I am working on a friends Toshiba Satellite R25-S3503. Win XP pro SP2.
I am getting the following error message when booting up on my Windows Desktop
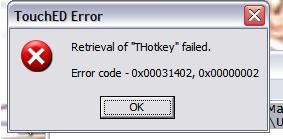
""TouchED Error Retrieval of "THotkey" failed Error Code -0x00031402, 0x00000002""
** SEE JPG Attached **
Before I was getting this message I was getting the ViewPt service error at startup. I was also not able to start or uninstall the software Malwarebytes' Anti-Malware. I found this software very useful in the past. This lappy had AVG AVirus on it. I updated
and ran, finding @ 18 viruses. Clicked to remove. I also was trying to run Disk Defrag & Analyze. It wasn't able to start. I then DL McAfee AVirus from my provider's site. After running a complete scan, this found 19 viruses and many other things. All were either quarantined or removed except one. I was then able to reboot as instructed to remove.
After rebooting I no longer received the ViewPt pop up error message and was receiving the TouchED Error Retrieval of "THotkey" failed Error Code -0x00031402, 0x00000002
error message. After reading your forums I have ran a quick scan w/ Dr. Web Scanner. I didn't get any problems. I am now running a complete scan. On another note.. I have downloaded and installed the latest driver for Hot Keys from Toshiba's website.
Below is the Logs from Malwarebytes:
Malwarebytes' Anti-Malware 1.36
Database version: 1966
Windows 5.1.2600 Service Pack 2
4/11/2009 2:14:39 PM
mbam-log-2009-04-11 (14-14-39).txt
Scan type: Full Scan (C:\|)
Objects scanned: 197809
Time elapsed: 1 hour(s), 19 minute(s), 48 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 6
Registry Values Infected: 2
Registry Data Items Infected: 12
Folders Infected: 3
Files Infected: 12
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{ca6319c0-31b7-401e-a518-a07c3db8f777} (Trojan.BHO.H) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ca6319c0-31b7-401e-a518-a07c3db8f777} (Trojan.BHO.H) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{3aa42713-5c1e-48e2-b432-d8bf420dd31d} (Rogue.Antivirus2008) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{28abc5c0-4fcb-11cf-aax5-81cx1c635612} (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\MalwareRemovalBot (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\UAC (Rootkit.Trace) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MalwareRemovalBot (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\13cfg914-k641-26sf-n31p (Trojan.Agent) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\System (Rootkit.DNSChanger.H) -> Data: kdwwq.exe -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\NameServer (Trojan.DNSChanger) -> Data: 85.255.114.54 85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{390215fd-0dad-4bcf-bc9e-5736b18ef92f}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{ae337415-ea36-42b7-ae28-a387aecfbc22}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters\NameServer (Trojan.DNSChanger) -> Data: 85.255.114.54 85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{390215fd-0dad-4bcf-bc9e-5736b18ef92f}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{ae337415-ea36-42b7-ae28-a387aecfbc22}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Services\Tcpip\Parameters\NameServer (Trojan.DNSChanger) -> Data: 85.255.114.54 85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Services\Tcpip\Parameters\Interfaces\{390215fd-0dad-4bcf-bc9e-5736b18ef92f}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Services\Tcpip\Parameters\Interfaces\{ae337415-ea36-42b7-ae28-a387aecfbc22}\DhcpNameServer (Trojan.DNSChanger) -> Data: 85.255.114.54,85.255.112.26 -> Quarantined and deleted successfully.
Folders Infected:
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\Log (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\Settings (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
Files Infected:
C:\WINDOWS\system32\kdwwq.exe (Rootkit.DNSChanger.H) -> Delete on reboot.
C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\WZSE1.TMP\GoogleAFE.dll (Trojan.BHO.H) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Local Settings\Temp\UACe396.tmp (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\rs.dat (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\Log\2009 Apr 10 - 11_39_38 PM_593.log (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\Log\2009 Apr 10 - 11_44_46 PM_187.log (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\Documents and Settings\Kimberly\Application Data\MalwareRemovalBot\Settings\ScanResults.pie (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\uacinit.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\Tasks\MalwareRemovalBot Scheduled Scan.job (Rogue.MalwareRemovalBot) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\UACrmhxehhb.dat (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\UACvkjkyxni.log (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\UACtlgxvjix.sys (Trojan.Agent) -> Quarantined and deleted successfully.
Anything that will help out is quite helpful..If any of the logs I am posting is endangering myself or my info, please let me know.
FYI.. I am over a 100K files scanned w/ no Infected files.
Tks..
K















 Sign In
Sign In Create Account
Create Account

