478D38-C3F9-4efb-9B51-7695ECA05670}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{02478D38-C3F9-4efb-9B51-7695ECA05670}\ not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{3706EE7C-3CAD-445D-8A43-03EBC3B75908}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3706EE7C-3CAD-445D-8A43-03EBC3B75908}\ deleted successfully.
C:\Program Files (x86)\Expat Shield\HssIE\ExpatIE.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\ deleted successfully.
C:\Program Files (x86)\Java\jre6\bin\ssv.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{a060276a-53be-45ec-8ebe-b94b1e803179}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{FD72061E-9FDE-484D-A58A-0BAB4151CAD8}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{FD72061E-9FDE-484D-A58A-0BAB4151CAD8}\ deleted successfully.
C:\Program Files (x86)\Yontoo\YontooIEClient.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\MRI_DISABLED\ deleted successfully.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{A060276A-53BE-45EC-8EBE-B94B1E803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{A060276A-53BE-45EC-8EBE-B94B1E803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\google.com\www\ deleted successfully.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Ranges\Range1\\http deleted successfully.
Starting removal of ActiveX control {8AD9C840-044E-11D1-B3E9-00805F499D93}
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Starting removal of ActiveX control {CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ not found.
Starting removal of ActiveX control {8AD9C840-044E-11D1-B3E9-00805F499D93}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Starting removal of ActiveX control {CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ not found.
Starting removal of ActiveX control {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ not found.
========== FILES ==========
< ipconfig /flushdns /c >
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
C:\Users\Owner\Downloads\cmd.bat deleted successfully.
C:\Users\Owner\Downloads\cmd.txt deleted successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca}\U folder moved successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca}\L folder moved successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca} folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca}\U folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca}\L folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca} folder moved successfully.
========== REGISTRY ==========
========== COMMANDS ==========
C:\Windows\System32\drivers\etc\Hosts moved successfully.
HOSTS file reset successfully
[EMPTYTEMP]
User: Alex
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Guest
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Owner
->Temp folder emptied: 69719587 bytes
->Temporary Internet Files folder emptied: 16441566 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 0 bytes
->Apple Safari cache emptied: 0 bytes
->Flash cache emptied: 706 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 270637 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 0 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 44196 bytes
RecycleBin emptied: 1910 bytes
Total Files Cleaned = 82.00 mb
Restore point Set: OTL Restore Point
OTL by OldTimer - Version 3.2.54.0 log created on 07232012_131413
Files\Folders moved on Reboot...
C:\Users\Owner\AppData\Local\Temp\FXSAPIDebugLogFile.txt moved successfully.
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF057D0C41F158BEC3.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF36BC3D6315AEE93F.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF601FFF028478AEDF.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DFE3FB71582E9CE58D.TMP not found!
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\SuggestedSites.dat moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\fastbutton[2].htm moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\page__pid__2181066[1].htm moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\AntiPhishing\2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2.dat moved successfully.
File\Folder C:\Windows\temp\fb_2532.lck not found!
File\Folder C:\Windows\temp\fc8bcbef-ca97-485b-9f8a-5831c7d1c46b.tmp not found!
File\Folder C:\Windows\temp\fla761.tmp not found!
PendingFileRenameOperations files...
File C:\Users\Owner\AppData\Local\Temp\FXSAPIDebugLogFile.txt not found!
File C:\Users\Owner\AppData\Local\Temp\~DF057D0C41F158BEC3.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DF36BC3D6315AEE93F.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DF601FFF028478AEDF.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DFE3FB71582E9CE58D.TMP not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\SuggestedSites.dat not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\fastbutton[2].htm not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\page__pid__2181066[1].htm not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\AntiPhishing\2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2.dat not found!
File C:\Windows\temp\fb_2532.lck not found!
File C:\Windows\temp\fc8bcbef-ca97-485b-9f8a-5831c7d1c46b.tmp not found!
File C:\Windows\temp\fla761.tmp not found!
Registry entries deleted on Reboot...
#18
![Search Engine re-directs [Closed]: post #18](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 04:06 PM
Posted 23 July 2012 - 04:06 PM

========== OTL ==========
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{2fa28606-de77-4029-af96-b231e3b8f827}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2fa28606-de77-4029-af96-b231e3b8f827}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\URLSearchHooks\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ deleted successfully.
C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{2fa28606-de77-4029-af96-b231e3b8f827}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2fa28606-de77-4029-af96-b231e3b8f827}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{4EF9D70C-FC56-C049-5A8E-29ABC30AA288}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{4EF9D70C-FC56-C049-5A8E-29ABC30AA288}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\URLSearchHooks\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\SearchScopes\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{afdbddaa-5d3f-42ee-b79c-185a7020515b}\ not found.
Registry key HKEY_LOCAL_MACHINE\Software\MozillaPlugins\@java.com/JavaPlugin\ deleted successfully.
C:\Program Files (x86)\Java\jre6\bin\new_plugin\npjp2.dll moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\META-INF folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\imgs\flgs folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\imgs folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content\images folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected]\content folder moved successfully.
C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\extensions\extensions\[email protected] folder moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{02478D38-C3F9-4efb-9B51-7695ECA05670}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{02478D38-C3F9-4efb-9B51-7695ECA05670}\ not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{3706EE7C-3CAD-445D-8A43-03EBC3B75908}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3706EE7C-3CAD-445D-8A43-03EBC3B75908}\ deleted successfully.
C:\Program Files (x86)\Expat Shield\HssIE\ExpatIE.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\ deleted successfully.
C:\Program Files (x86)\Java\jre6\bin\ssv.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{a060276a-53be-45ec-8ebe-b94b1e803179}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{FD72061E-9FDE-484D-A58A-0BAB4151CAD8}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{FD72061E-9FDE-484D-A58A-0BAB4151CAD8}\ deleted successfully.
C:\Program Files (x86)\Yontoo\YontooIEClient.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\MRI_DISABLED\ deleted successfully.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{a060276a-53be-45ec-8ebe-b94b1e803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{a060276a-53be-45ec-8ebe-b94b1e803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{A060276A-53BE-45EC-8EBE-B94B1E803179} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{A060276A-53BE-45EC-8EBE-B94B1E803179}\ not found.
File C:\Program Files (x86)\Expat_Shield\prxtbExpa.dll not found.
Registry key HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\google.com\www\ deleted successfully.
Registry value HKEY_USERS\S-1-5-21-4285407733-2807479433-3049265212-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Ranges\Range1\\http deleted successfully.
Starting removal of ActiveX control {8AD9C840-044E-11D1-B3E9-00805F499D93}
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Starting removal of ActiveX control {CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}\ not found.
Starting removal of ActiveX control {8AD9C840-044E-11D1-B3E9-00805F499D93}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D93}\ not found.
Starting removal of ActiveX control {CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_CURRENT_USER\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-0016-0000-0030-ABCDEFFEDCBA}\ not found.
Starting removal of ActiveX control {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}\ not found.
========== FILES ==========
< ipconfig /flushdns /c >
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
C:\Users\Owner\Downloads\cmd.bat deleted successfully.
C:\Users\Owner\Downloads\cmd.txt deleted successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca}\U folder moved successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca}\L folder moved successfully.
C:\Windows\Installer\{507829e3-236d-f5e0-6282-8b3c371a03ca} folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca}\U folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca}\L folder moved successfully.
C:\Users\Owner\AppData\Local\{507829e3-236d-f5e0-6282-8b3c371a03ca} folder moved successfully.
========== REGISTRY ==========
========== COMMANDS ==========
C:\Windows\System32\drivers\etc\Hosts moved successfully.
HOSTS file reset successfully
[EMPTYTEMP]
User: Alex
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Guest
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Owner
->Temp folder emptied: 69719587 bytes
->Temporary Internet Files folder emptied: 16441566 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 0 bytes
->Apple Safari cache emptied: 0 bytes
->Flash cache emptied: 706 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 270637 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 0 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 44196 bytes
RecycleBin emptied: 1910 bytes
Total Files Cleaned = 82.00 mb
Restore point Set: OTL Restore Point
OTL by OldTimer - Version 3.2.54.0 log created on 07232012_131413
Files\Folders moved on Reboot...
C:\Users\Owner\AppData\Local\Temp\FXSAPIDebugLogFile.txt moved successfully.
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF057D0C41F158BEC3.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF36BC3D6315AEE93F.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DF601FFF028478AEDF.TMP not found!
File\Folder C:\Users\Owner\AppData\Local\Temp\~DFE3FB71582E9CE58D.TMP not found!
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\SuggestedSites.dat moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\fastbutton[2].htm moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\page__pid__2181066[1].htm moved successfully.
C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\AntiPhishing\2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2.dat moved successfully.
File\Folder C:\Windows\temp\fb_2532.lck not found!
File\Folder C:\Windows\temp\fc8bcbef-ca97-485b-9f8a-5831c7d1c46b.tmp not found!
File\Folder C:\Windows\temp\fla761.tmp not found!
PendingFileRenameOperations files...
File C:\Users\Owner\AppData\Local\Temp\FXSAPIDebugLogFile.txt not found!
File C:\Users\Owner\AppData\Local\Temp\~DF057D0C41F158BEC3.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DF36BC3D6315AEE93F.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DF601FFF028478AEDF.TMP not found!
File C:\Users\Owner\AppData\Local\Temp\~DFE3FB71582E9CE58D.TMP not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\SuggestedSites.dat not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\fastbutton[2].htm not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\U8R9958N\page__pid__2181066[1].htm not found!
File C:\Users\Owner\AppData\Local\Microsoft\Windows\Temporary Internet Files\AntiPhishing\2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2.dat not found!
File C:\Windows\temp\fb_2532.lck not found!
File C:\Windows\temp\fc8bcbef-ca97-485b-9f8a-5831c7d1c46b.tmp not found!
File C:\Windows\temp\fla761.tmp not found!
Registry entries deleted on Reboot...
#19
![Search Engine re-directs [Closed]: post #19](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 04:30 PM
Posted 23 July 2012 - 04:30 PM

I see that Microsoft Security Essentials is your AV and Comodo your Firewall. Very good choices.
So we need to remove AVG remnants from your machine.
Please download this tool (AVG Remover 64 bit) and run it.
You also have iolo products, SpyBot S & D, and MalwareBytes' as resident anti spyware programs.
Please uninstall the iolo products and SpyBot S & D they are not as good as MalwareBytes' and they are resource hogs.
Once you have removed AVG remnants and uninstalled the iolo products and SpyBot S & D please run OTL, select All Users and 64-Bit and then click Quick Scan and post the OTL.txt file that is produced.
#20
![Search Engine re-directs [Closed]: post #20](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 05:48 PM
Posted 23 July 2012 - 05:48 PM

#21
![Search Engine re-directs [Closed]: post #21](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 06:15 PM
Posted 23 July 2012 - 06:15 PM

Download the adwCleaner
- Run the Tool
Windows Vista and Windows 7 users:
Right click in the adwCleaner.exe and select the option
- Select the Delete button.
- When the scan completes, it will open a notepad windows.
- Please, copy the content of this file in your next reply.
Please post the log.
#22
![Search Engine re-directs [Closed]: post #22](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 09:11 PM
Posted 23 July 2012 - 09:11 PM

# Updated 20/07/2012 by Xplode
# Operating system : Windows 7 Home Premium Service Pack 1 (64 bits)
# User : Owner - OWNER-HP
# Running from : C:\Users\Owner\Desktop\adwcleaner.exe
# Option [Delete]
***** [Services] *****
***** [Files / Folders] *****
Folder Deleted : C:\Users\Owner\AppData\Local\Conduit
Folder Deleted : C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\cjpglkicenollcignonpgiafdgfeehoj
Folder Deleted : C:\Users\Owner\AppData\LocalLow\BabylonToolbar
Folder Deleted : C:\Users\Owner\AppData\LocalLow\Conduit
Folder Deleted : C:\Users\Owner\AppData\LocalLow\Funmoods
Folder Deleted : C:\Users\Owner\AppData\LocalLow\PriceGong
Folder Deleted : C:\Users\Alex\AppData\LocalLow\Conduit
Folder Deleted : C:\Users\Alex\AppData\LocalLow\PriceGong
Folder Deleted : C:\ProgramData\Tarma Installer
Folder Deleted : C:\Program Files (x86)\Conduit
Folder Deleted : C:\Program Files (x86)\Yontoo
File Deleted : C:\Users\Owner\AppData\Local\funmoods-speeddial.crx
File Deleted : C:\Users\Public\Desktop\eBay.lnk
File Deleted : C:\ProgramData\Microsoft\Windows\Start Menu\Programs\eBay.lnk
***** [Registry] *****
[*] Key Deleted : HKLM\SOFTWARE\Classes\Toolbar.CT2549263
Key Deleted : HKCU\Software\AppDataLow\Software\Conduit
Key Deleted : HKCU\Software\AppDataLow\Software\ConduitSearchScopes
Key Deleted : HKCU\Software\AppDataLow\Software\PriceGong
Key Deleted : HKCU\Software\AppDataLow\Toolbar
Key Deleted : HKCU\Software\Funmoods
Key Deleted : HKLM\SOFTWARE\Classes\AppID\escort.DLL
Key Deleted : HKLM\SOFTWARE\Classes\AppID\escortApp.DLL
Key Deleted : HKLM\SOFTWARE\Classes\AppID\escortEng.DLL
Key Deleted : HKLM\SOFTWARE\Classes\AppID\escorTlbr.DLL
Key Deleted : HKLM\SOFTWARE\Classes\AppID\esrv.EXE
Key Deleted : HKLM\SOFTWARE\Classes\AppID\YontooIEClient.DLL
Key Deleted : HKLM\SOFTWARE\Classes\YontooIEClient.Api
Key Deleted : HKLM\SOFTWARE\Classes\YontooIEClient.Api.1
Key Deleted : HKLM\SOFTWARE\Classes\YontooIEClient.Layers
Key Deleted : HKLM\SOFTWARE\Classes\YontooIEClient.Layers.1
Key Deleted : HKLM\SOFTWARE\Conduit
Key Deleted : HKLM\SOFTWARE\Funmoods
Key Deleted : HKLM\SOFTWARE\Google\Chrome\Extensions\cjpglkicenollcignonpgiafdgfeehoj
Key Deleted : HKLM\SOFTWARE\Google\Chrome\Extensions\niapdbllcanepiiimjjndipklodoedlc
Key Deleted : HKLM\SOFTWARE\Iminent
[x64] Key Deleted : HKLM\SOFTWARE\Google\Chrome\Extensions\cjpglkicenollcignonpgiafdgfeehoj
[x64] Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{889DF117-14D1-44EE-9F31-C5FB5D47F68B}
***** [Registre - GUID] *****
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{4E1E9D45-8BF9-4139-915C-9F83CC3D5921}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{608D3067-77E8-463D-9084-908966806826}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{960DF771-CFCB-4E53-A5B5-6EF2BBE6E706}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{B12E99ED-69BD-437C-86BE-C862B9E5444D}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{CFDAFE39-20CE-451D-BD45-A37452F39CF0}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{D7EE8177-D51E-4F89-92B6-83EA2EC40800}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{EA28B360-05E0-4F93-8150-02891F1D8D3C}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{10DE7085-6A1E-4D41-A7BF-9AF93E351401}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{3C471948-F874-49F5-B338-4F214A2EE0B1}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{80922EE0-8A76-46AE-95D5-BD3C3FE0708D}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{99066096-8989-4612-841F-621A01D54AD7}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{DF7770F7-832F-4BDF-B144-100EDDD0C3AE}
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{FE9271F2-6EFD-44B0-A826-84C829536E93}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{10DE7085-6A1E-4D41-A7BF-9AF93E351401}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{1AD27395-1659-4DFF-A319-2CFA243861A5}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{BCFF5F55-6F44-11D2-86F8-00104B265ED5}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{2D5E2D34-BED5-4B9F-9793-A31E26E6806E}
Key Deleted : HKLM\SOFTWARE\Classes\TypeLib\{D372567D-67C1-4B29-B3F0-159B52B3E967}
Key Deleted : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{2FA28606-DE77-4029-AF96-B231E3B8F827}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\{DF7770F7-832F-4BDF-B144-100EDDD0C3AE}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Settings\{97F2FF5B-260C-4CCF-834A-2DDA4E29E39E}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2EECD738-5844-4A99-B4B6-146BF802613B}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{97F2FF5B-260C-4CCF-834A-2DDA4E29E39E}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{98889811-442D-49DD-99D7-DC866BE87DBC}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DF7770F7-832F-4BDF-B144-100EDDD0C3AE}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{10DE7085-6A1E-4D41-A7BF-9AF93E351401}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{1AD27395-1659-4DFF-A319-2CFA243861A5}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{23C70BCA-6E23-4A65-AD2E-1389062074F1}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{23D8EEF7-0E13-4000-B9C4-6603C1E912D1}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{295CACB4-51F5-46FD-914E-C72BAAE1B672}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{2CE5C4B9-6DBE-4528-96FA-C9FF38EF1762}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{34C1FDF7-02C1-4F23-B393-F48B16E071D1}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{54291324-7A3D-4F11-B707-3FB6A2C97BD9}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{59C63F11-D4E5-46E7-9B8A-EE158DCA83A8}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{5DA22CBD-0029-4A09-B757-CF0FAFC488ED}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{77A6E7D4-4A83-4A9B-A2A0-EF3B125DC29D}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{BCFF5F55-6F44-11D2-86F8-00104B265ED5}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{C0585B2F-74D7-4734-88DE-6C150C5D4036}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{D8242E89-2F81-484A-AE5B-BA8CAD5B7347}
[x64] Key Deleted : HKLM\SOFTWARE\Classes\Interface\{EF0588D6-1621-4A75-B8BE-F4BC34794136}
***** [Internet Browsers] *****
-\\ Internet Explorer v8.0.7601.17514
Replaced : [HKLM\SOFTWARE\Microsoft\Internet Explorer\AboutURls - Tabs] = hxxp://start.funmoods.com/?f=2&a=nv1&chnl=nv1&cd=2XzuyEtN2Y1L1QzuyCyE0DyE0D0AtBtByCyC0EzytC0FyByBtN0D0Tzu0CtBtDtDtN1L2XzutBtFtCtFtDtFtAtDtC&cr=868146021 --> hxxp://www.google.com
-\\ Google Chrome v20.0.1132.57
File : C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Preferences
Deleted : "homepage": "hxxp://start.funmoods.com/?f=1&a=nv1&chnl=nv1&cd=2XzuyEtN2Y1L1QzuyCyE0DyE0D0AtBtB[...]
Deleted : "urls_to_restore_on_startup": [ "hxxp://search.babylon.com/?affID=113959&tt=270612_518&babs[...]
Deleted : "baseUrl": "hxxp://start.funmoods.com/results.php?",
Deleted : "update_url": "hxxp://update.funmoods.com/speeddial/update.xml?bu=st",
Deleted : "description": "The fastest way to search the web.",
Deleted : "homepage": "hxxp://start.funmoods.com/?f=1&a=nv1&chnl=nv1&cd=2XzuyEtN2Y1L1QzuyCyE0DyE0D0AtBtByCy[...]
Deleted : "urls_to_restore_on_startup": [ "hxxp://search.babylon.com/?affID=113959&tt=270612_518&babsrc=[...]
*************************
AdwCleaner[S1].txt - [7566 octets] - [23/07/2012 20:03:51]
########## EOF - C:\AdwCleaner[S1].txt - [7694 octets] ##########
#23
![Search Engine re-directs [Closed]: post #23](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 23 July 2012 - 09:15 PM
Posted 23 July 2012 - 09:15 PM

- On the desktop click the My Computer icon
- Right click your main drive (I am on C) and select properties
- Select the tools tab
- Select error checking
- Place a tick in both boxes
- Press start
- You will get a warning that it needs to reboot to continue
- Allow it to do so
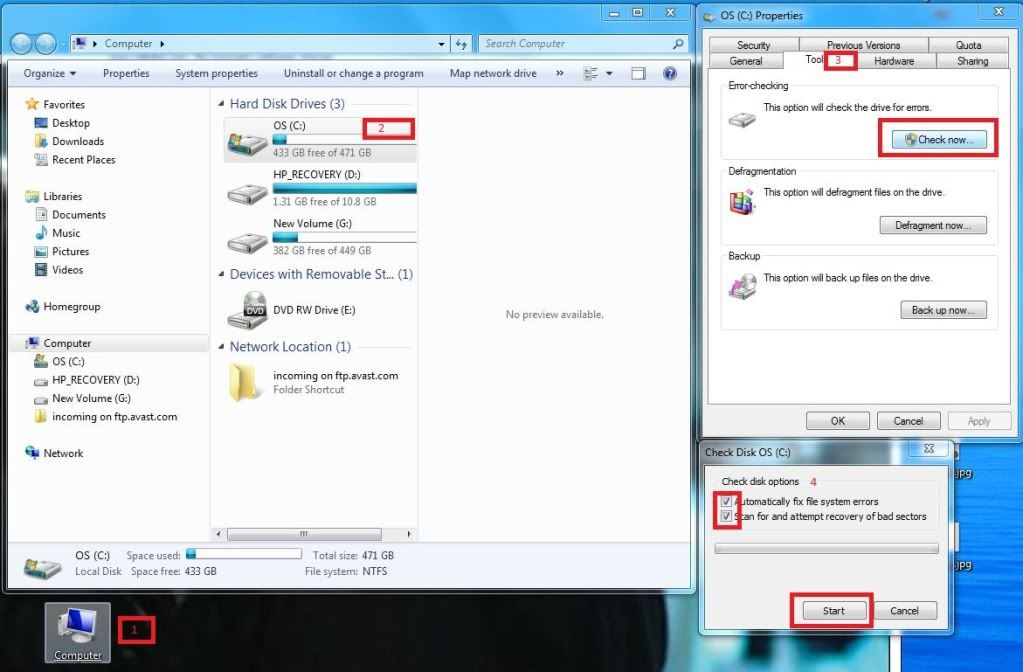
Once completed
Run an elevated command prompt
Go to Start, All programs, Accessories
Right click command prompt and select run as administrator
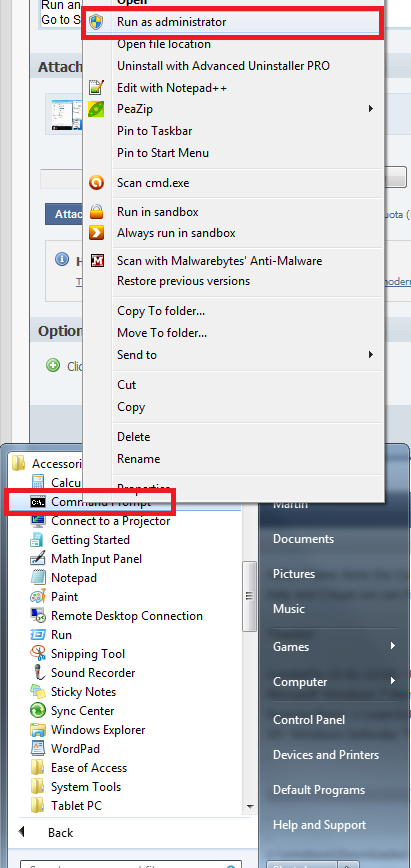
In the black box that opens type or copy and paste the following command and press enter:
sfc /scannow
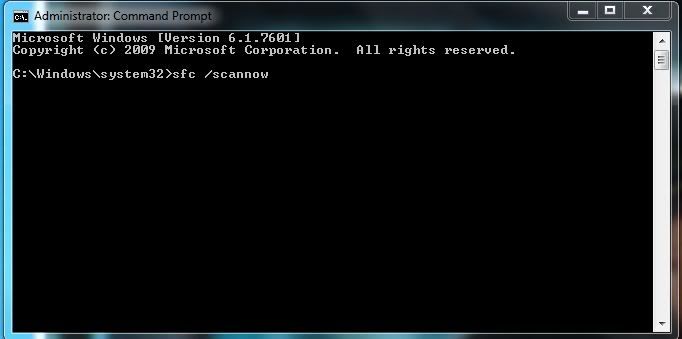
After all this is completed could you update me on the problems being experienced
#24
![Search Engine re-directs [Closed]: post #24](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 July 2012 - 10:19 PM
Posted 24 July 2012 - 10:19 PM

#25
![Search Engine re-directs [Closed]: post #25](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 July 2012 - 05:47 AM
Posted 25 July 2012 - 05:47 AM

#26
![Search Engine re-directs [Closed]: post #26](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 27 July 2012 - 08:35 PM
Posted 27 July 2012 - 08:35 PM

#27
![Search Engine re-directs [Closed]: post #27](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 27 July 2012 - 08:55 PM
Posted 27 July 2012 - 08:55 PM

The following lines in the TDSSKiller log point this issue out:
14:32:46.0830 6948 C:\Program Files\Belkin\Belkin USB Print and Storage Center\BkBackupScheduler.exe - copied to quarantine
14:32:46.0830 6948 Belkin Local Backup Service ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:46.0846 6948 C:\Program Files\Belkin\Belkin USB Print and Storage Center\Bkapcs.exe - copied to quarantine
14:32:46.0846 6948 Belkin Network USB Helper ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:46.0893 6948 C:\Program Files (x86)\Kaseya\ENDSGH33822833567552\KasAVSrv.exe - copied to quarantine
14:32:46.0893 6948 KaseyaAVService ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:46.0971 6948 C:\Program Files (x86)\Common Files\LightScribe\LSSrvc.exe - copied to quarantine
14:32:46.0971 6948 LightScribeService ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:47.0017 6948 C:\Windows\system32\HPZinw12.dll - copied to quarantine
14:32:47.0017 6948 Net Driver HPZ12 ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:47.0033 6948 C:\Windows\system32\HPZipm12.dll - copied to quarantine
14:32:47.0033 6948 Pml Driver HPZ12 ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:47.0111 6948 C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\VehStatusBroadcaster.exe - copied to quarantine
14:32:47.0111 6948 VehStatusBroadcaster ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:47.0220 6948 C:\Program Files\Intel\WiMAX\Bin\AppSrv.exe - copied to quarantine
14:32:47.0220 6948 WiMAXAppSrv ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
14:32:47.0251 6948 C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\ZollData.Dispatch.Services.ZollDataTripProp.exe - copied to quarantine
14:32:47.0251 6948 ZOLL Data Trip Prop ( UnsignedFile.Multi.Generic ) - User select action: Quarantine
0
Let's get information on quarantine to see if we can manually recover the files:
Download this simple little tool 'TDDS Qlook' to your desktop.
Run TDSSQlook
It will open and you will see three options.
Type A
Press Enter
A log will be produced named TDSSQ.txt
Copy and paste the contents into your next post.
Also check to see if you have a restore point prior to when your daughter was on the computer and downloaded the infection. Please tell me what restore point dates you have available just prior.
#28
![Search Engine re-directs [Closed]: post #28](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 28 July 2012 - 10:36 AM
Posted 28 July 2012 - 10:36 AM

TDSS Qlook Version 1.0.0.5 - Owner - Sat 07/28/2012 - 9:35:26.59.
Microsoft Windows 7 Home Premium 6.1.7601 Service Pack 1
***** START SCAN Sat 07/28/2012 9:35:33.87 *****
---------- TDSSKiller logs ----------
TDSSKiller.2.7.47.0_23.07.2012_14.31.10_log.txt
---------- TDSSStarter logs ----------
---------- DIR LIST ----------
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000\tsk0000.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000\object.ini
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000\tsk0000.dta
C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000\tsk0000.ini
---------- INI FILES ----------
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000\object.ini
[InfectedObject]
Type: Service
Name: AniImport
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\AniImport.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0000\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\AniImport.exe
md5: 0e310da8542df1cb94edf2f534be1172
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Belkin Local Backup Service
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Belkin\Belkin USB Print and Storage Center\BkBackupScheduler.exe" /service
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0001\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Belkin\Belkin USB Print and Storage Center\BkBackupScheduler.exe
md5: 299e54db3638a18e47bd3a2d2ef499f7
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Belkin Network USB Helper
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Belkin\Belkin USB Print and Storage Center\Bkapcs.exe" /service
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0002\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Belkin\Belkin USB Print and Storage Center\Bkapcs.exe
md5: e62a04d615a8cac83601e1f07c010d3c
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000\object.ini
[InfectedObject]
Type: Service
Name: DMAgent
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Intel\WiMAX\Bin\DMAgent.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0003\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Intel\WiMAX\Bin\DMAgent.exe
md5: 61458c120cddfe7514e2db125568ca59
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000\object.ini
[InfectedObject]
Type: Service
Name: hpqcxs08
Type: n/a (0x20)
Start: Demand (0x3)
ImagePath: %SystemRoot%\system32\svchost.exe -k hpdevmgmt
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0004\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\hpqcxs08.dll
md5: 0a3c6aa4a9fc38c20ba4eac2c3351c05
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000\object.ini
[InfectedObject]
Type: Service
Name: hpqddsvc
Type: n/a (0x20)
Start: Auto (0x2)
ImagePath: %SystemRoot%\system32\svchost.exe -k hpdevmgmt
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0005\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\hpqddsvc.dll
md5: f3f72a2a86c22610bca5439fa789dd52
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000\object.ini
[InfectedObject]
Type: Service
Name: HPSLPSVC
Type: n/a (0x20)
Start: Auto (0x2)
ImagePath: %SystemRoot%\system32\svchost.exe -k HPService
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0006\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\HPSLPSVC64.DLL
md5: f37882f128efacefe353e0bae2766909
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000\object.ini
[InfectedObject]
Type: Service
Name: KaseyaAVService
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files (x86)\Kaseya\ENDSGH33822833567552\KasAVSrv.exe" -s
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0007\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Kaseya\ENDSGH33822833567552\KasAVSrv.exe
md5: 3419fe00642ec4d51fcd80de9339cccb
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000\object.ini
[InfectedObject]
Type: Service
Name: LightScribeService
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files (x86)\Common Files\LightScribe\LSSrvc.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0008\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Common Files\LightScribe\LSSrvc.exe
md5: fcbdcc6f1801e32244235608e1277752
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Net Driver HPZ12
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k HPZ12
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0009\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Windows\system32\HPZinw12.dll
md5: 2334dc48997ba203b794df3ee70521db
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Pml Driver HPZ12
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k HPZ12
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0010\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Windows\system32\HPZipm12.dll
md5: ac78df349f0e4cfb8b667c0cfff83cce
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000\object.ini
[InfectedObject]
Type: Service
Name: VehStatusBroadcaster
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\VehStatusBroadcaster.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0011\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\VehStatusBroadcaster.exe
md5: 481f06ae7dfc57788e8897e3deddb3ef
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000\object.ini
[InfectedObject]
Type: Service
Name: WiMAXAppSrv
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Intel\WiMAX\Bin\AppSrv.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0012\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Intel\WiMAX\Bin\AppSrv.exe
md5: 8686e96e13f41ac9806a79ca8004feee
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000\object.ini
[InfectedObject]
Type: Service
Name: ZOLL Data Trip Prop
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\ZollData.Dispatch.Services.ZollDataTripProp.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0013\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\ZollData.Dispatch.Services.ZollDataTripProp.exe
md5: a52d02a21908e8e29c60cc5761561862
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000\object.ini
[InfectedObject]
Type: Service
Name: AniImport
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\AniImport.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0014\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\AniImport.exe
md5: 0e310da8542df1cb94edf2f534be1172
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000\object.ini
[InfectedObject]
Type: Service
Name: DMAgent
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Intel\WiMAX\Bin\DMAgent.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0015\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Intel\WiMAX\Bin\DMAgent.exe
md5: 61458c120cddfe7514e2db125568ca59
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000\object.ini
[InfectedObject]
Type: Service
Name: hpqcxs08
Type: n/a (0x20)
Start: Demand (0x3)
ImagePath: %SystemRoot%\system32\svchost.exe -k hpdevmgmt
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0016\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\hpqcxs08.dll
md5: 0a3c6aa4a9fc38c20ba4eac2c3351c05
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000\object.ini
[InfectedObject]
Type: Service
Name: hpqddsvc
Type: n/a (0x20)
Start: Auto (0x2)
ImagePath: %SystemRoot%\system32\svchost.exe -k hpdevmgmt
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0017\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\hpqddsvc.dll
md5: f3f72a2a86c22610bca5439fa789dd52
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000\object.ini
[InfectedObject]
Type: Service
Name: HPSLPSVC
Type: n/a (0x20)
Start: Auto (0x2)
ImagePath: %SystemRoot%\system32\svchost.exe -k HPService
=== C:\TDSSKiller_Quarantine\23.07.2012_11.01.27\susp0018\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\HP\Digital Imaging\bin\HPSLPSVC64.DLL
md5: f37882f128efacefe353e0bae2766909
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Belkin Local Backup Service
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Belkin\Belkin USB Print and Storage Center\BkBackupScheduler.exe" /service
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0000\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Belkin\Belkin USB Print and Storage Center\BkBackupScheduler.exe
md5: 299e54db3638a18e47bd3a2d2ef499f7
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Belkin Network USB Helper
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Belkin\Belkin USB Print and Storage Center\Bkapcs.exe" /service
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0001\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Belkin\Belkin USB Print and Storage Center\Bkapcs.exe
md5: e62a04d615a8cac83601e1f07c010d3c
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000\object.ini
[InfectedObject]
Type: Service
Name: KaseyaAVService
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files (x86)\Kaseya\ENDSGH33822833567552\KasAVSrv.exe" -s
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0002\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Kaseya\ENDSGH33822833567552\KasAVSrv.exe
md5: 3419fe00642ec4d51fcd80de9339cccb
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000\object.ini
[InfectedObject]
Type: Service
Name: LightScribeService
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files (x86)\Common Files\LightScribe\LSSrvc.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0003\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Common Files\LightScribe\LSSrvc.exe
md5: fcbdcc6f1801e32244235608e1277752
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Net Driver HPZ12
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k HPZ12
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0004\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Windows\system32\HPZinw12.dll
md5: 2334dc48997ba203b794df3ee70521db
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000\object.ini
[InfectedObject]
Type: Service
Name: Pml Driver HPZ12
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k HPZ12
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0005\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Windows\system32\HPZipm12.dll
md5: ac78df349f0e4cfb8b667c0cfff83cce
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000\object.ini
[InfectedObject]
Type: Service
Name: VehStatusBroadcaster
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\VehStatusBroadcaster.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0006\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\VehStatusBroadcaster.exe
md5: 481f06ae7dfc57788e8897e3deddb3ef
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000\object.ini
[InfectedObject]
Type: Service
Name: WiMAXAppSrv
Type: n/a (0x10)
Start: Auto (0x2)
ImagePath: "C:\Program Files\Intel\WiMAX\Bin\AppSrv.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0007\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files\Intel\WiMAX\Bin\AppSrv.exe
md5: 8686e96e13f41ac9806a79ca8004feee
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\object.ini
[InfectedObject]
Verdict: UnsignedFile.Multi.Generic
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000\object.ini
[InfectedObject]
Type: Service
Name: ZOLL Data Trip Prop
Type: n/a (0x10)
Start: Demand (0x3)
ImagePath: "C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\ZollData.Dispatch.Services.ZollDataTripProp.exe"
=== C:\TDSSKiller_Quarantine\23.07.2012_14.31.11\susp0008\svc0000\tsk0000.ini
[InfectedFile]
Type: Raw image
Src: C:\Program Files (x86)\Pinpoint Technologies, Inc\RightCAD\ZollData.Dispatch.Services.ZollDataTripProp.exe
md5: a52d02a21908e8e29c60cc5761561862
***** END SCAN Sat 07/28/2012 9:35:34.71 *****
#29
![Search Engine re-directs [Closed]: post #29](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 28 July 2012 - 11:42 AM
Posted 28 July 2012 - 11:42 AM

Also what is the exact error you get on startup? What is it looking for??
Regards,
CompCav
#30
![Search Engine re-directs [Closed]: post #30](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 29 July 2012 - 10:04 AM
Posted 29 July 2012 - 10:04 AM

I couldn t save the errors as pictures or copy and paste here, so I screen shot them and attached it to a word document its attached.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

