ComboFix 12-09-18.07 - User 09/19/2012 15:20:19.1.2 - x86
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.1982.1475 [GMT -5:00]
Running from: c:\documents and settings\User\Desktop\ComboFix.exe
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\44ac61mpu26vuwj12330qu71824
c:\documents and settings\All Users\Favorites\Error Cleaner.url
c:\documents and settings\All Users\Favorites\Privacy Protector.url
c:\documents and settings\All Users\Favorites\Spyware&Malware Protection.url
c:\documents and settings\User\Application Data\Roaming
c:\documents and settings\User\Application Data\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\#piephahn.com\settings.sol
c:\documents and settings\User\Application Data\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol
c:\documents and settings\User\Desktop\Search.lnk
c:\documents and settings\User\Favorites\Error Cleaner.url
c:\documents and settings\User\Favorites\Privacy Protector.url
c:\documents and settings\User\Favorites\Spyware&Malware Protection.url
c:\documents and settings\User\Local Settings\Application Data\bb73b.dll
c:\documents and settings\User\Local Settings\Application Data\xry.exe
c:\windows\system32\AutoRun.inf
c:\windows\system32\PowerToyReadme.htm
c:\windows\system32\URTTemp
c:\windows\system32\URTTemp\fusion.dll
c:\windows\system32\URTTemp\mscoree.dll
c:\windows\system32\URTTemp\mscoree.dll.local
c:\windows\system32\URTTemp\mscorsn.dll
c:\windows\system32\URTTemp\mscorwks.dll
c:\windows\system32\URTTemp\msvcr71.dll
c:\windows\system32\URTTemp\regtlib.exe
.
.
((((((((((((((((((((((((( Files Created from 2012-08-19 to 2012-09-19 )))))))))))))))))))))))))))))))
.
.
2012-09-19 19:27 . 2012-09-19 19:27 -------- d-----w- C:\FRST
2012-09-04 20:02 . 2012-09-04 20:02 -------- d-----w- c:\documents and settings\User\Local Settings\Application Data\PCHealth
2012-08-28 12:18 . 2012-08-28 12:18 -------- d-----w- C:\ProgramData
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2012-06-28 17:47 . 2012-06-28 17:47 260 ----a-w- c:\windows\system32\cmdVBS.vbs
2012-06-28 17:47 . 2012-06-28 17:47 256 ----a-w- c:\windows\system32\MSIevent.bat
2012-08-10 14:54 . 2012-06-25 17:35 136672 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2009-01-16 13680640]
"nwiz"="nwiz.exe" [2009-01-16 1657376]
"RTHDCPL"="RTHDCPL.EXE" [2009-02-03 18085888]
"NvMediaCenter"="c:\windows\system32\NvMcTray.dll" [2009-01-16 86016]
"HP Software Update"="c:\program files\HP\HP Software Update\HPWuSchd2.exe" [2007-03-12 49152]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-05-26 413696]
"VERIZONDM"="c:\program files\VERIZONDM\bin\sprtcmd.exe" [2010-07-20 206120]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 9.0\Reader\Reader_sl.exe" [2009-10-03 35696]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2012-01-03 843712]
.
c:\documents and settings\All Users\Start Menu\Programs\Startup\
HP Digital Imaging Monitor.lnk - c:\program files\HP\Digital Imaging\bin\hpqtra08.exe [2007-3-11 210520]
Microsoft Office.lnk - c:\program files\Microsoft Office\Office10\OSA.EXE [2001-2-13 83360]
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
"FirewallOverride"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
"c:\\Program Files\\Messenger\\msmsgs.exe"=
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"50001:UDP"= 50001:UDP:IHA_MessageCenter
.
R2 IHA_MessageCenter;IHA_MessageCenter;c:\program files\Verizon\IHA_MessageCenter\Bin\Verizon_IHAMessageCenter.exe [12/12/2011 11:03 AM 352248]
R2 sprtsvc_verizondm;SupportSoft Sprocket Service (verizondm);c:\program files\VERIZONDM\bin\sprtsvc.exe [7/20/2010 1:29 AM 206120]
R2 tgsrvc_verizondm;SupportSoft Repair Service (verizondm);c:\program files\VERIZONDM\bin\tgsrvc.exe [7/20/2010 1:29 AM 185640]
R4 AvgTdiX;AVG Free8 Network Redirector;c:\windows\system32\Drivers\avgtdix.sys --> c:\windows\system32\Drivers\avgtdix.sys [?]
S3 ADM8511;ADMtek ADM8511/AN986 USB To Fast Ethernet Converter;c:\windows\system32\drivers\ADM8511.SYS [8/14/2009 6:09 PM 20160]
S3 MozillaMaintenance;Mozilla Maintenance Service;c:\program files\Mozilla Maintenance Service\maintenanceservice.exe [6/25/2012 12:35 PM 113120]
.
--- Other Services/Drivers In Memory ---
.
*Deregistered* - AvgLdx86
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\svchost]
HPZ12 REG_MULTI_SZ Pml Driver HPZ12 Net Driver HPZ12
hpdevmgmt REG_MULTI_SZ hpqcxs08 hpqddsvc
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://wapp.verizon.net/bookmarks/bmredir.asp?region=all&bw=fiber&cd=7.0unattached&bm=ho_central
uInternet Settings,ProxyOverride = *.local
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~3\Office10\EXCEL.EXE/3000
TCP: DhcpNameServer = 192.168.1.1
FF - ProfilePath - c:\documents and settings\User\Application Data\Mozilla\Firefox\Profiles\2uy0jkor.default\
FF - prefs.js: browser.startup.homepage - hxxp://wapp.verizon.net/bookmarks/bmredir.asp?region=all&bw=fiber&cd=7.0unattached&bm=ho_central
FF - prefs.js: network.proxy.type - 0
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer,
http://www.gmer.net
Rootkit scan 2012-09-19 15:23
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
Completion time: 2012-09-19 15:24:19
ComboFix-quarantined-files.txt 2012-09-19 20:24
.
Pre-Run: 225,675,018,240 bytes free
Post-Run: 228,027,895,808 bytes free
.
WindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Windows XP Media Center Edition" /noexecute=optin /fastdetect
.
- - End Of File - - 258C8FFF90ECDFEED82F14F033C7738F

 This topic is locked
This topic is locked


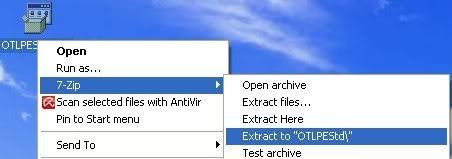
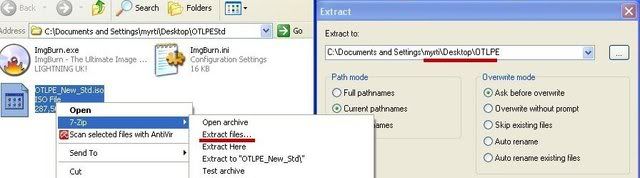
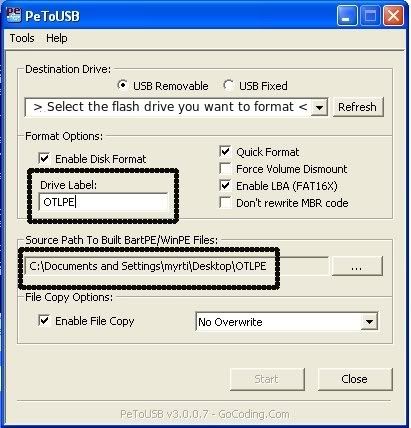
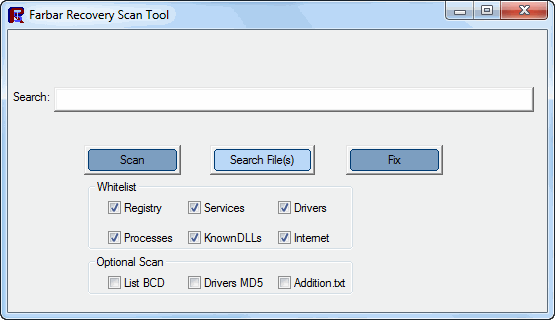














 Sign In
Sign In Create Account
Create Account

