Download and install Agent Ransack: http://www.mythicsof...x?page=download
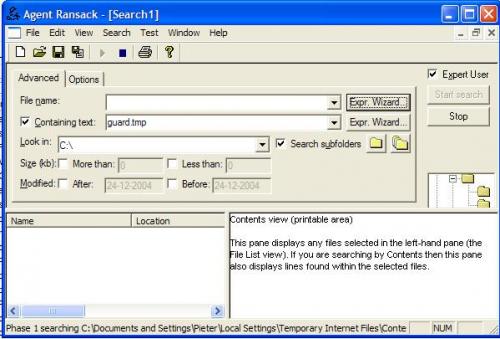
Then use the settings as in the example I wil attach.
It will take quite a while before it's done.
When it is click "Save results" (icon #4 from the left)
Choose save to clipboard and paste them into your next post.
Hopefully this will tell us which file(s) is reporting that ugly missing.
Regards,
Pieter
















 Sign In
Sign In Create Account
Create Account

