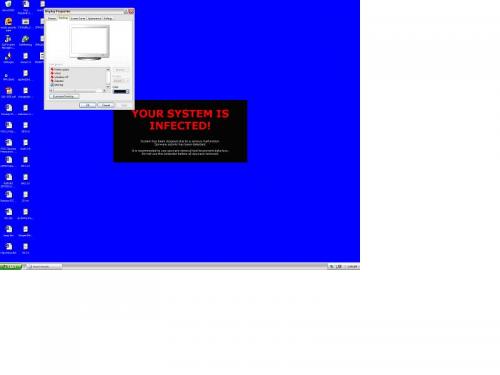
My desktop got locked could not change the settings. Please find the image how it looks.
Please suggest me what needs to be done to remove this.
I also scanned the system using TrojanHunter 4.2,ewidoguard.exe and Lavasoft
still no improvement. Please help me.
Here is the Hijackthis log file.
Logfile of HijackThis v1.99.1
Scan saved at 2:11:24 AM, on 9/28/2004
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180)
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\SYSTEM32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\LEXBCES.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\atiptaxx.exe
C:\Program Files\TrojanHunter 4.2\THGuard.exe
C:\Program Files\HAWKING\Hawking Technologies HWC54G Wireless-G CardBus Card\Installer\WINXP\ConfigUtility.exe
C:\WINDOWS\System32\Ati2evxx.exe
C:\Program Files\Yahoo!\Messenger\ymsgr_tray.exe
C:\WINDOWS\Cpqdiag\Cpqdfwag.exe
C:\Program Files\ewido\security suite\ewidoctrl.exe
c:\orant\bin\oracle80.exe
C:\orant\BIN\TNSLSNR80.EXE
C:\WINDOWS\system32\mspaint.exe
C:\WINDOWS\System32\svchost.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\hijackthis\HijackThis.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page =
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = about:blank
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page =
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Local Page =
R0 - HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName =
R3 - Default URLSearchHook is missing
O2 - BHO: UberButton Class - {5BAB4B5B-68BC-4B02-94D6-2FC0DE4A7897} - C:\Program Files\Yahoo!\Common\yiesrvc.dll
O2 - BHO: YahooTaggedBM Class - {65D886A2-7CA7-479B-BB95-14D1EFB7946A} - C:\Program Files\Yahoo!\Common\YIeTagBm.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn\yt.dll
O4 - HKLM\..\Run: [ATIModeChange] Ati2mdxx.exe
O4 - HKLM\..\Run: [AtiPTA] atiptaxx.exe
O4 - HKLM\..\Run: [javakh32.exe] C:\WINDOWS\javakh32.exe
O4 - HKLM\..\Run: [1E.tmp.exe] C:\DOCUME~1\TEKADM~1.SAP\LOCALS~1\Temp\1E.tmp.exe
O4 - HKLM\..\Run: [THGuard] "C:\Program Files\TrojanHunter 4.2\THGuard.exe"
O4 - HKLM\..\RunServices: [CPQDFWAG] C:\WINDOWS\Cpqdiag\CpqDfwAg.exe
O4 - HKCU\..\Run: [Yahoo! Pager] C:\Program Files\Yahoo!\Messenger\ypager.exe -quiet
O4 - HKCU\..\Run: [wupd] C:\WINDOWS\System32\win32.exe
O4 - HKCU\..\Run: [Tmntsrv32] C:\WINDOWS\System32\Tmntsrv32.EXE
O4 - HKCU\..\Run: [Windows installer] C:\winstall.exe
O4 - HKCU\..\Run: [SNInstall] C:\winstall.exe
O4 - Global Startup: ConfigUtility.lnk = C:\Program Files\HAWKING\Hawking Technologies HWC54G Wireless-G CardBus Card\Installer\WINXP\ConfigUtility.exe
O4 - Global Startup: Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office\OSA9.EXE
O8 - Extra context menu item: &Google Search - res://c:\program files\google\GoogleToolbar2.dll/cmsearch.html
O8 - Extra context menu item: &Yahoo! Search - file:///C:\Program Files\Yahoo!\Common/ycsrch.htm
O8 - Extra context menu item: Backward Links - res://c:\program files\google\GoogleToolbar2.dll/cmbacklinks.html
O8 - Extra context menu item: Cached Snapshot of Page - res://c:\program files\google\GoogleToolbar2.dll/cmcache.html
O8 - Extra context menu item: Similar Pages - res://c:\program files\google\GoogleToolbar2.dll/cmsimilar.html
O8 - Extra context menu item: Translate into English - res://c:\program files\google\GoogleToolbar2.dll/cmtrans.html
O8 - Extra context menu item: Yahoo! &Dictionary - file:///C:\Program Files\Yahoo!\Common/ycdict.htm
O8 - Extra context menu item: Yahoo! &Maps - file:///C:\Program Files\Yahoo!\Common/ycmap.htm
O8 - Extra context menu item: Yahoo! &SMS - file:///C:\Program Files\Yahoo!\Common/ycsms.htm
O9 - Extra button: Yahoo! Services - {5BAB4B5B-68BC-4B02-94D6-2FC0DE4A7897} - C:\Program Files\Yahoo!\Common\yiesrvc.dll
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra button: Microsoft AntiSpyware helper - {6D89FFA1-A46A-486A-8DCB-5D1BCD2F1C07} - C:\WINDOWS\System32\wldr.dll (file missing) (HKCU)
O9 - Extra 'Tools' menuitem: Microsoft AntiSpyware helper - {6D89FFA1-A46A-486A-8DCB-5D1BCD2F1C07} - C:\WINDOWS\System32\wldr.dll (file missing) (HKCU)
O12 - Plugin for .pdf: C:\Program Files\Internet Explorer\PLUGINS\nppdf32.dll
O12 - Plugin for .spop: C:\Program Files\Internet Explorer\Plugins\NPDocBox.dll
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (YInstStarter Class) - C:\Program Files\Yahoo!\Common\yinsthelper.dll
O16 - DPF: {74D05D43-3236-11D4-BDCD-00C04F9A3B61} (HouseCall Control) - http://a840.g.akamai...all/xscan53.cab
O16 - DPF: {D05F33E0-3F75-11D3-A176-006008944486} (Audible Words Codec) - http://download.audi...36/awrdscdc.cab
O20 - Winlogon Notify: STOPzilla - C:\WINDOWS\SYSTEM32\IS3WLHandler.dll
O23 - Service: Ati HotKey Poller - Unknown owner - C:\WINDOWS\System32\Ati2evxx.exe
O23 - Service: Compaq Remote Diagnostics Enabling Agent (CpqDfwWebAgent) - Compaq Computer Corporation - C:\WINDOWS\Cpqdiag\Cpqdfwag.exe
O23 - Service: ewido security suite control - ewido networks - C:\Program Files\ewido\security suite\ewidoctrl.exe
O23 - Service: iPod Service (iPodService) - Apple Computer, Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: LexBce Server (LexBceS) - Lexmark International, Inc. - C:\WINDOWS\system32\LEXBCES.EXE
O23 - Service: OracleAgent80 - oracle - C:\orant\agentbin\DBSNMP.EXE
O23 - Service: OracleClientCache80 - Unknown owner - C:\orant\BIN\ONRSD80.EXE
O23 - Service: OracleDataGatherer - Unknown owner - C:\orant\bin\vppdc.exe
O23 - Service: OracleExtprocAgent - Unknown owner - C:\orant\BIN\EXTPROCT.EXE
O23 - Service: OracleServiceTEK - Oracle Corporation - c:\orant\bin\oracle80.exe
O23 - Service: OracleTNSListener80 - Unknown owner - C:\orant\BIN\TNSLSNR80.EXE
O23 - Service: SAPOSCOL - Unknown owner - C:\usr\sap\TEK\sys\exe\run\SAPOSCOL.EXE
O23 - Service: SAPTEK_00 - SAP AG - C:\usr\sap\TEK\sys\exe\run\SAPSTARTSRV.EXE
O23 - Service: Symantec Network Drivers Service (SNDSrvc) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\SNDSrvc.exe
O23 - Service: VPN 5000 Service 1.00.00 (VPN5000Service) - Unknown owner - C:\Program Files\IntraPort Client\vpn5000service.exe

 This topic is locked
This topic is locked
















 Sign In
Sign In Create Account
Create Account

