We have detected that your PC is using a version of Microsoft Internet Explorer or Firefox, or another browser, that is not compatible with ActiveScan 2.0.
which is odd as I have latest firefox so had to download it, did find 9 suspicious files in the registry, do I clean them?
Malwarebytes Anti-Malware (PRO) 1.70.0.1100
www.malwarebytes.org
Database version: v2013.01.28.09
Windows Vista Service Pack 2 x86 NTFS
Internet Explorer 9.0.8112.16421
Chris :: DELL-530 [administrator]
Protection: Enabled
28/01/2013 18:50:17
mbam-log-2013-01-28 (18-50-17).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 200431
Time elapsed: 4 minute(s), 18 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\INTEROP.PRPLAYERCOR#\3AACB3AD0998BEA4CF56323794EB2C8F\INTEROP.PRPLAYERCORELIB.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\PHOTOMANAGER\BBD3DF31BDF82F00F0959B329F01AAF4\PHOTOMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\ALLSHARECONTROLLER\5B125EA25878945BE73A0B105206DF41\ALLSHARECONTROLLER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.MAINUI\04CBEE3072EC83A44739232219ED52D5\KIES.COMMON.MAINUI.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\DEVICEVIDEO\727C54F055DB0237275FE73A8BDC7E17\DEVICEVIDEO.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\EBOOKMANAGER\A733A21DF78E533A0BE98297F664753E\EBOOKMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.STOREMA#\70BB30BBC100D4FF16C7F87DBC2B31AA\KIES.COMMON.STOREMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.MVVM\BC2FFEEA3580F165F2314C754E24744C\KIES.MVVM.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\INTEROP.DEVFILESERV#\A675AFEC192581F0F32D6581C68E5E8F\INTEROP.DEVFILESERVICELIB.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES\E7E35EE7F52981CE1AB48C00EE262D37\KIES.NI.EXE to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.MULTIME#\B8FD6D21796B61A55C24AABE580C36D5\KIES.COMMON.MULTIMEDIA.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\E793084599A7BD89923C348E22057983\KIES.COMMON.DEVICESERVICELIB.INTERFACE.NI.DLL to be deleted.
Broken Link. FILE: File not found:C:\USERS\CHRIS\DESKTOP\COMBOFIX.EXE to be deleted.
Broken Link. REGKEY: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\combofix.exe. Key to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\VIDEOMANAGER\122AD0CEDF2147A2D9799AE69885F993\VIDEOMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\6BCF31801A136F6102D51C83FFE72448\KIES.COMMON.DEVICESERVICELIB.FIRMWAREUPDATE.COMMON.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\PODCASTSERVICE\CC5CCF7E2DE6141500219C08610BCF28\PODCASTSERVICE.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\PHONEBOOK\B593ABAB1718C26186E305B33383C7F9\PHONEBOOK.NI.DLL to be deleted.
Broken Link. FILE: File not found:FFDSHOW.AX to be deleted.
Unknown. FILE: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\ffdshow\Audio decoder configuration.lnk to be deleted.
Unknown. FILE: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\ffdshow\Video decoder configuration.lnk to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\DEVICEMUSIC\9AE37560B829ACDF9DCA42531006E9AA\DEVICEMUSIC.NI.DLL to be deleted.
Broken Link. FILE: File not found:"C:\PROGRAM FILES\REAL\REALPLAYER\UPDATE\REALSCHED.EXE" to be deleted.
Broken Link. REGKEY: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run[TkBellExe]. Value: TkBellExe To be deleted.
Broken Link. FILE: File not found:C:\PROGRAM FILES\NORTON 360\ENGINE\6.0.0.145\SYMERR.EXE to be deleted.
Broken Link. REGKEY: HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{08FF730A-494F-4cba-AA0B-E4F1D44715F9}. Key to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\INTEROP.DEVICESEARC#\85FF769496D6B3A3FB81025D06CD8F7C\INTEROP.DEVICESEARCHLIB.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\DEVICEPHOTO\AF8DBDFAD9FDFF93DF66D5ED493E331D\DEVICEPHOTO.NI.DLL to be deleted.
Unknown. FILE: C:\PROGRAM FILES\EVERNOTE\SKITCH\UNINSTALL.EXE to be deleted.
Unknown. FILE: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Skitch\Uninstall Skitch.lnk to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\012CFBFE13E795A6FA2365918B878386\KIES.COMMON.DEVICESERVICELIB.DEVICEDATASERVICE.NI.DLL to be deleted.
Unknown. FILE: C:\USERS\CHRIS\DOWNLOADS\WVCHECK.EXE to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.ALLSHARE\F5C5F12D694DE2A89C2D40BCD4578CA0\KIES.COMMON.ALLSHARE.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DBMANAG#\683A2ADB742AD60E4BEBA025BF957CF2\KIES.COMMON.DBMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\BF10BEB0FF3048E6048DBEA8E92C0C11\KIES.COMMON.DEVICESERVICELIB.FIRMWAREUPDATE.DOWNLOADER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\F853D4336528646EA1177D8033C6EF30\KIES.COMMON.DEVICESERVICELIB.DEVICEMANAGEMENT.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\CPKTMUSICPLUGIN\63C041A904F052EE3140744695EB0628\CPKTMUSICPLUGIN.NI.DLL to be deleted.
Broken Link. FILE: File not found:C:\PROGRAM FILES\OPERA\OPERA.EXE to be deleted.
Broken Link. REGKEY: HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mht\OpenWithProgids[Opera.HTML]. Value: Opera.HTML To be deleted.
Broken Link. REGKEY: HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mhtml\OpenWithProgids[Opera.HTML]. Value: Opera.HTML To be deleted.
Broken Link. FILE: File not found:"C:\PROGRAM FILES\INTERNET EXPLORER\IEXPLORE.EXE" to be deleted.
Unknown. FILE: C:\Users\Chris\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Internet Explorer (No Add-ons).lnk to be deleted.
Broken Link. FILE: File not found:DFSVC.EXE to be deleted.
Broken Link. REGKEY: HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{C8999AED-AECE-4E27-9BCB-5358B13F9FF9}. Key to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\DEVICEPODCAST\5515B99EF1F56FD99DD92B2411898D1B\DEVICEPODCAST.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\BATPLUGIN\9BABC9BC724237A609F4DE0AD3323C9F\BATPLUGIN.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\DEVICEHOST\0080908A889CB90FC874959C87FE0374\DEVICEHOST.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\294C94F981D637F17AB1735A88C71F84\KIES.COMMON.DEVICESERVICELIB.FIRMWAREUPDATE.FIRMWAREUPDATEAGENTHELPER.NI.DLL to be deleted.
Unknown. FILE: C:\PROGRAM FILES\AVAST SOFTWARE\AVAST\DEFS\13012800\ALGO.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\FFAFE10B3805924B1088BC69A5DE2F0B\KIES.COMMON.DEVICESERVICE.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.UTIL\EB93B73C1D4B45FEC994A8D751846FE5\KIES.COMMON.UTIL.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\PODCASTER\4A6FF3A0091024818451AF7DE4764388\PODCASTER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.MEDIADB\7AED44092B17A6A553F177B60CB9577E\KIES.COMMON.MEDIADB.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.UI\752AB77541C7F9ACBDAB1BD3F79FC6BA\KIES.UI.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.INTERFACE\94115754846BA74909B9C7247EA049C8\KIES.INTERFACE.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.THEME\8A4F27E3F254DED6F14720398A17AA16\KIES.THEME.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.LOCALE\8B05816D8B09B1B2B7E1DDB16A4AF9E6\KIES.LOCALE.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MUSICMANAGER\E6587BC657F47680E956AD43831C6C8D\MUSICMANAGER.NI.DLL to be deleted.
Unknown. FILE: C:\WINDOWS\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\KIES.COMMON.DEVICES#\FCA01DDD89F601AA8F3457E0F6DC0878\KIES.COMMON.DEVICESERVICELIB.FILESERVICE.NI.DLL to be deleted.
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[SHOWSUPERHIDDEN] to be changed to: 1
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[SUPERHIDDEN] to be changed to: 0
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[HIDEFILEEXT] to be changed to: 0
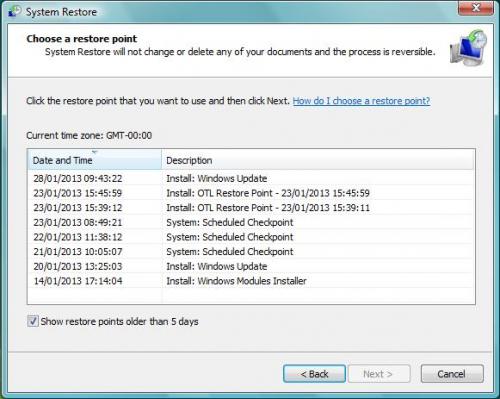
Edited by BristolCity, 28 January 2013 - 01:27 PM.

 This topic is locked
This topic is locked













 Sign In
Sign In Create Account
Create Account

