Problems after virus removal
Started by
18928
, Jun 04 2011 08:33 PM
#46

 Posted 14 June 2011 - 12:48 PM
Posted 14 June 2011 - 12:48 PM

#47

 Posted 14 June 2011 - 01:03 PM
Posted 14 June 2011 - 01:03 PM

Hi,
This looks better now. Now please try to run OTL.exe and hit Quick scan button. Then post OTL log in your next reply.
This looks better now. Now please try to run OTL.exe and hit Quick scan button. Then post OTL log in your next reply.
#48

 Posted 14 June 2011 - 01:14 PM
Posted 14 June 2011 - 01:14 PM

I tried it's freezing again on AudioX files
#49

 Posted 14 June 2011 - 01:21 PM
Posted 14 June 2011 - 01:21 PM

I still don't know what is going on here. Please bear with me and repeat these steps:
- Go to Start > All Programs > Accessories
- Right click Command Prompt and select Run as administrator
- When the prompt opens type the following bolded text and press enter
sfc /scannow (Note: There is a space between sfc and /scannow)
- On completion reboot
- Please download attachment cbs-log.zip to your desktop.
- UnZip it to your desktop.
- Right-click on cbs-log.bat icon and click on Run as administrator.
- If User Account Control (UAC) window will open click on Yes button.
- CBS.log file will be on your desktop.
- Please upload that file here and post a link to it in your next reply.
#50

 Posted 14 June 2011 - 02:19 PM
Posted 14 June 2011 - 02:19 PM

I have a problem uploading CBS.log with 2shared. It starts for a second and stops.
#51

 Posted 14 June 2011 - 02:25 PM
Posted 14 June 2011 - 02:25 PM

#52

 Posted 14 June 2011 - 03:22 PM
Posted 14 June 2011 - 03:22 PM

Please do the following:
- Open Windows Explorer and navigate to this folder: C:\Windows\System32.
- Inside that folder find file autochk.exe and copy it to your desktop.
- On your desktop right click on this file and select Send to and then click on Compressed (zipped) folder.
- File autochk.zip should be on your desktop.
- Please attach that file in your next reply.
#53

 Posted 14 June 2011 - 03:32 PM
Posted 14 June 2011 - 03:32 PM

And also do the same for autochk.exe.old please. You should find this file in same folder as autochk.exe.
#54

 Posted 14 June 2011 - 06:45 PM
Posted 14 June 2011 - 06:45 PM

Here they are.
Attached Files
#55

 Posted 14 June 2011 - 06:47 PM
Posted 14 June 2011 - 06:47 PM

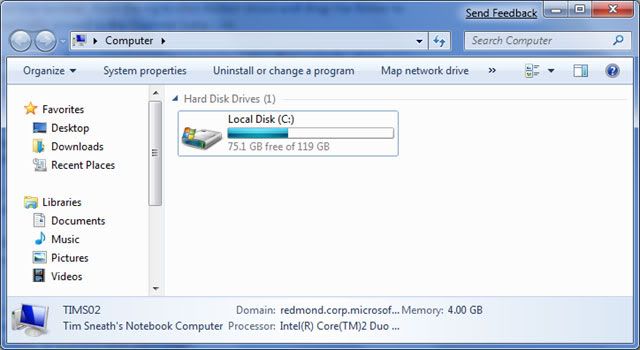
From the Start menu open your Computer
You should see something like this:
Right click your system partition (usually C) and select Properties
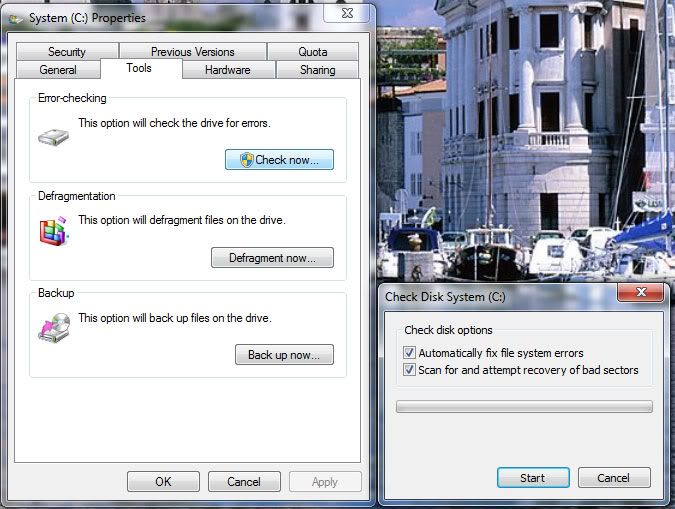
Select Tools tab and then Check now...
The second window will popup
Ensure you have ticks in both boxes
Then click Start
Windows will schedule it for the next boot
Reboot
You should see something like this:

Right click your system partition (usually C) and select Properties

Select Tools tab and then Check now...
The second window will popup
Ensure you have ticks in both boxes
Then click Start
Windows will schedule it for the next boot
Reboot
#56

 Posted 14 June 2011 - 08:58 PM
Posted 14 June 2011 - 08:58 PM

Finished it. It seems, that skype is working!!!!!! Still few problems: if I want to open any program it asks me what do I want to use to open it up. I'm still being redirected only this time another windows pop up. And what should I do with the"interactive services detection"? should I view the message? Thank you.
#57

 Posted 15 June 2011 - 05:33 AM
Posted 15 June 2011 - 05:33 AM

Please try to run OTL once again. Just click on Quick scan button and post a log.
#58

 Posted 15 June 2011 - 09:32 AM
Posted 15 June 2011 - 09:32 AM

OTL is not working. Same thing - freezing up on Xaudio.
#59

 Posted 15 June 2011 - 09:52 AM
Posted 15 June 2011 - 09:52 AM

Try now with this tool as instructed below:
 GMER Rootkit Scanner
GMER Rootkit Scanner
NOTE - Not all of the tick boxes will be available if you are running a 64bit Operating System. You may also get an error message display on the screen when using a 64bit Operating System, this is normal, just click on OK and let it carry on.
Caution - Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
If GMER should crash then proceed to the OTL scan!
- Download GMER from HERE.
- Extract the contents of zipped file to your desktop.
- Double click GMER.exe.

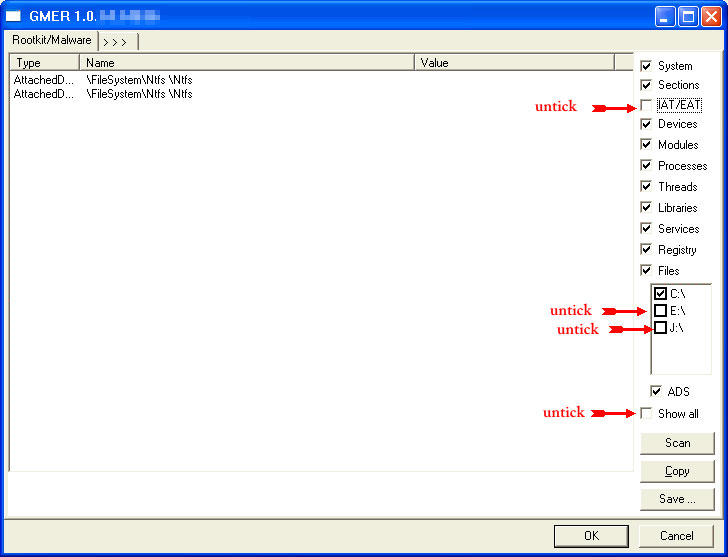
- If it gives you a warning about rootkit activity and asks if you want to run a full scan...click on NO, then use the following settings for a more complete scan..
- In the right panel, you will see several boxes that have been checked. Ensure the following are UNCHECKED:
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
NOTE - Not all of the tick boxes will be available if you are running a 64bit Operating System. You may also get an error message display on the screen when using a 64bit Operating System, this is normal, just click on OK and let it carry on.
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "ark.txt"
- Save the log where you can easily find it, such as your desktop.
- Please copy and paste the report into your Post.
Caution - Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
If GMER should crash then proceed to the OTL scan!
#60

 Posted 15 June 2011 - 01:29 PM
Posted 15 June 2011 - 01:29 PM

GMER 1.0.15.15640 - http://www.gmer.net
Rootkit scan 2011-06-15 15:27:52
Windows 6.1.7600 Harddisk0\DR0 -> \Device\Ide\iaStor0 ST925041 rev.D005
Running: gmer.exe; Driver: C:\Users\asta\AppData\Local\Temp\pxldrpow.sys
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwSaveKeyEx + 13BD 83488569 1 Byte [06]
.text ntkrnlpa.exe!KiDispatchInterrupt + 5A2 834AD092 19 Bytes [E0, 0F, BA, F0, 07, 73, 09, ...] {LOOPNZ 0x11; MOV EDX, 0x97307f0; MOV CR4, EAX; OR AL, 0x80; MOV CR4, EAX; RET ; MOV ECX, CR3}
---- User code sections - GMER 1.0.15 ----
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0031000A
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0035000A
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 001F000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0018000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 002E000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0013000A
.text C:\Windows\system32\svchost.exe[1080] ole32.dll!CoCreateInstance 75F2590C 5 Bytes JMP 0062000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!GetCursorPos 7774C198 5 Bytes JMP 0063000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!GetForegroundWindow 7775565D 5 Bytes JMP 0128000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!WindowFromPoint 77776D0C 5 Bytes JMP 0127000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 00B4000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 00B5000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 00AF000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 018D000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0194000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0038000A
.text C:\Program Files\Mozilla Firefox\plugin-container.exe[3128] USER32.dll!TrackPopupMenu 77774B3B 4 Bytes JMP 63A2C334 C:\Program Files\Mozilla Firefox\xul.dll (Mozilla Foundation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0023000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0067000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0022000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!CreateWindowExW 77750E51 5 Bytes JMP 6EFB8197 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxIndirectParamW 77774AA7 5 Bytes JMP 6F0DFED8 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxParamW 7777564A 5 Bytes JMP 6EED4BA7 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxParamA 7778CF6A 5 Bytes JMP 6F0DFE75 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxIndirectParamA 7778D29C 5 Bytes JMP 6F0DFF3B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxIndirectA 7779E8C9 5 Bytes JMP 6F0DFE0A C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxIndirectW 7779E9C3 5 Bytes JMP 6F0DFD9F C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxExA 7779EA29 5 Bytes JMP 6F0DFD3D C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxExW 7779EA4D 5 Bytes JMP 6F0DFCDB C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 01E6000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 01E7000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 01E5000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!UnhookWindowsHookEx 7774CC7B 5 Bytes JMP 6EFC83A2 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!CallNextHookEx 7774CC8F 5 Bytes JMP 6EFA9D94 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!CreateWindowExW 77750E51 5 Bytes JMP 6EFB8197 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!SetWindowsHookExW 7775210A 5 Bytes JMP 6EF6463B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxIndirectParamW 77774AA7 5 Bytes JMP 6F0DFED8 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxParamW 7777564A 5 Bytes JMP 6EED4BA7 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxParamA 7778CF6A 5 Bytes JMP 6F0DFE75 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxIndirectParamA 7778D29C 5 Bytes JMP 6F0DFF3B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxIndirectA 7779E8C9 5 Bytes JMP 6F0DFE0A C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxIndirectW 7779E9C3 5 Bytes JMP 6F0DFD9F C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxExA 7779EA29 5 Bytes JMP 6F0DFD3D C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxExW 7779EA4D 5 Bytes JMP 6F0DFCDB C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ole32.dll!OleLoadFromStream 75ED5BF6 5 Bytes JMP 6F0E022B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ole32.dll!CoCreateInstance 75F2590C 5 Bytes JMP 6EFB8C85 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
---- Devices - GMER 1.0.15 ----
Device \Driver\ACPI_HAL \Device\00000056 halmacpi.dll (Hardware Abstraction Layer DLL/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume3 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume3 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \FileSystem\fastfat \Fat fltmgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
---- Registry - GMER 1.0.15 ----
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}\Connection@Name isatap.{84BF6E8C-0D53-46DD-B5AD-2123B351536A}
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Bind \Device\{0625E7DE-F3CE-4BE5-9689-709BD77B190E}?\Device\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}?\Device\{935ECB00-6D14-45D0-A207-1C341BCEDE84}?\Device\{2B98EE92-59C7-43B3-8385-F15E083FC314}?
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Route "{0625E7DE-F3CE-4BE5-9689-709BD77B190E}"?"{5C409518-4135-4204-A8F0-BDEFBE2C09B6}"?"{935ECB00-6D14-45D0-A207-1C341BCEDE84}"?"{2B98EE92-59C7-43B3-8385-F15E083FC314}"?
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Export \Device\TCPIP6TUNNEL_{0625E7DE-F3CE-4BE5-9689-709BD77B190E}?\Device\TCPIP6TUNNEL_{5C409518-4135-4204-A8F0-BDEFBE2C09B6}?\Device\TCPIP6TUNNEL_{935ECB00-6D14-45D0-A207-1C341BCEDE84}?\Device\TCPIP6TUNNEL_{2B98EE92-59C7-43B3-8385-F15E083FC314}?
Reg HKLM\SYSTEM\CurrentControlSet\services\iphlpsvc\Parameters\Isatap\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}@InterfaceName isatap.{84BF6E8C-0D53-46DD-B5AD-2123B351536A}
Reg HKLM\SYSTEM\CurrentControlSet\services\iphlpsvc\Parameters\Isatap\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}@ReusableType 0
---- Disk sectors - GMER 1.0.15 ----
Disk \Device\Harddisk0\DR0 TDL4@MBR code has been found <-- ROOTKIT !!!
Disk \Device\Harddisk0\DR0 sector 00: rootkit-like behavior
---- Files - GMER 1.0.15 ----
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\female-reporter-gets-hit-with-ball[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\50c38b7cd25873c0d4ce412639d12a43f4d670a8[1].jpg 6058 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\adsCA6B5CKW 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\toppicks[3] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\ponsored=0;nickname=Indian_Larry;ispub=1;isLog=0;hpcdp=0;tags=microphone,prank,reporter;brkref=1;mar=ms-pr-breakhp;ord=442842110671576[1].3 62 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\611704_067cb090-87e3-4f6d-b23b-9c2b67b3bcf9_prod_1_0001_thumb[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\spanish-reporter-ruins-sand-castle2[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\ndian_Larry;ispub=1;isLog=0;hpcdp=0;tags=microphone,prank,reporter;isBreakHotShot=false;brkref=1;mar=ms-pr-breakhp;ord=442842110671576[1].3 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\reporter-gets-kissed-by-homeless-dude[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\flashtrail[3].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\pixel[10].htm 6528 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\pixel[9].htm 6533 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\6b9aae9760c9b1000bc7ac70010acfb8019c429d[1].jpg 9346 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\712708_c8237b01-3e9b-424e-b7e9-f3e7bccd566e_prod_100_thumb[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\amazing-blob-jump-launch[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\01[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\01[2].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\0a771df6b7c9d45ad777ee521e7a0a9ebba44cf8[1].jpg 7195 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\annoying-reporter-microphone-prank[1].html 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\caa87250faed5dc31507b99dd2a627db94d6e031[1].jpg 3477 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\presspause_mevio_com[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\techhippy-254849-10-26-2010[1].mp4 9232885 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\telemetry_player_vpaid_as3[1].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\GetRelatedVideos[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\getSegment[2].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\2e034baec0cc1b316b75e670c666dcd9b92315f2[1].png 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\70463f75-04d7-42ba-b132-f34b004f6ebc[1].swf 37946 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[2].htm 977 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[3].htm 986 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[4].htm 975 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\tion=site_below_header;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=728x90,728x91;;source=site;t=;tile=1;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fbf81ab14ed49506184406e1047db2300d625b6c[1].png 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\optn=64[10] 6011 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\optn=64[9] 6089 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\data_sync[1].htm 26 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\890239[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\log[8].htm 11 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\login_status[3].php 1136 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\1203020679@x15[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\StdBanner[1].js 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\signup[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\dlocation=site_above_results;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=300x250;;source=site;t=;tile=3;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\dot[2].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\ion=site_below_player;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=468x62,300x251;;source=site;t=;tile=2;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\adservercontinuation[1].aspx 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\Std_P6Champ_SuperPigN_V1_300x250_LP2_1_0_0_0_0[2].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\xumo[1].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\5210c02e309aa923727c54364d8ce1ed2ffee25e[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\get[1].xml 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\5c2801abcc621aceaa897ad3b71d8dece7c859fe[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\data_sync[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\cation=site_below_header;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=728x90,728x91;;source=site;t=;tile=1;ord=4586909198007678[1] 244 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\optn=64[9] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\log[8].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\log[9].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\DDD_15_prem_sun_9.8c_LO_RES_640x480[1].flv 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\dearprudence-256037-10-11-2010[1].mp4 9284635 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\01[3].htm 7363 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\verifyc[8] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\custom_tab2;sz=195x44;ord=8608567190596601[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[2] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[3] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[4] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[1].php 7089 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[2].php 7103 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[3].php 7147 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[4].php 7167 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\01[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\osd[1].js 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\data_sync[2].htm 26 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\2-1x1+PIXEL[1].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\8[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\adsCA4NQ9TR 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\adsCA99JY53 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\login_status[2].php 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Cookies\system@apex-ad[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Cookies\[email protected][3].txt 0 bytes
---- EOF - GMER 1.0.15 ----
Rootkit scan 2011-06-15 15:27:52
Windows 6.1.7600 Harddisk0\DR0 -> \Device\Ide\iaStor0 ST925041 rev.D005
Running: gmer.exe; Driver: C:\Users\asta\AppData\Local\Temp\pxldrpow.sys
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!ZwSaveKeyEx + 13BD 83488569 1 Byte [06]
.text ntkrnlpa.exe!KiDispatchInterrupt + 5A2 834AD092 19 Bytes [E0, 0F, BA, F0, 07, 73, 09, ...] {LOOPNZ 0x11; MOV EDX, 0x97307f0; MOV CR4, EAX; OR AL, 0x80; MOV CR4, EAX; RET ; MOV ECX, CR3}
---- User code sections - GMER 1.0.15 ----
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0031000A
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0035000A
.text C:\Program Files\Mozilla Firefox\firefox.exe[456] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 001F000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0018000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 002E000A
.text C:\Windows\system32\svchost.exe[1080] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0013000A
.text C:\Windows\system32\svchost.exe[1080] ole32.dll!CoCreateInstance 75F2590C 5 Bytes JMP 0062000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!GetCursorPos 7774C198 5 Bytes JMP 0063000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!GetForegroundWindow 7775565D 5 Bytes JMP 0128000A
.text C:\Windows\system32\svchost.exe[1080] USER32.dll!WindowFromPoint 77776D0C 5 Bytes JMP 0127000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 00B4000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 00B5000A
.text C:\Windows\Explorer.EXE[1804] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 00AF000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 018D000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0194000A
.text C:\Windows\system32\wuauclt.exe[2800] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0038000A
.text C:\Program Files\Mozilla Firefox\plugin-container.exe[3128] USER32.dll!TrackPopupMenu 77774B3B 4 Bytes JMP 63A2C334 C:\Program Files\Mozilla Firefox\xul.dll (Mozilla Foundation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 0023000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 0067000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 0022000A
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!CreateWindowExW 77750E51 5 Bytes JMP 6EFB8197 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxIndirectParamW 77774AA7 5 Bytes JMP 6F0DFED8 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxParamW 7777564A 5 Bytes JMP 6EED4BA7 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxParamA 7778CF6A 5 Bytes JMP 6F0DFE75 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!DialogBoxIndirectParamA 7778D29C 5 Bytes JMP 6F0DFF3B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxIndirectA 7779E8C9 5 Bytes JMP 6F0DFE0A C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxIndirectW 7779E9C3 5 Bytes JMP 6F0DFD9F C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxExA 7779EA29 5 Bytes JMP 6F0DFD3D C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[7872] USER32.dll!MessageBoxExW 7779EA4D 5 Bytes JMP 6F0DFCDB C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!NtProtectVirtualMemory 77AB51C0 5 Bytes JMP 01E6000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!NtWriteVirtualMemory 77AB5D40 5 Bytes JMP 01E7000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ntdll.dll!KiUserExceptionDispatcher 77AB6298 5 Bytes JMP 01E5000A
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!UnhookWindowsHookEx 7774CC7B 5 Bytes JMP 6EFC83A2 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!CallNextHookEx 7774CC8F 5 Bytes JMP 6EFA9D94 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!CreateWindowExW 77750E51 5 Bytes JMP 6EFB8197 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!SetWindowsHookExW 7775210A 5 Bytes JMP 6EF6463B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxIndirectParamW 77774AA7 5 Bytes JMP 6F0DFED8 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxParamW 7777564A 5 Bytes JMP 6EED4BA7 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxParamA 7778CF6A 5 Bytes JMP 6F0DFE75 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!DialogBoxIndirectParamA 7778D29C 5 Bytes JMP 6F0DFF3B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxIndirectA 7779E8C9 5 Bytes JMP 6F0DFE0A C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxIndirectW 7779E9C3 5 Bytes JMP 6F0DFD9F C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxExA 7779EA29 5 Bytes JMP 6F0DFD3D C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] USER32.dll!MessageBoxExW 7779EA4D 5 Bytes JMP 6F0DFCDB C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ole32.dll!OleLoadFromStream 75ED5BF6 5 Bytes JMP 6F0E022B C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\iexplore.exe[8288] ole32.dll!CoCreateInstance 75F2590C 5 Bytes JMP 6EFB8C85 C:\Windows\system32\IEFRAME.dll (Internet Browser/Microsoft Corporation)
---- Devices - GMER 1.0.15 ----
Device \Driver\ACPI_HAL \Device\00000056 halmacpi.dll (Hardware Abstraction Layer DLL/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume1 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume2 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume3 fvevol.sys (BitLocker Drive Encryption Driver/Microsoft Corporation)
AttachedDevice \Driver\volmgr \Device\HarddiskVolume3 rdyboost.sys (ReadyBoost Driver/Microsoft Corporation)
AttachedDevice \FileSystem\fastfat \Fat fltmgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
---- Registry - GMER 1.0.15 ----
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}\Connection@Name isatap.{84BF6E8C-0D53-46DD-B5AD-2123B351536A}
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Bind \Device\{0625E7DE-F3CE-4BE5-9689-709BD77B190E}?\Device\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}?\Device\{935ECB00-6D14-45D0-A207-1C341BCEDE84}?\Device\{2B98EE92-59C7-43B3-8385-F15E083FC314}?
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Route "{0625E7DE-F3CE-4BE5-9689-709BD77B190E}"?"{5C409518-4135-4204-A8F0-BDEFBE2C09B6}"?"{935ECB00-6D14-45D0-A207-1C341BCEDE84}"?"{2B98EE92-59C7-43B3-8385-F15E083FC314}"?
Reg HKLM\SYSTEM\CurrentControlSet\Control\Network\{4d36e975-e325-11ce-bfc1-08002be10318}\{6B683E0E-1505-488C-8053-3C1301924246}\Linkage@Export \Device\TCPIP6TUNNEL_{0625E7DE-F3CE-4BE5-9689-709BD77B190E}?\Device\TCPIP6TUNNEL_{5C409518-4135-4204-A8F0-BDEFBE2C09B6}?\Device\TCPIP6TUNNEL_{935ECB00-6D14-45D0-A207-1C341BCEDE84}?\Device\TCPIP6TUNNEL_{2B98EE92-59C7-43B3-8385-F15E083FC314}?
Reg HKLM\SYSTEM\CurrentControlSet\services\iphlpsvc\Parameters\Isatap\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}@InterfaceName isatap.{84BF6E8C-0D53-46DD-B5AD-2123B351536A}
Reg HKLM\SYSTEM\CurrentControlSet\services\iphlpsvc\Parameters\Isatap\{5C409518-4135-4204-A8F0-BDEFBE2C09B6}@ReusableType 0
---- Disk sectors - GMER 1.0.15 ----
Disk \Device\Harddisk0\DR0 TDL4@MBR code has been found <-- ROOTKIT !!!
Disk \Device\Harddisk0\DR0 sector 00: rootkit-like behavior
---- Files - GMER 1.0.15 ----
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\female-reporter-gets-hit-with-ball[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\50c38b7cd25873c0d4ce412639d12a43f4d670a8[1].jpg 6058 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\adsCA6B5CKW 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\toppicks[3] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\ponsored=0;nickname=Indian_Larry;ispub=1;isLog=0;hpcdp=0;tags=microphone,prank,reporter;brkref=1;mar=ms-pr-breakhp;ord=442842110671576[1].3 62 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\611704_067cb090-87e3-4f6d-b23b-9c2b67b3bcf9_prod_1_0001_thumb[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\spanish-reporter-ruins-sand-castle2[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\ndian_Larry;ispub=1;isLog=0;hpcdp=0;tags=microphone,prank,reporter;isBreakHotShot=false;brkref=1;mar=ms-pr-breakhp;ord=442842110671576[1].3 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\reporter-gets-kissed-by-homeless-dude[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\flashtrail[3].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\pixel[10].htm 6528 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\pixel[9].htm 6533 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\6b9aae9760c9b1000bc7ac70010acfb8019c429d[1].jpg 9346 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\712708_c8237b01-3e9b-424e-b7e9-f3e7bccd566e_prod_100_thumb[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\amazing-blob-jump-launch[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\01[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\01[2].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\0a771df6b7c9d45ad777ee521e7a0a9ebba44cf8[1].jpg 7195 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\annoying-reporter-microphone-prank[1].html 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\caa87250faed5dc31507b99dd2a627db94d6e031[1].jpg 3477 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\presspause_mevio_com[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\techhippy-254849-10-26-2010[1].mp4 9232885 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\telemetry_player_vpaid_as3[1].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\GetRelatedVideos[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0HBR4O75\getSegment[2].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\2e034baec0cc1b316b75e670c666dcd9b92315f2[1].png 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\70463f75-04d7-42ba-b132-f34b004f6ebc[1].swf 37946 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[2].htm 977 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[3].htm 986 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fw-nonplayer-banner[4].htm 975 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\tion=site_below_header;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=728x90,728x91;;source=site;t=;tile=1;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\fbf81ab14ed49506184406e1047db2300d625b6c[1].png 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\optn=64[10] 6011 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\optn=64[9] 6089 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\data_sync[1].htm 26 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\890239[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\log[8].htm 11 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\login_status[3].php 1136 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\1203020679@x15[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\StdBanner[1].js 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\signup[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\dlocation=site_above_results;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=300x250;;source=site;t=;tile=3;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\dot[2].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\ion=site_below_player;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=468x62,300x251;;source=site;t=;tile=2;ord=3033303410576728[1].5 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\adservercontinuation[1].aspx 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\Std_P6Champ_SuperPigN_V1_300x250_LP2_1_0_0_0_0[2].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\xumo[1].swf 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\5210c02e309aa923727c54364d8ce1ed2ffee25e[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2REKI3X9\get[1].xml 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\5c2801abcc621aceaa897ad3b71d8dece7c859fe[1].jpg 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\data_sync[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\cation=site_below_header;dcopt=ist;campaign=;page=category;kw=blinkx;pid=10;sz=728x90,728x91;;source=site;t=;tile=1;ord=4586909198007678[1] 244 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\optn=64[9] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\log[8].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\log[9].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\DDD_15_prem_sun_9.8c_LO_RES_640x480[1].flv 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\dearprudence-256037-10-11-2010[1].mp4 9284635 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\01[3].htm 7363 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EAYOPKOV\verifyc[8] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\custom_tab2;sz=195x44;ord=8608567190596601[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[2] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[3] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\ads[4] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[1].php 7089 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[2].php 7103 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[3].php 7147 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\like[4].php 7167 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\01[1].htm 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\osd[1].js 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\data_sync[2].htm 26 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\2-1x1+PIXEL[1].gif 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\8[1] 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\adsCA4NQ9TR 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\adsCA99JY53 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ULXW4KKY\login_status[2].php 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Cookies\system@apex-ad[1].txt 0 bytes
File C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Cookies\[email protected][3].txt 0 bytes
---- EOF - GMER 1.0.15 ----
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

