Kaspersky Online ScannerWelcome to the Kaspersky Online Scanner! Use it to
scan your PC for viruses and other malware for free
Warning: if you have installed Kaspersky Online Scanner Pro, please
manually uninstall it using "Add/Remove Programs" before installing this
version! Otherwise this version will not function correctly.
Benefits:
Kaspersky Anti-Virus exceptional detection rates and thorough scanning
Hourly AV database updates available each time the Online Scanner is
launched
Heuristic analysis to detect unknown viruses
Simple installation (just click on a link)
Requirements and limitations:
When using this service for the first time, you have to run with
Administrator privileges in order to install the product. Also, you will
need to download and install files about 400 KB in size followed by 9 MB
of virus definitions.
However, if you use the Online Scanner again, you will only need to
download the files that have been updated since your last scan.
The Online Scanner service offered by Kaspersky Lab uses Microsoft ActiveX
technology. Microsoft ActiveX Technology and the Kaspersky Online Scanner
work only with MS Internet Explorer 6.0 or higher.
We cannot guarantee that the Online Scanner will function correctly if you
are using any other browser or any Internet Explorer extensions (such as
AvantBrowser). If you use a different browser, you can use the Kaspersky
File Scanner to scan individual files.
The free Kaspersky Online Scanner does not scan boot sectors and MBRs, so
it cannot detect malicious code located in these areas.
Please note: The free Kaspersky Online Scanner does not protect against
malicious code, and cannot prevent future infections. It only detects
malware that has already penetrated your computer. We strongly recommend
that you install a full antivirus solution to protect your system.
Privacy statement:
The Kaspersky Online Scanner will collect information about the malicious
programs found on your computer during the scanning process. The
information will be sent to the Kaspersky Virus Lab for statistical
purposes. No personal information about you or specific information about
your system will be collected or transmitted to Kaspersky Lab.
Select: All, None, Suspicious Selected objects: 0
Scan settings:
Here you can configure the scanning process.
Scan using the following antivirus database:
standard - detect viruses, worms, Trojans,
rootkits
extended - protect your computer from Spyware,
adware, dialers and potentially dangerous
software such as remote access utilities, prank
programs and jokes. We do not recommend this
option to beginners or inexperienced users.
Scan options:
Scan Archives - scan files inside archives
Note: affects all targets except 'A
File...' scan target.
Scan Mail Bases - scan e-mails/attachments
inside mail base files
Note: affects all targets except 'My
Email' and 'A File...' scan targets.
Initialize Kaspersky Online Scanner
(downloading and installing Kaspersky Online
Scanner ActiveX from the server into your
computer)
Update Kaspersky Anti-Virus Databases [100%]:
(downloading and installing the latest Kaspersky
Anti-Virus Databases)
Please wait to update the virus definitions...
Downloading from url:
http://downloads1.kaspersky-labs.com
Downloading remote file: master.xml
Downloading remote file: kavset.xml
Downloading remote file: soft.xml
Downloading remote file: updcfg.xml
Downloading remote file: kernel.avc
Downloading remote file: krnunp.avc
Downloading remote file: krnexe.avc
Downloading remote file: krnmacro.avc
Downloading remote file: krnjava.avc
Downloading remote file: krndos.avc
Downloading remote file: krngen.avc
Downloading remote file: krnexe32.avc
Downloading remote file: krnengn.avc
Downloading remote file: krn001.avc
Downloading remote file: krn002.avc
Downloading remote file: krn003.avc
Downloading remote file: krn004.avc
Downloading remote file: krn005.avc
Downloading remote file: smart.avc
Downloading remote file: ocr.avc
Downloading remote file: chuka.avc
Downloading remote file: fa001.avc
Downloading remote file: base001c.avc
Downloading remote file: base002c.avc
Downloading remote file: base003c.avc
Downloading remote file: base004c.avc
Downloading remote file: base005c.avc
Downloading remote file: base006c.avc
Downloading remote file: base007c.avc
Downloading remote file: base008c.avc
Downloading remote file: base009c.avc
Downloading remote file: base010c.avc
Downloading remote file: base011c.avc
Downloading remote file: base012c.avc
Downloading remote file: base013c.avc
Downloading remote file: base014c.avc
Downloading remote file: base015c.avc
Downloading remote file: base016c.avc
Downloading remote file: base017c.avc
Downloading remote file: base018c.avc
Downloading remote file: base019c.avc
Downloading remote file: base020c.avc
Downloading remote file: base021c.avc
Downloading remote file: base022c.avc
Downloading remote file: base023c.avc
Downloading remote file: base024c.avc
Downloading remote file: base025c.avc
Downloading remote file: base026c.avc
Downloading remote file: base027c.avc
Downloading remote file: base028c.avc
Downloading remote file: base029c.avc
Downloading remote file: base030c.avc
Downloading remote file: base031c.avc
Downloading remote file: base032c.avc
Downloading remote file: base033c.avc
Downloading remote file: base034c.avc
Downloading remote file: base035c.avc
Downloading remote file: base036c.avc
Downloading remote file: base037c.avc
Downloading remote file: base038c.avc
Downloading remote file: base039c.avc
Downloading remote file: base040c.avc
Downloading remote file: base041c.avc
Downloading remote file: base042c.avc
Downloading remote file: base043c.avc
Downloading remote file: base044c.avc
Downloading remote file: base045c.avc
Downloading remote file: base046c.avc
Downloading remote file: base047c.avc
Downloading remote file: base048c.avc
Downloading remote file: base049c.avc
Downloading remote file: base050c.avc
Downloading remote file: base051c.avc
Downloading remote file: base052c.avc
Downloading remote file: base053c.avc
Downloading remote file: base054c.avc
Downloading remote file: base055c.avc
Downloading remote file: base056c.avc
Downloading remote file: base057c.avc
Downloading remote file: base058c.avc
Downloading remote file: base059c.avc
Downloading remote file: base060c.avc
Downloading remote file: base061c.avc
Downloading remote file: base062c.avc
Downloading remote file: base063c.avc
Downloading remote file: base064c.avc
Downloading remote file: base065c.avc
Downloading remote file: base066c.avc
Downloading remote file: base067c.avc
Downloading remote file: base068c.avc
Downloading remote file: base069c.avc
Downloading remote file: base070c.avc
Downloading remote file: base071c.avc
Downloading remote file: base072c.avc
Downloading remote file: base073c.avc
Downloading remote file: base074c.avc
Downloading remote file: base075c.avc
Downloading remote file: base076c.avc
Downloading remote file: base077c.avc
Downloading remote file: base078c.avc
Downloading remote file: base079c.avc
Downloading remote file: base080c.avc
Downloading remote file: base081c.avc
Downloading remote file: base082c.avc
Downloading remote file: base083c.avc
Downloading remote file: base084c.avc
Downloading remote file: base085c.avc
Downloading remote file: base086c.avc
Downloading remote file: base087c.avc
Downloading remote file: base088c.avc
Downloading remote file: base089c.avc
Downloading remote file: base090c.avc
Downloading remote file: base091c.avc
Downloading remote file: base092c.avc
Downloading remote file: base093c.avc
Downloading remote file: base094c.avc
Downloading remote file: base095c.avc
Downloading remote file: base096c.avc
Downloading remote file: base097c.avc
Downloading remote file: dailyc.avc
Downloading remote file: ext001c.avc
Downloading remote file: ext002c.avc
Downloading remote file: ext003c.avc
Downloading remote file: ext004c.avc
Downloading remote file: ext005c.avc
Downloading remote file: ext006c.avc
Downloading remote file: ext007c.avc
Downloading remote file: ext008c.avc
Downloading remote file: ext009c.avc
Downloading remote file: ext010c.avc
Downloading remote file: ext011c.avc
Downloading remote file: daily-ec.avc
Downloading remote file: base001.avc
Downloading remote file: base002.avc
Downloading remote file: base003.avc
Downloading remote file: base004.avc
Downloading remote file: base005.avc
Downloading remote file: base006.avc
Downloading remote file: base007.avc
Downloading remote file: base008.avc
Downloading remote file: base009.avc
Downloading remote file: base010.avc
Downloading remote file: base011.avc
Downloading remote file: base012.avc
Downloading remote file: base013.avc
Downloading remote file: base014.avc
Downloading remote file: base015.avc
Downloading remote file: base016.avc
Downloading remote file: base017.avc
Downloading remote file: base018.avc
Downloading remote file: base019.avc
Downloading remote file: base020.avc
Downloading remote file: base021.avc
Downloading remote file: base022.avc
Downloading remote file: base023.avc
Downloading remote file: base024.avc
Downloading remote file: base025.avc
Downloading remote file: base026.avc
Downloading remote file: base027.avc
Downloading remote file: base028.avc
Downloading remote file: base029.avc
Downloading remote file: base030.avc
Downloading remote file: base031.avc
Downloading remote file: base032.avc
Downloading remote file: base033.avc
Downloading remote file: base034.avc
Downloading remote file: base035.avc
Downloading remote file: base036.avc
Downloading remote file: base037.avc
Downloading remote file: base038.avc
Downloading remote file: base039.avc
Downloading remote file: base040.avc
Downloading remote file: base041.avc
Downloading remote file: base042.avc
Downloading remote file: base043.avc
Downloading remote file: base044.avc
Downloading remote file: base045.avc
Downloading remote file: base046.avc
Downloading remote file: base047.avc
Downloading remote file: base048.avc
Downloading remote file: base049.avc
Downloading remote file: base050.avc
Downloading remote file: base051.avc
Downloading remote file: base052.avc
Downloading remote file: base053.avc
Downloading remote file: base054.avc
Downloading remote file: base055.avc
Downloading remote file: base056.avc
Downloading remote file: base057.avc
Downloading remote file: base058.avc
Downloading remote file: base059.avc
Downloading remote file: base060.avc
Downloading remote file: base061.avc
Downloading remote file: base062.avc
Downloading remote file: base063.avc
Downloading remote file: base064.avc
Downloading remote file: base065.avc
Downloading remote file: base066.avc
Downloading remote file: base067.avc
Downloading remote file: base068.avc
Downloading remote file: base069.avc
Downloading remote file: base070.avc
Downloading remote file: base071.avc
Downloading remote file: base072.avc
Downloading remote file: base073.avc
Downloading remote file: base074.avc
Downloading remote file: base075.avc
Downloading remote file: base076.avc
Downloading remote file: base077.avc
Downloading remote file: base078.avc
Downloading remote file: base079.avc
Downloading remote file: base080.avc
Downloading remote file: base081.avc
Downloading remote file: base082.avc
Downloading remote file: base083.avc
Downloading remote file: base084.avc
Downloading remote file: base085.avc
Downloading remote file: base086.avc
Downloading remote file: base087.avc
Downloading remote file: base088.avc
Downloading remote file: base089.avc
Downloading remote file: base090.avc
Downloading remote file: base091.avc
Downloading remote file: base092.avc
Downloading remote file: base093.avc
Downloading remote file: base094.avc
Downloading remote file: base095.avc
Downloading remote file: base096.avc
Downloading remote file: base097.avc
Downloading remote file: base098.avc
Downloading remote file: base099.avc
Downloading remote file: base100.avc
Downloading remote file: base101.avc
Downloading remote file: base102.avc
Downloading remote file: base103.avc
Downloading remote file: base104.avc
Downloading remote file: base105.avc
Downloading remote file: base106.avc
Downloading remote file: base107.avc
Downloading remote file: base108.avc
Downloading remote file: base109.avc
Downloading remote file: base110.avc
Downloading remote file: base111.avc
Downloading remote file: base112.avc
Downloading remote file: base113.avc
Downloading remote file: base114.avc
Downloading remote file: base115.avc
Downloading remote file: base116.avc
Downloading remote file: base117.avc
Downloading remote file: base118.avc
Downloading remote file: base119.avc
Downloading remote file: base120.avc
Downloading remote file: base121.avc
Downloading remote file: base122.avc
Downloading remote file: base123.avc
Downloading remote file: base124.avc
Downloading remote file: base125.avc
Downloading remote file: base126.avc
Downloading remote file: base127.avc
Downloading remote file: base128.avc
Downloading remote file: base129.avc
Downloading remote file: base130.avc
Downloading remote file: base131.avc
Downloading remote file: base132.avc
Downloading remote file: base133.avc
Downloading remote file: base134.avc
Downloading remote file: base135.avc
Downloading remote file: base136.avc
Downloading remote file: base137.avc
Downloading remote file: base138.avc
Downloading remote file: base139.avc
Downloading remote file: base140.avc
Downloading remote file: base141.avc
Downloading remote file: base142.avc
Downloading remote file: base143.avc
Downloading remote file: base144.avc
Downloading remote file: base145.avc
Downloading remote file: base146.avc
Downloading remote file: base147.avc
Downloading remote file: base148.avc
Downloading remote file: base149.avc
Downloading remote file: base150.avc
Downloading remote file: base151.avc
Downloading remote file: base152.avc
Downloading remote file: base153.avc
Downloading remote file: base154.avc
Downloading remote file: base155.avc
Downloading remote file: base156.avc
Downloading remote file: base157.avc
Downloading remote file: base158.avc
Downloading remote file: base159.avc
Downloading remote file: base160.avc
Downloading remote file: base161.avc
Downloading remote file: base162.avc
Downloading remote file: base163.avc
Downloading remote file: base999.avc
Downloading remote file: unp000.avc
Downloading remote file: unp001.avc
Downloading remote file: unp002.avc
Downloading remote file: unp003.avc
Downloading remote file: unp004.avc
Downloading remote file: unp005.avc
Downloading remote file: unp006.avc
Downloading remote file: unp007.avc
Downloading remote file: unp008.avc
Downloading remote file: unp009.avc
Downloading remote file: unp010.avc
Downloading remote file: unp011.avc
Downloading remote file: unp012.avc
Downloading remote file: unp013.avc
Downloading remote file: unp014.avc
Downloading remote file: unp015.avc
Downloading remote file: unp016.avc
Downloading remote file: unp017.avc
Downloading remote file: unp018.avc
Downloading remote file: unp019.avc
Downloading remote file: unp020.avc
Downloading remote file: unp021.avc
Downloading remote file: unp022.avc
Downloading remote file: unp023.avc
Downloading remote file: unp024.avc
Downloading remote file: unp025.avc
Downloading remote file: unp026.avc
Downloading remote file: unp027.avc
Downloading remote file: unp028.avc
Downloading remote file: unp029.avc
Downloading remote file: unp030.avc
Downloading remote file: unp031.avc
Downloading remote file: unp032.avc
Downloading remote file: unp033.avc
Downloading remote file: unp034.avc
Downloading remote file: unp035.avc
Downloading remote file: unp036.avc
Downloading remote file: unp037.avc
Downloading remote file: unp038.avc
Downloading remote file: unp039.avc
Downloading remote file: daily.avc
Downloading remote file: daily-ex.avc
Downloading remote file: urgent.avc
Downloading remote file: mail.avc
Downloading remote file: ext001.avc
Downloading remote file: ext002.avc
Downloading remote file: ext003.avc
Downloading remote file: ext004.avc
Downloading remote file: ext005.avc
Downloading remote file: ext006.avc
Downloading remote file: ext007.avc
Downloading remote file: ext008.avc
Downloading remote file: ext009.avc
Downloading remote file: ext999.avc
Downloading remote file: gen001.avc
Downloading remote file: gen002.avc
Downloading remote file: gen003.avc
Downloading remote file: gen004.avc
Downloading remote file: gen005.avc
Downloading remote file: gen999.avc
Downloading remote file: ca.avc
Downloading remote file: fa.avc
Downloading remote file: eicar.avc
Downloading remote file: verdicts.ini
Downloading remote file: engine.dt
Downloading remote file: engine.cfg
Downloading remote file: avcmhk5.mhk
Downloading remote file: black.lst
Downloading remote file: avp.set
Downloading remote file: avp_ext.set
Downloading remote file: avp_x.set
Downloading remote file: avp.vnd
Downloading remote file: avp.klb
Downloading remote file: soft.ver
Update finished. Ready to scan.
Next
Please select a target to scan:
You can configure the scanning process by
pressing "Scan Settings" button.
Critical Areas
scan critical areas of your hard disks
specified in %windir% and %tmp% system variables
Memory
scan disk modules of running processes
My Computer
scan all your hard and mapped disks
My Email
scan all your hard and mapped disks only for the
following extensions: *.PST; *.MSG; *.OST;
*.MDB; *.DBX; *.EML; *.MBS
Folders...
scan selected folders
A File...
scan a one file
Warning: The Kaspersky Online Scanner may not
run successfully while any other Anti-Virus
software is running. If you have Anti-Virus
software installed, please disable your AV
protection before running the Kaspersky Online
Scanner.
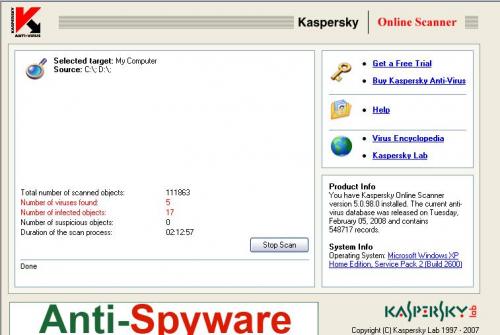
Selected target: My Computer
Source: C:\; D:\;
Report is empty.
Please note: The free Kaspersky Online Scanner
does not provide comprehensive protection and
cannot prevent future infections. It only
detects malware that has already penetrated your
storage devices. We strongly recommend that you
use a fully-functional antivirus solution to
protect your computer at all times.
Please wait, this process may take a long time
depending on the selected target. If you want to
continue browsing, open a new window.
Scan Progress [99%]:
Total number of scanned objects:111863
Number of viruses found:5
Number of infected objects:17
Number of suspicious objects:0
Duration of the scan process:02:12:57
Stop Scan
Get a Free Trial
Buy Kaspersky Anti-Virus
Help
Virus Encyclopedia
Kaspersky Lab
Product Info
You have Kaspersky Online Scanner version 5.0.98.0
installed. The current anti-virus database was
released on Tuesday, February 05, 2008 and
contains 548717 records.
System Info
Operating System: Microsoft Windows XP Home
Edition, Service Pack 2 (Build 2600)Please wait
while the Kaspersky Online Scanner is initializing
and updating...
Copyright © Kaspersky Lab 1997 - 2007
Portions Copyright © Lan Crypto

 This topic is locked
This topic is locked













 Sign In
Sign In Create Account
Create Account

