Wow, you are really fast.
 Warning!
Warning! Your computer is infected with Backdoor.
What is Backdoor?Backdoor is malware, which allows another person to remotely control your computer, so this infection can execute files, download files from the internet or steal your data.
How can you deal with this infection?We can clean this infection. However, we aren't sure, that you can trust your computer even after removal of this infection. So, there is only one way to completely remove this infection - format your hard drive and reinstall Windows.
Please, read info
here to learn more, why you need to reinstall Windows.
So, If you decided to format hard drive and reinstall Windows, please, let me know about it. If you didn't, please, follow these steps:Step 1. FRST Fix.
- Open notepad (Start =>All Programs => Accessories => Notepad). Please copy the entire contents of the code box below. (To do this highlight the contents of the box, right click on it and select copy.
- Right-click in the open notepad and select Paste.
- Save it on the flashdrive as fixlist.txt
start
HKLM\...D6A79037F57F\InprocServer32: [Default-fastprox] ATTENTION! ====> ZeroAccess?
HKLM-x32\...\Run: [AS2014] - C:\ProgramData\gV3ni763\gV3ni763.exe [577536 2013-08-29] ()
HKU\Tim\...\Run: [AS2014] - C:\ProgramData\gV3ni763\gV3ni763.exe [577536 2013-08-29] ()
C:\ProgramData\gV3ni763\gV3ni763.exe
HKU\Tim\...\Winlogon: [Shell] C:\Users\Tim\AppData\Roaming\dlc.xmm,explorer.exe <==== ATTENTION
C:\Users\Tim\AppData\Roaming\dlc.xmm
S2 *etadpug; "C:\Program Files (x86)\Google\Desktop\Install\{195bea59-cf36-485d-9c6f-8a46beed1d6c}\ \...\???\{195bea59-cf36-485d-9c6f-8a46beed1d6c}\GoogleUpdate.exe" < <==== ATTENTION (ZeroAccess)
C:\Program Files (x86)\Google\Desktop\Install\{195bea59-cf36-485d-9c6f-8a46beed1d6c}\ \...\???\{195bea59-cf36-485d-9c6f-8a46beed1d6c}\GoogleUpdate.exe
2013-08-29 07:37 - 2013-08-29 09:44 - 00000000 ____D C:\ProgramData\gV3ni763
2013-08-28 19:49 - 2013-08-28 19:49 - 00201216 _____ C:\ProgramData\cfwjpg.exe
2013-08-28 19:49 - 2013-08-28 19:49 - 00000000 ____D C:\ProgramData\ulske
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\yijcb.exe
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\rvhk.exe
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\rfspsw.exe
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\pssvp.exe
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\otgmut.exe
2013-08-28 19:48 - 2013-08-28 19:48 - 00201216 _____ C:\ProgramData\njjv.exe
2013-08-28 19:47 - 2013-08-28 19:47 - 00201216 _____ C:\ProgramData\dkrcve.exe
2013-08-29 10:23 - 2013-08-29 10:28 - 00001668 _____ C:\Users\Tim\Desktop\Antivirus Security Pro.lnk
2013-08-29 10:23 - 2013-08-29 10:28 - 00000118 _____ C:\Users\Tim\Desktop\Antivirus Security Pro support.url
C:\Program Files (x86)\Google\Desktop\Install\{195bea59-cf36-485d-9c6f-8a46beed1d6c}
C:\Users\Tim\AppData\Roaming\cache.dat
C:\Users\Tim\AppData\Roaming\cache.ini
C:\$Recycle.Bin\S-1-5-18\$195bea59cf36485d9c6f8a46beed1d6c
C:\$Recycle.Bin\S-1-5-21-606431231-295175572-1105962100-1000\$195bea59cf36485d9c6f8a46beed1d6c
C:\Windows\svchost.exe
DeleteJunctionsIndirectory: C:\Program Files\Windows Defender
TDL4: custom:26000022
endNOTICE:
This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating systemNow please enter System Recovery Options.
Run
FRST and press the
Fix button just once and wait. The tool will make a log on the flashdrive (
Fixlog.txt) please post it in your next reply.
Step 2. OTL scan.
Boot in normal mode now and download
OTL to your Desktop
Step 3. RogueKiller scan.
Download
RogueKiller to your desktop
Note: This is a French tool so don't be surprised when you find the page displays with some French.
- Quit all running programs
- For Vista/Seven, right click -> run as administrator, for XP simply run RogueKiller.exe
- Wait until Prescan has finished...
- Click on Scan
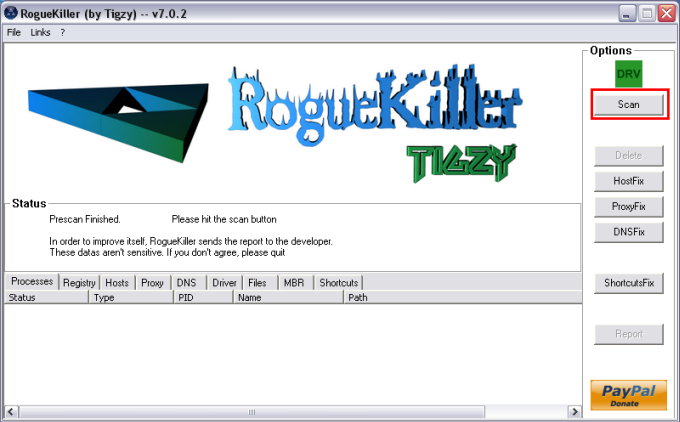
- Wait for the scan to finish.
- The report is created on your desktop.
- If the program is blocked, do not hesitate to try several times. If it really does not work (it could happen), rename it to winlogon.exe
Please post the contents of all the
RKreport.txt files from your desktop in your next Reply.
So, please, don't forget to post in your next message:
- Fixlog.txt
- OTL.txt
- Extras.txt
- RKreport.txt















 Sign In
Sign In Create Account
Create Account

