wuauclt trojan, concerned it's still lurking
Started by
expMarmoset
, May 05 2011 02:12 AM
#1

 Posted 05 May 2011 - 02:12 AM
Posted 05 May 2011 - 02:12 AM

#2

 Posted 08 May 2011 - 03:22 PM
Posted 08 May 2011 - 03:22 PM

Hi, expMarmoset! Welcome to GeeksToGo! My nick name is Render and I will be assisting you with your Malware/Security problems. Please make sure you read all of the instructions and fixes thoroughly before continuing with them. If you have any queries or you are unsure about anything, just say and I'll help you out 
It may well be worth you printing/saving the instructions throughout the fix, so you have them to hand just in case you are unable to access this site.
Please note:
Forum and helpers has been busy and we're sorry about the delay.
Besides this problem, do you have any other issues that point at malware?
Please perform the following steps below so we can have a look at the current condition of your machine.
Step 1
 GMER Rootkit Scanner
GMER Rootkit Scanner
NOTE - Not all of the tick boxes will be available if you are running a 64bit Operating System. You may also get an error message display on the screen when using a 64bit Operating System, this is normal, just click on OK and let it carry on.
Caution - Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Step 2
 OTL Custom Scan
OTL Custom Scan
When completed the above, please post back the following in the order asked for:
It may well be worth you printing/saving the instructions throughout the fix, so you have them to hand just in case you are unable to access this site.
Please note:
- Remember to post your logs, not attach them. So, any logs from any programs we run, should be just 'copied & pasted' into your reply.
- Please only run the tools that I request. I know malware can be frustrating but running other tools in the meantime and between posts, only makes it harder for us to analyze and fix your PC in the long run.
Forum and helpers has been busy and we're sorry about the delay.
Besides this problem, do you have any other issues that point at malware?
Please perform the following steps below so we can have a look at the current condition of your machine.
Step 1
- Download GMER from HERE.
- Extract the contents of zipped file to your desktop.
- Double click GMER.exe.

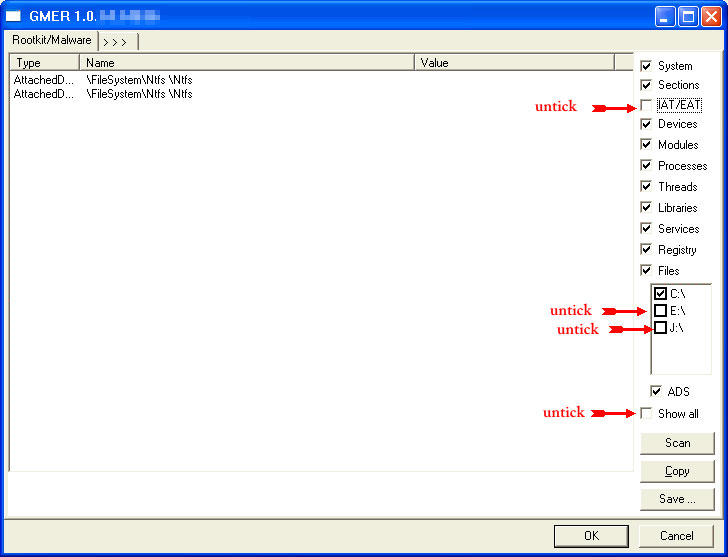
- If it gives you a warning about rootkit activity and asks if you want to run a full scan...click on NO, then use the following settings for a more complete scan..
- In the right panel, you will see several boxes that have been checked. Ensure the following are UNCHECKED:
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
NOTE - Not all of the tick boxes will be available if you are running a 64bit Operating System. You may also get an error message display on the screen when using a 64bit Operating System, this is normal, just click on OK and let it carry on.
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "ark.txt"
- Save the log where you can easily find it, such as your desktop.
- Please copy and paste the report into your Post.
Caution - Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Step 2
- Double click on the
 icon to run it.
icon to run it. - Make sure all other windows are closed and to let it run uninterrupted.
- When the window appears, underneath Output at the top, make sure Stadard output is selected.
- Check the boxes beside LOP Check and Purity Check.
- Copy (select all lines inside quote box and press CTRL+C) and Paste (press CTRL+V) the following code into the
 textbox.
textbox.
netsvcs %SYSTEMDRIVE%\*.exe /md5start explorer.exe winlogon.exe Userinit.exe svchost.exe /md5stop %systemroot%\*. /mp /s hklm\software\clients\startmenuinternet|command /rs CREATERESTOREPOINT
- Click the
 button. Do not change any settings unless otherwise told to do so. The scan wont take long.
button. Do not change any settings unless otherwise told to do so. The scan wont take long. - When the scan completes, it will open OTL.Txt in Notepad window.
- Please copy (Edit->Select All, Edit->Copy) the content of this file and post it with your next reply.
When completed the above, please post back the following in the order asked for:
- GMER log
- OTL scan log
#3

 Posted 16 May 2011 - 09:57 AM
Posted 16 May 2011 - 09:57 AM

Due to lack of feedback, this topic has been closed.
If you need this topic reopened, please contact a staff member. This applies only to the original topic starter. Everyone else please begin a New Topic.
If you need this topic reopened, please contact a staff member. This applies only to the original topic starter. Everyone else please begin a New Topic.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

