OSX.RSPlug.A Trojan Info and Removal
To many Windows users, it sounds all too familiar. Attempting to watch a video online, a prompt directs them to download a codec to enable viewing. However, the download is malware, and it infects their computer.
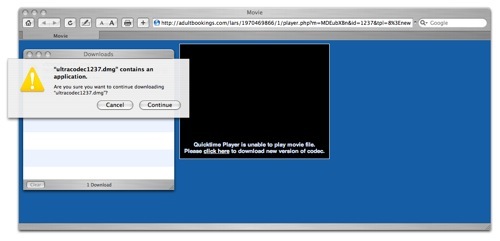
Now this popular, and successful social engineering technique is being used to spread a Mac OSX trojan, OSX.RSPlug.A. At this time spam is being flooded onto Mac forums trying to lure users to the sites where this is employed. The pornography sites present a still image of a video. Clicking on the image to play the video returns the following message:
Quicktime Player is unable to play movie file.
Please click here to download new version of codec.
After that page loads the malware is download as a disk image (.dmg), and launches an installer. The installer requires the user to enter the admin password. If the password entered then the malware infection is complete. This infection alters DNS setting to redirect web pages, and advertisments for porn sites. However, it could just as easily be used for phishing attacks, or search redirects.
The easiest way to tell if you’ve been infected is to go to the top-level /Library -> Internet Plug-Ins folder, and look for a file named plugins.settings. If you find one there, chances are, you’re infected.
If you’re infected, here are removal instructions from MacWorld:
- In the Finder, navigate to /Library -> Internet Plug-Ins, and delete the file named plugins.settings. Empty the trash. This deletes the tool that sets the rogue DNS Server information.
- In Terminal, type sudo crontab -r and provide your admin password when asked. This deletes the root cron job that checks the DNS Server settings. You can prove it worked by typing sudo crontab -l; you should see the message crontab: no crontab for root.
- Open your Network System Preferences panel, go to the DNS Server box, and copy the entries you can see to a Stickies note, TextEdit document, or memorize them. Now retype those same values in the box, then click Apply.
- Reboot your Mac.
While this is newsworthy because there are rarely OSX trojans, there is no ground-breaking code, or new social engineering techniques employed. The goal of this trojan is to generate revenue. This could easily be replicated by any site displaying popular videos, and quickly become widespread among Apple users. While Apple market share has been on the rise, at about 8% it’s still a low-priority target for money-seeking malware authors. However, this could change as Apple continues to gain market share. Is this the start of a new wave of malware aimed at Apple users?