Can I start by saying how impressed I am with this resource and thanks in advance for any help. I've already worked through malware and spyware removal guide and it was clear and well written.
Potted history of issue - I'll try to be as thorough as I can:
Googled for "iron horse" (a bicycle brand) a couple of days ago and clicked on "iron horse owners club" or something like that. Computer went crazy with java windows popping up and what not resulting in a fairly quick 'seizure' which if I remember I recovered with Ctrl+Alt+Del. Normally I just browse a few specific websites so navigate there from the address bar which worked fine on restart. However, when googling, the clicked links take me to all manner of random advertising style websites. Some links within 'proper' websites also take me to random pages. At this point I realised something had afflicted my machine. I had a quick chat with the IT guy at work and he recommended malwarebytes so I ran this and I attach the log below (full scan - sorry I now realise this is not ideal for you). This did appear to remove some junk but the problem persisted and following googling (on work PC) I found your website and followed through the removal guide. I have also looked at some other tips and include the outcomes below. Thanks again for any help I may receive.
Actions taken
Checked LAN settings - 'use a proxy server for your LAN' is unchecked
Checked DNS settings - 'Obtain DNS server address automatically' is selected
Checked HOSTS file - Contains only one line: 127.0.0.1 localhost
Checked for TDSSserv.sys file and does not seem to be on my computer
And so to your actions:
Malwarebytes log
Malwarebytes' Anti-Malware 1.46
www.malwarebytes.org
Database version: 4440
Windows 5.1.2600 Service Pack 2
Internet Explorer 7.0.5730.11
17/08/2010 19:45:19
mbam-log-2010-08-17 (19-45-19).txt
Scan type: Full scan (C:\|D:\|)
Objects scanned: 245593
Time elapsed: 1 hour(s), 15 minute(s), 40 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 30
Registry Values Infected: 0
Registry Data Items Infected: 2
Folders Infected: 18
Files Infected: 275
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_CLASSES_ROOT\videoegg.activexloader (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{168dc258-1455-4e61-8590-9dac2f27b675} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{1a8642f1-dc80-4edc-a39d-0fb62a58b455} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{3f91eb90-ef62-44ee-a685-fac29af111cd} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{5c29c7e4-5321-4cad-be2e-877666bed5df} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{83dfb6ee-ab18-41b5-86d4-b544a141d67e} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{88d6cf0e-cf70-4c24-bf6e-e4e414bc649c} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{8f6a82a2-d7b1-443e-bb9f-f7dc887dd618} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{9856e2d8-ffb2-4fe5-8cad-d5ad6a35a804} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{a3d06987-c35e-49e4-8fe2-ac67b9fbfb4c} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{a58c497b-3ee2-45e7-9594-daca6be2a0d0} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ad0a3058-fd49-4f98-a514-fd055201835e} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ad5915ea-b61a-4dba-b5c8-ef4b2df0a3c7} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{af2e62b6-f9e1-4d4f-a10a-9dc8e6dcbcc0} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{af2e62b6-f9e1-4d4f-a10a-9dc8e6dcbcc0} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\{af2e62b6-f9e1-4d4f-a10a-9dc8e6dcbcc0} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{bb187c0d-6f53-4f3e-9590-98fd3a7364a2} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{c5041fd9-4819-4dc4-b20e-c950b5b03d2a} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{d17726cc-d4dd-4c4a-9671-471d56e413b5} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{db8cce99-59c6-4552-8bfc-058feb38d6ce} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{dc3a04ee-cdd7-4407-915c-a5502f97eecd} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{e1a63484-a022-4d42-830a-fbd411514440} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{e282c728-189d-419e-8ee2-1601f4b39ba5} (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\videoegg.activexloader.1 (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{1d4db7d2-6ec9-47a3-bd87-1e41684e07bb} (Adware.MyWebSearch) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\videoegg (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\MozillaPlugins\@videoegg.com/publisher,version=1.5 (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\VideoEgg (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\MozillaPlugins\@videoegg.com/publisher,version=1.5 (Adware.VideoEgg) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\VideoEgg (Adware.VideoEgg) -> Quarantined and deleted successfully.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
C:\Documents and Settings\Tommy\Application Data\VideoEgg (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Loader (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Loader\4665 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\messages (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4665 (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\4665 (Adware.VideoEgg) -> Quarantined and deleted successfully.
Files Infected:
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Loader\4665\npvideoegg-loader.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\updater.exe (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\VideoEggBroker.exe (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\VideoEggBroker.exe.old (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\DataLOCKED (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Uninstall.exe (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\report.log (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\aol_watermark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\audio_combo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\audio_source.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\bebo_tv_watermark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\bebo_tv_watermark_1.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\big_gray_logo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\big_logo_cropped.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\blank_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\button_browse_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\button_browse_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\button_browse_up.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\camcorders_title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\camcorder_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\camcorder_slide copy.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\camcorder_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\corners_bottom_left.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\corners_bottom_left_curve.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\corners_bottom_right.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\corners_top_right.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\done_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dropshadow_bottom_left.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dropshadow_horiz.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dropshadow_vertical.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dropzone.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dv_fast_forward.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dv_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dv_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dv_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\dv_stop.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\email_instructions.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\email_sent.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\email_sent_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\email_sent_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\eraser.CUR (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\eraser_cursor.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\file_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\file_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\help.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_camcorders.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_ff.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_stop.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\icon_webcams.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\loading.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\loading_movie.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\locating.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\logo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\logo_bottom.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\logo_middle.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\logo_top.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\mobile_btn_highlighted copy.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\mobile_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\mobile_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\mobile_slide_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\movie_placeholder.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\ok.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\ok_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\ok_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_fast_forward.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_fast_forward_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_fill.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_rewind_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\player_rewind_to_start.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\playhead.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\powered_by.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\progress.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\refresh_list_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\refresh_list_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\refresh_list_up.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\skin.ver (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\skin.zip (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_capture_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_over_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\start_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\stop_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\stop_capture_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\stop_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\stop_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\stop_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\tab_slide_deselected.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\tape_control.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\upload.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading_fill.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading_high.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading_low.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading_medium.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\uploading_thumbnail.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\upload_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\upload_from.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\upload_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\videoegg-large.ico (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\videoegg-small.ico (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\videoegg.ico (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_gray.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_green.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_high.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_low.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_orange.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_red.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\volume_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\waiting_for_email.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\webcams_title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\webcam_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Data\Resources\gid329\cid1124\bebo03\images\webcam_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Loader\loader.ver (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\publisher.ver (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\avcodec.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\crashRpt.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\FLVEncoder.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\lame_enc.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\LevelMeter.ax (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\libcurlve.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\libpng.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\npvideoegg-publisher.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\VideoEgg_FLVWriter.ax (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\zlib.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\aol_watermark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\audio_combo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\audio_source.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\big_gray_logo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\big_logo_cropped.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\blank_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\button_browse_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\button_browse_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\button_browse_up.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\camcorders_title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\camcorder_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\camcorder_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\corners_bottom_left.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\corners_bottom_left_curve.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\corners_bottom_right.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\corners_top_right.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\done_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dropshadow_bottom_left.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dropshadow_horiz.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dropshadow_vertical.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dropzone.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dv_fast_forward.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dv_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dv_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dv_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\dv_stop.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\email_instructions.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\email_sent.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\email_sent_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\email_sent_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\eraser.CUR (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\eraser_cursor.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\file_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\file_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\help.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_camcorder.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_camcorders.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_camcorder_dark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_camcorder_light.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_ff.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_file_dark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_file_light.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_phone_dark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_phone_light.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_stop.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_webcam.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_webcams.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_webcam_dark.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\icon_webcam_light.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\loading.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\loading_movie.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\locating.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\logo.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\logo_bottom.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\logo_middle.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\logo_top.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\mobile_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\mobile_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\mobile_slide_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\movie_placeholder.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\ok.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\ok_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\ok_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_fast_forward.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_fast_forward_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_fill.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_pause.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_play.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_rewind.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_rewind_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\player_rewind_to_start.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\playhead.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\powered_by.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\progress.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\refresh_list_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\refresh_list_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\refresh_list_up.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\restart.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\restart_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_capture_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_over_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\start_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\stop_capture.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\stop_capture_disabled.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\stop_capture_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\stop_capture_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\stop_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\tab_slide_deselected.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\tape_control.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_camcorder.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_camcorder_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_file.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_file_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_phone.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_phone_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_webcam.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\text_webcam_highlight.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\upload.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading_fill.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading_high.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading_low.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading_medium.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\uploading_thumbnail.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\upload_down.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\upload_from.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\upload_over.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_gray.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_green.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_high.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_low.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_orange.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_red.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\volume_slider.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\waiting_for_email.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\webcams_title.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\webcam_btn_highlighted.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\images\webcam_slide.png (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Publisher\4520\resources\VideoEgg\messages\messages.en-US.bundle (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\updater.ver (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\4665\libcurlve.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Application Data\VideoEgg\Updater\4665\updater.dll (Adware.VideoEgg) -> Quarantined and deleted successfully.
C:\Documents and Settings\Tommy\Local Settings\Application Data\Windows Server\admin.txt (Malware.Trace) -> Quarantined and deleted successfully.
Most recent Malwarebytes log
Malwarebytes' Anti-Malware 1.46
www.malwarebytes.org
Database version: 4440
Windows 5.1.2600 Service Pack 2
Internet Explorer 7.0.5730.11
18/08/2010 19:33:26
mbam-log-2010-08-18 (19-33-26).txt
Scan type: Quick scan
Objects scanned: 142705
Time elapsed: 7 minute(s), 54 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
GMER log
GMER 1.0.15.15281 - http://www.gmer.net
Rootkit scan 2010-08-18 22:35:13
Windows 5.1.2600 Service Pack 2
Running: gmer.exe; Driver: C:\DOCUME~1\Tommy\LOCALS~1\Temp\pxtdipow.sys
---- System - GMER 1.0.15 ----
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateFile [0xA8C5B78A]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateKey [0xA8C5B821]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateProcess [0xA8C5B738]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateProcessEx [0xA8C5B74C]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwDeleteKey [0xA8C5B835]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwDeleteValueKey [0xA8C5B861]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwEnumerateKey [0xA8C5B8CF]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwEnumerateValueKey [0xA8C5B8B9]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwMapViewOfSection [0xA8C5B7CA]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwNotifyChangeKey [0xA8C5B8FB]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwOpenKey [0xA8C5B80D]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwOpenProcess [0xA8C5B710]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwOpenThread [0xA8C5B724]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwProtectVirtualMemory [0xA8C5B79E]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwQueryKey [0xA8C5B937]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwQueryMultipleValueKey [0xA8C5B8A3]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwQueryValueKey [0xA8C5B88D]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwRenameKey [0xA8C5B84B]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwReplaceKey [0xA8C5B923]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwRestoreKey [0xA8C5B90F]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwSetContextThread [0xA8C5B776]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwSetInformationProcess [0xA8C5B762]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwSetValueKey [0xA8C5B877]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwTerminateProcess [0xA8C5B7F9]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwUnloadKey [0xA8C5B8E5]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwUnmapViewOfSection [0xA8C5B7E0]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwYieldExecution [0xA8C5B7B4]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtCreateFile
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtMapViewOfSection
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtOpenProcess
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtOpenThread
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtSetInformationProcess
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwYieldExecution 80504ABC 7 Bytes JMP A8C5B7B8 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!NtCreateFile 80577F76 5 Bytes JMP A8C5B78E \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!NtMapViewOfSection 805B0E3E 7 Bytes JMP A8C5B7CE \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwUnmapViewOfSection 805B1C4C 5 Bytes JMP A8C5B7E4 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwProtectVirtualMemory 805B7222 7 Bytes JMP A8C5B7A2 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!NtOpenProcess 805CA160 5 Bytes JMP A8C5B714 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!NtOpenThread 805CA3EC 5 Bytes JMP A8C5B728 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!NtSetInformationProcess 805CCBAA 5 Bytes JMP A8C5B766 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwCreateProcessEx 805CFE96 7 Bytes JMP A8C5B750 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwCreateProcess 805CFF4C 5 Bytes JMP A8C5B73C \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwSetContextThread 805D0456 5 Bytes JMP A8C5B77A \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwTerminateProcess 805D1686 5 Bytes JMP A8C5B7FD \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwQueryValueKey 80620664 7 Bytes JMP A8C5B891 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwRestoreKey 806209B2 5 Bytes JMP A8C5B913 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwSetValueKey 80620C6A 7 Bytes JMP A8C5B87B \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwUnloadKey 80620F32 7 Bytes JMP A8C5B8E9 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwQueryMultipleValueKey 8062178C 7 Bytes JMP A8C5B8A7 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwRenameKey 80621FE4 7 Bytes JMP A8C5B84F \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwCreateKey 806225BE 5 Bytes JMP A8C5B825 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwDeleteKey 80622A5A 7 Bytes JMP A8C5B839 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwDeleteValueKey 80622C2A 7 Bytes JMP A8C5B865 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwEnumerateKey 80622E0A 7 Bytes JMP A8C5B8D3 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwEnumerateValueKey 80623074 7 Bytes JMP A8C5B8BD \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwOpenKey 80623960 5 Bytes JMP A8C5B811 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwQueryKey 80623CA0 7 Bytes JMP A8C5B93B \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwReplaceKey 806241C6 5 Bytes JMP A8C5B927 \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
PAGE ntkrnlpa.exe!ZwNotifyChangeKey 806242E0 5 Bytes JMP A8C5B8FF \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 014B0FEF
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 014B0065
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 014B0F66
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 014B0040
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 014B0F83
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 014B002F
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 014B0F29
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 014B0F3A
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 014B00AA
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 014B0F07
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 014B0EEC
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 014B0F9E
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 014B0FDE
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateProcessInternalW 7C819527 5 Bytes JMP 00B2874A
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 014B0F4B
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 014B001E
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 014B0FCD
.text C:\WINDOWS\Explorer.EXE[284] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 014B0F18
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 01450FDE
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 0145006F
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 0145002F
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 01450FEF
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 01450FB2
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 01450000
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 01450FC3
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [65, 89]
.text C:\WINDOWS\Explorer.EXE[284] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 0145004A
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 01440066
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!system 77C293C7 5 Bytes JMP 0144004B
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 01440FE5
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!_open 77C2F566 5 Bytes JMP 0144000C
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 0144003A
.text C:\WINDOWS\Explorer.EXE[284] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 0144001D
.text C:\WINDOWS\Explorer.EXE[284] WININET.dll!InternetOpenA 3D953081 5 Bytes JMP 00FF0FEF
.text C:\WINDOWS\Explorer.EXE[284] WININET.dll!InternetOpenW 3D9536B1 5 Bytes JMP 00FF0000
.text C:\WINDOWS\Explorer.EXE[284] WININET.dll!InternetOpenUrlA 3D956F5A 5 Bytes JMP 00FF0FCA
.text C:\WINDOWS\Explorer.EXE[284] WININET.dll!InternetOpenUrlW 3D998439 5 Bytes JMP 00FF0011
.text C:\WINDOWS\Explorer.EXE[284] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 011D0000
.text c:\PROGRA~1\COMMON~1\mcafee\mcproxy\mcproxy.exe[752] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 0041C130 c:\PROGRA~1\COMMON~1\mcafee\mcproxy\mcproxy.exe (McAfee Proxy Service Module/McAfee, Inc.)
.text c:\PROGRA~1\COMMON~1\mcafee\mcproxy\mcproxy.exe[752] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 0041C1B0 c:\PROGRA~1\COMMON~1\mcafee\mcproxy\mcproxy.exe (McAfee Proxy Service Module/McAfee, Inc.)
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00040FEF
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 000400C2
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 000400A7
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 0004008C
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00040FC3
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00040FD4
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00040FA1
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 000400DD
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00040F90
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 0004011F
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00040144
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00040065
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 0004000A
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00040FB2
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00040036
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00040025
.text C:\WINDOWS\system32\services.exe[884] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 0004010E
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00070FDB
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00070073
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 0007002C
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00070011
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00070062
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00070000
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00070051
.text C:\WINDOWS\system32\services.exe[884] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00070FC0
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00060FC3
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!system 77C293C7 5 Bytes JMP 00060FD4
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00060029
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00060FEF
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00060044
.text C:\WINDOWS\system32\services.exe[884] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 0006000C
.text C:\WINDOWS\system32\services.exe[884] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00050000
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00CE0000
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00CE0F80
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00CE0F91
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00CE005F
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00CE004E
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00CE003D
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00CE00AD
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00CE0F65
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00CE00E3
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00CE00C8
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00CE0F2F
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00CE0FB6
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00CE0011
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00CE0090
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00CE0FD1
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00CE002C
.text C:\WINDOWS\system32\lsass.exe[896] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00CE0F54
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00D10036
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00D10FB6
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00D10FDB
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00D10011
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00D10073
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00D10000
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00D10062
.text C:\WINDOWS\system32\lsass.exe[896] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00D10047
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00D0002C
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!system 77C293C7 5 Bytes JMP 00D00011
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00D00000
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00D00FEF
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00D00FA1
.text C:\WINDOWS\system32\lsass.exe[896] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00D00FD2
.text C:\WINDOWS\system32\lsass.exe[896] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00CF0FEF
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00D40000
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00D40F77
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00D40F92
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00D40FAF
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00D4006C
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00D40FCA
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00D40087
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00D40F3F
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00D40F13
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00D40F2E
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00D40F02
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00D4005B
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00D40011
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00D40F5C
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00D40036
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00D40FE5
.text C:\WINDOWS\system32\svchost.exe[1132] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00D400AC
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00D70FC3
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00D70F97
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00D70FD4
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00D70FE5
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00D70054
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00D70000
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00D7002F
.text C:\WINDOWS\system32\svchost.exe[1132] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00D70FA8
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00D60FAD
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!system 77C293C7 5 Bytes JMP 00D60038
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00D60FC8
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00D60FE3
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00D6001D
.text C:\WINDOWS\system32\svchost.exe[1132] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00D6000C
.text C:\WINDOWS\system32\svchost.exe[1132] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00D50000
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00AE0FEF
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00AE0F95
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00AE008A
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00AE006F
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00AE005E
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00AE0039
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00AE0F4E
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00AE0F69
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00AE00D6
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00AE0F3D
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00AE00E7
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00AE0FB2
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00AE0014
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00AE0F84
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00AE0FC3
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00AE0FD4
.text C:\WINDOWS\system32\svchost.exe[1200] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00AE00B1
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00B10FB9
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00B10FA8
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00B1000A
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00B10FDE
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00B10065
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00B10FEF
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00B10040
.text C:\WINDOWS\system32\svchost.exe[1200] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00B1002F
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00B0001E
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!system 77C293C7 5 Bytes JMP 00B00F93
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00B00FB5
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00B00FE3
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00B00FA4
.text C:\WINDOWS\system32\svchost.exe[1200] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00B00FC6
.text C:\WINDOWS\system32\svchost.exe[1200] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00AF0FEF
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 001B0000
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 001B0F9E
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 001B0093
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 001B006C
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 001B0FAF
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 001B0FCA
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 001B0F83
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 001B00D5
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 001B0F68
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 001B00F7
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 001B0F57
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 001B0051
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 001B0011
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 001B00B8
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 001B0036
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 001B0FE5
.text C:\WINDOWS\system32\wuauclt.exe[1264] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 001B00E6
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00290F90
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!system 77C293C7 5 Bytes JMP 00290FA1
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00290FD7
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00290000
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00290FBC
.text C:\WINDOWS\system32\wuauclt.exe[1264] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00290011
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 002A0FEF
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 002A0065
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 002A0036
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 002A001B
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 002A0FB2
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 002A000A
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 002A0FC3
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [4A, 88]
.text C:\WINDOWS\system32\wuauclt.exe[1264] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 002A0FD4
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00C40FEF
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00C4004A
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00C40039
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00C40F6B
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00C40F86
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00C40FB2
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00C40082
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00C40F3A
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00C400B8
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00C40F29
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00C40F04
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00C40F97
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00C40FDE
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00C4005B
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00C4001E
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00C40FC3
.text C:\WINDOWS\System32\svchost.exe[1344] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00C4009D
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 01F3001B
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 01F30058
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 01F30FCA
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 01F30FEF
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 01F30047
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 01F3000A
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 01F30FA5
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [13, 8A]
.text C:\WINDOWS\System32\svchost.exe[1344] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 01F3002C
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 01F20FB9
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!system 77C293C7 5 Bytes JMP 01F20044
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 01F20029
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!_open 77C2F566 5 Bytes JMP 01F20FEF
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 01F20FD4
.text C:\WINDOWS\System32\svchost.exe[1344] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 01F20018
.text C:\WINDOWS\System32\svchost.exe[1344] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 01F10FE5
.text C:\WINDOWS\System32\svchost.exe[1344] WININET.dll!InternetOpenA 3D953081 5 Bytes JMP 00C70000
.text C:\WINDOWS\System32\svchost.exe[1344] WININET.dll!InternetOpenW 3D9536B1 5 Bytes JMP 00C70011
.text C:\WINDOWS\System32\svchost.exe[1344] WININET.dll!InternetOpenUrlA 3D956F5A 5 Bytes JMP 00C7002C
.text C:\WINDOWS\System32\svchost.exe[1344] WININET.dll!InternetOpenUrlW 3D998439 1 Byte [E9]
.text C:\WINDOWS\System32\svchost.exe[1344] WININET.dll!InternetOpenUrlW 3D998439 5 Bytes JMP 00C7003D
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00640FEF
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00640F65
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00640F76
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00640F91
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00640FA2
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 0064003D
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00640F34
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00640086
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 006400BC
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 006400AB
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 006400D7
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 0064004E
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 0064000A
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00640075
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 0064002C
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 0064001B
.text C:\WINDOWS\system32\svchost.exe[1384] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00640F23
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 0063001E
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00630F7C
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00630FCD
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00630FDE
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 0063002F
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00630FEF
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 00630F8D
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [83, 88]
.text C:\WINDOWS\system32\svchost.exe[1384] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00630FA8
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00620025
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!system 77C293C7 5 Bytes JMP 00620F9A
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00620FC6
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00620FE3
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00620FB5
.text C:\WINDOWS\system32\svchost.exe[1384] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00620000
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 007A0FE5
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 007A0F72
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 007A005D
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 007A0040
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 007A0F83
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 007A0FA8
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 007A0F57
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 007A0093
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 007A0F10
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 007A0F2B
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 007A00C4
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 007A0025
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 007A0FCA
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 007A0082
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 007A000A
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 007A0FB9
.text C:\WINDOWS\system32\svchost.exe[1520] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 007A0F3C
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 0079001B
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00790FA5
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00790FCA
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00790FDB
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00790062
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00790000
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00790047
.text C:\WINDOWS\system32\svchost.exe[1520] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00790036
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00780047
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!system 77C293C7 5 Bytes JMP 00780FBC
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00780022
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00780FEF
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00780FCD
.text C:\WINDOWS\system32\svchost.exe[1520] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00780FDE
.text C:\WINDOWS\system32\svchost.exe[1520] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 0077000A
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00720000
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00720093
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00720078
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00720F9E
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00720FB9
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00720040
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 007200D0
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 007200BF
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 0072010D
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 007200FC
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00720F59
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 0072005B
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00720FEF
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 007200AE
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00720FD4
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00720025
.text C:\WINDOWS\system32\svchost.exe[1660] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 007200E1
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00710FD4
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00710051
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00710025
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00710FEF
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00710040
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 0071000A
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 00710F9E
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [91, 88]
.text C:\WINDOWS\system32\svchost.exe[1660] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00710FB9
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00700FA6
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!system 77C293C7 5 Bytes JMP 00700031
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00700FD2
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00700000
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00700FC1
.text C:\WINDOWS\system32\svchost.exe[1660] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00700FE3
.text C:\WINDOWS\system32\svchost.exe[1660] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 006F0000
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 008F0FEF
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 008F0F70
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 008F0F8B
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 008F0F9C
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 008F005B
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 008F0040
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 008F00B8
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 008F0091
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 008F0F29
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 008F0F3A
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 008F00E7
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 008F0FC3
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 008F0FDE
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 008F0080
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 008F002F
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 008F001E
.text C:\WINDOWS\system32\svchost.exe[1944] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 008F0F55
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00650FB9
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00650F8D
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00650000
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00650FD4
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00650FA8
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00650FEF
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00650040
.text C:\WINDOWS\system32\svchost.exe[1944] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 0065002F
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00640042
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!system 77C293C7 5 Bytes JMP 00640FB7
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 0064001D
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00640000
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00640FC8
.text C:\WINDOWS\system32\svchost.exe[1944] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00640FE3
.text C:\WINDOWS\system32\svchost.exe[1944] WININET.dll!InternetOpenA 3D953081 5 Bytes JMP 00620000
.text C:\WINDOWS\system32\svchost.exe[1944] WININET.dll!InternetOpenW 3D9536B1 5 Bytes JMP 00620011
.text C:\WINDOWS\system32\svchost.exe[1944] WININET.dll!InternetOpenUrlA 3D956F5A 5 Bytes JMP 00620FDB
.text C:\WINDOWS\system32\svchost.exe[1944] WININET.dll!InternetOpenUrlW 3D998439 5 Bytes JMP 00620FB6
.text C:\WINDOWS\system32\svchost.exe[1944] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00630FEF
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 008F0000
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 008F0FA5
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 008F009A
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 008F0FC0
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 008F0FD1
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 008F0058
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 008F00C6
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 008F0F8A
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 008F0F4F
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 008F00E8
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 008F0F34
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 008F0069
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 008F0011
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 008F00B5
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 008F0047
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 008F002C
.text C:\WINDOWS\system32\svchost.exe[2124] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 008F00D7
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 008E0FDB
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 008E0FA8
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 008E002C
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 008E001B
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 008E0065
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 008E0000
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 2 Bytes JMP 008E0FB9
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegCreateKeyW + 3 77DFBA40 2 Bytes [AE, 88]
.text C:\WINDOWS\system32\svchost.exe[2124] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 008E0FCA
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 008D0038
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!system 77C293C7 5 Bytes JMP 008D0FAD
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 008D001D
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!_open 77C2F566 5 Bytes JMP 008D0FE3
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 008D0FC8
.text C:\WINDOWS\system32\svchost.exe[2124] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 008D0000
.text C:\WINDOWS\system32\svchost.exe[2124] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 008C0000
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00C20FE5
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00C20F52
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00C20F6D
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00C20F94
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00C20051
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00C20025
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00C20F41
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00C20089
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00C200C9
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00C20F30
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00C200E4
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00C20036
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00C20FD4
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00C2006C
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00C20FB9
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00C2000A
.text C:\WINDOWS\system32\dllhost.exe[2212] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00C200A4
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00C00FBC
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!system 77C293C7 5 Bytes JMP 00C00FCD
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00C00029
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00C00FEF
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00C00FDE
.text C:\WINDOWS\system32\dllhost.exe[2212] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00C0000C
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00C10036
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00C10FAF
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00C10025
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00C1000A
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00C1006C
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00C10FEF
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00C10051
.text C:\WINDOWS\system32\dllhost.exe[2212] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00C10FCA
.text C:\WINDOWS\system32\dllhost.exe[2212] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00BF0000
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 008A0FEF
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 008A0F76
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 008A0075
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 008A0058
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 008A0047
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 008A0036
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 008A00A3
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 008A0092
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 008A0F25
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 008A00BE
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 008A0F0A
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 008A0FA5
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 008A000A
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 008A0F65
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 008A0FCA
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 008A001B
.text C:\WINDOWS\system32\svchost.exe[2248] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 008A0F40
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 0089003D
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 0089007A
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 0089002C
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 0089001B
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 0089005F
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00890000
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 0089004E
.text C:\WINDOWS\system32\svchost.exe[2248] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00890FD1
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00880FAD
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!system 77C293C7 5 Bytes JMP 00880038
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00880027
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00880FEF
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00880FC8
.text C:\WINDOWS\system32\svchost.exe[2248] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 0088000C
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 001A0000
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 001A006F
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 001A0F84
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 001A005E
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 001A0FAB
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 001A0FCD
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 001A00A7
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 001A0F5F
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 001A00E4
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 001A00D3
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 001A0F26
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 001A0FBC
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 001A001B
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 001A0080
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 001A0FDE
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 001A0FEF
.text C:\WINDOWS\System32\svchost.exe[2804] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 001A00B8
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00280025
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00280091
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00280FD4
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 0028000A
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00280080
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00280FEF
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 0028005B
.text C:\WINDOWS\System32\svchost.exe[2804] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 0028004A
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 003D0053
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!system 77C293C7 5 Bytes JMP 003D0038
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 003D000C
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!_open 77C2F566 5 Bytes JMP 003D0FEF
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 003D001D
.text C:\WINDOWS\System32\svchost.exe[2804] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 003D0FD2
.text C:\WINDOWS\System32\svchost.exe[2804] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 006D0FEF
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 0027000A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00270F92
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 0027007D
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 0027006C
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00270FB9
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 0027004A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00270F3F
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00270F5A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00270F1D
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00270F2E
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00270F0C
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 0027005B
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00270FEF
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateProcessInternalW 7C819527 5 Bytes JMP 0015775D
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00270F77
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 0027002F
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00270FD4
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 002700A2
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 0035000A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00350047
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00350FB9
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00350FDE
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00350F8A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00350FEF
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00350036
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 0035001B
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!DialogBoxParamW 7E42555F 5 Bytes JMP 3E1DF4B9 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!DialogBoxIndirectParamW 7E432032 5 Bytes JMP 3E35203E C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!MessageBoxIndirectA 7E43A04A 5 Bytes JMP 3E351FBF C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!DialogBoxParamA 7E43B10C 5 Bytes JMP 3E352003 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!MessageBoxExW 7E4505D8 5 Bytes JMP 3E351F4B C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!MessageBoxExA 7E4505FC 5 Bytes JMP 3E351F85 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!DialogBoxIndirectParamA 7E456B50 5 Bytes JMP 3E352079 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] USER32.dll!MessageBoxIndirectW 7E4662AB 5 Bytes JMP 3E20176A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00360038
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!system 77C293C7 5 Bytes JMP 00360FAD
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 0036000C
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00360FEF
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00360027
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00360FDE
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ole32.dll!OleLoadFromStream 7752A257 5 Bytes JMP 3E35223B C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!socket 71AB3B91 5 Bytes JMP 00A00FE5
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!send 71AB428A 5 Bytes JMP 0015634D
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!WSARecv 71AB4318 5 Bytes JMP 00156511
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!recv 71AB615A 5 Bytes JMP 001563C0
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!WSASend 71AB6233 5 Bytes JMP 00156477
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] ws2_32.dll!closesocket 71AB9639 5 Bytes JMP 0015660B
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] Wininet.dll!InternetOpenA 3D953081 5 Bytes JMP 00DD0FEF
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] Wininet.dll!InternetOpenW 3D9536B1 5 Bytes JMP 00DD000A
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] Wininet.dll!InternetOpenUrlA 3D956F5A 5 Bytes JMP 00DD001B
.text C:\Program Files\Internet Explorer\iexplore.exe[3724] Wininet.dll!InternetOpenUrlW 3D998439 5 Bytes JMP 00DD0FCA
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateFileA 7C801A24 5 Bytes JMP 00F80000
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!VirtualProtectEx 7C801A5D 5 Bytes JMP 00F80F52
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!VirtualProtect 7C801AD0 5 Bytes JMP 00F80F63
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!LoadLibraryExW 7C801AF1 5 Bytes JMP 00F80F7E
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!LoadLibraryExA 7C801D4F 5 Bytes JMP 00F80FA5
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!LoadLibraryA 7C801D77 5 Bytes JMP 00F80FC0
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!GetStartupInfoW 7C801E50 5 Bytes JMP 00F80086
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!GetStartupInfoA 7C801EEE 5 Bytes JMP 00F80075
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateProcessW 7C802332 5 Bytes JMP 00F800BC
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateProcessA 7C802367 5 Bytes JMP 00F800A1
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!GetProcAddress 7C80ADB0 5 Bytes JMP 00F80F08
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!LoadLibraryW 7C80AE5B 5 Bytes JMP 00F80047
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateFileW 7C810770 5 Bytes JMP 00F80011
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreatePipe 7C81E0D7 5 Bytes JMP 00F80058
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateNamedPipeW 7C82F0EF 5 Bytes JMP 00F80036
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!CreateNamedPipeA 7C85FE94 5 Bytes JMP 00F80FE5
.text C:\Program Files\Messenger\msmsgs.exe[3820] kernel32.dll!WinExec 7C86158D 5 Bytes JMP 00F80F23
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!_wsystem 77C2931E 5 Bytes JMP 00F60053
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!system 77C293C7 5 Bytes JMP 00F60038
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!_creat 77C2D40F 5 Bytes JMP 00F6001D
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!_open 77C2F566 5 Bytes JMP 00F60000
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!_wcreat 77C2FC9B 5 Bytes JMP 00F60FD2
.text C:\Program Files\Messenger\msmsgs.exe[3820] msvcrt.dll!_wopen 77C30055 5 Bytes JMP 00F60FEF
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegOpenKeyExW 77DD6AAF 5 Bytes JMP 00F70033
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegCreateKeyExW 77DD776C 5 Bytes JMP 00F7005F
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegOpenKeyExA 77DD7852 5 Bytes JMP 00F70022
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegOpenKeyW 77DD7946 5 Bytes JMP 00F70011
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegCreateKeyExA 77DDE9D4 5 Bytes JMP 00F70F98
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegOpenKeyA 77DDEFA8 5 Bytes JMP 00F70000
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegCreateKeyW 77DFBA3D 5 Bytes JMP 00F70044
.text C:\Program Files\Messenger\msmsgs.exe[3820] ADVAPI32.dll!RegCreateKeyA 77DFBCDB 5 Bytes JMP 00F70FC7
.text C:\Program Files\Messenger\msmsgs.exe[3820] WS2_32.dll!socket 71AB3B91 5 Bytes JMP 00F50FEF
.text C:\Program Files\Messenger\msmsgs.exe[3820] WININET.dll!InternetOpenA 3D953081 5 Bytes JMP 00F40FEF
.text C:\Program Files\Messenger\msmsgs.exe[3820] WININET.dll!InternetOpenW 3D9536B1 5 Bytes JMP 00F4000A
.text C:\Program Files\Messenger\msmsgs.exe[3820] WININET.dll!InternetOpenUrlA 3D956F5A 5 Bytes JMP 00F40FD4
.text C:\Program Files\Messenger\msmsgs.exe[3820] WININET.dll!InternetOpenUrlW 3D998439 5 Bytes JMP 00F4001B
---- Devices - GMER 1.0.15 ----
AttachedDevice \FileSystem\Ntfs \Ntfs mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
AttachedDevice \Driver\Tcpip \Device\Ip Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \Driver\Tcpip \Device\Tcp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \Driver\Tcpip \Device\Udp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \Driver\Tcpip \Device\RawIp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \FileSystem\Fastfat \Fat mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
Device \FileSystem\Cdfs \Cdfs DLAIFS_M.SYS (Drive Letter Access Component/Sonic Solutions)
---- EOF - GMER 1.0.15 ----
OTL log
OTL logfile created on: 18/08/2010 22:38:37 - Run 1
OTL by OldTimer - Version 3.2.10.0 Folder = C:\Documents and Settings\Tommy\Desktop
Windows XP Media Center Edition Service Pack 2 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 7.0.5730.11)
Locale: 00000809 | Country: United Kingdom | Language: ENG | Date Format: dd/MM/yyyy
2.00 Gb Total Physical Memory | 1.00 Gb Available Physical Memory | 73.00% Memory free
3.00 Gb Paging File | 2.00 Gb Available in Paging File | 83.00% Paging File free
Paging file location(s): C:\pagefile.sys 756 1512 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 107.09 Gb Total Space | 34.24 Gb Free Space | 31.97% Space Free | Partition Type: NTFS
Drive D: | 37.24 Gb Total Space | 36.86 Gb Free Space | 98.98% Space Free | Partition Type: NTFS
E: Drive not present or media not loaded
F: Drive not present or media not loaded
G: Drive not present or media not loaded
H: Drive not present or media not loaded
I: Drive not present or media not loaded
Drive K: | 964.54 Mb Total Space | 951.22 Mb Free Space | 98.62% Space Free | Partition Type: FAT32
Computer Name: TOM
Current User Name: Tommy
Logged in as Administrator.
Current Boot Mode: Normal
Scan Mode: Current user
Company Name Whitelist: On
Skip Microsoft Files: On
File Age = 90 Days
Output = Standard
Quick Scan
========== Processes (SafeList) ==========
PRC - [2010/08/18 22:36:51 | 000,575,488 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\OTL.exe
PRC - [2010/06/10 06:58:32 | 000,865,832 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\MSC\mcmscsvc.exe
PRC - [2009/10/29 07:54:44 | 001,218,008 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee.com\Agent\mcagent.exe
PRC - [2009/10/27 12:19:46 | 000,895,696 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\MPF\MpfSrv.exe
PRC - [2009/10/11 05:17:45 | 000,386,872 | ---- | M] (Sun Microsystems, Inc.) -- C:\Program Files\Java\jre6\bin\jucheck.exe
PRC - [2009/09/16 10:22:08 | 000,144,704 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\VirusScan\Mcshield.exe
PRC - [2009/09/16 09:28:38 | 000,606,736 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\VirusScan\mcsysmon.exe
PRC - [2009/09/06 07:06:20 | 000,169,312 | ---- | M] (Adobe Systems Incorporated) -- C:\Program Files\Adobe\Elements Organizer 8.0\PhotoshopElementsFileAgent.exe
PRC - [2009/07/08 14:48:48 | 000,026,640 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\MSK\msksrver.exe
PRC - [2009/07/08 11:54:34 | 000,359,952 | ---- | M] (McAfee, Inc.) -- c:\Program Files\Common Files\McAfee\McProxy\McProxy.exe
PRC - [2009/07/07 19:10:02 | 002,482,848 | ---- | M] (McAfee, Inc.) -- c:\Program Files\Common Files\McAfee\MNA\McNASvc.exe
PRC - [2009/07/07 17:45:22 | 000,436,752 | ---- | M] (McAfee, Inc.) -- C:\Program Files\Common Files\McAfee\MSC\McUICnt.exe
PRC - [2009/05/07 23:30:22 | 000,192,128 | ---- | M] (McAfee, Inc.) -- C:\Program Files\McAfee\MSM\McSmtFwk.exe
PRC - [2009/02/11 11:06:36 | 000,210,216 | ---- | M] () -- C:\Program Files\McAfee\SiteAdvisor\McSACore.exe
PRC - [2007/06/13 11:23:07 | 001,033,216 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\explorer.exe
PRC - [2006/10/18 04:33:29 | 000,026,112 | ---- | M] (RealNetworks, Inc.) -- C:\Program Files\Real\RealPlayer\realplay.exe
PRC - [2006/09/11 05:40:32 | 000,218,032 | ---- | M] (Macrovision Corporation) -- C:\Program Files\Common Files\InstallShield\UpdateService\ISUSPM.exe
PRC - [2006/01/25 15:49:02 | 000,884,840 | ---- | M] (NETGEAR) -- C:\Program Files\NETGEAR\WG111T\wlan111t.exe
PRC - [2005/10/05 03:12:00 | 000,094,208 | ---- | M] () -- C:\Program Files\Dell\Media Experience\DMXLauncher.exe
PRC - [2005/09/08 05:20:00 | 000,122,940 | ---- | M] (Sonic Solutions) -- C:\WINDOWS\system32\DLA\DLACTRLW.EXE
========== Modules (SafeList) ==========
MOD - [2010/08/18 22:36:51 | 000,575,488 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\OTL.exe
MOD - [2009/02/11 11:06:38 | 000,014,032 | ---- | M] () -- C:\Program Files\McAfee\SiteAdvisor\sahook.dll
MOD - [2006/08/25 16:45:55 | 001,054,208 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.2982_x-ww_ac3f9c03\comctl32.dll
MOD - [2004/08/10 05:00:00 | 000,102,400 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\system32\msscript.ocx
========== Win32 Services (SafeList) ==========
SRV - File not found [Auto | Stopped] -- C:\WINDOWS\System32\HPZipm12.dll -- (Pml Driver HPZ12)
SRV - File not found [Auto | Stopped] -- C:\WINDOWS\System32\HPZinw12.dll -- (Net Driver HPZ12)
SRV - File not found [Disabled | Stopped] -- C:\WINDOWS\System32\hidserv.dll -- (HidServ)
SRV - [2010/06/10 06:58:32 | 000,865,832 | ---- | M] (McAfee, Inc.) [Auto | Running] -- C:\Program Files\McAfee\MSC\mcmscsvc.exe -- (mcmscsvc)
SRV - [2010/01/06 22:56:05 | 000,867,080 | ---- | M] (Acresso Software Inc.) [On_Demand | Stopped] -- C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe -- (FLEXnet Licensing Service)
SRV - [2009/10/27 12:19:46 | 000,895,696 | ---- | M] (McAfee, Inc.) [Auto | Running] -- C:\Program Files\McAfee\MPF\MPFSrv.exe -- (MpfService)
SRV - [2009/09/16 11:23:32 | 000,365,072 | ---- | M] (McAfee, Inc.) [On_Demand | Stopped] -- C:\Program Files\McAfee\VirusScan\mcods.exe -- (McODS)
SRV - [2009/09/16 10:22:08 | 000,144,704 | ---- | M] (McAfee, Inc.) [Unknown | Running] -- C:\Program Files\McAfee\VirusScan\Mcshield.exe -- (McShield)
SRV - [2009/09/16 09:28:38 | 000,606,736 | ---- | M] (McAfee, Inc.) [On_Demand | Running] -- C:\Program Files\McAfee\VirusScan\mcsysmon.exe -- (McSysmon)
SRV - [2009/09/06 07:06:20 | 000,169,312 | ---- | M] (Adobe Systems Incorporated) [Auto | Running] -- C:\Program Files\Adobe\Elements Organizer 8.0\PhotoshopElementsFileAgent.exe -- (AdobeActiveFileMonitor8.0)
SRV - [2009/07/08 14:48:48 | 000,026,640 | ---- | M] (McAfee, Inc.) [Auto | Running] -- C:\Program Files\McAfee\MSK\MskSrver.exe -- (MSK80Service)
SRV - [2009/07/08 11:54:34 | 000,359,952 | ---- | M] (McAfee, Inc.) [Auto | Running] -- c:\Program Files\Common Files\McAfee\McProxy\McProxy.exe -- (McProxy)
SRV - [2009/07/07 19:10:02 | 002,482,848 | ---- | M] (McAfee, Inc.) [Auto | Running] -- c:\Program Files\Common Files\McAfee\MNA\McNASvc.exe -- (McNASvc)
SRV - [2009/02/11 11:06:36 | 000,210,216 | ---- | M] () [Auto | Running] -- C:\Program Files\McAfee\SiteAdvisor\McSACore.exe -- (McAfee SiteAdvisor Service)
SRV - [2008/08/29 10:00:30 | 000,033,752 | ---- | M] (NOS Microsystems Ltd.) [On_Demand | Stopped] -- C:\Program Files\NOS\bin\getPlus_HelperSvc.exe -- (getPlus® Helper) getPlus®
SRV - [2007/03/26 14:06:24 | 000,292,864 | ---- | M] (Nokia.) [On_Demand | Stopped] -- C:\Program Files\PC Connectivity Solution\ServiceLayer.exe -- (ServiceLayer)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\System32\DRIVERS\wanatw4.sys -- (wanatw) WAN Miniport (ATW)
DRV - [2010/07/15 15:18:22 | 000,120,136 | ---- | M] (McAfee, Inc.) [Kernel | System | Running] -- C:\WINDOWS\system32\drivers\Mpfp.sys -- (MPFP)
DRV - [2009/09/16 10:22:48 | 000,214,664 | ---- | M] (McAfee, Inc.) [Kernel | System | Running] -- C:\WINDOWS\system32\drivers\mfehidk.sys -- (mfehidk)
DRV - [2009/09/16 10:22:48 | 000,079,816 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\mfeavfk.sys -- (mfeavfk)
DRV - [2009/09/16 10:22:48 | 000,040,552 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\mfesmfk.sys -- (mfesmfk)
DRV - [2009/09/16 10:22:48 | 000,035,272 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\mfebopk.sys -- (mfebopk)
DRV - [2009/09/16 10:22:14 | 000,034,248 | ---- | M] (McAfee, Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\mferkdk.sys -- (mferkdk)
DRV - [2007/02/22 11:15:56 | 000,137,216 | ---- | M] (Nokia) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\nmwcd.sys -- (nmwcd)
DRV - [2007/02/22 11:15:14 | 000,012,288 | ---- | M] (Nokia) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\nmwcdcm.sys -- (nmwcdcm)
DRV - [2007/02/22 11:15:14 | 000,012,288 | ---- | M] (Nokia) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\nmwcdcj.sys -- (nmwcdcj)
DRV - [2007/02/22 11:15:14 | 000,008,320 | ---- | M] (Nokia) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\nmwcdc.sys -- (nmwcdc)
DRV - [2006/10/18 04:33:32 | 000,008,552 | ---- | M] (Windows ® 2000 DDK provider) [Kernel | Auto | Running] -- C:\WINDOWS\System32\drivers\asctrm.sys -- (ASCTRM)
DRV - [2006/02/10 11:19:12 | 001,107,224 | ---- | M] (SigmaTel, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\sthda.sys -- (STHDA)
DRV - [2006/01/10 12:07:58 | 000,004,864 | ---- | M] (GTek Technologies Ltd.) [Kernel | On_Demand | Stopped] -- C:\Program Files\Dell Support\GTAction\triggers\DSproct.sys -- (DSproct)
DRV - [2005/09/12 03:30:00 | 000,089,264 | ---- | M] (Sonic Solutions) [Kernel | Boot | Running] -- C:\WINDOWS\System32\Drivers\DRVMCDB.SYS -- (DRVMCDB)
DRV - [2005/09/08 05:20:00 | 000,094,332 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLAUDFAM.SYS -- (DLAUDFAM)
DRV - [2005/09/08 05:20:00 | 000,087,036 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLAUDF_M.SYS -- (DLAUDF_M)
DRV - [2005/09/08 05:20:00 | 000,086,524 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLAIFS_M.SYS -- (DLAIFS_M)
DRV - [2005/09/08 05:20:00 | 000,025,628 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLABOIOM.SYS -- (DLABOIOM)
DRV - [2005/09/08 05:20:00 | 000,014,684 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLAOPIOM.SYS -- (DLAOPIOM)
DRV - [2005/09/08 05:20:00 | 000,006,364 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLAPoolM.SYS -- (DLAPoolM)
DRV - [2005/09/08 05:20:00 | 000,002,496 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\DLA\DLADResN.SYS -- (DLADResN)
DRV - [2005/09/05 11:21:06 | 000,362,944 | ---- | M] (NETGEAR, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\WG11TND5.sys -- (AR5523)
DRV - [2005/08/25 12:16:52 | 000,005,628 | ---- | M] (Sonic Solutions) [File_System | System | Running] -- C:\WINDOWS\system32\drivers\DLACDBHM.SYS -- (DLACDBHM)
DRV - [2005/08/25 12:16:16 | 000,022,684 | ---- | M] (Sonic Solutions) [File_System | System | Running] -- C:\WINDOWS\system32\drivers\DLARTL_N.SYS -- (DLARTL_N)
DRV - [2005/08/12 05:20:00 | 000,040,544 | ---- | M] (Sonic Solutions) [File_System | Auto | Running] -- C:\WINDOWS\system32\drivers\DRVNDDM.SYS -- (DRVNDDM)
DRV - [2004/08/12 17:45:54 | 000,137,728 | ---- | M] (Windows ® Server 2003 DDK provider) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\Hdaudbus.sys -- (HDAudBus)
DRV - [2004/08/03 23:07:44 | 000,043,008 | ---- | M] (Advanced Micro Devices, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\amdagp.sys -- (amdagp)
DRV - [2004/08/03 23:07:44 | 000,041,088 | ---- | M] (Silicon Integrated Systems Corporation) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\sisagp.sys -- (sisagp)
DRV - [2004/08/03 22:29:56 | 001,897,408 | ---- | M] (NVIDIA Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\nv4_mini.sys -- (nv)
DRV - [2003/07/24 12:10:34 | 000,017,149 | ---- | M] (Printing Communications Assoc., Inc. (PCAUSA)) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\DNINDIS5.sys -- (DNINDIS5)
DRV - [2002/10/01 10:22:32 | 000,009,856 | ---- | M] (Padus, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\system32\drivers\pfc.sys -- (pfc)
DRV - [2001/08/17 14:07:44 | 000,019,072 | ---- | M] (Adaptec, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\sparrow.sys -- (Sparrow)
DRV - [2001/08/17 14:07:42 | 000,030,688 | ---- | M] (LSI Logic) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\sym_u3.sys -- (sym_u3)
DRV - [2001/08/17 14:07:40 | 000,028,384 | ---- | M] (LSI Logic) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\sym_hi.sys -- (sym_hi)
DRV - [2001/08/17 14:07:36 | 000,032,640 | ---- | M] (LSI Logic) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\symc8xx.sys -- (symc8xx)
DRV - [2001/08/17 14:07:34 | 000,016,256 | ---- | M] (Symbios Logic Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\symc810.sys -- (symc810)
DRV - [2001/08/17 13:52:22 | 000,036,736 | ---- | M] (Promise Technology, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\ultra.sys -- (ultra)
DRV - [2001/08/17 13:52:20 | 000,045,312 | ---- | M] (QLogic Corporation) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\ql12160.sys -- (ql12160)
DRV - [2001/08/17 13:52:20 | 000,040,320 | ---- | M] (QLogic Corporation) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\ql1080.sys -- (ql1080)
DRV - [2001/08/17 13:52:18 | 000,049,024 | ---- | M] (QLogic Corporation) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\ql1280.sys -- (ql1280)
DRV - [2001/08/17 13:52:16 | 000,179,584 | ---- | M] (Mylex Corporation) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\dac2w2k.sys -- (dac2w2k)
DRV - [2001/08/17 13:52:12 | 000,017,280 | ---- | M] (American Megatrends Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\mraid35x.sys -- (mraid35x)
DRV - [2001/08/17 13:52:00 | 000,026,496 | ---- | M] (Advanced System Products, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\asc.sys -- (asc)
DRV - [2001/08/17 13:51:58 | 000,014,848 | ---- | M] (Advanced System Products, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\asc3550.sys -- (asc3550)
DRV - [2001/08/17 13:51:56 | 000,005,248 | ---- | M] (Acer Laboratories Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\aliide.sys -- (AliIde)
DRV - [2001/08/17 13:51:54 | 000,006,656 | ---- | M] (CMD Technology, Inc.) [Kernel | Disabled | Stopped] -- C:\WINDOWS\system32\DRIVERS\cmdide.sys -- (CmdIde)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Local Page = %SystemRoot%\system32\blank.htm
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,Default_Page_URL = www.google.co.uk/ig/dell?hl=en&client=dell-usuk&channel=uk&ibd=6061018
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,Default_Search_URL = http://www.google.com/ie
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,SearchAssistant = http://www.google.com/ie
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,Start Page = www.google.co.uk/ig/dell?hl=en&client=dell-usuk&channel=uk&ibd=6061018
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = www.google.co.uk/ig/dell?hl=en&client=dell-usuk&channel=uk&ibd=6061018
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Search Page = http://www.google.com
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,SearchMigratedDefaultName = Google
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,SearchMigratedDefaultURL = http://www.google.co...ie=utf8&oe=utf8
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.google.co.uk/
IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Search,SearchAssistant = http://www.google.com/ie
IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
FF - HKLM\software\mozilla\Firefox\Extensions\\{B7082FAA-CB62-4872-9106-E42DD88EDE45}: C:\Program Files\McAfee\SiteAdvisor [2010/03/06 19:11:43 | 000,000,000 | ---D | M]
O1 HOSTS File: ([2004/08/10 05:00:00 | 000,000,734 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (HP Print Enhancer) - {0347C33E-8762-4905-BF09-768834316C61} - C:\Program Files\HP\Digital Imaging\Smart Web Printing\hpswp_printenhancer.dll (Hewlett-Packard Co.)
O2 - BHO: (Adobe PDF Reader Link Helper) - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll (Adobe Systems Incorporated)
O2 - BHO: (McAfee Phishing Filter) - {27B4851A-3207-45A2-B947-BE8AFE6163AB} - c:\Program Files\McAfee\MSK\mskapbho.dll ()
O2 - BHO: (DriveLetterAccess) - {5CA3D70E-1895-11CF-8E15-001234567890} - C:\WINDOWS\system32\DLA\DLASHX_W.DLL (Sonic Solutions)
O2 - BHO: (scriptproxy) - {7DB2D5A0-7241-4E79-B68D-6309F01C5231} - C:\Program Files\McAfee\VirusScan\scriptsn.dll (McAfee, Inc.)
O2 - BHO: (McAfee SiteAdvisor BHO) - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - c:\Program Files\McAfee\SiteAdvisor\McIEPlg.dll ()
O2 - BHO: (CBrowserHelperObject Object) - {CA6319C0-31B7-401E-A518-A07C3DB8F777} - C:\Program Files\BAE\BAE.dll (Dell Inc.)
O2 - BHO: (HP Smart BHO Class) - {FFFFFFFF-CF4E-4F2B-BDC2-0E72E116A856} - C:\Program Files\HP\Digital Imaging\Smart Web Printing\hpswp_BHO.dll (Hewlett-Packard Co.)
O3 - HKLM\..\Toolbar: (McAfee SiteAdvisor Toolbar) - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - c:\Program Files\McAfee\SiteAdvisor\McIEPlg.dll ()
O4 - HKLM..\Run: [] File not found
O4 - HKLM..\Run: [DLA] C:\WINDOWS\system32\DLA\DLACTRLW.EXE (Sonic Solutions)
O4 - HKLM..\Run: [DMXLauncher] C:\Program Files\Dell\Media Experience\DMXLauncher.exe ()
O4 - HKLM..\Run: [HitmanPro35] C:\Program Files\Hitman Pro 3.5\HitmanPro35.exe (SurfRight B.V.)
O4 - HKLM..\Run: [ISUSPM Startup] C:\Program Files\Common Files\InstallShield\UpdateService\isuspm.exe (Macrovision Corporation)
O4 - HKLM..\Run: [ISUSScheduler] C:\Program Files\Common Files\InstallShield\UpdateService\issch.exe (Macrovision Corporation)
O4 - HKLM..\Run: [mcagent_exe] C:\Program Files\McAfee.com\Agent\mcagent.exe (McAfee, Inc.)
O4 - HKLM..\Run: [PCSuiteTrayApplication] C:\Program Files\Nokia\Nokia PC Suite 6\LaunchApplication.exe (Nokia)
O4 - HKLM..\Run: [RealTray] C:\Program Files\Real\RealPlayer\RealPlay.exe (RealNetworks, Inc.)
O4 - HKCU..\Run: [ISUSPM] C:\Program Files\Common Files\InstallShield\UpdateService\isuspm.exe (Macrovision Corporation)
O4 - Startup: C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office\OSA9.EXE (Microsoft Corporation)
O4 - Startup: C:\Documents and Settings\All Users\Start Menu\Programs\Startup\NETGEAR WG111T Smart Wizard.lnk = C:\Program Files\NETGEAR\WG111T\wlan111t.exe (NETGEAR)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoCDBurning = 0
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: InstallVisualStyle = C:\WINDOWS\Resources\Themes\Royale\Royale.msstyles (Microsoft)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: InstallTheme = C:\WINDOWS\Resources\Themes\Royale.theme ()
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O9 - Extra Button: HP Smart Select - {DDE87865-83C5-48c4-8357-2F5B1AA84522} - C:\Program Files\HP\Digital Imaging\Smart Web Printing\hpswp_BHO.dll (Hewlett-Packard Co.)
O16 - DPF: {166B1BCA-3F9C-11CF-8075-444553540000} http://download.macr...director/sw.cab (Shockwave ActiveX Control)
O16 - DPF: {6A6F4B83-45C5-4CA9-BDD9-0D81C12295E4} https://exchange.aws...emote/msrdp.cab (Microsoft RDP Client Control (redist))
O16 - DPF: {8100D56A-5661-482C-BEE8-AFECE305D968} http://upload.facebo...oUploader55.cab (Facebook Photo Uploader 5 Control)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_17)
O16 - DPF: {A1F35586-A5A8-4D37-947A-81875350B11F} http://webalbum.bonu...geUploader4.cab (Bonusprint Image Uploader Version 4.5 Control)
O16 - DPF: {CAFEEFAC-0015-0000-0006-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0015-0000-0009-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0001-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0002-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0003-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0005-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0007-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Reg Error: Key error.)
O16 - DPF: {CAFEEFAC-0016-0000-0017-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_17)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_17)
O16 - DPF: {E008A543-CEFB-4559-912F-C27C2B89F13B} https://cat-b5pk-01....t.com/dwa7W.cab (Domino Web Access 7 Control)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.1.1
O18 - Protocol\Handler\sacore {5513F07E-936B-4E52-9B00-067394E91CC5} - c:\Program Files\McAfee\SiteAdvisor\McIEPlg.dll ()
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - Winlogon\Notify\igfxcui: DllName - igfxdev.dll - C:\WINDOWS\System32\igfxdev.dll (Intel Corporation)
O24 - Desktop WallPaper: C:\Documents and Settings\Tommy\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O24 - Desktop BackupWallPaper: C:\Documents and Settings\Tommy\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2005/08/16 04:43:04 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O33 - MountPoints2\{361ac05d-0e0d-11da-9aa9-806d6172696f}\Shell - "" = AutoRun
O33 - MountPoints2\{361ac05d-0e0d-11da-9aa9-806d6172696f}\Shell\AutoRun - "" = Auto&Play
O33 - MountPoints2\{361ac05d-0e0d-11da-9aa9-806d6172696f}\Shell\AutoRun\command - "" = E:\setup.exe -- File not found
O34 - HKLM BootExecute: (autocheck autochk *) - File not found
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = comfile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
NetSvcs: 6to4 - File not found
NetSvcs: HidServ - C:\WINDOWS\System32\hidserv.dll File not found
NetSvcs: Ias - File not found
NetSvcs: Iprip - File not found
NetSvcs: Irmon - File not found
NetSvcs: NWCWorkstation - File not found
NetSvcs: Nwsapagent - File not found
NetSvcs: WmdmPmSp - File not found
CREATERESTOREPOINT
Restore point Set: OTL Restore Point (54619756233228288)
========== Files/Folders - Created Within 90 Days ==========
[2010/08/18 22:36:43 | 000,575,488 | ---- | C] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\OTL.exe
[2010/08/18 19:24:34 | 000,000,000 | ---D | C] -- C:\WINDOWS\ERDNT
[2010/08/18 19:22:00 | 000,000,000 | ---D | C] -- C:\Program Files\ERUNT
[2010/08/18 19:21:12 | 000,791,393 | ---- | C] (Lars Hederer ) -- C:\Documents and Settings\Tommy\Desktop\erunt-setup.exe
[2010/08/18 17:43:03 | 000,446,464 | ---- | C] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\TFC.exe
[2010/08/17 18:26:09 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Tommy\Application Data\Malwarebytes
[2010/08/17 18:25:55 | 000,038,224 | ---- | C] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbamswissarmy.sys
[2010/08/17 18:25:54 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\Malwarebytes
[2010/08/17 18:22:02 | 006,153,352 | ---- | C] (Malwarebytes Corporation ) -- C:\Documents and Settings\Tommy\Desktop\mbam-setup-1.46.exe
[2010/08/17 17:39:57 | 000,000,000 | ---D | C] -- C:\WINDOWS\CSC
[2010/08/17 17:37:52 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\Hitman Pro
[2010/08/17 17:37:49 | 000,000,000 | ---D | C] -- C:\Program Files\Hitman Pro 3.5
[2010/08/17 17:37:01 | 000,020,952 | ---- | C] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbam.sys
[2010/08/17 17:37:01 | 000,000,000 | ---D | C] -- C:\Program Files\Malwarebytes' Anti-Malware
[2010/08/15 21:55:58 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Tommy\Local Settings\Application Data\Windows Server
[2010/07/06 18:17:34 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Tommy\Desktop\Panoramas
[2006/10/25 22:39:29 | 000,581,632 | ---- | C] (Joshua F. Madison) -- C:\Program Files\CONVERT.EXE
========== Files - Modified Within 90 Days ==========
[2010/08/18 22:36:51 | 000,575,488 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\OTL.exe
[2010/08/18 22:35:21 | 006,553,600 | -H-- | M] () -- C:\Documents and Settings\Tommy\NTUSER.DAT
[2010/08/18 19:34:32 | 000,284,915 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\gmer.zip
[2010/08/18 19:22:00 | 000,000,592 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\ERUNT.lnk
[2010/08/18 19:21:21 | 000,791,393 | ---- | M] (Lars Hederer ) -- C:\Documents and Settings\Tommy\Desktop\erunt-setup.exe
[2010/08/18 19:17:21 | 000,016,968 | ---- | M] () -- C:\WINDOWS\System32\drivers\hitmanpro35.sys
[2010/08/18 19:17:21 | 000,011,965 | ---- | M] () -- C:\WINDOWS\System32\Config.MPF
[2010/08/18 19:16:53 | 000,002,206 | ---- | M] () -- C:\WINDOWS\System32\wpa.dbl
[2010/08/18 19:16:30 | 000,054,156 | -H-- | M] () -- C:\WINDOWS\QTFont.qfn
[2010/08/18 19:16:15 | 000,000,006 | -H-- | M] () -- C:\WINDOWS\tasks\SA.DAT
[2010/08/18 19:16:11 | 000,002,048 | --S- | M] () -- C:\WINDOWS\bootstat.dat
[2010/08/18 19:16:10 | 2137,149,440 | -HS- | M] () -- C:\hiberfil.sys
[2010/08/18 19:15:30 | 000,000,278 | -HS- | M] () -- C:\Documents and Settings\Tommy\ntuser.ini
[2010/08/18 17:43:12 | 000,446,464 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\TFC.exe
[2010/08/17 18:22:02 | 006,153,352 | ---- | M] (Malwarebytes Corporation ) -- C:\Documents and Settings\Tommy\Desktop\mbam-setup-1.46.exe
[2010/08/17 18:14:24 | 000,001,014 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\log.xml
[2010/08/17 17:37:50 | 000,001,663 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\Hitman Pro 3.5.lnk
[2010/08/16 23:24:04 | 000,266,208 | ---- | M] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2010/08/16 23:22:19 | 000,073,688 | ---- | M] () -- C:\Documents and Settings\Tommy\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
[2010/08/15 22:14:39 | 000,002,237 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Memory-Map OS-5.lnk
[2010/08/14 17:51:39 | 000,631,542 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\RAC win BTCC.jpg
[2010/08/14 17:50:23 | 000,002,445 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Paint Shop Pro 7.lnk
[2010/08/12 22:41:59 | 000,094,720 | ---- | M] () -- C:\Documents and Settings\Tommy\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2010/07/30 17:22:36 | 000,002,489 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Microsoft Excel.lnk
[2010/07/29 21:45:23 | 000,002,491 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Microsoft Word.lnk
[2010/07/15 23:20:02 | 000,203,776 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\Calculation of rotating damper charactersticsjuly2010.doc
[2010/07/15 15:18:22 | 000,120,136 | ---- | M] (McAfee, Inc.) -- C:\WINDOWS\System32\drivers\Mpfp.sys
[2010/07/12 23:30:23 | 000,000,720 | ---- | M] () -- C:\WINDOWS\win.ini
[2010/07/12 17:47:10 | 000,000,938 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Adobe Photoshop Elements 8.0.lnk
[2010/07/01 01:00:05 | 000,000,318 | ---- | M] () -- C:\WINDOWS\tasks\McQcTask.job
[2010/06/25 09:18:54 | 000,002,473 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\Microsoft Word.lnk
[2010/06/19 18:19:09 | 005,349,869 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\Moy190610.wmv
[2010/06/08 23:22:18 | 000,001,355 | ---- | M] () -- C:\WINDOWS\imsins.BAK
[2010/06/01 22:05:20 | 080,976,972 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\DSCF1515.AVI
[2010/06/01 21:59:40 | 082,864,116 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\DSCF1514.AVI
[2010/05/29 21:35:46 | 004,683,205 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\S200_en.pdf
[2010/05/28 20:49:33 | 031,850,262 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\Wideopenmag_Issue_12.pdf
[2010/05/28 20:47:59 | 026,714,354 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\Wideopenmag_Issue_7.pdf
[2010/05/26 21:31:00 | 000,381,162 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\bikeparkkarta_lr.pdf
[2010/05/25 19:05:08 | 004,547,186 | ---- | M] () -- C:\Documents and Settings\Tommy\Desktop\7stanes7.wmv
========== Files Created - No Company Name ==========
[2010/08/18 19:34:28 | 000,284,915 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\gmer.zip
[2010/08/18 19:22:00 | 000,000,592 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\ERUNT.lnk
[2010/08/17 18:14:24 | 000,001,014 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\log.xml
[2010/08/17 17:47:51 | 000,016,968 | ---- | C] () -- C:\WINDOWS\System32\drivers\hitmanpro35.sys
[2010/08/17 17:46:38 | 2137,149,440 | -HS- | C] () -- C:\hiberfil.sys
[2010/08/17 17:37:50 | 000,001,663 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\Hitman Pro 3.5.lnk
[2010/08/14 17:51:39 | 000,631,542 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\RAC win BTCC.jpg
[2010/07/15 23:19:59 | 000,203,776 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\Calculation of rotating damper charactersticsjuly2010.doc
[2010/07/12 17:47:10 | 000,000,938 | ---- | C] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Adobe Photoshop Elements 8.0.lnk
[2010/06/19 18:18:05 | 005,349,869 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\Moy190610.wmv
[2010/06/01 23:47:24 | 080,976,972 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\DSCF1515.AVI
[2010/06/01 23:46:58 | 082,864,116 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\DSCF1514.AVI
[2010/05/29 21:35:06 | 004,683,205 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\S200_en.pdf
[2010/05/28 20:49:31 | 031,850,262 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\Wideopenmag_Issue_12.pdf
[2010/05/28 20:47:57 | 026,714,354 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\Wideopenmag_Issue_7.pdf
[2010/05/26 21:31:00 | 000,381,162 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\bikeparkkarta_lr.pdf
[2010/05/25 19:05:07 | 004,547,186 | ---- | C] () -- C:\Documents and Settings\Tommy\Desktop\7stanes7.wmv
[2010/02/12 21:50:50 | 000,000,065 | ---- | C] () -- C:\WINDOWS\minitab.ini
[2009/06/04 09:48:40 | 000,001,633 | ---- | C] () -- C:\Documents and Settings\All Users\Application Data\hpzinstall.log
[2009/02/15 16:38:29 | 000,000,049 | ---- | C] () -- C:\Documents and Settings\Tommy\Local Settings\Application Data\mm-device-08.ini
[2009/02/15 16:35:28 | 000,000,597 | ---- | C] () -- C:\WINDOWS\{55E24696-B7D5-498B-8F6A-DF2161859303}_WiseFW.ini
[2008/09/10 20:17:31 | 000,651,264 | ---- | C] () -- C:\WINDOWS\System32\libeay32.dll
[2008/09/10 20:17:31 | 000,147,456 | ---- | C] () -- C:\WINDOWS\System32\ssleay32.dll
[2008/05/24 18:27:49 | 000,007,154 | ---- | C] () -- C:\WINDOWS\Perkins 1104D.ini
[2008/01/19 13:08:23 | 003,287,355 | ---- | C] () -- C:\Documents and Settings\Tommy\Application Data\NMM-MetaData.db
[2007/11/19 23:00:16 | 000,000,196 | ---- | C] () -- C:\WINDOWS\ppdrv.ini
[2007/07/04 22:02:46 | 000,000,251 | ---- | C] () -- C:\Program Files\wt3d.ini
[2007/02/25 20:41:00 | 000,003,072 | ---- | C] () -- C:\Documents and Settings\Tommy\Application Data\dvd.bmk
[2007/01/14 23:06:55 | 000,000,021 | ---- | C] () -- C:\WINDOWS\VI2_SETUP.ini
[2007/01/14 00:33:06 | 000,001,751 | ---- | C] () -- C:\Documents and Settings\All Users\Application Data\QTSBandwidthCache
[2006/11/22 00:14:01 | 000,000,002 | ---- | C] () -- C:\WINDOWS\msoffice.ini
[2006/11/08 22:20:23 | 000,000,187 | ---- | C] () -- C:\Documents and Settings\Tommy\Application Data\G-Force Prefs (WindowsMediaPlayer).txt
[2006/10/24 22:49:18 | 000,000,376 | ---- | C] () -- C:\WINDOWS\ODBC.INI
[2006/10/23 22:25:22 | 000,094,720 | ---- | C] () -- C:\Documents and Settings\Tommy\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2006/10/20 11:06:03 | 000,003,558 | -HS- | C] () -- C:\WINDOWS\System32\KGyGaAvL.sys
[2006/10/20 11:06:03 | 000,000,088 | RHS- | C] () -- C:\WINDOWS\System32\AA05F475A1.sys
[2006/10/20 10:48:12 | 000,000,128 | ---- | C] () -- C:\Documents and Settings\Tommy\Local Settings\Application Data\fusioncache.dat
[2006/10/18 04:43:21 | 000,000,061 | ---- | C] () -- C:\WINDOWS\smscfg.ini
[2006/10/18 04:36:35 | 000,000,126 | ---- | C] () -- C:\WINDOWS\wininit.ini
[2006/10/18 04:31:32 | 000,712,704 | ---- | C] () -- C:\WINDOWS\System32\DellSystemRestore.dll
[2006/10/18 04:05:03 | 000,000,475 | ---- | C] () -- C:\WINDOWS\System32\OEMINFO.INI
[2005/12/07 13:31:00 | 000,202,752 | R--- | C] () -- C:\WINDOWS\System32\CddbCdda.dll
[2005/11/10 01:56:34 | 000,000,000 | ---- | C] () -- C:\WINDOWS\System32\px.ini
[2005/08/31 12:11:14 | 000,000,442 | ---- | C] () -- C:\WINDOWS\System32\dlcfplc.ini
[2005/08/16 04:37:24 | 000,001,793 | ---- | C] () -- C:\WINDOWS\System32\fxsperf.ini
[2005/08/05 14:01:54 | 000,235,008 | ---- | C] () -- C:\WINDOWS\System32\psisdecd.dll
[1999/01/22 19:46:58 | 000,065,536 | ---- | C] () -- C:\WINDOWS\System32\MSRTEDIT.DLL
[1998/01/12 09:00:00 | 000,040,448 | ---- | C] () -- C:\WINDOWS\System32\REGOBJ.DLL
========== LOP Check ==========
[2010/08/17 17:47:48 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Hitman Pro
[2008/01/19 12:20:26 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Installations
[2009/02/15 16:38:29 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Memory-Map-License
[2008/01/19 12:30:47 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\PC Suite
[2006/10/24 22:51:27 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\SBT
[2006/10/18 04:33:45 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Viewpoint
[2008/12/21 21:19:05 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\Amazon
[2008/01/13 22:51:54 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\FUJIFILM
[2009/12/31 14:06:23 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\HDRsoft
[2007/04/24 22:50:08 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\Jasc
[2006/10/20 11:37:50 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\Leadertech
[2008/02/06 21:00:53 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\Nokia
[2008/01/19 12:38:34 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\Nokia Multimedia Player
[2008/01/19 12:49:20 | 000,000,000 | ---D | M] -- C:\Documents and Settings\Tommy\Application Data\PC Suite
[2010/05/15 02:21:41 | 000,000,340 | ---- | M] () -- C:\WINDOWS\Tasks\McDefragTask.job
[2010/07/01 01:00:05 | 000,000,318 | ---- | M] () -- C:\WINDOWS\Tasks\McQcTask.job
========== Purity Check ==========
========== Custom Scans ==========
< %SYSTEMDRIVE%\*.* >
[2005/08/16 04:43:04 | 000,000,000 | ---- | M] () -- C:\AUTOEXEC.BAT
[2009/11/18 22:56:44 | 000,000,209 | RHS- | M] () -- C:\boot.ini
[2005/08/16 04:43:04 | 000,000,000 | ---- | M] () -- C:\CONFIG.SYS
[2006/10/18 04:10:48 | 000,005,556 | RH-- | M] () -- C:\dell.sdr
[2009/10/05 23:13:55 | 000,096,670 | ---- | M] () -- C:\dlcf.log
[2007/02/12 22:28:26 | 000,440,320 | -HS- | M] () -- C:\ehthumbs.db
[2010/08/18 19:16:10 | 2137,149,440 | -HS- | M] () -- C:\hiberfil.sys
[2006/10/24 23:24:28 | 000,004,128 | ---- | M] () -- C:\INFCACHE.1
[2005/08/16 04:43:04 | 000,000,000 | -H-- | M] () -- C:\IO.SYS
[2006/10/18 04:33:53 | 000,000,909 | -H-- | M] () -- C:\IPH.PH
[2005/08/16 04:43:04 | 000,000,000 | -H-- | M] () -- C:\MSDOS.SYS
[2004/08/10 05:00:00 | 000,047,564 | RHS- | M] () -- C:\NTDETECT.COM
[2004/08/10 05:00:00 | 000,250,032 | RHS- | M] () -- C:\ntldr
[2010/08/18 19:16:08 | 792,723,456 | -HS- | M] () -- C:\pagefile.sys
[2009/06/10 22:17:15 | 000,000,594 | ---- | M] () -- C:\updatedatfix.log
< %systemroot%\Fonts\*.com >
< %systemroot%\Fonts\*.dll >
< %systemroot%\Fonts\*.ini >
[2005/08/16 04:42:12 | 000,000,067 | -HS- | M] () -- C:\WINDOWS\Fonts\desktop.ini
< %systemroot%\Fonts\*.ini2 >
< %systemroot%\Fonts\*.exe >
< %systemroot%\system32\spool\prtprocs\w32x86\*.* >
[2007/12/17 18:05:32 | 000,278,016 | ---- | M] (Hewlett-Packard Corporation) -- C:\WINDOWS\system32\spool\prtprocs\w32x86\hpzpp5mu.dll
< %systemroot%\REPAIR\*.bak1 >
< %systemroot%\REPAIR\*.ini >
< %systemroot%\system32\*.jpg >
< %systemroot%\*.jpg >
< %systemroot%\*.png >
< %systemroot%\*.scr >
[2008/05/24 18:27:49 | 000,462,336 | ---- | M] () -- C:\WINDOWS\Perkins 1104D.scr
< %systemroot%\*._sy >
< %APPDATA%\Adobe\Update\*.* >
< %ALLUSERSPROFILE%\Favorites\*.* >
< %APPDATA%\Microsoft\*.* >
< %PROGRAMFILES%\*.* >
[2000/09/28 16:36:34 | 000,581,632 | ---- | M] (Joshua F. Madison) -- C:\Program Files\CONVERT.EXE
[2007/07/04 22:02:46 | 000,000,251 | ---- | M] () -- C:\Program Files\wt3d.ini
< %APPDATA%\Update\*.* >
< %systemroot%\*. /mp /s >
< %systemroot%\System32\config\*.sav >
[2005/08/16 04:27:08 | 000,094,208 | ---- | M] () -- C:\WINDOWS\system32\config\default.sav
[2005/08/16 04:27:08 | 000,659,456 | ---- | M] () -- C:\WINDOWS\system32\config\software.sav
[2005/08/16 04:27:08 | 000,876,544 | ---- | M] () -- C:\WINDOWS\system32\config\system.sav
< %PROGRAMFILES%\bak. /s >
< %systemroot%\system32\bak. /s >
< %ALLUSERSPROFILE%\Start Menu\*.lnk /x >
[2005/08/16 04:43:10 | 000,000,294 | -HS- | M] () -- C:\Documents and Settings\All Users\Start Menu\desktop.ini
< %systemroot%\system32\config\systemprofile\*.dat /x >
< %systemroot%\*.config >
< %systemroot%\system32\*.db >
< %PROGRAMFILES%\Internet Explorer\*.dat >
< %APPDATA%\Microsoft\Internet Explorer\Quick Launch\*.lnk /x >
[2006/10/20 10:48:28 | 000,000,170 | -HS- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\desktop.ini
[2005/08/16 04:50:28 | 000,000,079 | ---- | M] () -- C:\Documents and Settings\Tommy\Application Data\Microsoft\Internet Explorer\Quick Launch\Show Desktop.scf
< %USERPROFILE%\Desktop\*.exe >
[2010/08/18 19:21:21 | 000,791,393 | ---- | M] (Lars Hederer ) -- C:\Documents and Settings\Tommy\Desktop\erunt-setup.exe
[2010/08/17 18:22:02 | 006,153,352 | ---- | M] (Malwarebytes Corporation ) -- C:\Documents and Settings\Tommy\Desktop\mbam-setup-1.46.exe
[2010/08/18 22:36:51 | 000,575,488 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\OTL.exe
[2009/12/31 13:52:54 | 003,338,808 | ---- | M] (HDRsoft Sarl ) -- C:\Documents and Settings\Tommy\Desktop\PhotomatixPro326x32.exe
[2010/08/18 17:43:12 | 000,446,464 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\Tommy\Desktop\TFC.exe
< %PROGRAMFILES%\Common Files\*.* >
< %systemroot%\*.src >
< %systemroot%\install\*.* >
< %systemroot%\system32\DLL\*.* >
< %systemroot%\system32\HelpFiles\*.* >
< %systemroot%\system32\rundll\*.* >
< %systemroot%\winn32\*.* >
< %systemroot%\Java\*.* >
< %systemroot%\system32\test\*.* >
< %systemroot%\system32\Rundll32\*.* >
< HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU >
< HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\Results\Install|LastSuccessTime /rs >
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\Results\Install\\LastSuccessTime: 2010-08-17 16:51:03
< End of report >
OTL Extras log
OTL Extras logfile created on: 18/08/2010 22:38:37 - Run 1
OTL by OldTimer - Version 3.2.10.0 Folder = C:\Documents and Settings\Tommy\Desktop
Windows XP Media Center Edition Service Pack 2 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 7.0.5730.11)
Locale: 00000809 | Country: United Kingdom | Language: ENG | Date Format: dd/MM/yyyy
2.00 Gb Total Physical Memory | 1.00 Gb Available Physical Memory | 73.00% Memory free
3.00 Gb Paging File | 2.00 Gb Available in Paging File | 83.00% Paging File free
Paging file location(s): C:\pagefile.sys 756 1512 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 107.09 Gb Total Space | 34.24 Gb Free Space | 31.97% Space Free | Partition Type: NTFS
Drive D: | 37.24 Gb Total Space | 36.86 Gb Free Space | 98.98% Space Free | Partition Type: NTFS
E: Drive not present or media not loaded
F: Drive not present or media not loaded
G: Drive not present or media not loaded
H: Drive not present or media not loaded
I: Drive not present or media not loaded
Drive K: | 964.54 Mb Total Space | 951.22 Mb Free Space | 98.62% Space Free | Partition Type: FAT32
Computer Name: TOM
Current User Name: Tommy
Logged in as Administrator.
Current Boot Mode: Normal
Scan Mode: Current user
Company Name Whitelist: On
Skip Microsoft Files: On
File Age = 90 Days
Output = Standard
Quick Scan
========== Extra Registry (SafeList) ==========
========== File Associations ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<extension>]
========== Shell Spawning ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<key>\shell\[command]\command]
batfile [open] -- "%1" %*
cmdfile [open] -- "%1" %*
comfile [open] -- "%1" %*
exefile [open] -- "%1" %*
htmlfile [edit] -- "C:\Program Files\Microsoft Office\Office\msohtmed.exe" %1 (Microsoft Corporation)
htmlfile [print] -- "C:\Program Files\Microsoft Office\Office\msohtmed.exe" /p %1 (Microsoft Corporation)
piffile [open] -- "%1" %*
regfile [merge] -- Reg Error: Key error.
scrfile [config] -- "%1"
scrfile [install] -- rundll32.exe desk.cpl,InstallScreenSaver %l (Microsoft Corporation)
scrfile [open] -- "%1" /S
txtfile [edit] -- Reg Error: Key error.
Unknown [openas] -- %SystemRoot%\system32\rundll32.exe %SystemRoot%\system32\shell32.dll,OpenAs_RunDLL %1
Directory [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Folder [open] -- %SystemRoot%\Explorer.exe /idlist,%I,%L (Microsoft Corporation)
Folder [explore] -- %SystemRoot%\Explorer.exe /e,/idlist,%I,%L (Microsoft Corporation)
Drive [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
========== Security Center Settings ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"FirstRunDisabled" = 1
"UpdatesDisableNotify" = 0
"AntiVirusOverride" = 0
"FirewallOverride" = 0
"AntiVirusDisableNotify" = 0
"FirewallDisableNotify" = 0
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\AhnlabAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\ComputerAssociatesAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\KasperskyAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\McAfeeAntiVirus]
"DisableMonitoring" = 1
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\McAfeeFirewall]
"DisableMonitoring" = 1
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\PandaAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\PandaFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SophosAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SymantecAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\SymantecFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TinyFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TrendAntiVirus]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\TrendFirewall]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring\ZoneLabsFirewall]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile]
"EnableFirewall" = 0
"DisableNotifications" = 0
"DoNotAllowExceptions" = 0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\GloballyOpenPorts\List]
"1900:UDP" = 1900:UDP:LocalSubNet:Disabled:@xpsp2res.dll,-22007
"2869:TCP" = 2869:TCP:LocalSubNet:Disabled:@xpsp2res.dll,-22008
========== Authorized Applications List ==========
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List]
"C:\Program Files\Bonusprint PhotoBook Editor\apc.exe" = C:\Program Files\Bonusprint PhotoBook Editor\apc.exe:*:Enabled:Bonusprint PhotoBook Editor -- (Albumprinter.com)
"C:\Program Files\McAfee\MSC\mcshell.exe" = C:\Program Files\McAfee\MSC\mcshell.exe:*:Enabled:McAfee SecurityCenter -- (McAfee, Inc.)
"C:\Program Files\iTunes\iTunes.exe" = C:\Program Files\iTunes\iTunes.exe:*:Enabled:iTunes -- (Apple Inc.)
"F:\Autorun.exe" = F:\Autorun.exe:*:Enabled:CD navigator -- File not found
"C:\Program Files\Memory-Map\OS-5\mm3d.exe" = C:\Program Files\Memory-Map\OS-5\mm3d.exe:*:Enabled:Memory-Map 3D -- (Memory-Map, Inc)
"C:\Program Files\Memory-Map\OS-5\MMNav.exe" = C:\Program Files\Memory-Map\OS-5\MMNav.exe:*:Enabled:Memory-Map -- (Memory-Map, Inc)
"C:\Program Files\Memory-Map\OS-5\showmmcrypt.exe" = C:\Program Files\Memory-Map\OS-5\showmmcrypt.exe:*:Enabled:License-Managed Data Viewer -- ()
"C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe" = C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe:*:Enabled:hpqtra08.exe -- File not found
"C:\Program Files\HP\Digital Imaging\bin\hpqste08.exe" = C:\Program Files\HP\Digital Imaging\bin\hpqste08.exe:*:Enabled:hpqste08.exe -- File not found
"C:\Program Files\HP\Digital Imaging\bin\hposid01.exe" = C:\Program Files\HP\Digital Imaging\bin\hposid01.exe:*:Enabled:hposid01.exe -- File not found
"C:\Program Files\HP\Digital Imaging\bin\hpiscnapp.exe" = C:\Program Files\HP\Digital Imaging\bin\hpiscnapp.exe:*:Enabled:hpiscnapp.exe -- File not found
"C:\Program Files\HP\Digital Imaging\bin\hpqkygrp.exe" = C:\Program Files\HP\Digital Imaging\bin\hpqkygrp.exe:*:Enabled:hpqkygrp.exe -- File not found
"C:\Program Files\Common Files\McAfee\MNA\McNASvc.exe" = C:\Program Files\Common Files\McAfee\MNA\McNASvc.exe:*:Enabled:McAfee Network Agent -- (McAfee, Inc.)
"C:\Program Files\Adobe\Elements Organizer 8.0\AdobePhotoshopElementsMediaServer.exe" = C:\Program Files\Adobe\Elements Organizer 8.0\AdobePhotoshopElementsMediaServer.exe:*:Disabled:Adobe Photoshop Elements Media Server -- (Adobe Systems Incorporated)
========== HKEY_LOCAL_MACHINE Uninstall List ==========
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall]
"{00010409-78E1-11D2-B60F-006097C998E7}" = Microsoft Office 2000 Professional
"{00040409-78E1-11D2-B60F-006097C998E7}" = Microsoft Office 2000 Disc 2
"{00203668-8170-44A0-BE44-B632FA4D780F}" = Adobe AIR
"{066D65EA-ED53-44E4-A96A-F81B6E409D2E}" = PC Connectivity Solution
"{075473F5-846A-448B-BCB3-104AA1760205}" = Roxio RecordNow Data
"{0D19B2D8-4FE4-48B2-BBA1-194B82A81230}" = Hyper-Utility2
"{1206EF92-2E83-4859-ACCB-2048C3CB7DA6}" = Roxio DLA
"{138CEA91-A651-45B0-9C2C-D69A44493E0F}" = Hyper-Utility Software Add-On
"{162D2FB8-60A3-4871-B6A1-5C744CD34FF5}" = 725plc32
"{17DFE37C-064E-4834-AD8F-A4B2B4DF68F8}" = Adobe Photoshop Elements 8.0
"{1D3C662A-F6C6-4767-A788-7AA43A9A1317}" = ARTEuro
"{21657574-BD54-48A2-9450-EB03B2C7FC29}" = Roxio MyDVD LE
"{26A24AE4-039D-4CA4-87B4-2F83216011FF}" = Java™ 6 Update 17
"{2CAB0F24-9552-4303-8C28-589F1911AA21}" = FinePixS3Pro ShootingDriver
"{30465B6C-B53F-49A1-9EBA-A3F187AD502E}" = Roxio Update Manager
"{3248F0A8-6813-11D6-A77B-00B0D0150060}" = J2SE Runtime Environment 5.0 Update 6
"{3248F0A8-6813-11D6-A77B-00B0D0150090}" = J2SE Runtime Environment 5.0 Update 9
"{3248F0A8-6813-11D6-A77B-00B0D0160010}" = Java™ SE Runtime Environment 6 Update 1
"{3248F0A8-6813-11D6-A77B-00B0D0160020}" = Java™ 6 Update 2
"{3248F0A8-6813-11D6-A77B-00B0D0160030}" = Java™ 6 Update 3
"{3248F0A8-6813-11D6-A77B-00B0D0160050}" = Java™ 6 Update 5
"{3248F0A8-6813-11D6-A77B-00B0D0160070}" = Java™ 6 Update 7
"{350C97B0-3D7C-4EE8-BAA9-00BCB3D54227}" = WebFldrs XP
"{3846E811-639D-4DE1-844B-30491C0A6C0C}" = Dell Support 3.2
"{3DE5E7D4-7B88-403C-A3FD-2017A8240C5B}" = Google Earth
"{3EE33958-7381-4E7B-A4F3-6E43098E9E9C}" = URL Assistant
"{43CAC9A1-1993-4F65-9096-7C9AFC2BBF54}" = Dell CinePlayer
"{45634CA5-CFDE-4794-9C1C-65613F2A0E4E}" = Hyper-Utility2 CCD-RAW Plug-In
"{4F5CE18C-D97D-48FF-A510-A0D90C918294}" = iTunes
"{5109C064-813E-4e87-B0DE-C8AF7B5BC02B}" = SmartWebPrintingOC
"{51123D42-6B9C-4B93-900C-29F9EC5963C9}" = NETGEAR WG111T 108Mbps Wireless USB2.0 Adapter
"{55E24696-B7D5-498B-8F6A-DF2161859303}" = Memory-Map OS Edition Version 5
"{57A48477-92F0-4C1F-ADF9-4806C4EC3CF2}" = Nokia PC Suite
"{5905F42D-3F5F-4916-ADA6-94A3646AEE76}" = Dell Driver Reset Tool
"{5B6BE547-21E2-49CA-B2E2-6A5F470593B1}" = Sonic Activation Module
"{5D063AFD-05EF-4CE8-895A-7817118B1D6A}" = Hyper-Utility2 FinePixS20Pro SHOOTING Plug-In
"{60DE73EA-5012-4106-84F1-2F0BD9EC6D9A}" = FinePixS20Pro ShootingDriver
"{6762AB61-2BE9-45D8-B9F2-24014324CD35}" = ArcSoft VideoImpression 2
"{6D52C408-B09A-4520-9B18-475B81D393F1}" = Microsoft Works
"{71D075F0-A6F5-40B9-A771-FC59E90B0181}" = Minitab 15 English
"{74F7662C-B1DB-489E-A8AC-07A06B24978B}" = Dell System Restore
"{758E2C3F-24F1-4172-99A5-51A62E4A5775}" = FinePixS2Pro ShootingDriver
"{76583DD5-2BCE-46F7-ACC4-3BF37645F4E0}" = FUJIFILM Hyper-Utility Software
"{77DCDCE3-2DED-62F3-8154-05E745472D07}" = Acrobat.com
"{80B3B090-7FE0-487D-9065-5D0B3FB9FC31}" = Studio Utility
"{819A351B-09B9-4AE2-A9E9-EAFBF8952A56}" = Hyper-Utility2 Preview Print
"{83F793B5-8BBF-42FD-A8A6-868CB3E2AAEA}" = Intel® PROSet for Wired Connections
"{8A708DD8-A5E6-11D4-A706-000629E95E20}" = Intel® Graphics Media Accelerator Driver
"{8A9B8148-DDD7-448F-BD6C-358386D32354}" = Corel Photo Album 6
"{8AE68327-FAA7-403D-AEEC-CBBA1DE2DBAD}" = Hyper-Utility2 CustomRendered Modifier Plug-In
"{972B1D9B-0EAD-49E8-B7D6-3B83FD5665B1}" = Nokia Connectivity Cable Driver
"{9763E36A-08E9-4228-BBCE-12989A4EB1A8}" = QuickTime
"{9941F0AA-B903-4AF4-A055-83A9815CC011}" = Sonic Encoders
"{AB708C9B-97C8-4AC9-899B-DBF226AC9382}" = Roxio RecordNow Audio
"{AC76BA86-7AD7-1033-7B44-A71000000002}" = Adobe Reader 7.1.0
"{B12665F4-4E93-4AB4-B7FC-37053B524629}" = Roxio RecordNow Copy
"{B1709DC3-3A8C-4C29-B0E7-F033450A62A0}" = Studio Utility shooting plug-in
"{B71E0018-25B9-4093-937E-13E6398B853B}" = Hyper-Utility2 File Format Plug-In
"{B74F042E-E1B9-4A5B-8D46-387BB172F0A4}" = Apple Software Update
"{BEA19A41-E180-40EE-A083-995A2C6B10C4}" = Hyper-Utility2 Print/Contact Sheet Output Plug-In
"{CB2F7EDD-9D1F-43C1-90FC-4F52EAE172A1}" = Microsoft .NET Framework 1.1
"{CF40ACC5-E1BB-4aff-AC72-04C2F616BCA7}" = getPlus® for Adobe
"{D2988E9B-C73F-422C-AD4B-A66EBE257120}" = MCU
"{D2A0F8F4-CE50-4857-A21C-3061682B2E87}" = Sansa Media Converter
"{D6DE02C7-1F47-11D4-9515-00105AE4B89A}" = Paint Shop Pro 7 Try And Buy
"{EE548EB1-4CF6-4A37-884D-0EA9DDB0F549}" = Hyper-Utility2 FinePixS3Pro SHOOTING Plug-In
"{F20E77B0-F2E0-402B-8868-BDEB5CC2D01B}" = Hyper-Utility2 Slide Show Plug-In
"{F261CFF7-ABE1-4DE3-8B5F-69DFD0D18972}" = HS-V2 Components
"{F87FF0A2-E55F-4BF8-9D0E-1B9BD846E17B}" = Hyper-Utility2 FinePixS2Pro SHOOTING Plug-In
"{FE57DE70-95DE-4B64-9266-84DA811053DB}" = HP Update
"0852D05415AB9A4F1EF451E342267F76C776ED2F" = Windows Driver Package - Nokia Modem (11/03/2006 6.82.0.1)
"0C5EDC3653FED5B121F464339EAC12534D253B25" = Windows Driver Package - Nokia Modem (02/15/2007 3.1)
"Adobe AIR" = Adobe AIR
"Adobe Flash Player ActiveX" = Adobe Flash Player 10 ActiveX
"Adobe Photoshop Elements 8.0" = Adobe Photoshop Elements 8.0
"Adobe Shockwave Player" = Adobe Shockwave Player
"Amazon MP3 Downloader" = Amazon MP3 Downloader 1.0.4
"Bonusprint PhotoBook Editor_is1" = Bonusprint PhotoBook Editor
"com.adobe.mauby.4875E02D9FB21EE389F73B8D1702B320485DF8CE.1" = Acrobat.com
"EmeraldQFE2" = Windows Media Player 10 Hotfix [See EmeraldQFE2 for more information]
"ERUNT_is1" = ERUNT 1.1j
"F064B256B4A20996EA9E333B5E0F14B61AB3333D" = Windows Driver Package - Nokia (WUDFRd) WPD (03/19/2007 6.83.31.1)
"HitmanPro35" = Hitman Pro 3.5
"HP Smart Web Printing" = HP Smart Web Printing
"IDNMitigationAPIs" = Microsoft Internationalized Domain Names Mitigation APIs
"ie7" = Windows Internet Explorer 7
"Image Resizer Pro 2006_is1" = Image Resizer Pro 2006 2.6.7
"LiveUpdate" = LiveUpdate 2.6 (Symantec Corporation)
"Malwarebytes' Anti-Malware_is1" = Malwarebytes' Anti-Malware
"McAfee Uninstall Utility" = McAfee Uninstaller
"Microsoft .NET Framework 1.1 (1033)" = Microsoft .NET Framework 1.1
"MSC" = McAfee SecurityCenter
"MSCompPackV1" = Microsoft Compression Client Pack 1.0 for Windows XP
"NLSDownlevelMapping" = Microsoft National Language Support Downlevel APIs
"Nokia PC Suite" = Nokia PC Suite
"PhotomatixPro3x32_is1" = Photomatix Pro version 3.2.6
"PROSet" = Intel® PRO Network Connections Drivers
"RealPlayer 6.0" = RealPlayer Basic
"SearchAssist" = SearchAssist
"StreetPlugin" = Learn2 Player (Uninstall Only)
"ViewpointMediaPlayer" = Viewpoint Media Player
"Windows Media Format Runtime" = Windows Media Format 11 runtime
"Windows Media Player" = Windows Media Player 11
"WMFDist11" = Windows Media Format 11 runtime
"wmp11" = Windows Media Player 11
"Wudf01005" = Microsoft User-Mode Driver Framework Feature Pack 1.5
========== Last 10 Event Log Errors ==========
[ Application Events ]
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 17/08/2010 12:43:00 | Computer Name = TOM | Source = crypt32 | ID = 131080
Description = Failed auto update retrieval of third-party root list sequence number
from: <http://www.download....uthrootseq.txt>
with error: This network connection does not exist.
Error - 18/08/2010 12:42:53 | Computer Name = TOM | Source = McLogEvent | ID = 5019
Description = Exception in McShield.Exe! Exception details follow : VSCORE.14.0.0.435
Exception
Code : 0XC0000005 Exception Address : 0X7C91AB0A Exception Parameters :
2 Param 1 = 0X00000001 Param 2 = 0X01CB3F04 More information : ScanRequest : NTName
is \Device\HarddiskVolume2\Documents and Settings\Tommy\Local Settings\Temporary
Internet Files\Content.IE5\0EP0LDC3\TFC[1].exe.
Error - 18/08/2010 12:43:10 | Computer Name = TOM | Source = Application Error | ID = 1000
Description = Faulting application Mcshield.exe, version 14.0.0.435, faulting module
ntdll.dll, version 5.1.2600.3520, fault address 0x0001ab0a.
Error - 18/08/2010 12:44:23 | Computer Name = TOM | Source = McLogEvent | ID = 5051
Description = A thread in process C:\PROGRA~1\McAfee\VIRUSS~1\mcshield.exe took
longer than 90000 ms to complete a request. The process will be terminated. Thread
id : 4048 (0xfd0) Thread address : 0x7C90E514 Thread message : Object being scanned
= \Device\HarddiskVolume2\Documents and Settings\Tommy\Local Settings\Temporary
Internet Files\Content.IE5\0EP0LDC3\TFC[1].exe by C:\Program Files\Internet Explorer\iexplore.exe
4(0)(0) 4(0)(0) 7200(0)(0) 7595(0)(0) 7005(0)(0) 7004(0)(0) 5006(0)(0) 5004(0)(0)
[ System Events ]
Error - 18/08/2010 14:11:52 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee Services service terminated unexpectedly. It has done
this 1 time(s). The following corrective action will be taken in 60000 milliseconds:
Restart the service.
Error - 18/08/2010 14:11:53 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee Network Agent service terminated unexpectedly. It has
done this 1 time(s). The following corrective action will be taken in 60000 milliseconds:
Restart the service.
Error - 18/08/2010 14:11:53 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee Proxy Service service terminated unexpectedly. It has
done this 1 time(s). The following corrective action will be taken in 60000 milliseconds:
Restart the service.
Error - 18/08/2010 14:11:53 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee Personal Firewall Service service terminated unexpectedly.
It has done this 1 time(s). The following corrective action will be taken in
5000 milliseconds: Run the configured recovery program.
Error - 18/08/2010 14:11:53 | Computer Name = TOM | Source = Service Control Manager | ID = 7034
Description = The McAfee Anti-Spam Service service terminated unexpectedly. It
has done this 1 time(s).
Error - 18/08/2010 14:11:55 | Computer Name = TOM | Source = Service Control Manager | ID = 7034
Description = The iPod Service service terminated unexpectedly. It has done this
1 time(s).
Error - 18/08/2010 14:11:56 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee SystemGuards service terminated unexpectedly. It has done
this 1 time(s). The following corrective action will be taken in 60000 milliseconds:
Restart the service.
Error - 18/08/2010 14:11:56 | Computer Name = TOM | Source = Service Control Manager | ID = 7031
Description = The McAfee Real-time Scanner service terminated unexpectedly. It
has done this 2 time(s). The following corrective action will be taken in 60000
milliseconds: Restart the service.
Error - 18/08/2010 14:16:27 | Computer Name = TOM | Source = Service Control Manager | ID = 7023
Description = The Net Driver HPZ12 service terminated with the following error:
%%126
Error - 18/08/2010 14:16:27 | Computer Name = TOM | Source = Service Control Manager | ID = 7023
Description = The Pml Driver HPZ12 service terminated with the following error:
%%126
< End of report >





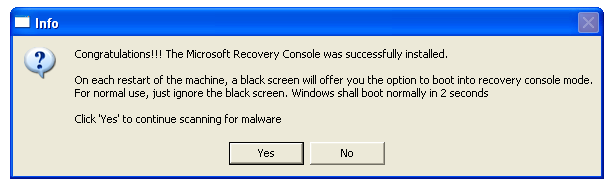












 Sign In
Sign In Create Account
Create Account

