If you want to format it I guess it won't hurt just make sure that it doesn't pick up an MBR in the process.
Windows 10 hard drive failing (I think)

Best Answer RKinner , 01 September 2016 - 06:41 AM
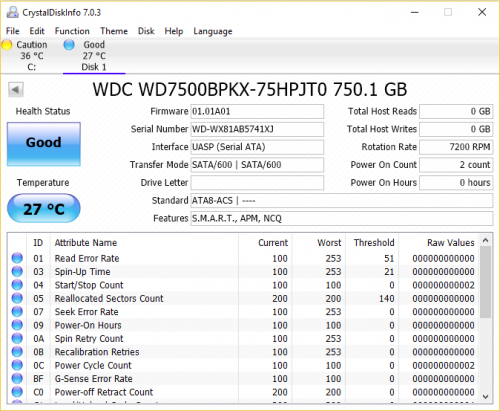
Your current drive is:Samsung SpinPoint ST750LM022 750GB SATA/300 5400RPM 8MB 2.5" Hard Drive' Get a replacement drive of the same size or bigger. Don't get another Seagate. ... Go to the full post »
#46

 Posted 09 October 2016 - 04:32 PM
Posted 09 October 2016 - 04:32 PM

#47

 Posted 09 October 2016 - 04:54 PM
Posted 09 October 2016 - 04:54 PM

#48

 Posted 09 October 2016 - 05:19 PM
Posted 09 October 2016 - 05:19 PM

Looks good and you do have the correct AOMEI.
If I remember correctly with AOMEI you may need to check on it periodically while it clones. I think it will stop if it finds a bad sector then you need to tell it to Skip.
#49

 Posted 09 October 2016 - 05:26 PM
Posted 09 October 2016 - 05:26 PM

OK will update. And under settings, "copy without resizing partitions" is selected. Is that right?
#50

 Posted 09 October 2016 - 05:32 PM
Posted 09 October 2016 - 05:32 PM

Yes. Since both drives are the same size there is no need to change the partitions.
#51

 Posted 09 October 2016 - 09:50 PM
Posted 09 October 2016 - 09:50 PM

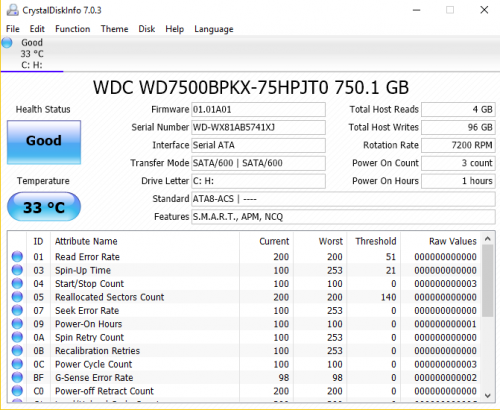
It worked! I want to thank you for all the help RKinner. Really appreciate it.
#52

 Posted 09 October 2016 - 09:55 PM
Posted 09 October 2016 - 09:55 PM

#53

 Posted 09 October 2016 - 11:02 PM
Posted 09 October 2016 - 11:02 PM

Great. Run a disk check and a defrag to make sure everything is OK.
#54

 Posted 10 October 2016 - 12:04 AM
Posted 10 October 2016 - 12:04 AM

#55

 Posted 10 October 2016 - 08:02 AM
Posted 10 October 2016 - 08:02 AM

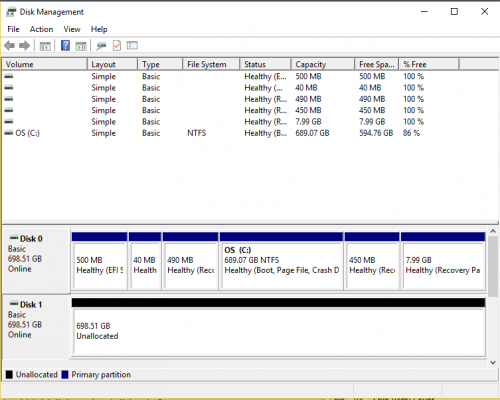
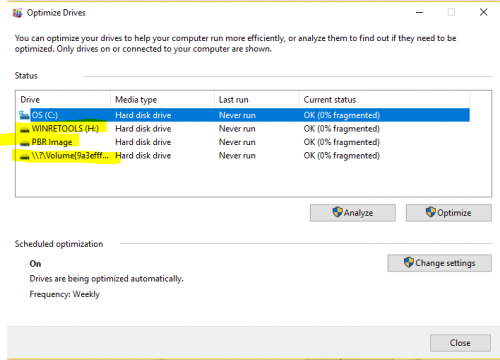
PBR Image drive and WINRETOOLS drive are the recovery partitions and contain the recovery image (PBR Image) and Windows Recovery Environment tools (WINRETOOLS) used by Dell. Apparently they became visible with Win 10. I expect they would take your system back to how it was when it came from the factory.
Not enough info to tell you what the last one was.
Copy the foloowing:
reg query HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices /s > \junk.txt notepad \junk.txt
#56

 Posted 11 October 2016 - 12:55 AM
Posted 11 October 2016 - 12:55 AM

PBR Image drive and WINRETOOLS drive are the recovery partitions and contain the recovery image (PBR Image) and Windows Recovery Environment tools (WINRETOOLS) used by Dell. Apparently they became visible with Win 10. I expect they would take your system back to how it was when it came from the factory.
Not enough info to tell you what the last one was.
Copy the foloowing:
reg query HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices /s > \junk.txt notepad \junk.txtOpen an elevated command prompt:If you open an elevated command prompt it will by default open in c:\Windows\system32Once you have an elevated command prompt:Right click and Paste (or Edit then Paste) and the copied text should appear. Hit Enter if notepad does not open. Copy and paste the text from notepad to a reply.
#57

 Posted 11 October 2016 - 07:46 PM
Posted 11 October 2016 - 07:46 PM

No sign of it in the registry. I wonder if it's a leftover from a zero access infection? There used to be one that installed its own partition then modified the mbr to boot from it.
See if TDSSKiller will run on your OS.
http://support.kaspe...lity#TDSSKiller
I'd download the exe version.
#58

 Posted 11 October 2016 - 10:06 PM
Posted 11 October 2016 - 10:06 PM

Working on my reply but this dialog box is annoying me, I digress: do you what the deal is with this? it wont go away. And I never seen it before http://imgur.com/m0RTO9m
#59

 Posted 11 October 2016 - 10:08 PM
Posted 11 October 2016 - 10:08 PM

OK so download the program and run a scan. Then reboot. Then run it again. ? I understand the rest of instructions but just asking how many scans you meant for me to run.
Disregard previous post, got the dialog removed in windows processes.
Edited by Established301, 12 October 2016 - 01:37 AM.
#60

 Posted 12 October 2016 - 07:15 AM
Posted 12 October 2016 - 07:15 AM

Total of two scans for now. They shouldn't take too long.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:













 Sign In
Sign In Create Account
Create Account

