Sounds good to me. log follows:
Virustotal Log:
AhnLab-V3 2008.8.21.0 2008.08.25 -
AntiVir 7.8.1.23 2008.08.24 -
Authentium 5.1.0.4 2008.08.25 -
Avast 4.8.1195.0 2008.08.24 -
AVG 8.0.0.161 2008.08.24 -
BitDefender 7.2 2008.08.25 -
CAT-QuickHeal 9.50 2008.08.22 -
ClamAV 0.93.1 2008.08.25 -
DrWeb 4.44.0.09170 2008.08.24 -
eSafe 7.0.17.0 2008.08.24 -
eTrust-Vet 31.6.6044 2008.08.23 -
Ewido 4.0 2008.08.24 -
F-Prot 4.4.4.56 2008.08.25 -
F-Secure 7.60.13501.0 2008.08.25 -
Fortinet 3.14.0.0 2008.08.25 -
GData 2.0.7306.1023 2008.08.20 -
Ikarus T3.1.1.34.0 2008.08.24 -
K7AntiVirus 7.10.427 2008.08.23 -
Kaspersky 7.0.0.125 2008.08.25 -
McAfee 5368 2008.08.22 -
Microsoft 1.3807 2008.08.25 -
NOD32v2 3383 2008.08.24 -
Norman 5.80.02 2008.08.22 -
Panda 9.0.0.4 2008.08.24 -
PCTools 4.4.2.0 2008.08.24 -
Prevx1 V2 2008.08.25 -
Rising 20.58.62.00 2008.08.24 -
Sophos 4.32.0 2008.08.25 -
Sunbelt 3.1.1575.1 2008.08.23 -
Symantec 10 2008.08.25 -
TheHacker 6.3.0.6.060 2008.08.23 -
TrendMicro 8.700.0.1004 2008.08.25 -
ViRobot 2008.8.22.1346 2008.08.22 -
VirusBuster 4.5.11.0 2008.08.24 -
Webwasher-Gateway 6.6.2 2008.08.25 -
Additional information
File size: 2187904 bytes
MD5...: c3b84871dece94e335b96fafd756316c
SHA1..: da964b943fe4c07424244380b1ba00f0c2aa33cc
SHA256: 13fc5541dd2f6866a0950475e02b46b70394274c7874d90a36b2777a599af554
SHA512: f977d55a255a8c0dee4459300deeac7b0443c500d03eea7eaf3234f26a61c215
f2804ab10d1c22f8713565684e592cfcf6ec9d9629dfd159fc15f31c5e0734a7
PEiD..: -
PEInfo: PE Structure information
( base data )
entrypointaddress.: 0x5d55f6
timedatestamp.....: 0x433b2f93 (Thu Sep 29 00:04:35 2005)
machinetype.......: 0x14c (I386)
( 21 sections )
name viradd virsiz rawdsiz ntrpy md5
.text 0x580 0x71951 0x71980 6.62 02922ea4668d31bf473c15b7ea986555
POOLMI 0x71f00 0x12b3 0x1300 6.32 66979a4015760a909c1182affe21f237
MISYSPTE 0x73200 0x700 0x700 6.27 0613a028fd2937f6ac55ee31b37f441e
POOLCODE 0x73900 0x15a0 0x1600 6.41 1fa48e35a695914b5b0f83db5cb6437f
.data 0x74f00 0x16ca0 0x16d00 0.46 f2f6de406c951cf2e1b6cd3083945f40
PAGE 0x8bc00 0xf8dec 0xf8e00 6.65 13d8dc4cf77d1ca3321313baf56422ff
PAGELK 0x184a00 0xe359 0xe380 6.73 e61720b7dd6871c71b2b8cc9289dac38
PAGEVRFY 0x192d80 0xf1cd 0xf200 6.69 c331b2a8271cb2fae09a90c1c677b3f5
PAGEWMI 0x1a1f80 0x17f2 0x1800 6.48 463f0e486da2e40b3e74bf70df4bce91
PAGEKD 0x1a3780 0x4052 0x4080 6.49 de5a631bb40308edd71111a1cac4aada
PAGESPEC 0x1a7800 0xc43 0xc80 6.33 6c4e74618b033d48f637b5c0af845663
PAGEHDLS 0x1a8480 0x1dd8 0x1e00 6.26 68d8087dc7f750c6faac1a6fb1888020
.edata 0x1aa280 0xb50a 0xb580 6.01 ecf0d90a69a2d28fb55f32c3204a6380
PAGEDATA 0x1b5800 0x1558 0x1580 2.72 852844ad922fd7c0e6f28acde1fde69a
PAGEKD 0x1b6d80 0xc021 0xc080 0.00 cbad60ee682dcc5a4588a519499cd3f3
PAGECONS 0x1c2e00 0x18c 0x200 2.22 b19861548e040fe2ff7c50d37753c648
PAGEVRFC 0x1c3000 0x3449 0x3480 5.25 76276063346ba256e182ace6c6c1c464
PAGEVRFD 0x1c6480 0x648 0x680 2.73 9b138317358351e4d96d6f1cbdcc8c79
INIT 0x1c6b00 0x2d7b8 0x2d800 6.52 e79308b42b492471289184abbdd208b3
.rsrc 0x1f4300 0x12508 0x12580 5.49 911244dbe4ea99948a94eccda6317202
.reloc 0x206880 0xf998 0xfa00 6.78 931be2aee34b761333826c654fca9391
( 3 imports )
> BOOTVID.dll: VidInitialize, VidDisplayString, VidSetTextColor, VidSolidColorFill, VidBitBlt, VidBufferToScreenBlt, VidScreenToBufferBlt, VidResetDisplay, VidCleanUp, VidSetScrollRegion
> HAL.dll: HalReportResourceUsage, HalAllProcessorsStarted, HalQueryRealTimeClock, HalAllocateAdapterChannel, KeStallExecutionProcessor, HalTranslateBusAddress, KfReleaseSpinLock, KfAcquireSpinLock, HalGetBusDataByOffset, HalSetBusDataByOffset, KeQueryPerformanceCounter, HalReturnToFirmware, READ_PORT_UCHAR, READ_PORT_USHORT, READ_PORT_ULONG, WRITE_PORT_UCHAR, WRITE_PORT_USHORT, WRITE_PORT_ULONG, HalInitializeProcessor, HalCalibratePerformanceCounter, HalSetRealTimeClock, HalHandleNMI, HalBeginSystemInterrupt, HalEndSystemInterrupt, KeRaiseIrqlToSynchLevel, KeAcquireInStackQueuedSpinLockRaiseToSynch, HalInitSystem, HalDisableSystemInterrupt, HalEnableSystemInterrupt, KeRaiseIrql, KeLowerIrql, HalClearSoftwareInterrupt, KeReleaseSpinLock, KeAcquireSpinLock, ExTryToAcquireFastMutex, KeAcquireSpinLockRaiseToSynch, KeFlushWriteBuffer, HalProcessorIdle, HalReadDmaCounter, IoMapTransfer, IoFreeMapRegisters, IoFreeAdapterChannel, IoFlushAdapterBuffers, HalFreeCommonBuffer, HalAllocateCommonBuffer, HalAllocateCrashDumpRegisters, HalGetAdapter, HalSetTimeIncrement, HalGetEnvironmentVariable, HalSetEnvironmentVariable, KfRaiseIrql, HalGetInterruptVector, KeGetCurrentIrql, HalRequestSoftwareInterrupt, KeAcquireInStackQueuedSpinLock, KeReleaseInStackQueuedSpinLock, ExAcquireFastMutex, ExReleaseFastMutex, KeRaiseIrqlToDpcLevel, HalSystemVectorDispatchEntry, KfLowerIrql, HalStartProfileInterrupt, HalSetProfileInterval, HalStopProfileInterrupt
> KDCOM.dll: KdD0Transition, KdD3Transition, KdRestore, KdReceivePacket, KdDebuggerInitialize0, KdSave, KdDebuggerInitialize1, KdSendPacket
( 1483 exports )
CcCanIWrite, CcCopyRead, CcCopyWrite, CcDeferWrite, CcFastCopyRead, CcFastCopyWrite, CcFastMdlReadWait, CcFastReadNotPossible, CcFastReadWait, CcFlushCache, CcGetDirtyPages, CcGetFileObjectFromBcb, CcGetFileObjectFromSectionPtrs, CcGetFlushedValidData, CcGetLsnForFileObject, CcInitializeCacheMap, CcIsThereDirtyData, CcMapData, CcMdlRead, CcMdlReadComplete, CcMdlWriteAbort, CcMdlWriteComplete, CcPinMappedData, CcPinRead, CcPrepareMdlWrite, CcPreparePinWrite, CcPurgeCacheSection, CcRemapBcb, CcRepinBcb, CcScheduleReadAhead, CcSetAdditionalCacheAttributes, CcSetBcbOwnerPointer, CcSetDirtyPageThreshold, CcSetDirtyPinnedData, CcSetFileSizes, CcSetLogHandleForFile, CcSetReadAheadGranularity, CcUninitializeCacheMap, CcUnpinData, CcUnpinDataForThread, CcUnpinRepinnedBcb, CcWaitForCurrentLazyWriterActivity, CcZeroData, CmRegisterCallback, CmUnRegisterCallback, DbgBreakPoint, DbgBreakPointWithStatus, DbgLoadImageSymbols, DbgPrint, DbgPrintEx, DbgPrintReturnControlC, DbgPrompt, DbgQueryDebugFilterState, DbgSetDebugFilterState, ExAcquireFastMutexUnsafe, ExAcquireResourceExclusiveLite, ExAcquireResourceSharedLite, ExAcquireRundownProtection, ExAcquireRundownProtectionEx, ExAcquireSharedStarveExclusive, ExAcquireSharedWaitForExclusive, ExAllocateFromPagedLookasideList, ExAllocatePool, ExAllocatePoolWithQuota, ExAllocatePoolWithQuotaTag, ExAllocatePoolWithTag, ExAllocatePoolWithTagPriority, ExConvertExclusiveToSharedLite, ExCreateCallback, ExDeleteNPagedLookasideList, ExDeletePagedLookasideList, ExDeleteResourceLite, ExDesktopObjectType, ExDisableResourceBoostLite, ExEnumHandleTable, ExEventObjectType, ExExtendZone, ExFreePool, ExFreePoolWithTag, ExFreeToPagedLookasideList, ExGetCurrentProcessorCounts, ExGetCurrentProcessorCpuUsage, ExGetExclusiveWaiterCount, ExGetPreviousMode, ExGetSharedWaiterCount, ExInitializeNPagedLookasideList, ExInitializePagedLookasideList, ExInitializeResourceLite, ExInitializeRundownProtection, ExInitializeZone, ExInterlockedAddLargeInteger, ExInterlockedAddLargeStatistic, ExInterlockedAddUlong, ExInterlockedCompareExchange64, ExInterlockedDecrementLong, ExInterlockedExchangeUlong, ExInterlockedExtendZone, ExInterlockedFlushSList, ExInterlockedIncrementLong, ExInterlockedInsertHeadList, ExInterlockedInsertTailList, ExInterlockedPopEntryList, ExInterlockedPopEntrySList, ExInterlockedPushEntryList, ExInterlockedPushEntrySList, ExInterlockedRemoveHeadList, ExIsProcessorFeaturePresent, ExIsResourceAcquiredExclusiveLite, ExIsResourceAcquiredSharedLite, ExLocalTimeToSystemTime, ExNotifyCallback, ExQueryPoolBlockSize, ExQueueWorkItem, ExRaiseAccessViolation, ExRaiseDatatypeMisalignment, ExRaiseException, ExRaiseHardError, ExRaiseStatus, ExReInitializeRundownProtection, ExRegisterCallback, ExReinitializeResourceLite, ExReleaseFastMutexUnsafe, ExReleaseResourceForThreadLite, ExReleaseResourceLite, ExReleaseRundownProtection, ExReleaseRundownProtectionEx, ExRundownCompleted, ExSemaphoreObjectType, ExSetResourceOwnerPointer, ExSetTimerResolution, ExSystemExceptionFilter, ExSystemTimeToLocalTime, ExUnregisterCallback, ExUuidCreate, ExVerifySuite, ExWaitForRundownProtectionRelease, ExWindowStationObjectType, ExfAcquirePushLockExclusive, ExfAcquirePushLockShared, ExfInterlockedAddUlong, ExfInterlockedCompareExchange64, ExfInterlockedInsertHeadList, ExfInterlockedInsertTailList, ExfInterlockedPopEntryList, ExfInterlockedPushEntryList, ExfInterlockedRemoveHeadList, ExfReleasePushLock, Exfi386InterlockedDecrementLong, Exfi386InterlockedExchangeUlong, Exfi386InterlockedIncrementLong, Exi386InterlockedDecrementLong, Exi386InterlockedExchangeUlong, Exi386InterlockedIncrementLong, FsRtlAcquireFileExclusive, FsRtlAddLargeMcbEntry, FsRtlAddMcbEntry, FsRtlAddToTunnelCache, FsRtlAllocateFileLock, FsRtlAllocatePool, FsRtlAllocatePoolWithQuota, FsRtlAllocatePoolWithQuotaTag, FsRtlAllocatePoolWithTag, FsRtlAllocateResource, FsRtlAreNamesEqual, FsRtlBalanceReads, FsRtlCheckLockForReadAccess, FsRtlCheckLockForWriteAccess, FsRtlCheckOplock, FsRtlCopyRead, FsRtlCopyWrite, FsRtlCurrentBatchOplock, FsRtlDeleteKeyFromTunnelCache, FsRtlDeleteTunnelCache, FsRtlDeregisterUncProvider, FsRtlDissectDbcs, FsRtlDissectName, FsRtlDoesDbcsContainWildCards, FsRtlDoesNameContainWildCards, FsRtlFastCheckLockForRead, FsRtlFastCheckLockForWrite, FsRtlFastUnlockAll, FsRtlFastUnlockAllByKey, FsRtlFastUnlockSingle, FsRtlFindInTunnelCache, FsRtlFreeFileLock, FsRtlGetFileSize, FsRtlGetNextFileLock, FsRtlGetNextLargeMcbEntry, FsRtlGetNextMcbEntry, FsRtlIncrementCcFastReadNoWait, FsRtlIncrementCcFastReadNotPossible, FsRtlIncrementCcFastReadResourceMiss, FsRtlIncrementCcFastReadWait, FsRtlInitializeFileLock, FsRtlInitializeLargeMcb, FsRtlInitializeMcb, FsRtlInitializeOplock, FsRtlInitializeTunnelCache, FsRtlInsertPerFileObjectContext, FsRtlInsertPerStreamContext, FsRtlIsDbcsInExpression, FsRtlIsFatDbcsLegal, FsRtlIsHpfsDbcsLegal, FsRtlIsNameInExpression, FsRtlIsNtstatusExpected, FsRtlIsPagingFile, FsRtlIsTotalDeviceFailure, FsRtlLegalAnsiCharacterArray, FsRtlLookupLargeMcbEntry, FsRtlLookupLastLargeMcbEntry, FsRtlLookupLastLargeMcbEntryAndIndex, FsRtlLookupLastMcbEntry, FsRtlLookupMcbEntry, FsRtlLookupPerFileObjectContext, FsRtlLookupPerStreamContextInternal, FsRtlMdlRead, FsRtlMdlReadComplete, FsRtlMdlReadCompleteDev, FsRtlMdlReadDev, FsRtlMdlWriteComplete, FsRtlMdlWriteCompleteDev, FsRtlNormalizeNtstatus, FsRtlNotifyChangeDirectory, FsRtlNotifyCleanup, FsRtlNotifyFilterChangeDirectory, FsRtlNotifyFilterReportChange, FsRtlNotifyFullChangeDirectory, FsRtlNotifyFullReportChange, FsRtlNotifyInitializeSync, FsRtlNotifyReportChange, FsRtlNotifyUninitializeSync, FsRtlNotifyVolumeEvent, FsRtlNumberOfRunsInLargeMcb, FsRtlNumberOfRunsInMcb, FsRtlOplockFsctrl, FsRtlOplockIsFastIoPossible, FsRtlPostPagingFileStackOverflow, FsRtlPostStackOverflow, FsRtlPrepareMdlWrite, FsRtlPrepareMdlWriteDev, FsRtlPrivateLock, FsRtlProcessFileLock, FsRtlRegisterFileSystemFilterCallbacks, FsRtlRegisterUncProvider, FsRtlReleaseFile, FsRtlRemoveLargeMcbEntry, FsRtlRemoveMcbEntry, FsRtlRemovePerFileObjectContext, FsRtlRemovePerStreamContext, FsRtlResetLargeMcb, FsRtlSplitLargeMcb, FsRtlSyncVolumes, FsRtlTeardownPerStreamContexts, FsRtlTruncateLargeMcb, FsRtlTruncateMcb, FsRtlUninitializeFileLock, FsRtlUninitializeLargeMcb, FsRtlUninitializeMcb, FsRtlUninitializeOplock, HalDispatchTable, HalExamineMBR, HalPrivateDispatchTable, HeadlessDispatch, InbvAcquireDisplayOwnership, InbvCheckDisplayOwnership, InbvDisplayString, InbvEnableBootDriver, InbvEnableDisplayString, InbvInstallDisplayStringFilter, InbvIsBootDriverInstalled, InbvNotifyDisplayOwnershipLost, InbvResetDisplay, InbvSetScrollRegion, InbvSetTextColor, InbvSolidColorFill, InitSafeBootMode, InterlockedCompareExchange, InterlockedDecrement, InterlockedExchange, InterlockedExchangeAdd, InterlockedIncrement, InterlockedPopEntrySList, InterlockedPushEntrySList, IoAcquireCancelSpinLock, IoAcquireRemoveLockEx, IoAcquireVpbSpinLock, IoAdapterObjectType, IoAllocateAdapterChannel, IoAllocateController, IoAllocateDriverObjectExtension, IoAllocateErrorLogEntry, IoAllocateIrp, IoAllocateMdl, IoAllocateWorkItem, IoAssignDriveLetters, IoAssignResources, IoAttachDevice, IoAttachDeviceByPointer, IoAttachDeviceToDeviceStack, IoAttachDeviceToDeviceStackSafe, IoBuildAsynchronousFsdRequest, IoBuildDeviceIoControlRequest, IoBuildPartialMdl, IoBuildSynchronousFsdRequest, IoCallDriver, IoCancelFileOpen, IoCancelIrp, IoCheckDesiredAccess, IoCheckEaBufferValidity, IoCheckFunctionAccess, IoCheckQuerySetFileInformation, IoCheckQuerySetVolumeInformation, IoCheckQuotaBufferValidity, IoCheckShareAccess, IoCompleteRequest, IoConnectInterrupt, IoCreateController, IoCreateDevice, IoCreateDisk, IoCreateDriver, IoCreateFile, IoCreateFileSpecifyDeviceObjectHint, IoCreateNotificationEvent, IoCreateStreamFileObject, IoCreateStreamFileObjectEx, IoCreateStreamFileObjectLite, IoCreateSymbolicLink, IoCreateSynchronizationEvent, IoCreateUnprotectedSymbolicLink, IoCsqInitialize, IoCsqInsertIrp, IoCsqRemoveIrp, IoCsqRemoveNextIrp, IoDeleteController, IoDeleteDevice, IoDeleteDriver, IoDeleteSymbolicLink, IoDetachDevice, IoDeviceHandlerObjectSize, IoDeviceHandlerObjectType, IoDeviceObjectType, IoDisconnectInterrupt, IoDriverObjectType, IoEnqueueIrp, IoEnumerateDeviceObjectList, IoFastQueryNetworkAttributes, IoFileObjectType, IoForwardAndCatchIrp, IoForwardIrpSynchronously, IoFreeController, IoFreeErrorLogEntry, IoFreeIrp, IoFreeMdl, IoFreeWorkItem, IoGetAttachedDevice, IoGetAttachedDeviceReference, IoGetBaseFileSystemDeviceObject, IoGetBootDiskInformation, IoGetConfigurationInformation, IoGetCurrentProcess, IoGetDeviceAttachmentBaseRef, IoGetDeviceInterfaceAlias, IoGetDeviceInterfaces, IoGetDeviceObjectPointer, IoGetDeviceProperty, IoGetDeviceToVerify, IoGetDiskDeviceObject, IoGetDmaAdapter, IoGetDriverObjectExtension, IoGetFileObjectGenericMapping, IoGetInitialStack, IoGetLowerDeviceObject, IoGetRelatedDeviceObject, IoGetRequestorProcess, IoGetRequestorProcessId, IoGetRequestorSessionId, IoGetStackLimits, IoGetTopLevelIrp, IoInitializeIrp, IoInitializeRemoveLockEx, IoInitializeTimer, IoInvalidateDeviceRelations, IoInvalidateDeviceState, IoIsFileOriginRemote, IoIsOperationSynchronous, IoIsSystemThread, IoIsValidNameGraftingBuffer, IoIsWdmVersionAvailable, IoMakeAssociatedIrp, IoOpenDeviceInterfaceRegistryKey, IoOpenDeviceRegistryKey, IoPageRead, IoPnPDeliverServicePowerNotification, IoQueryDeviceDescription, IoQueryFileDosDeviceName, IoQueryFileInformation, IoQueryVolumeInformation, IoQueueThreadIrp, IoQueueWorkItem, IoRaiseHardError, IoRaiseInformationalHardError, IoReadDiskSignature, IoReadOperationCount, IoReadPartitionTable, IoReadPartitionTableEx, IoReadTransferCount, IoRegisterBootDriverReinitialization, IoRegisterDeviceInterface, IoRegisterDriverReinitialization, IoRegisterFileSystem, IoRegisterFsRegistrationChange, IoRegisterLastChanceShutdownNotification, IoRegisterPlugPlayNotification, IoRegisterShutdownNotification, IoReleaseCancelSpinLock, IoReleaseRemoveLockAndWaitEx, IoReleaseRemoveLockEx, IoReleaseVpbSpinLock, IoRemoveShareAccess, IoReportDetectedDevice, IoReportHalResourceUsage, IoReportResourceForDetection, IoReportResourceUsage, IoReportTargetDeviceChange, IoReportTargetDeviceChangeAsynchronous, IoRequestDeviceEject, IoReuseIrp, IoSetCompletionRoutineEx, IoSetDeviceInterfaceState, IoSetDeviceToVerify, IoSetFileOrigin, IoSetHardErrorOrVerifyDevice, IoSetInformation, IoSetIoCompletion, IoSetPartitionInformation, IoSetPartitionInformationEx, IoSetShareAccess, IoSetStartIoAttributes, IoSetSystemPartition, IoSetThreadHardErrorMode, IoSetTopLevelIrp, IoStartNextPacket, IoStartNextPacketByKey, IoStartPacket, IoStartTimer, IoStatisticsLock, IoStopTimer, IoSynchronousInvalidateDeviceRelations, IoSynchronousPageWrite, IoThreadToProcess, IoUnregisterFileSystem, IoUnregisterFsRegistrationChange, IoUnregisterPlugPlayNotification, IoUnregisterShutdownNotification, IoUpdateShareAccess, IoValidateDeviceIoControlAccess, IoVerifyPartitionTable, IoVerifyVolume, IoVolumeDeviceToDosName, IoWMIAllocateInstanceIds, IoWMIDeviceObjectToInstanceName, IoWMIExecuteMethod, IoWMIHandleToInstanceName, IoWMIOpenBlock, IoWMIQueryAllData, IoWMIQueryAllDataMultiple, IoWMIQuerySingleInstance, IoWMIQuerySingleInstanceMultiple, IoWMIRegistrationControl, IoWMISetNotificationCallback, IoWMISetSingleInstance, IoWMISetSingleItem, IoWMISuggestInstanceName, IoWMIWriteEvent, IoWriteErrorLogEntry, IoWriteOperationCount, IoWritePartitionTable, IoWritePartitionTableEx, IoWriteTransferCount, IofCallDriver, IofCompleteRequest, KdDebuggerEnabled, KdDebuggerNotPresent, KdDisableDebugger, KdEnableDebugger, KdEnteredDebugger, KdPollBreakIn, KdPowerTransition, Ke386CallBios, Ke386IoSetAccessProcess, Ke386QueryIoAccessMap, Ke386SetIoAccessMap, KeAcquireInStackQueuedSpinLockAtDpcLevel, KeAcquireInterruptSpinLock, KeAcquireSpinLockAtDpcLevel, KeAddSystemServiceTable, KeAreApcsDisabled, KeAttachProcess, KeBugCheck, KeBugCheckEx, KeCancelTimer, KeCapturePersistentThreadState, KeClearEvent, KeConnectInterrupt, KeDcacheFlushCount, KeDelayExecutionThread, KeDeregisterBugCheckCallback, KeDeregisterBugCheckReasonCallback, KeDetachProcess, KeDisconnectInterrupt, KeEnterCriticalRegion, KeEnterKernelDebugger, KeFindConfigurationEntry, KeFindConfigurationNextEntry, KeFlushEntireTb, KeFlushQueuedDpcs, KeGetCurrentThread, KeGetPreviousMode, KeGetRecommendedSharedDataAlignment, KeI386AbiosCall, KeI386AllocateGdtSelectors, KeI386Call16BitCStyleFunction, KeI386Call16BitFunction, KeI386FlatToGdtSelector, KeI386GetLid, KeI386MachineType, KeI386ReleaseGdtSelectors, KeI386ReleaseLid, KeI386SetGdtSelector, KeIcacheFlushCount, KeInitializeApc, KeInitializeDeviceQueue, KeInitializeDpc, KeInitializeEvent, KeInitializeInterrupt, KeInitializeMutant, KeInitializeMutex, KeInitializeQueue, KeInitializeSemaphore, KeInitializeSpinLock, KeInitializeTimer, KeInitializeTimerEx, KeInsertByKeyDeviceQueue, KeInsertDeviceQueue, KeInsertHeadQueue, KeInsertQueue, KeInsertQueueApc, KeInsertQueueDpc, KeIsAttachedProcess, KeIsExecutingDpc, KeLeaveCriticalRegion, KeLoaderBlock, KeNumberProcessors, KeProfileInterrupt, KeProfileInterruptWithSource, KePulseEvent, KeQueryActiveProcessors, KeQueryInterruptTime, KeQueryPriorityThread, KeQueryRuntimeThread, KeQuerySystemTime, KeQueryTickCount, KeQueryTimeIncrement, KeRaiseUserException, KeReadStateEvent, KeReadStateMutant, KeReadStateMutex, KeReadStateQueue, KeReadStateSemaphore, KeReadStateTimer, KeRegisterBugCheckCallback, KeRegisterBugCheckReasonCallback, KeReleaseInStackQueuedSpinLockFromDpcLevel, KeReleaseInterruptSpinLock, KeReleaseMutant, KeReleaseMutex, KeReleaseSemaphore, KeReleaseSpinLockFromDpcLevel, KeRemoveByKeyDeviceQueue, KeRemoveByKeyDeviceQueueIfBusy, KeRemoveDeviceQueue, KeRemoveEntryDeviceQueue, KeRemoveQueue, KeRemoveQueueDpc, KeRemoveSystemServiceTable, KeResetEvent, KeRestoreFloatingPointState, KeRevertToUserAffinityThread, KeRundownQueue, KeSaveFloatingPointState, KeSaveStateForHibernate, KeServiceDescriptorTable, KeSetAffinityThread, KeSetBasePriorityThread, KeSetDmaIoCoherency, KeSetEvent, KeSetEventBoostPriority, KeSetIdealProcessorThread, KeSetImportanceDpc, KeSetKernelStackSwapEnable, KeSetPriorityThread, KeSetProfileIrql, KeSetSystemAffinityThread, KeSetTargetProcessorDpc, KeSetTimeIncrement, KeSetTimeUpdateNotifyRoutine, KeSetTimer, KeSetTimerEx, KeStackAttachProcess, KeSynchronizeExecution, KeTerminateThread, KeTickCount, KeUnstackDetachProcess, KeUpdateRunTime, KeUpdateSystemTime, KeUserModeCallback, KeWaitForMultipleObjects, KeWaitForMutexObject, KeWaitForSingleObject, KefAcquireSpinLockAtDpcLevel, KefReleaseSpinLockFromDpcLevel, Kei386EoiHelper, KiAcquireSpinLock, KiBugCheckData, KiCoprocessorError, KiDeliverApc, KiDispatchInterrupt, KiEnableTimerWatchdog, KiIpiServiceRoutine, KiReleaseSpinLock, KiUnexpectedInterrupt, Kii386SpinOnSpinLock, LdrAccessResource, LdrEnumResources, LdrFindResourceDirectory_U, LdrFindResource_U, LpcPortObjectType, LpcRequestPort, LpcRequestWaitReplyPort, LsaCallAuthenticationPackage, LsaDeregisterLogonProcess, LsaFreeReturnBuffer, LsaLogonUser, LsaLookupAuthenticationPackage, LsaRegisterLogonProcess, Mm64BitPhysicalAddress, MmAddPhysicalMemory, MmAddVerifierThunks, MmAdjustWorkingSetSize, MmAdvanceMdl, MmAllocateContiguousMemory, MmAllocateContiguousMemorySpecifyCache, MmAllocateMappingAddress, MmAllocateNonCachedMemory, MmAllocatePagesForMdl, MmBuildMdlForNonPagedPool, MmCanFileBeTruncated, MmCommitSessionMappedView, MmCreateMdl, MmCreateSection, MmDisableModifiedWriteOfSection, MmFlushImageSection, MmForceSectionClosed, MmFreeContiguousMemory, MmFreeContiguousMemorySpecifyCache, MmFreeMappingAddress, MmFreeNonCachedMemory, MmFreePagesFromMdl, MmGetPhysicalAddress, MmGetPhysicalMemoryRanges, MmGetSystemRoutineAddress, MmGetVirtualForPhysical, MmGrowKernelStack, MmHighestUserAddress, MmIsAddressValid, MmIsDriverVerifying, MmIsNonPagedSystemAddressValid, MmIsRecursiveIoFault, MmIsThisAnNtAsSystem, MmIsVerifierEnabled, MmLockPagableDataSection, MmLockPagableImageSection, MmLockPagableSectionByHandle, MmMapIoSpace, MmMapLockedPages, MmMapLockedPagesSpecifyCache, MmMapLockedPagesWithReservedMapping, MmMapMemoryDumpMdl, MmMapUserAddressesToPage, MmMapVideoDisplay, MmMapViewInSessionSpace, MmMapViewInSystemSpace, MmMapViewOfSection, MmMarkPhysicalMemoryAsBad, MmMarkPhysicalMemoryAsGood, MmPageEntireDriver, MmPrefetchPages, MmProbeAndLockPages, MmProbeAndLockProcessPages, MmProbeAndLockSelectedPages, MmProtectMdlSystemAddress, MmQuerySystemSize, MmRemovePhysicalMemory, MmResetDriverPaging, MmSectionObjectType, MmSecureVirtualMemory, MmSetAddressRangeModified, MmSetBankedSection, MmSizeOfMdl, MmSystemRangeStart, MmTrimAllSystemPagableMemory, MmUnlockPagableImageSection, MmUnlockPages, MmUnmapIoSpace, MmUnmapLockedPages, MmUnmapReservedMapping, MmUnmapVideoDisplay, MmUnmapViewInSessionSpace, MmUnmapViewInSystemSpace, MmUnmapViewOfSection, MmUnsecureVirtualMemory, MmUserProbeAddress, NlsAnsiCodePage, NlsLeadByteInfo, NlsMbCodePageTag, NlsMbOemCodePageTag, NlsOemCodePage, NlsOemLeadByteInfo, NtAddAtom, NtAdjustPrivilegesToken, NtAllocateLocallyUniqueId, NtAllocateUuids, NtAllocateVirtualMemory, NtBuildNumber, NtClose, NtConnectPort, NtCreateEvent, NtCreateFile, NtCreateSection, NtDeleteAtom, NtDeleteFile, NtDeviceIoControlFile, NtDuplicateObject, NtDuplicateToken, NtFindAtom, NtFreeVirtualMemory, NtFsControlFile, NtGlobalFlag, NtLockFile, NtMakePermanentObject, NtMapViewOfSection, NtNotifyChangeDirectoryFile, NtOpenFile, NtOpenProcess, NtOpenProcessToken, NtOpenProcessTokenEx, NtOpenThread, NtOpenThreadToken, NtOpenThreadTokenEx, NtQueryDirectoryFile, NtQueryEaFile, NtQueryInformationAtom, NtQueryInformationFile, NtQueryInformationProcess, NtQueryInformationThread, NtQueryInformationToken, NtQueryQuotaInformationFile, NtQuerySecurityObject, NtQuerySystemInformation, NtQueryVolumeInformationFile, NtReadFile, NtRequestPort, NtRequestWaitReplyPort, NtSetEaFile, NtSetEvent, NtSetInformationFile, NtSetInformationProcess, NtSetInformationThread, NtSetQuotaInformationFile, NtSetSecurityObject, NtSetVolumeInformationFile, NtShutdownSystem, NtTraceEvent, NtUnlockFile, NtVdmControl, NtWaitForSingleObject, NtWriteFile, ObAssignSecurity, ObCheckCreateObjectAccess, ObCheckObjectAccess, ObCloseHandle, ObCreateObject, ObCreateObjectType, ObDereferenceObject, ObDereferenceSecurityDescriptor, ObFindHandleForObject, ObGetObjectSecurity, ObInsertObject, ObLogSecurityDescriptor, ObMakeTemporaryObject, ObOpenObjectByName, ObOpenObjectByPointer, ObQueryNameString, ObQueryObjectAuditingByHandle, ObReferenceObjectByHandle, ObReferenceObjectByName, ObReferenceObjectByPointer, ObReferenceSecurityDescriptor, ObReleaseObjectSecurity, ObSetHandleAttributes, ObSetSecurityDescriptorInfo, ObSetSecurityObjectByPointer, ObfDereferenceObject, ObfReferenceObject, PfxFindPrefix, PfxInitialize, PfxInsertPrefix, PfxRemovePrefix, PoCallDriver, PoCancelDeviceNotify, PoQueueShutdownWorkItem, PoRegisterDeviceForIdleDetection, PoRegisterDeviceNotify, PoRegisterSystemState, PoRequestPowerIrp, PoRequestShutdownEvent, PoSetHiberRange, PoSetPowerState, PoSetSystemState, PoShutdownBugCheck, PoStartNextPowerIrp, PoUnregisterSystemState, ProbeForRead, ProbeForWrite, PsAssignImpersonationToken, PsChargePoolQuota, PsChargeProcessNonPagedPoolQuota, PsChargeProcessPagedPoolQuota, PsChargeProcessPoolQuota, PsCreateSystemProcess, PsCreateSystemThread, PsDereferenceImpersonationToken, PsDereferencePrimaryToken, PsDisableImpersonation, PsEstablishWin32Callouts, PsGetContextThread, PsGetCurrentProcess, PsGetCurrentProcessId, PsGetCurrentProcessSessionId, PsGetCurrentThread, PsGetCurrentThreadId, PsGetCurrentThreadPreviousMode, PsGetCurrentThreadStackBase, PsGetCurrentThreadStackLimit, PsGetJobLock, PsGetJobSessionId, PsGetJobUIRestrictionsClass, PsGetProcessCreateTimeQuadPart, PsGetProcessDebugPort, PsGetProcessExitProcessCalled, PsGetProcessExitStatus, PsGetProcessExitTime, PsGetProcessId, PsGetProcessImageFileName, PsGetProcessInheritedFromUniqueProcessId, PsGetProcessJob, PsGetProcessPeb, PsGetProcessPriorityClass, PsGetProcessSectionBaseAddress, PsGetProcessSecurityPort, PsGetProcessSessionId, PsGetProcessWin32Process, PsGetProcessWin32WindowStation, PsGetThreadFreezeCount, PsGetThreadHardErrorsAreDisabled, PsGetThreadId, PsGetThreadProcess, PsGetThreadProcessId, PsGetThreadSessionId, PsGetThreadTeb, PsGetThreadWin32Thread, PsGetVersion, PsImpersonateClient, PsInitialSystemProcess, PsIsProcessBeingDebugged, PsIsSystemThread, PsIsThreadImpersonating, PsIsThreadTerminating, PsJobType, PsLookupProcessByProcessId, PsLookupProcessThreadByCid, PsLookupThreadByThreadId, PsProcessType, PsReferenceImpersonationToken, PsReferencePrimaryToken, PsRemoveCreateThreadNotifyRoutine, PsRemoveLoadImageNotifyRoutine, PsRestoreImpersonation, PsReturnPoolQuota, PsReturnProcessNonPagedPoolQuota, PsReturnProcessPagedPoolQuota, PsRevertThreadToSelf, PsRevertToSelf, PsSetContextThread, PsSetCreateProcessNotifyRoutine, PsSetCreateThreadNotifyRoutine, PsSetJobUIRestrictionsClass, PsSetLegoNotifyRoutine, PsSetLoadImageNotifyRoutine, PsSetProcessPriorityByClass, PsSetProcessPriorityClass, PsSetProcessSecurityPort, PsSetProcessWin32Process, PsSetProcessWindowStation, PsSetThreadHardErrorsAreDisabled, PsSetThreadWin32Thread, PsTerminateSystemThread, PsThreadType, READ_REGISTER_BUFFER_UCHAR, READ_REGISTER_BUFFER_ULONG, READ_REGISTER_BUFFER_USHORT, READ_REGISTER_UCHAR, READ_REGISTER_ULONG, READ_REGISTER_USHORT, RtlAbsoluteToSelfRelativeSD, RtlAddAccessAllowedAce, RtlAddAccessAllowedAceEx, RtlAddAce, RtlAddAtomToAtomTable, RtlAddRange, RtlAllocateHeap, RtlAnsiCharToUnicodeChar, RtlAnsiStringToUnicodeSize, RtlAnsiStringToUnicodeString, RtlAppendAsciizToString, RtlAppendStringToString, RtlAppendUnicodeStringToString, RtlAppendUnicodeToString, RtlAreAllAccessesGranted, RtlAreAnyAccessesGranted, RtlAreBitsClear, RtlAreBitsSet, RtlAssert, RtlCaptureContext, RtlCaptureStackBackTrace, RtlCharToInteger, RtlCheckRegistryKey, RtlClearAllBits, RtlClearBit, RtlClearBits, RtlCompareMemory, RtlCompareMemoryUlong, RtlCompareString, RtlCompareUnicodeString, RtlCompressBuffer, RtlCompressChunks, RtlConvertLongToLargeInteger, RtlConvertSidToUnicodeString, RtlConvertUlongToLargeInteger, RtlCopyLuid, RtlCopyRangeList, RtlCopySid, RtlCopyString, RtlCopyUnicodeString, RtlCreateAcl, RtlCreateAtomTable, RtlCreateHeap, RtlCreateRegistryKey, RtlCreateSecurityDescriptor, RtlCreateSystemVolumeInformationFolder, RtlCreateUnicodeString, RtlCustomCPToUnicodeN, RtlDecompressBuffer, RtlDecompressChunks, RtlDecompressFragment, RtlDelete, RtlDeleteAce, RtlDeleteAtomFromAtomTable, RtlDeleteElementGenericTable, RtlDeleteElementGenericTableAvl, RtlDeleteNoSplay, RtlDeleteOwnersRanges, RtlDeleteRange, RtlDeleteRegistryValue, RtlDescribeChunk, RtlDestroyAtomTable, RtlDestroyHeap, RtlDowncaseUnicodeString, RtlEmptyAtomTable, RtlEnlargedIntegerMultiply, RtlEnlargedUnsignedDivide, RtlEnlargedUnsignedMultiply, RtlEnumerateGenericTable, RtlEnumerateGenericTableAvl, RtlEnumerateGenericTableLikeADirectory, RtlEnumerateGenericTableWithoutSplaying, RtlEnumerateGenericTableWithoutSplayingAvl, RtlEqualLuid, RtlEqualSid, RtlEqualString, RtlEqualUnicodeString, RtlExtendedIntegerMultiply, RtlExtendedLargeIntegerDivide, RtlExtendedMagicDivide, RtlFillMemory, RtlFillMemoryUlong, RtlFindClearBits, RtlFindClearBitsAndSet, RtlFindClearRuns, RtlFindFirstRunClear, RtlFindLastBackwardRunClear, RtlFindLeastSignificantBit, RtlFindLongestRunClear, RtlFindMessage, RtlFindMostSignificantBit, RtlFindNextForwardRunClear, RtlFindRange, RtlFindSetBits, RtlFindSetBitsAndClear, RtlFindUnicodePrefix, RtlFormatCurrentUserKeyPath, RtlFreeAnsiString, RtlFreeHeap, RtlFreeOemString, RtlFreeRangeList, RtlFreeUnicodeString, RtlGUIDFromString, RtlGenerate8dot3Name, RtlGetAce, RtlGetCallersAddress, RtlGetCompressionWorkSpaceSize, RtlGetDaclSecurityDescriptor, RtlGetDefaultCodePage, RtlGetElementGenericTable, RtlGetElementGenericTableAvl, RtlGetFirstRange, RtlGetGroupSecurityDescriptor, RtlGetNextRange, RtlGetNtGlobalFlags, RtlGetOwnerSecurityDescriptor, RtlGetSaclSecurityDescriptor, RtlGetSetBootStatusData, RtlGetVersion, RtlHashUnicodeString, RtlImageDirectoryEntryToData, RtlImageNtHeader, RtlInitAnsiString, RtlInitCodePageTable, RtlInitString, RtlInitUnicodeString, RtlInitializeBitMap, RtlInitializeGenericTable, RtlInitializeGenericTableAvl, RtlInitializeRangeList, RtlInitializeSid, RtlInitializeUnicodePrefix, RtlInsertElementGenericTable, RtlInsertElementGenericTableAvl, RtlInsertElementGenericTableFull, RtlInsertElementGenericTableFullAvl, RtlInsertUnicodePrefix, RtlInt64ToUnicodeString, RtlIntegerToChar, RtlIntegerToUnicode, RtlIntegerToUnicodeString, RtlInvertRangeList, RtlIpv4AddressToStringA, RtlIpv4AddressToStringExA, RtlIpv4AddressToStringExW, RtlIpv4AddressToStringW, RtlIpv4StringToAddressA, RtlIpv4StringToAddressExA, RtlIpv4StringToAddressExW, RtlIpv4StringToAddressW, RtlIpv6AddressToStringA, RtlIpv6AddressToStringExA, RtlIpv6AddressToStringExW, RtlIpv6AddressToStringW, RtlIpv6StringToAddressA, RtlIpv6StringToAddressExA, RtlIpv6StringToAddressExW, RtlIpv6StringToAddressW, RtlIsGenericTableEmpty, RtlIsGenericTableEmptyAvl, RtlIsNameLegalDOS8Dot3, RtlIsRangeAvailable, RtlIsValidOemCharacter, RtlLargeIntegerAdd, RtlLargeIntegerArithmeticShift, RtlLargeIntegerDivide, RtlLargeIntegerNegate, RtlLargeIntegerShiftLeft, RtlLargeIntegerShiftRight, RtlLargeIntegerSubtract, RtlLengthRequiredSid, RtlLengthSecurityDescriptor, RtlLengthSid, RtlLockBootStatusData, RtlLookupAtomInAtomTable, RtlLookupElementGenericTable, RtlLookupElementGenericTableAvl, RtlLookupElementGenericTableFull, RtlLookupElementGenericTableFullAvl, RtlMapGenericMask, RtlMapSecurityErrorToNtStatus, RtlMergeRangeLists, RtlMoveMemory, RtlMultiByteToUnicodeN, RtlMultiByteToUnicodeSize, RtlNextUnicodePrefix, RtlNtStatusToDosError, RtlNtStatusToDosErrorNoTeb, RtlNumberGenericTableElements, RtlNumberGenericTableElementsAvl, RtlNumberOfClearBits, RtlNumberOfSetBits, RtlOemStringToCountedUnicodeString, RtlOemStringToUnicodeSize, RtlOemStringToUnicodeString, RtlOemToUnicodeN, RtlPinAtomInAtomTable, RtlPrefetchMemoryNonTemporal, RtlPrefixString, RtlPrefixUnicodeString, RtlQueryAtomInAtomTable, RtlQueryRegistryValues, RtlQueryTimeZoneInformation, RtlRaiseException, RtlRandom, RtlRandomEx, RtlRealPredecessor, RtlRealSuccessor, RtlRemoveUnicodePrefix, RtlReserveChunk, RtlSecondsSince1970ToTime, RtlSecondsSince1980ToTime, RtlSelfRelativeToAbsoluteSD, RtlSelfRelativeToAbsoluteSD2, RtlSetAllBits, RtlSetBit, RtlSetBits, RtlSetDaclSecurityDescriptor, RtlSetGroupSecurityDescriptor, RtlSetOwnerSecurityDescriptor, RtlSetSaclSecurityDescriptor, RtlSetTimeZoneInformation, RtlSizeHeap, RtlSplay, RtlStringFromGUID, RtlSubAuthorityCountSid, RtlSubAuthoritySid, RtlSubtreePredecessor, RtlSubtreeSuccessor, RtlTestBit, RtlTimeFieldsToTime, RtlTimeToElapsedTimeFields, RtlTimeToSecondsSince1970, RtlTimeToSecondsSince1980, RtlTimeToTimeFields, RtlTraceDatabaseAdd, RtlTraceDatabaseCreate, RtlTraceDatabaseDestroy, RtlTraceDatabaseEnumerate, RtlTraceDatabaseFind, RtlTraceDatabaseLock, RtlTraceDatabaseUnlock, RtlTraceDatabaseValidate, RtlUlongByteSwap, RtlUlonglongByteSwap, RtlUnicodeStringToAnsiSize, RtlUnicodeStringToAnsiString, RtlUnicodeStringToCountedOemString, RtlUnicodeStringToInteger, RtlUnicodeStringToOemSize, RtlUnicodeStringToOemString, RtlUnicodeToCustomCPN, RtlUnicodeToMultiByteN, RtlUnicodeToMultiByteSize, RtlUnicodeToOemN, RtlUnlockBootStatusData, RtlUnwind, RtlUpcaseUnicodeChar, RtlUpcaseUnicodeString, RtlUpcaseUnicodeStringToAnsiString, RtlUpcaseUnicodeStringToCountedOemString, RtlUpcaseUnicodeStringToOemString, RtlUpcaseUnicodeToCustomCPN, RtlUpcaseUnicodeToMultiByteN, RtlUpcaseUnicodeToOemN, RtlUpperChar, RtlUpperString, RtlUshortByteSwap, RtlValidRelativeSecurityDescriptor, RtlValidSecurityDescriptor, RtlValidSid, RtlVerifyVersionInfo, RtlVolumeDeviceToDosName, RtlWalkFrameChain, RtlWriteRegistryValue, RtlZeroHeap, RtlZeroMemory, RtlxAnsiStringToUnicodeSize, RtlxOemStringToUnicodeSize, RtlxUnicodeStringToAnsiSize, RtlxUnicodeStringToOemSize, SeAccessCheck, SeAppendPrivileges, SeAssignSecurity, SeAssignSecurityEx, SeAuditHardLinkCreation, SeAuditingFileEvents, SeAuditingFileEventsWithContext, SeAuditingFileOrGlobalEvents, SeAuditingHardLinkEvents, SeAuditingHardLinkEventsWithContext, SeCaptureSecurityDescriptor, SeCaptureSubjectContext, SeCloseObjectAuditAlarm, SeCreateAccessState, SeCreateClientSecurity, SeCreateClientSecurityFromSubjectContext, SeDeassignSecurity, SeDeleteAccessState, SeDeleteObjectAuditAlarm, SeExports, SeFilterToken, SeFreePrivileges, SeImpersonateClient, SeImpersonateClientEx, SeLockSubjectContext, SeMarkLogonSessionForTerminationNotification, SeOpenObjectAuditAlarm, SeOpenObjectForDeleteAuditAlarm, SePrivilegeCheck, SePrivilegeObjectAuditAlarm, SePublicDefaultDacl, SeQueryAuthenticationIdToken, SeQueryInformationToken, SeQuerySecurityDescriptorInfo, SeQuerySessionIdToken, SeRegisterLogonSessionTerminatedRoutine, SeReleaseSecurityDescriptor, SeReleaseSubjectContext, SeSetAccessStateGenericMapping, SeSetSecurityDescriptorInfo, SeSetSecurityDescriptorInfoEx, SeSinglePrivilegeCheck, SeSystemDefaultDacl, SeTokenImpersonationLevel, SeTokenIsAdmin, SeTokenIsRestricted, SeTokenIsWriteRestricted, SeTokenObjectType, SeTokenType, SeUnlockSubjectContext, SeUnregisterLogonSessionTerminatedRoutine, SeValidSecurityDescriptor, VerSetConditionMask, VfFailDeviceNode, VfFailDriver, VfFailSystemBIOS, VfIsVerificationEnabled, WRITE_REGISTER_BUFFER_UCHAR, WRITE_REGISTER_BUFFER_ULONG, WRITE_REGISTER_BUFFER_USHORT, WRITE_REGISTER_UCHAR, WRITE_REGISTER_ULONG, WRITE_REGISTER_USHORT, WmiFlushTrace, WmiGetClock, WmiQueryTrace, WmiQueryTraceInformation, WmiStartTrace, WmiStopTrace, WmiTraceMessage, WmiTraceMessageVa, WmiUpdateTrace, XIPDispatch, ZwAccessCheckAndAuditAlarm, ZwAddBootEntry, ZwAdjustPrivilegesToken, ZwAlertThread, ZwAllocateVirtualMemory, ZwAssignProcessToJobObject, ZwCancelIoFile, ZwCancelTimer, ZwClearEvent, ZwClose, ZwCloseObjectAuditAlarm, ZwConnectPort, ZwCreateDirectoryObject, ZwCreateEvent, ZwCreateFile, ZwCreateJobObject, ZwCreateKey, ZwCreateSection, ZwCreateSymbolicLinkObject, ZwCreateTimer, ZwDeleteBootEntry, ZwDeleteFile, ZwDeleteKey, ZwDeleteValueKey, ZwDeviceIoControlFile, ZwDisplayString, ZwDuplicateObject, ZwDuplicateToken, ZwEnumerateBootEntries, ZwEnumerateKey, ZwEnumerateValueKey, ZwFlushInstructionCache, ZwFlushKey, ZwFlushVirtualMemory, ZwFreeVirtualMemory, ZwFsControlFile, ZwInitiatePowerAction, ZwIsProcessInJob, ZwLoadDriver, ZwLoadKey, ZwMakeTemporaryObject, ZwMapViewOfSection, ZwNotifyChangeKey, ZwOpenDirectoryObject, ZwOpenEvent, ZwOpenFile, ZwOpenJobObject, ZwOpenKey, ZwOpenProcess, ZwOpenProcessToken, ZwOpenProcessTokenEx, ZwOpenSection, ZwOpenSymbolicLinkObject, ZwOpenThread, ZwOpenThreadToken, ZwOpenThreadTokenEx, ZwOpenTimer, ZwPowerInformation, ZwPulseEvent, ZwQueryBootEntryOrder, ZwQueryBootOptions, ZwQueryDefaultLocale, ZwQueryDefaultUILanguage, ZwQueryDirectoryFile, ZwQueryDirectoryObject, ZwQueryEaFile, ZwQueryFullAttributesFile, ZwQueryInformationFile, ZwQueryInformationJobObject, ZwQueryInformationProcess, ZwQueryInformationThread, ZwQueryInformationToken, ZwQueryInstallUILanguage, ZwQueryKey, ZwQueryObject, ZwQuerySection, ZwQuerySecurityObject, ZwQuerySymbolicLinkObject, ZwQuerySystemInformation, ZwQueryValueKey, ZwQueryVolumeInformationFile, ZwReadFile, ZwReplaceKey, ZwRequestWaitReplyPort, ZwResetEvent, ZwRestoreKey, ZwSaveKey, ZwSaveKeyEx, ZwSetBootEntryOrder, ZwSetBootOptions, ZwSetDefaultLocale, ZwSetDefaultUILanguage, ZwSetEaFile, ZwSetEvent, ZwSetInformationFile, ZwSetInformationJobObject, ZwSetInformationObject, ZwSetInformationProcess, ZwSetInformationThread, ZwSetSecurityObject, ZwSetSystemInformation, ZwSetSystemTime, ZwSetTimer, ZwSetValueKey, ZwSetVolumeInformationFile, ZwTerminateJobObject, ZwTerminateProcess, ZwTranslateFilePath, ZwUnloadDriver, ZwUnloadKey, ZwUnmapViewOfSection, ZwWaitForMultipleObjects, ZwWaitForSingleObject, ZwWriteFile, ZwYieldExecution, _CIcos, _CIsin, _CIsqrt, _abnormal_termination, _alldiv, _alldvrm, _allmul, _alloca_probe, _allrem, _allshl, _allshr, _aulldiv, _aulldvrm, _aullrem, _aullshr, _except_handler2, _except_handler3, _global_unwind2, _itoa, _itow, _local_unwind2, _purecall, _snprintf, _snwprintf, _stricmp, _strlwr, _strnicmp, _strnset, _strrev, _strset, _strupr, _vsnprintf, _vsnwprintf, _wcsicmp, _wcslwr, _wcsnicmp, _wcsnset, _wcsrev, _wcsupr, atoi, atol, isdigit, islower, isprint, isspace, isupper, isxdigit, mbstowcs, mbtowc, memchr, memcpy, memmove, memset, qsort, rand, sprintf, srand, strcat, strchr, strcmp, strcpy, strlen, strncat, strncmp, strncpy, strrchr, strspn, strstr, swprintf, tolower, toupper, towlower, towupper, vDbgPrintEx, vDbgPrintExWithPrefix, vsprintf, wcscat, wcschr, wcscmp, wcscpy, wcscspn, wcslen, wcsncat, wcsncmp, wcsncpy, wcsrchr, wcsspn, wcsstr, wcstombs, wctomb
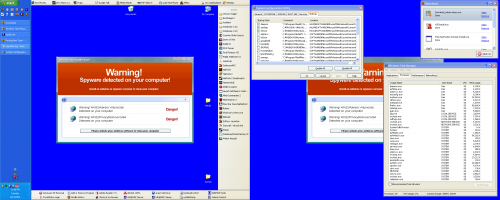
Man. That's a pretty long log, compared to the other ones so far. Hope that helps clear things up!

 This topic is locked
This topic is locked















 Sign In
Sign In Create Account
Create Account

