Google Redirection problem; tutorial didn't work [Closed]
Started by
ron26
, Dec 12 2012 04:17 PM
#91
![Google Redirection problem; tutorial didn't work [Closed]: post #91](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 January 2013 - 01:22 PM
Posted 21 January 2013 - 01:22 PM

#92
![Google Redirection problem; tutorial didn't work [Closed]: post #92](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 January 2013 - 04:33 PM
Posted 21 January 2013 - 04:33 PM

OK, I apologize.  I ran these commands on my computer and they worked just fine.......but it had Vista on it. After your last post I fired up the XP machine and ran them again. They didn't work. Got the same error.
I ran these commands on my computer and they worked just fine.......but it had Vista on it. After your last post I fired up the XP machine and ran them again. They didn't work. Got the same error.
Evidently XP will not let you save the results of a reg query command anywhere other than the root drive (C:\). So I have rewritten the thing and tried it on my XP machine, several times, and it worked just fine.
I'm trying to find out what the LEGACY_WXCSVC key has in it. I don't have that key on my machine and I'm wondering if the malware renamed the key. If it is a legitimate key, put there by a program I don't have, we will need to try to manually set the permissions on the Root key and then see if we can merge the LEGACY_WSCSVC key.
I believe this is the last thing that we need to get sorted out. All of the last scans looked good. But the Security Center needs to be functioning.
Are we having fun yet?
Evidently XP will not let you save the results of a reg query command anywhere other than the root drive (C:\). So I have rewritten the thing and tried it on my XP machine, several times, and it worked just fine.
I'm trying to find out what the LEGACY_WXCSVC key has in it. I don't have that key on my machine and I'm wondering if the malware renamed the key. If it is a legitimate key, put there by a program I don't have, we will need to try to manually set the permissions on the Root key and then see if we can merge the LEGACY_WSCSVC key.
I believe this is the last thing that we need to get sorted out. All of the last scans looked good. But the Security Center needs to be functioning.
Are we having fun yet?
- Click Start, then click Run. A Run window will open.
- Type cmd.exe in the Open box and click the OK button. A Command Window will open.
- At the blinking cursor type or Copy and Paste the following, then press the Enter key:
reg query HKLM\system\currentcontrolset\enum\root\LEGACY_WXCSVC /s > C:\wxcsvc.txt
(Notice the space between WXCSVC and the /s, and between the /s and >, and > and C:\)
This will put a file in the root driectory (C:\) named wxcsvc.txt - Back at the blinking cursor, type the following and press the Enter key:
exit
The Command Window should close. - Click Start, then click Run. In the Open box type the following and click the OK button:
notepad C:\wxcsvc.txt - The wxcsvc.txt file should open on the desktop.
- Pleas post the contents of that file.
#93
![Google Redirection problem; tutorial didn't work [Closed]: post #93](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 January 2013 - 05:03 PM
Posted 21 January 2013 - 05:03 PM

Oh yeah, tons of fun! I've actually been delaying the fixes on purpose just to draw this out...
Okay, I followed all of those steps.
1) in the command window I got an error message (The system was unable to find the specified registry key or value)
2) I went ahead and it opened a word pad file...but it's blank.
Okay, I followed all of those steps.
1) in the command window I got an error message (The system was unable to find the specified registry key or value)
2) I went ahead and it opened a word pad file...but it's blank.
#94
![Google Redirection problem; tutorial didn't work [Closed]: post #94](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 22 January 2013 - 11:15 AM
Posted 22 January 2013 - 11:15 AM

OK, now the system can't find that key. This scan will tell me what registry keys are under the root key. I have changed the settings so please read them carefully.
 OTL Custom Scan
OTL Custom Scan
1. Please copy the text in the Quote box below, (Do Not copy the word Quote), and paste it in the box in OTL. To do that:
box in OTL. To do that:
2. Re-open OTL on the desktop. To do that:
1. Please copy the text in the Quote box below, (Do Not copy the word Quote), and paste it in the
 box in OTL. To do that:
box in OTL. To do that:- Highlight everything inside the quote box, (except the word Quote), right click the mouse and click Copy.
HKLM\SYSTEM\CurrentControlSet\Enum\Root
2. Re-open OTL on the desktop. To do that:
- Double click on the
 OTL icon to run it. (Vista / 7 Users:Right click on the icon and click Run as Administrator)
OTL icon to run it. (Vista / 7 Users:Right click on the icon and click Run as Administrator)
Make sure all other windows are closed. - You will see a console like the one below:

- Click the greyed out box beside None at the top of the console.<---VERY IMPORTANT
- Place the mouse pointer inside the
 box, right click and click Paste. This will put the above script inside OTL
box, right click and click Paste. This will put the above script inside OTL - Click the
 button. Do not change any settings unless otherwise told to do so.
button. Do not change any settings unless otherwise told to do so. - Let the scan run uninterrupted. The scan won't take long.
- When the scan completes, it will open OTL.Txt. This file is also saved in the same location as OTL (it should be on your desktop).
- Please copy the contents of this file and paste it into your reply. To do that:
- On the OTL.txt file Menu Bar click Edit then click Select All. This will highlight the contents of the file. Then click Copy.
- Right click inside the forum post window then click Paste.This will paste the contents of the OTL.txt file in the in the post window.
#95
![Google Redirection problem; tutorial didn't work [Closed]: post #95](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 January 2013 - 07:11 AM
Posted 25 January 2013 - 07:11 AM

OTL logfile created on: 1/25/2013 8:10:09 AM - Run 8
OTL by OldTimer - Version 3.2.69.0 Folder = C:\Documents and Settings\Ron (the merciful)\Desktop
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
509.98 Mb Total Physical Memory | 291.34 Mb Available Physical Memory | 57.13% Memory free
1.22 Gb Paging File | 0.81 Gb Available in Paging File | 66.26% Paging File free
Paging file location(s): C:\pagefile.sys 768 1536 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 70.65 Gb Total Space | 41.12 Gb Free Space | 58.20% Space Free | Partition Type: NTFS
Computer Name: RUSSO-DESKTOP | User Name: Ron (the merciful) | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: Off | File Age = 30 Days
========== Custom Scans ==========
< HKLM\SYSTEM\CurrentControlSet\Enum\Root >
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\*PNP0501]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\ACPI_HAL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\dmio]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\DNI_DNEMP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\ftdisk]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_32415076]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ADOBEFLASHPLAYERUPDATESVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AEGISP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_APPLE_MOBILE_DEVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_APPMGMT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ASWMBR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AUDIOSRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BEEP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BITS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BONJOUR_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BROWSER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CATCHME]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CDFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CLR_OPTIMIZATION_V2.0.50727_32]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_COMSYSAPP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CRYPTSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CVPND]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CVPNDRVA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DCOMLAUNCH]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DHCP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMADMIN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMBOOT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMLOAD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMSERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DNSCACHE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_EVENTSYSTEM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FASTFAT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FASTUSERSWITCHINGCOMPATIBILITY]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FIPS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FLEXNET_LICENSING_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FLTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FS_REC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_GPC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_GUPDATE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HELPSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HTTP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HTTPFILTER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IDRIVERT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IMAPISERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPNAT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPOD_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPSEC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_JAVAQUICKSTARTERSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_KSECDD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LANMANSERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LANMANWORKSTATION]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LMHOSTS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MBR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MODEM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MOUNTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPFILTER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSL7ABA7A5E]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSLAF9262DD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSLE01D262F]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXDAV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXSMB]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSDTC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSISERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSMPSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MUP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDIS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISTAPI]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISUIO]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDPROXY]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETBIOS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETBT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETMAN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NLA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NPFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NTFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NULL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OSE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PARTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PARVDM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PCIIDE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PML_DRIVER_HPZ12]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_POLICYAGENT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PROCEXP113]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PROTECTEDSTORAGE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASACD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASMAN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDBSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDPCDD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDPNP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXIO_UPNP_SERVER_9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXLIVESHARE9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXWATCH9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RPCSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RSVP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SAMSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SCHEDULE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SECLOGON]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SENS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SHELLHWDETECTION]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SPOOLER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SSDPSRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_STISVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SYSMONLOG]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TAPISRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TCPIP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TERMSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_THEMES]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TRKWKS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_UDFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_UPNPHOST]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VGA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VGASAVE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VOLSNAP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VSDATANT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_W32TIME]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WANARP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WEBCLIENT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WINMGMT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WS2IFSL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WUAUSERV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WZCSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MEDIA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_L2TPMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_NDISWANIP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PPPOEMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PPTPMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PSCHEDMP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PTIMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\NET]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\PORTS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDPDR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDP_KBD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDP_MOU]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\SYSTEM]
< End of report >
OTL by OldTimer - Version 3.2.69.0 Folder = C:\Documents and Settings\Ron (the merciful)\Desktop
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
509.98 Mb Total Physical Memory | 291.34 Mb Available Physical Memory | 57.13% Memory free
1.22 Gb Paging File | 0.81 Gb Available in Paging File | 66.26% Paging File free
Paging file location(s): C:\pagefile.sys 768 1536 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 70.65 Gb Total Space | 41.12 Gb Free Space | 58.20% Space Free | Partition Type: NTFS
Computer Name: RUSSO-DESKTOP | User Name: Ron (the merciful) | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: Off | File Age = 30 Days
========== Custom Scans ==========
< HKLM\SYSTEM\CurrentControlSet\Enum\Root >
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\*PNP0501]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\ACPI_HAL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\dmio]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\DNI_DNEMP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\ftdisk]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_32415076]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ADOBEFLASHPLAYERUPDATESVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AEGISP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_APPLE_MOBILE_DEVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_APPMGMT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ASWMBR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AUDIOSRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BEEP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BITS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BONJOUR_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_BROWSER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CATCHME]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CDFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CLR_OPTIMIZATION_V2.0.50727_32]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_COMSYSAPP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CRYPTSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CVPND]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CVPNDRVA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DCOMLAUNCH]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DHCP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMADMIN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMBOOT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMLOAD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DMSERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_DNSCACHE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_EVENTSYSTEM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FASTFAT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FASTUSERSWITCHINGCOMPATIBILITY]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FIPS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FLEXNET_LICENSING_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FLTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_FS_REC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_GPC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_GUPDATE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HELPSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HTTP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_HTTPFILTER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IDRIVERT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IMAPISERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPNAT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPOD_SERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPSEC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_JAVAQUICKSTARTERSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_KSECDD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LANMANSERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LANMANWORKSTATION]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_LMHOSTS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MBR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MODEM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MOUNTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPFILTER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSL7ABA7A5E]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSLAF9262DD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MPKSLE01D262F]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXDAV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MRXSMB]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSDTC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSISERVER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MSMPSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MUP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDIS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISTAPI]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDISUIO]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NDPROXY]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETBIOS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETBT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NETMAN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NLA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NPFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NTFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_NULL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OSE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PARTMGR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PARVDM]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PCIIDE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PML_DRIVER_HPZ12]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_POLICYAGENT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PROCEXP113]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_PROTECTEDSTORAGE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASACD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASMAN]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDBSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDPCDD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RDPNP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXIO_UPNP_SERVER_9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXLIVESHARE9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ROXWATCH9]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RPCSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RSVP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SAMSS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SCHEDULE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SECLOGON]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SENS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SHELLHWDETECTION]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SPOOLER]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SSDPSRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_STISVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SYSMONLOG]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TAPISRV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TCPIP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TERMSERVICE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_THEMES]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TRKWKS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_UDFS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_UPNPHOST]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VGA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VGASAVE]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VOLSNAP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_VSDATANT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_W32TIME]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WANARP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WEBCLIENT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WINMGMT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WS2IFSL]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WUAUSERV]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WZCSVC]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MEDIA]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_L2TPMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_NDISWANIP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PPPOEMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PPTPMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PSCHEDMP]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\MS_PTIMINIPORT]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\NET]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\PORTS]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDPDR]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDP_KBD]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\RDP_MOU]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\SYSTEM]
< End of report >
#96
![Google Redirection problem; tutorial didn't work [Closed]: post #96](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 January 2013 - 09:32 AM
Posted 25 January 2013 - 09:32 AM

Thanks Ron. OK, the LEGACY_WSCSVC key is not in the Root key, and our earlier attempts to give you permission to edit that key have not been successful. This time we are gonna do it manually. I'm sorry, but that means editing the registry.
If something is not clear or you don't understand something, stop and let me know.
Step-1
Back Up the WSCSVC_LEGACY registry key.
Step-2.
How To Take Ownership of a Registry key
NOTE: The images below show the name grooveDexter. Do Not type that in. Instead type what is in the instructions.
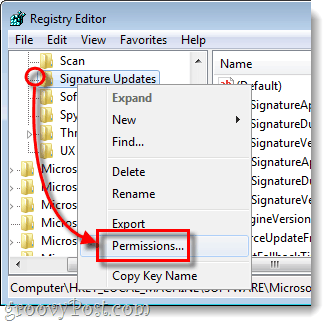
A.
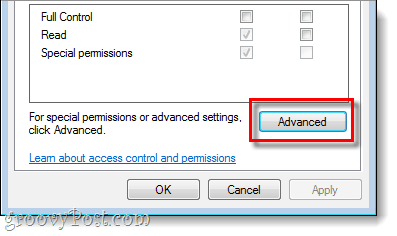
B.
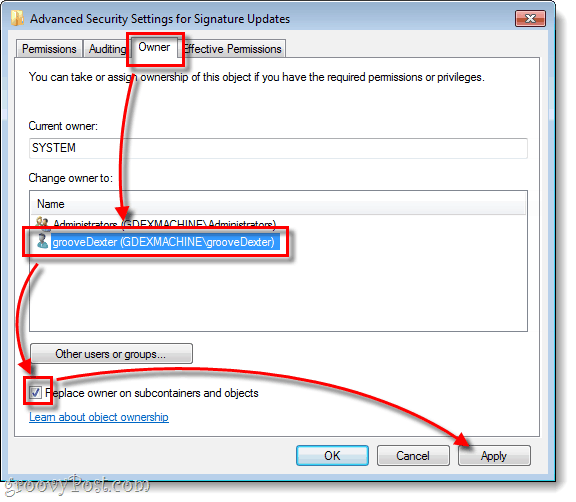
C.
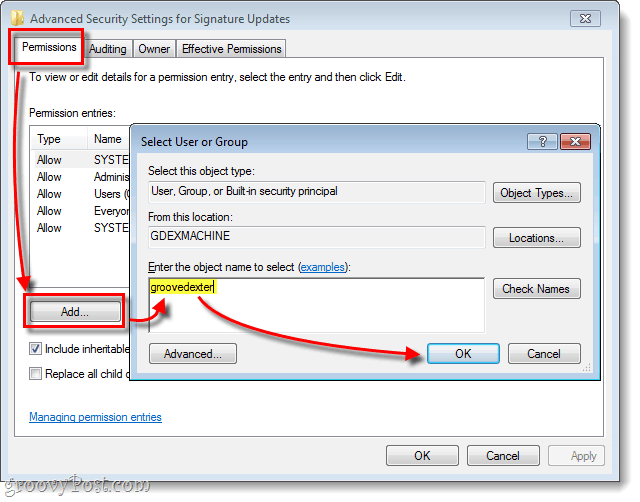
D.
A new Permissions Entry for Root window should open up.
E.
Back on the previous window your username should be on the list with Permissions set to Full Control.
Step-3.
Back on the desktop, right click the LEGACY_WSCSVC.reg file and click Merge and OK any prompts you get.
Let me know if you got the error this time or if you got a message saying the file was merged successfully.
If something is not clear or you don't understand something, stop and let me know.
Step-1
Back Up the WSCSVC_LEGACY registry key.
- Click Start, then click Run. The Run window will open.
- In the Open box type regedit and click OK. The registry editor window will open.
- Click the + beside HKEY_LOCAL_MACHINE
- Click the + beside SYSTEM
- Click the + beside CurrentControlSet
- Click the + beside Enum
- Right click the Root key and click Export on the context menu. The Export Registry File window will open.
- In the left hand column, click Desktop. This will put the Desktop in the Save in: box.
- In the File name: box, type Rootbak
- In the Save as type: box make sure it says Registration files *.reg
- Click the Save button. This will put a backup of the HKEY\System\CurrentControlSet\Enum\Root on the desktop. The file will be named Rootbak.reg
Make sure the file is on the desktop and then close the Registry Editor.
Step-2.
How To Take Ownership of a Registry key
NOTE: The images below show the name grooveDexter. Do Not type that in. Instead type what is in the instructions.
- Click Start, then click Run. The Run window will open.
- In the Open box type regedit and click OK. The registry editor window will open.
- Click the + beside HKEY_LOCAL_MACHINE
- Click the + beside SYSTEM
- Click the + beside CurrentControlSet
- Click the + beside Enum
- Right-Click the Root key and click Permissions. The Permissions window will open.

A.
- Click the Advanced button at the bottom of the page. The Advanced Security Settings for Root window will open.

B.
- On the Advanced Security Settings for Root page, click the Owner tab.
- In the Change owner to: box, click Ron(RUSSO-DESKTOP\Ron (the merciful))
- Click the box beside Replace owner on subcontainers and objects
- Click the Apply button.

C.
- Now, click the Permissions tab at the top of the Advanced Security Settings for Root window.
- Click the Add button. The Select User Group window will open.(See image below)
- Click inside the Enter the object name to select window and type Ron and click the OK button.(See image below)

D.
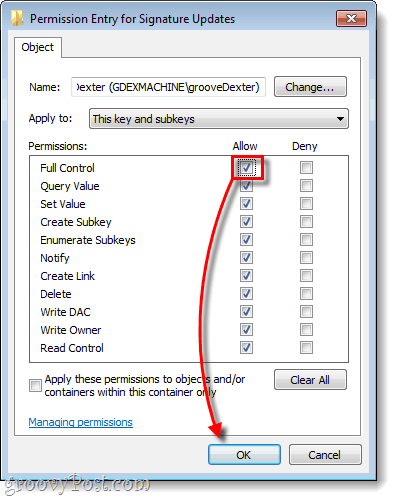
A new Permissions Entry for Root window should open up.
- Beside the Full Control line, check the box under the Allow column and click the OK button.

E.
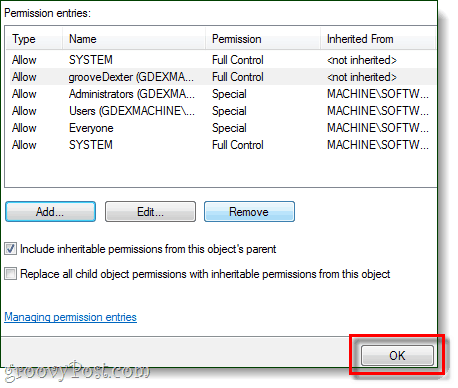
Back on the previous window your username should be on the list with Permissions set to Full Control.

- Click the OK button until you get back to the Registry Editor window, then close the Registry Editor.
- Reboot the computer.
Step-3.
Back on the desktop, right click the LEGACY_WSCSVC.reg file and click Merge and OK any prompts you get.
Let me know if you got the error this time or if you got a message saying the file was merged successfully.
#97
![Google Redirection problem; tutorial didn't work [Closed]: post #97](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 28 January 2013 - 04:54 PM
Posted 28 January 2013 - 04:54 PM

Okay, followed through the steps....
.reg has been successfully entered into the registry.
I think that worked, huh?
.reg has been successfully entered into the registry.
I think that worked, huh?
#98
![Google Redirection problem; tutorial didn't work [Closed]: post #98](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 28 January 2013 - 09:17 PM
Posted 28 January 2013 - 09:17 PM

Yep, looks like that did it. We need to run FSS again to make sure that the Security Center service is working and no registry keys are missing.
Run Farbar Service Scanner
Please download Farbar Service Scanner to the desktop.
Doubleclick the FSS.exe file to run it. (Vista and 7 users may need to right click the file and click Run as Administrator)
Please post the FSS.txt log
Run Farbar Service Scanner
Please download Farbar Service Scanner to the desktop.
Doubleclick the FSS.exe file to run it. (Vista and 7 users may need to right click the file and click Run as Administrator)

- Make sure the following options are checked:
- Internet Services
- Windows Firewall
- System Restore
- Security Center
- Windows Update
- Windows Defender
- Other Services
- Press "Scan".
- It will create a log (FSS.txt) in the same directory the tool is run.
- Please copy and paste the log to your reply.
Please post the FSS.txt log
#99
![Google Redirection problem; tutorial didn't work [Closed]: post #99](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 January 2013 - 01:00 PM
Posted 30 January 2013 - 01:00 PM

Farbar Service Scanner Version: 10-12-2012
Ran by Ron (the merciful) (administrator) on 30-01-2013 at 13:57:38
Running from "C:\Documents and Settings\Ron (the merciful)\My Documents\Downloads"
Microsoft Windows XP Service Pack 3 (X86)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Security Center:
============
wscsvc Service is not running. Checking service configuration:
The start type of wscsvc service is OK.
The ImagePath of wscsvc service is OK.
The ServiceDll of wscsvc service is OK.
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
File Check:
========
C:\WINDOWS\system32\dhcpcsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\afd.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\netbt.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\tcpip.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\ipsec.sys => MD5 is legit
C:\WINDOWS\system32\dnsrslvr.dll => MD5 is legit
C:\WINDOWS\system32\ipnathlp.dll => MD5 is legit
C:\WINDOWS\system32\netman.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\srsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\sr.sys => MD5 is legit
C:\WINDOWS\system32\wscsvc.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\wuauserv.dll => MD5 is legit
C:\WINDOWS\system32\qmgr.dll => MD5 is legit
C:\WINDOWS\system32\es.dll => MD5 is legit
C:\WINDOWS\system32\cryptsvc.dll => MD5 is legit
C:\WINDOWS\system32\svchost.exe => MD5 is legit
C:\WINDOWS\system32\rpcss.dll => MD5 is legit
C:\WINDOWS\system32\services.exe => MD5 is legit
Extra List:
=======
AegisP(9) DNE(8) Gpc(6) IPSec(4) NetBT(5) PSched(7) Tcpip(3)
0x09000000040000000100000002000000030000000500000006000000070000000800000009000000
IpSec Tag value is correct.
**** End of log ****
Ran by Ron (the merciful) (administrator) on 30-01-2013 at 13:57:38
Running from "C:\Documents and Settings\Ron (the merciful)\My Documents\Downloads"
Microsoft Windows XP Service Pack 3 (X86)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Security Center:
============
wscsvc Service is not running. Checking service configuration:
The start type of wscsvc service is OK.
The ImagePath of wscsvc service is OK.
The ServiceDll of wscsvc service is OK.
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
File Check:
========
C:\WINDOWS\system32\dhcpcsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\afd.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\netbt.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\tcpip.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\ipsec.sys => MD5 is legit
C:\WINDOWS\system32\dnsrslvr.dll => MD5 is legit
C:\WINDOWS\system32\ipnathlp.dll => MD5 is legit
C:\WINDOWS\system32\netman.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\srsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\sr.sys => MD5 is legit
C:\WINDOWS\system32\wscsvc.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\wuauserv.dll => MD5 is legit
C:\WINDOWS\system32\qmgr.dll => MD5 is legit
C:\WINDOWS\system32\es.dll => MD5 is legit
C:\WINDOWS\system32\cryptsvc.dll => MD5 is legit
C:\WINDOWS\system32\svchost.exe => MD5 is legit
C:\WINDOWS\system32\rpcss.dll => MD5 is legit
C:\WINDOWS\system32\services.exe => MD5 is legit
Extra List:
=======
AegisP(9) DNE(8) Gpc(6) IPSec(4) NetBT(5) PSched(7) Tcpip(3)
0x09000000040000000100000002000000030000000500000006000000070000000800000009000000
IpSec Tag value is correct.
**** End of log ****
#100
![Google Redirection problem; tutorial didn't work [Closed]: post #100](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 January 2013 - 01:57 PM
Posted 30 January 2013 - 01:57 PM

OK, let's see if we can get the service started.
Step-1.
 OTL Fix
OTL Fix
Be advised that when the fix commences it will shut down all running processes and you may lose the desktop and icons, they will return on reboot
1. Please copy all of the text in the quote box below (Do Not copy the word Quote. To do this, highlight everything
inside the quote box (except the word Quote) , right click and click Copy.
Warning: This fix is relevant for this system and no other. If you are not this user, do NOT follow these directions as they could damage the workings of your system.
2. Please re-open on your desktop. To do that:
on your desktop. To do that: textbox, right click and click Paste. This will put the above script inside the textbox.
textbox, right click and click Paste. This will put the above script inside the textbox.
4. Click the button.
button.
5. Let the program run unhindered.
6. OTL may ask to reboot the machine. Please do so if asked.
7. Click the button.
button.
8. A report will open. Copy and Paste that report in your next reply.
9. If the machine reboots, the log will be located at C:\_OTL\MovedFiles\mmddyyyy_hhmmss.log, (where mmddyyyy_hhmmss is the date of the tool run).
Step-2.
Re-run FSS.exe
Step-3.
Things For Your Next Post:
Please post the logs in the order requested. Do Not attach the logs unless I request it.
1. The OTL fixes log
2. The new FSS.txt log
Step-1.
Be advised that when the fix commences it will shut down all running processes and you may lose the desktop and icons, they will return on reboot
1. Please copy all of the text in the quote box below (Do Not copy the word Quote. To do this, highlight everything
inside the quote box (except the word Quote) , right click and click Copy.
:COMMANDS
[createrestorepoint]
:FILES
net stop wscsvc /c
net start wscsvc /c
:COMMANDS
[emptytemp]
Warning: This fix is relevant for this system and no other. If you are not this user, do NOT follow these directions as they could damage the workings of your system.
2. Please re-open
- XP users: Double click the icon.
 textbox, right click and click Paste. This will put the above script inside the textbox.
textbox, right click and click Paste. This will put the above script inside the textbox.4. Click the
 button.
button.5. Let the program run unhindered.
6. OTL may ask to reboot the machine. Please do so if asked.
7. Click the
 button.
button.8. A report will open. Copy and Paste that report in your next reply.
9. If the machine reboots, the log will be located at C:\_OTL\MovedFiles\mmddyyyy_hhmmss.log, (where mmddyyyy_hhmmss is the date of the tool run).
Step-2.
Re-run FSS.exe
Step-3.
Things For Your Next Post:
Please post the logs in the order requested. Do Not attach the logs unless I request it.
1. The OTL fixes log
2. The new FSS.txt log
#101
![Google Redirection problem; tutorial didn't work [Closed]: post #101](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 January 2013 - 03:12 PM
Posted 30 January 2013 - 03:12 PM

All processes killed
========== COMMANDS ==========
Restore point Set: OTL Restore Point
========== FILES ==========
< net stop wscsvc /c >
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.txt deleted successfully.
< net start wscsvc /c >
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: Administrator
->Temp folder emptied: 64727 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 0 bytes
->Google Chrome cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: All Users
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: LocalService
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Flash cache emptied: 0 bytes
User: NetworkService
->Temp folder emptied: 103438 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Ron (the merciful)
->Temp folder emptied: 523862529 bytes
->Temporary Internet Files folder emptied: 33839312 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 6768153 bytes
->Google Chrome cache emptied: 345955774 bytes
->Flash cache emptied: 1397 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32\dllcache .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 697650 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 4142 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temporary Internet Files folder emptied: 0 bytes
RecycleBin emptied: 128822451 bytes
Total Files Cleaned = 992.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 01302013_155800
Files\Folders moved on Reboot...
File\Folder C:\WINDOWS\temp\TMP00000001AB9698F38BAAD6B9 not found!
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
========== COMMANDS ==========
Restore point Set: OTL Restore Point
========== FILES ==========
< net stop wscsvc /c >
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.txt deleted successfully.
< net start wscsvc /c >
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\Ron (the merciful)\Desktop\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: Administrator
->Temp folder emptied: 64727 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 0 bytes
->Google Chrome cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: All Users
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: LocalService
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Flash cache emptied: 0 bytes
User: NetworkService
->Temp folder emptied: 103438 bytes
->Temporary Internet Files folder emptied: 33170 bytes
->Java cache emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Ron (the merciful)
->Temp folder emptied: 523862529 bytes
->Temporary Internet Files folder emptied: 33839312 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 6768153 bytes
->Google Chrome cache emptied: 345955774 bytes
->Flash cache emptied: 1397 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32\dllcache .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 697650 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 4142 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temporary Internet Files folder emptied: 0 bytes
RecycleBin emptied: 128822451 bytes
Total Files Cleaned = 992.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 01302013_155800
Files\Folders moved on Reboot...
File\Folder C:\WINDOWS\temp\TMP00000001AB9698F38BAAD6B9 not found!
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
#102
![Google Redirection problem; tutorial didn't work [Closed]: post #102](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 January 2013 - 03:31 PM
Posted 30 January 2013 - 03:31 PM

Farbar Service Scanner Version: 10-12-2012
Ran by Ron (the merciful) (administrator) on 30-01-2013 at 16:19:26
Running from "C:\Documents and Settings\Ron (the merciful)\My Documents\Downloads"
Microsoft Windows XP Service Pack 3 (X86)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Security Center:
============
wscsvc Service is not running. Checking service configuration:
The start type of wscsvc service is OK.
The ImagePath of wscsvc service is OK.
The ServiceDll of wscsvc service is OK.
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
File Check:
========
C:\WINDOWS\system32\dhcpcsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\afd.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\netbt.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\tcpip.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\ipsec.sys => MD5 is legit
C:\WINDOWS\system32\dnsrslvr.dll => MD5 is legit
C:\WINDOWS\system32\ipnathlp.dll => MD5 is legit
C:\WINDOWS\system32\netman.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\srsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\sr.sys => MD5 is legit
C:\WINDOWS\system32\wscsvc.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\wuauserv.dll => MD5 is legit
C:\WINDOWS\system32\qmgr.dll => MD5 is legit
C:\WINDOWS\system32\es.dll => MD5 is legit
C:\WINDOWS\system32\cryptsvc.dll => MD5 is legit
C:\WINDOWS\system32\svchost.exe => MD5 is legit
C:\WINDOWS\system32\rpcss.dll => MD5 is legit
C:\WINDOWS\system32\services.exe => MD5 is legit
Extra List:
=======
AegisP(9) DNE(8) Gpc(6) IPSec(4) NetBT(5) PSched(7) Tcpip(3)
0x09000000040000000100000002000000030000000500000006000000070000000800000009000000
IpSec Tag value is correct.
**** End of log ****
Ran by Ron (the merciful) (administrator) on 30-01-2013 at 16:19:26
Running from "C:\Documents and Settings\Ron (the merciful)\My Documents\Downloads"
Microsoft Windows XP Service Pack 3 (X86)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Security Center:
============
wscsvc Service is not running. Checking service configuration:
The start type of wscsvc service is OK.
The ImagePath of wscsvc service is OK.
The ServiceDll of wscsvc service is OK.
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
File Check:
========
C:\WINDOWS\system32\dhcpcsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\afd.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\netbt.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\tcpip.sys => MD5 is legit
C:\WINDOWS\system32\Drivers\ipsec.sys => MD5 is legit
C:\WINDOWS\system32\dnsrslvr.dll => MD5 is legit
C:\WINDOWS\system32\ipnathlp.dll => MD5 is legit
C:\WINDOWS\system32\netman.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\srsvc.dll => MD5 is legit
C:\WINDOWS\system32\Drivers\sr.sys => MD5 is legit
C:\WINDOWS\system32\wscsvc.dll => MD5 is legit
C:\WINDOWS\system32\wbem\WMIsvc.dll => MD5 is legit
C:\WINDOWS\system32\wuauserv.dll => MD5 is legit
C:\WINDOWS\system32\qmgr.dll => MD5 is legit
C:\WINDOWS\system32\es.dll => MD5 is legit
C:\WINDOWS\system32\cryptsvc.dll => MD5 is legit
C:\WINDOWS\system32\svchost.exe => MD5 is legit
C:\WINDOWS\system32\rpcss.dll => MD5 is legit
C:\WINDOWS\system32\services.exe => MD5 is legit
Extra List:
=======
AegisP(9) DNE(8) Gpc(6) IPSec(4) NetBT(5) PSched(7) Tcpip(3)
0x09000000040000000100000002000000030000000500000006000000070000000800000009000000
IpSec Tag value is correct.
**** End of log ****
#103
![Google Redirection problem; tutorial didn't work [Closed]: post #103](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 January 2013 - 10:32 PM
Posted 30 January 2013 - 10:32 PM

Well that was disapointing. I thought that would start it. Let's look at data in the service key and the dependancies
Create and Run a Batch File
Please copy everything in the code box below into notepad. To do this highlight all text, then right click and click Copy.
Create and Run a Batch File
Please copy everything in the code box below into notepad. To do this highlight all text, then right click and click Copy.
@Echo Off reg query "HKLM\system\currentcontrolset\services\wscsvc" >> C:\look.txt sc query RpcSs >> C:\look.txt sc query winmgmt >> C:\look.txt exit
- Next, open Notepad, or click Start->Run and in the Open: box type notepad.exe and click OK.
- Right click in the notepad window and click Paste, or put the cursor inside the notepad window and press the Ctrl-V keys to paste the text into notepad.
- On the File menu, click Save
- On the Save AS window that comes up, do the following:
- On the left side, click the Desktop Icon. This will put "Desktop" in the Save In: box at the top.
- At the bottom in the File Name: box type look.bat
- In the Save as type: box, click the down arrow and click All Files(*.*)
- Click Save
Close all open windows and any open Browsers. - Double click the look.bat file on the desktop to run the file. A command window will open briefly, then close. This is quite normal. A file named look.txt will be placed in the Root directory (C:\look.txt)
- Click Start, then click Run. The Run box will open.
- In the Open box type notepad C:\look.txt and click OK. The file will open on the desktop.
#104
![Google Redirection problem; tutorial didn't work [Closed]: post #104](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 04 February 2013 - 10:31 AM
Posted 04 February 2013 - 10:31 AM

Due to lack of feedback, this topic has been closed.
If you need this topic reopened, please contact a staff member. This applies only to the original topic starter. Everyone else please begin a New Topic.
If you need this topic reopened, please contact a staff member. This applies only to the original topic starter. Everyone else please begin a New Topic.
#105
![Google Redirection problem; tutorial didn't work [Closed]: post #105](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 13 February 2013 - 10:22 PM
Posted 13 February 2013 - 10:22 PM

User returned.
Hi Ron,
Did you complete the steps in post #60?
Please complete the steps in post #103 and post the OTL.txt log
Hi Ron,
Did you complete the steps in post #60?
Please complete the steps in post #103 and post the OTL.txt log
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

