Internet works on the infected computer.
Uncertain of What I Have - Redirects, WinPatrol Popups
#31

 Posted 01 November 2011 - 04:46 PM
Posted 01 November 2011 - 04:46 PM

Internet works on the infected computer.
#32

 Posted 02 November 2011 - 01:43 PM
Posted 02 November 2011 - 01:43 PM

We need to check to see what files are locked:
We need to scan the system with this special tool:
- Please download and save:
Junction.zip
- Unzip it and place Junction.exe in the Windows directory (C:\Windows).
- Go to Start => Run... => Copy and paste the following command in the Run box and click OK
cmd /c junction -s c:\ >log.txt&log.txt& del log.txt
A command window opens starting to scan the system. Wait until a log file opens. Copy and paste the log in your next reply.
#33

 Posted 02 November 2011 - 10:24 PM
Posted 02 November 2011 - 10:24 PM

Copyright © 2000-2010 Mark Russinovich
Sysinternals - www.sysinternals.com
Failed to open \\?\c:\\hiberfil.sys: The process cannot access the file because it is being used by another process.
Failed to open \\?\c:\\pagefile.sys: The process cannot access the file because it is being used by another process.
...
...
..
Failed to open \\?\c:\\Documents and Settings\Talg\Desktop\OTL.com: Access is denied.
Failed to open \\?\c:\\Documents and Settings\Talg\Desktop\OTL.exe: Access is denied.
Failed to open \\?\c:\\Documents and Settings\Talg\Desktop\OTL.scr: Access is denied.
Failed to open \\?\c:\\Documents and Settings\Talg\Desktop\rkill.exe: Access is denied.
.
...
...
...
...
...
...
...
...
...
...
...
...
Failed to open \\?\c:\\Program Files\SUPERAntiSpyware\SUPERANTISPYWARE.EXE: Access is denied.
..
Failed to open \\?\c:\\Qoobox\BackEnv: Access is denied.
.
...
...
...
...
...
...
...
...
...
.\\?\c:\\WINDOWS\assembly\GAC_32\System.EnterpriseServices\2.0.0.0__b03f5f7f11d50a3a: JUNCTION
Print Name : C:\WINDOWS\WinSxS\x86_System.EnterpriseServices_b03f5f7f11d50a3a_2.0.0.0_x-ww_7d5f3790
Substitute Name: C:\WINDOWS\WinSxS\x86_System.EnterpriseServices_b03f5f7f11d50a3a_2.0.0.0_x-ww_7d5f3790
\\?\c:\\WINDOWS\assembly\GAC_MSIL\IEExecRemote\2.0.0.0__b03f5f7f11d50a3a: JUNCTION
Print Name : C:\WINDOWS\WinSxS\MSIL_IEExecRemote_b03f5f7f11d50a3a_2.0.0.0_x-ww_6e57c34e
Substitute Name: C:\WINDOWS\WinSxS\MSIL_IEExecRemote_b03f5f7f11d50a3a_2.0.0.0_x-ww_6e57c34e
..
...
...
...
...
...
...
...
...
...
...
..
Failed to open \\?\c:\\WINDOWS\system32\MRT.exe: Access is denied.
.
...
...
#34

 Posted 03 November 2011 - 12:49 PM
Posted 03 November 2011 - 12:49 PM

Can you please do the following:
Step 1:
Please download GrantPerms.zip and save it to your desktop.
Unzip the file and depending on the system run GrantPerms.exe
Copy and paste the following in the edit box:
c:\\Documents and Settings\Talg\Desktop\OTL.com
c:\\Documents and Settings\Talg\Desktop\OTL.exe
c:\\Documents and Settings\Talg\Desktop\OTL.scr
c:\\Documents and Settings\Talg\Desktop\rkill.exe
c:\\Program Files\SUPERAntiSpyware\SUPERANTISPYWARE.EXE
c:\\Qoobox\BackEnv
c:\\WINDOWS\system32\MRT.exe
Click Unlock. When it is done click "OK".
Click List Permissions and post the result (Perms.txt) that pops up. A copy of Perms.txt will be saved in the same directory the tool is run.
Step 2:
Please run a free online scan with the ESET Online Scanner
Note: You will need to use Internet Explorer for this scan
- Tick the box next to YES, I accept the Terms of Use
- Click Start
- When asked, allow the ActiveX control to install
- Click Start
- Make sure that the options Remove found threats and the option Scan unwanted applications is checked
- Click Scan (This scan can take several hours, so please be patient)
- Once the scan is completed, you may close the window
- Use Notepad to open the logfile located at C:\Program Files\EsetOnlineScanner\log.txt
- Copy and paste that log as a reply to this topic
Homburg
#35

 Posted 04 November 2011 - 12:55 PM
Posted 04 November 2011 - 12:55 PM

Ran by Talg at 2011-11-04 09:01:41
===============================================
\\?\c:\\Documents and Settings\Talg\Desktop\OTL.com
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
\\?\c:\\Documents and Settings\Talg\Desktop\OTL.exe
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
\\?\c:\\Documents and Settings\Talg\Desktop\OTL.scr
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
\\?\c:\\Documents and Settings\Talg\Desktop\rkill.exe
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
\\?\c:\\Program Files\SUPERAntiSpyware\SUPERANTISPYWARE.EXE
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
\\?\c:\\Qoobox\BackEnv
Owner: BUILTIN\Administrators
DACL(NP)(AI):
BUILTIN\Administrators FULL ALLOW (CI)(OI)(I)
NT AUTHORITY\SYSTEM FULL ALLOW (CI)(OI)(I)
CREATOR OWNER FULL ALLOW (CI)(OI)(IO)(I)
BUILTIN\Users READ/EXECUTE ALLOW (CI)(OI)(I)
BUILTIN\Users ADD SUBDIRECTORY ALLOW (CI)(I)
BUILTIN\Users ADD FILE ALLOW (CI)(I)
\\?\c:\\WINDOWS\system32\MRT.exe
Owner: BUILTIN\Administrators
DACL(P)(AI):
BUILTIN\Administrators FULL ALLOW (NI)
NT AUTHORITY\SYSTEM FULL ALLOW (NI)
BUILTIN\Users READ/EXECUTE ALLOW (NI)
ESETSmartInstaller@High as CAB hook log:
OnlineScanner.ocx - registred OK
# version=7
# iexplore.exe=8.00.6001.18702 (longhorn_ie8_rtm(wmbla).090308-0339)
# OnlineScanner.ocx=1.0.0.6583
# api_version=3.0.2
# EOSSerial=cf908f46a0f4db46bd12ced09c4e2d47
# end=finished
# remove_checked=true
# archives_checked=false
# unwanted_checked=true
# unsafe_checked=false
# antistealth_checked=true
# utc_time=2011-11-04 02:16:38
# local_time=2011-11-04 10:16:38 (-0500, Eastern Daylight Time)
# country="United States"
# lang=1033
# osver=5.1.2600 NT Service Pack 3
# compatibility_mode=512 16777215 100 0 62701488 62701488 0 0
# compatibility_mode=768 16777215 100 0 50131403 50131403 0 0
# compatibility_mode=8192 67108863 100 0 61747651 61747651 0 0
# scanned=71592
# found=87
# cleaned=87
# scan_time=3709
C:\Qoobox\Quarantine\C\Program Files\Intel\Wireless\Bin\EvtEng.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\Program Files\Intel\Wireless\Bin\RegSrvc.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\Program Files\Intel\Wireless\Bin\S24EvMon.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\Program Files\Java\jre6\bin\jqs.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\Program Files\Sony\VAIO Event Service\VESMgr.exe.vir Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\WINDOWS\assembly\GAC_MSIL\desktop.ini.vir a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\Qoobox\Quarantine\C\WINDOWS\system32\rasapubw.dll.vir a variant of Win32/Kryptik.BQR trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP221\A0082144.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP222\A0082214.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP222\A0082215.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP223\A0082307.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP223\A0082308.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP223\A0083323.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP223\A0083324.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084326.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084327.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084343.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084344.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084366.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP224\A0084367.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0084393.rbf Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0084502.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0084503.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0084523.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0084524.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0085526.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP225\A0085527.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP232\A0085800.rbf Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP233\A0085909.rbf Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086308.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086309.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086380.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086393.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086395.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086396.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086417.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086418.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086444.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086445.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086457.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP235\A0086458.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP236\A0086552.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP236\A0086553.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086572.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086573.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086593.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086594.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086622.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0086623.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0087622.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0087623.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0088622.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP237\A0088623.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088636.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088637.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088656.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088657.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088670.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP238\A0088671.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP239\A0088693.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP239\A0088694.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0089693.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0089694.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090693.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090694.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090706.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090707.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090720.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090721.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090770.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090771.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090787.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090788.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090800.sys Win32/Rootkit.Agent.NUT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP240\A0090801.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090837.ini a variant of Win32/Sirefef.CH trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090876.dll a variant of Win32/Kryptik.BQR trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090942.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090943.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090944.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090945.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090946.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\System Volume Information\_restore{54C72960-2267-4872-93F9-556BF4397A54}\RP241\A0090947.exe Win32/Patched.HN trojan (cleaned - quarantined) 00000000000000000000000000000000 C
C:\_OTL\MovedFiles\10072011_090508\C_WINDOWS\246875462:3120187633.exe Win32/Sirefef.CT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\_OTL\MovedFiles\10072011_091712\C_WINDOWS\246875462:3120187633.exe Win32/Sirefef.CT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
C:\_OTL\MovedFiles\10072011_092947\C_WINDOWS\246875462:3120187633.exe Win32/Sirefef.CT trojan (cleaned by deleting - quarantined) 00000000000000000000000000000000 C
#36

 Posted 05 November 2011 - 07:00 AM
Posted 05 November 2011 - 07:00 AM

Your PC is now clean
First we'll remove the tools that we've used then look at preventing getting infected again. It's important to remove the tools as it also removes the malware that we currently have quarantined.
Please do the following:
Clean up with OTL:
- Leave OTL.exe on your desktop and delete the others
- Double-click OTL.exe to start the program.
- On the OTL main screen, depress the CleanUp button.
- Say Yes to the prompt and then allow the program to reboot your computer.
Follow these steps to uninstall Combofix
- Please press the Windows Key and R on your keyboard. This will bring up the Run... command.
- Now copy/paste this: ComboFix /Uninstall in the runbox and click OK. Note the space between the X and the /Uninstall, it needs to be there.
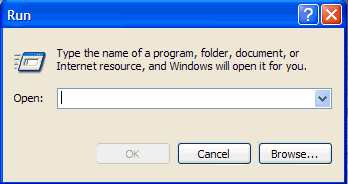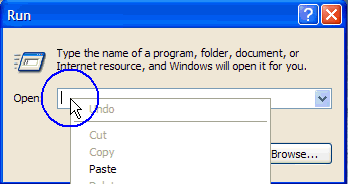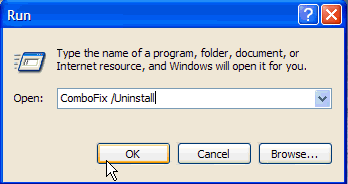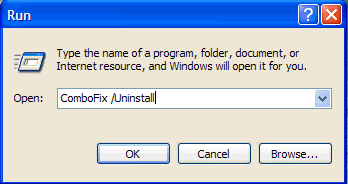
- Please follow the prompts to uninstall Combofix.
- This will uninstall Combofix, delete its related folders and files, reset your clock settings, hide file extensions, hide the system/hidden files and resets System Restore again.
- You will then receive a message saying Combofix was uninstalled successfully once it's done uninstalling itself.
Please delete aswMBR and any remaining logs from your desktop.
Windows Updates.
It is essential that you regularly check and install the latest Windows Updates. Vulnerabilities within Windows can leave your computer open to infection. Regular updates are released to fix these security vulnerabilities. I recommend that you set Windows to check, download and install your updates automatically.
Click Start
Select Control Panel
Click on Automatic (recommended)
Set the day and time for the update check. Set this to a time when your computer will normally be on and connected to the internet.
Click Apply then OK.
JAVA updates.
As with Windows, Java also needs to be regularly updated to fix security vulnerabilities. You can download the latest version of the Java Runtime Environment (JRE) from here. Download, install and reboot your computer. You also need to uininstall older versions of Java.
Click Start
Select Control Panel
Select Add or Remove Programs
Remove all Java updates except the latest one you have just installed.
Adobe updates.
You should ensure you use the latest Adobe Acrobat Reader and install any security updates that are released. Older versions are susceptible to attack. You can download the latest reader and updates from here.
To learn more about how to protect yourself while on the internet you might like to read this GeeksToGo article. This covers some of the safety measures that I've included and also some more.
Happy surfing and stay safe
Homburg.
#37

 Posted 06 November 2011 - 07:43 PM
Posted 06 November 2011 - 07:43 PM

#38

 Posted 14 November 2011 - 01:42 PM
Posted 14 November 2011 - 01:42 PM

If you're the topic starter, and need this topic reopened, please contact a staff member with the address of the thread.
Everyone else please begin a New Topic.
Similar Topics
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

