HELP! My computer won't let me download ANYTHING [Closed]
Started by
Tomc82d
, Oct 15 2013 06:34 AM
#1
![HELP! My computer won't let me download ANYTHING [Closed]: post #1](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 15 October 2013 - 06:34 AM
Posted 15 October 2013 - 06:34 AM

#2
![HELP! My computer won't let me download ANYTHING [Closed]: post #2](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 16 October 2013 - 09:36 AM
Posted 16 October 2013 - 09:36 AM

Greetings,
Welcome to Geeks to Go--the friendliest online community dedicated to the sole goal of helping people from all around the world!
I am Pyxis and I will be assisting you with the problem at hand. Whilst I am taking the time to analyse your set of provided logs, I would like to stress the following reminders:

Thank you.
Welcome to Geeks to Go--the friendliest online community dedicated to the sole goal of helping people from all around the world!
I am Pyxis and I will be assisting you with the problem at hand. Whilst I am taking the time to analyse your set of provided logs, I would like to stress the following reminders:
- I am a student that is currently undergoing training. As such, my responses have to be checked by a professional before I present them to you to ensure you get the best quality help. If you deem I have overlooked your thread, which is in a matter of more than 24 hours, please send me a PM and I will get back to you shortly.
- It is important that you do not install anything unless asked while the process is ongoing. Doing so may hinder or even complicate the cleaning of your system. You will get the chance to install things as you would like after the process has been completed.
- Ensure you take extra caution to precisely follow my instructions. It is important that you only use the tools I have asked you to. The instructions for your computer are unique and should therefore only apply to your system.
Thank you.
#3
![HELP! My computer won't let me download ANYTHING [Closed]: post #3](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 16 October 2013 - 09:45 PM
Posted 16 October 2013 - 09:45 PM

Hi Tomc82d,
That sounds like the ZeroAccess infection. Do you have a spare flash drive and computer where you can prepare the below for me?
'32-bit'
'64-bit'
That sounds like the ZeroAccess infection. Do you have a spare flash drive and computer where you can prepare the below for me?
- Step 1
'32-bit'
'64-bit'
- Plug the flash drive into the infected computer.
- Simply double-click the program icon to run it. It will ask for administrator privileges. If the first one you tried does not work, try the other version.
- The program will initialize. Press Yes to accept the disclaimer.

- Press the Scan button.
- It will produce a log (FRST.txt) on the flash drive once done. Additionally, Addition.txt would be included if this is your first time running it.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log(s) back here.
- Logs to Post
- Addition.txt (Farbar Recovery Scan Tool)
- FRST.txt (Farbar Recovery Scan Tool)
#4
![HELP! My computer won't let me download ANYTHING [Closed]: post #4](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 October 2013 - 12:28 AM
Posted 17 October 2013 - 12:28 AM

This is the only .txt file that appeared.
Attached Files
#5
![HELP! My computer won't let me download ANYTHING [Closed]: post #5](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 18 October 2013 - 10:00 AM
Posted 18 October 2013 - 10:00 AM

Do you mind if I ask you to kindly recheck whether or not the flash drive really only contains that? If you do not still see it, please follow the steps below in order to produce it.
- Step 1
- Reboot with the flash drive plugged in.
- Press and hold the F8 key immediately. You should do so before the Windows logo comes up.
- If successful, you will see the Advanced Boot Options screen like below. Use the arrow keys to choose Repair Your Computer. Press Enter after.

- Select US as the keyboard setting and click Next.
- Select the operating system you want to repair (Windows 7), and then click Next.
- Select your user account if prompted and click Next. You will then see the following:
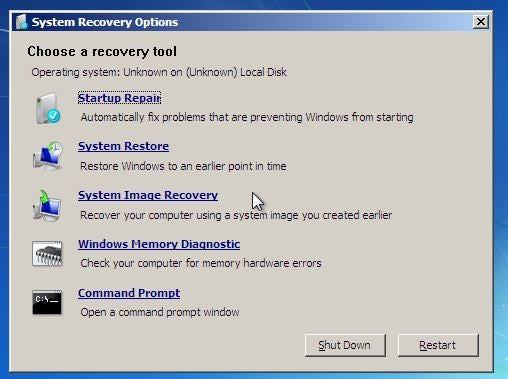
- Select Command Prompt.
- In the black command window, type notepad and press Enter.
- Notepad will pop-up. Select File > Open... > Computer.
- Keep in mind the drive letter assigned to your flash drive. Close Notepad.
- Back at the command window, type Z:\frst64 ("Z" should be replaced with your flash drive's letter) and press Enter.
- When Farbar Recovery Scan Tool opens click Yes. Ensure the settings below are followed.

- Press Scan after.
- It will produce a log (FRST.txt) on the flash drive once done. Reboot and turn off your computer.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Logs to Post
- FRST.txt (Farbar Recovery Scan Tool)
#7
![HELP! My computer won't let me download ANYTHING [Closed]: post #7](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 19 October 2013 - 10:12 AM
Posted 19 October 2013 - 10:12 AM

Awesome. Allow me to get my fix checked by my professor. It won't take long.
#8
![HELP! My computer won't let me download ANYTHING [Closed]: post #8](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 19 October 2013 - 11:17 AM
Posted 19 October 2013 - 11:17 AM

If this goes well, you will be able to download files normally after the first step. There remains a lot to be cleaned after, however, so let's get started.  Please be reminded that the below steps should be done in normal mode (the usual way, and not the way I asked you to do so earlier).
Please be reminded that the below steps should be done in normal mode (the usual way, and not the way I asked you to do so earlier).
 fixlist.txt 182bytes
305 downloads
fixlist.txt 182bytes
305 downloads
- Step 1
 fixlist.txt 182bytes
305 downloads
fixlist.txt 182bytes
305 downloads- Simply double-click the program icon to run it. It will ask for administrator privileges.
- When Farbar Recovery Scan Tool opens click Yes.

- Press Fix after.
- It will produce a log (fixlog.txt) on the flash drive once done. Reboot your computer.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Step 2
- Simply double-click the program icon to run it. It will ask for administrator privileges.
- Click Scan and choose Clean after.
- Wait for it to finish. It won't take long.
- Click OK for the next prompts. Your system will automatically reboot.
- A log will automatically pop-up after rebooting. Alternatively, you can find it at C:\AdwCleaner[S*].txt.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Step 3
- Simply double-click the program icon to run it. It will ask for administrator privileges.

- Copy and paste the following into the Custom Scans/Fixes box:
netsvcs BASESERVICES %SYSTEMDRIVE%\*.exe c:\program files (x86)\Google\Desktop c:\program files\Google\Desktop dir "%systemdrive%\*" /S /A:L /C /md5start services.* explorer.exe Userinit.exe svchost.exe /md5stop CREATERESTOREPOINT
- Click Run Scan.
- Files are being searched and it may take some time. Once done, two Notepad windows will appear, named OTL.txt and Extras.txt. Alternatively, you can also find these at your desktop.
- Copy and paste (CTRL + A and CTRL + C) the content of these logs in your next reply.
- Logs to Post
- AdwCleaner[S*].txt (AdwCleaner)
- Extras.txt (OTL)
- fixlog.txt (Farbar Recovery Scan Tool)
- OTL.txt (OTL)
#9
![HELP! My computer won't let me download ANYTHING [Closed]: post #9](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 19 October 2013 - 01:40 PM
Posted 19 October 2013 - 01:40 PM

Next set.
Attached Files
#10
![HELP! My computer won't let me download ANYTHING [Closed]: post #10](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 October 2013 - 10:05 AM
Posted 20 October 2013 - 10:05 AM

Looks like we have quite a lot to do. Most of these are automatic, so you can listen to music or do something else while you wait for each one to finish.  I believe you are able to download normally now, but the infection you acquired is one of the nastiest one in the wild. As such, please carefully read my warning below.
I believe you are able to download normally now, but the infection you acquired is one of the nastiest one in the wild. As such, please carefully read my warning below.
Below are the steps that you should administer:
- Warning
Below are the steps that you should administer:
- Disconnect from the Internet immediately and do not use it unless requested to and until we finish the cleaning process. This is especially true when you are using the computer in question for online banking and other sites that require sensitive and personal information.
- Using a clean and private computer, change your passwords that concern accounts like PayPal, Amazon, banks and other personal accounts. The password(s) for your e-mail account(s) should also be modified.
- How do I respond to possible identity theft, or to someone stealing my credit card or bank account number?
- When should I re-format? How should I reinstall?
- Step 1
- Simply double-click the program icon to run it. It will ask for administrator privileges.

- Copy and paste the following into the Custom Scans/Fixes box:
:OTL [2013/01/21 14:10:45 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\xhfqkibm.exe [2013/01/20 10:11:38 | 000,046,117 | ---- | C] () -- C:\Users\Owner\AppData\Local\sahjdmuc [2013/01/20 09:30:47 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\tuvspajb.exe [2013/01/20 09:28:11 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\kibnmxta.exe [2013/01/20 09:26:34 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\ntmvsnsv.exe [2013/01/20 09:24:51 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\jotqftps.exe [2013/01/20 09:23:15 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\hdsnopvm.exe [2013/01/20 09:21:08 | 000,000,001 | ---- | C] () -- C:\Users\Owner\AppData\Local\lihnerlq.exe [2010/04/08 01:26:21 | 000,099,384 | ---- | C] () -- C:\Users\Owner\AppData\Roaming\inst.exe [2007/11/07 08:03:18 | 000,562,688 | ---- | M] (Microsoft Corporation) -- C:\install.exe @Alternate Data Stream - 376 bytes -> C:\ProgramData\Temp:D4EEFCC4 @Alternate Data Stream - 376 bytes -> C:\ProgramData\Temp:214562D2 @Alternate Data Stream - 202 bytes -> C:\ProgramData\Temp:41C283B2 @Alternate Data Stream - 133 bytes -> C:\ProgramData\Temp:0B4227B4 @Alternate Data Stream - 122 bytes -> C:\ProgramData\Temp:A8ADE5D8 @Alternate Data Stream - 121 bytes -> C:\ProgramData\Temp:DFC5A2B2 @Alternate Data Stream - 120 bytes -> C:\ProgramData\Temp:75EFCFC2 @Alternate Data Stream - 119 bytes -> C:\ProgramData\Temp:411E1BE2 @Alternate Data Stream - 113 bytes -> C:\ProgramData\Temp:B9AB561D @Alternate Data Stream - 109 bytes -> C:\ProgramData\Temp:C1F4198F :Commands [emptytemp]
- Click Run Fix.
- OTL will reboot your system. Allow it by clicking OK.
- After a the reboot, a Notepad window will appear, named MMDDYYYY_HHMMSS.log. Alternatively, you can find that log at C:\_OTL\MovedFiles\MMDDYYYY_HHMMSS.log.
- Copy and paste (CTRL + A and CTRL + C) the content of that log in your next reply.
- Step 2
- Double-click the file. It will ask for administrator privileges. Allow it by clicking Yes.
- You will be asked to confirm. Press Yes to continue.
- Once done, you will be asked to reboot. Press Yes once more.
- Step 3
- Double-click TDSSKiller.exe to run it. It will ask for administrator privileges.
- Click Start Scan to begin the scan.
- If an infected file is detected, the default action will be Cure, click on Continue.
- If a suspicious file is detected, the default action will be Skip, click on Continue.
- It may ask you to reboot the computer to complete the process. Click on Reboot Now. If not, click Close.
- The log will be made available at C:\TDSSKiller.*_*_*_log.txt. Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Step 4
- Ensure the following options are checked:
Internet Services
Windows Firewall
System Restore
Windows Update
Windows Defender
- Ensure the following options are checked:
- Press Scan.
- A log will pop-up once done. Alternatively, you can find FSS.txt at your desktop.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Step 5
- Simply double-click the program icon to run it. It will ask for administrator privileges.
- Ensure that the following settings are followed. Make sure all other windows are closed and let it run uninterrupted.

- Click Run Scan.
- After a short while, two Notepad windows will appear, named OTL.txt and Extras.txt. Alternatively, you can also find these at your desktop.
- Copy and paste (CTRL + A and CTRL + C) the content of these logs in your next reply.
- Logs to Post
- MMDDYYYY_HHMMSS.log (OTL)
- Extras.txt (OTL)
- OTL.txt (OTL)
- FSS.txt (Farbar Service Scanner)
- TDSSKiller.*_*_*_log.txt (TDSSKiller)
#11
![HELP! My computer won't let me download ANYTHING [Closed]: post #11](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 October 2013 - 03:59 PM
Posted 20 October 2013 - 03:59 PM

Next list.
Attached Files
#12
![HELP! My computer won't let me download ANYTHING [Closed]: post #12](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 October 2013 - 08:09 AM
Posted 21 October 2013 - 08:09 AM

A few more unwanted files left and your system will be a happy bunny. 
ArcadeFrontier
AVG SafeGuard Toolbar
Coupon Printer for Windows
Homepage Protection
MovieTrack
Rechips Ship V1.2
SendoriInform me if you encounter problems in the removal process.
'File 1'
- Step 1
ArcadeFrontier
AVG SafeGuard Toolbar
Coupon Printer for Windows
Homepage Protection
MovieTrack
Rechips Ship V1.2
SendoriInform me if you encounter problems in the removal process.
- Step 2
- Simply double-click the program icon to run it. It will ask for administrator privileges.

- Copy and paste the following into the Custom Scans/Fixes box:
:OTL PRC - [2013/07/01 15:28:16 | 000,196,896 | ---- | M] (Sendori, Inc.) -- C:\Program Files (x86)\Sendori\SendoriUp.exe PRC - [2013/07/01 15:28:16 | 000,119,072 | ---- | M] (Sendori, Inc.) -- C:\Program Files (x86)\Sendori\SendoriSvc.exe PRC - [2013/07/01 15:28:16 | 000,083,232 | ---- | M] (Sendori, Inc.) -- C:\Program Files (x86)\Sendori\SendoriTray.exe PRC - [2013/07/01 15:28:14 | 000,022,304 | ---- | M] (sendori) -- C:\Program Files (x86)\Sendori\Sendori.Service.exe PRC - [2013/07/01 15:28:12 | 003,623,200 | ---- | M] (Sendori) -- C:\Program Files (x86)\Sendori\sndappv2.exe SRV - [2013/07/01 15:28:16 | 000,119,072 | ---- | M] (Sendori, Inc.) [Auto | Running] -- C:\Program Files (x86)\Sendori\SendoriSvc.exe -- (Application Sendori) SRV - [2013/07/01 15:28:14 | 000,022,304 | ---- | M] (sendori) [Auto | Running] -- C:\Program Files (x86)\Sendori\Sendori.Service.exe -- (Service Sendori) SRV - [2013/07/01 15:28:12 | 003,623,200 | ---- | M] (Sendori) [Auto | Running] -- C:\Program Files (x86)\Sendori\sndappv2.exe -- (sndappv2) IE:64bit: - HKLM\..\SearchScopes\{271E6FE6-9A91-4FBD-9A41-9CC8350CCFE8}: "URL" = http://www.ask.com/web?q={searchterms}&l=dis&o=ushpd IE:64bit: - HKLM\..\SearchScopes\{55A59039-4C17-4F98-8079-927417DEA22E}: "URL" = http://www.bing.com/search?q={searchTerms}&FORM=HPDTDF&pc=HPDTDF&src=IE-SearchBox IE - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://www.bing.com/search?q={searchTerms}&FORM=IE8SRC IE - HKLM\..\SearchScopes\{271E6FE6-9A91-4FBD-9A41-9CC8350CCFE8}: "URL" = http://www.ask.com/web?q={searchterms}&l=dis&o=ushpd IE - HKLM\..\SearchScopes\{55A59039-4C17-4F98-8079-927417DEA22E}: "URL" = http://www.startsearcher.com/?q={searchTerms}&src=IETB IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{15E74859-A864-4F75-94CF-6AC0BA42A851}: "URL" = http://www.mysearchresults.com/search?&c=4200&t=11&q={searchTerms} IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{472D3000-2D1C-4EEF-9073-18556B4C852D}: "URL" = http://websearch.shopathome.com?user_id=%guid&q={searchTerms} IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{55A59039-4C17-4F98-8079-927417DEA22E}: "URL" = http://www.startsearcher.com/?q={searchTerms}&src=IE IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{6461CD24-7157-4A8F-A61E-D6112344D3D7}: "URL" = http://search.conduit.com/ResultsExt.aspx?q={searchTerms}&SearchSource=4&ctid=CT3201318 IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{650B7F71-F3A0-4EC1-979D-13325C2034D1}: "URL" = http://search.yahoo.com/search?p={searchTerms}&ei=utf-8&fr=ie8 IE - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\SearchScopes\{66DBA66A-59CE-4AFE-8670-A2084D92DE60}: "URL" = http://websearch.ask.com/redirect?client=ie&tb=ORJ&o=&src=kw&q={searchTerms}&locale=&apn_ptnrs=TV&apn_dtid=OSJ000YYUS&apn_uid=85C66280-A2C5-41A0-9FBB-E98CA4133B63&apn_sauid=D399EBF5-7559-4C78-9C9A-687F5316C1C6 FF - prefs.js..browser.startup.homepage: "http://mysearch.avg.com/?cid={4F8817D4-F8BF-4AF3-B457-EE6591C44382}&mid=8495942abde0fcc918d4a6d29dba2150-e00727f5367d1996ed4e7ab040d1625d451db508&lang=en&ds=AVG&pr=fr&d=2013-01-21 09:49:49&v=17.0.1.12&pid=safeguard&sg=34&sap=hp" FF - prefs.js..extensions.enabledAddons: avg@toolbar:12.2.5.32 FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{B7082FAA-CB62-4872-9106-E42DD88EDE45}: C:\Program Files (x86)\McAfee\SiteAdvisor [2010/11/12 11:14:53 | 000,000,000 | ---D | M] [2013/08/23 14:08:02 | 000,000,000 | ---D | M] (ArcadeFrontier) -- C:\Users\Owner\AppData\Roaming\mozilla\Firefox\Profiles\q3sq8xw5.default\extensions\{1a68cbde-3e4c-4fae-bf49-af5ab9868e53} [2012/09/19 11:30:52 | 000,022,392 | ---- | M] () (No name found) -- C:\Users\Owner\AppData\Roaming\mozilla\firefox\profiles\q3sq8xw5.default\extensions\staged\[email protected] [2013/10/15 14:20:44 | 000,003,735 | ---- | M] () -- C:\Users\Owner\AppData\Roaming\mozilla\firefox\profiles\q3sq8xw5.default\searchplugins\safeguard-secure-search.xml [2012/10/19 19:18:49 | 000,248,192 | ---- | M] (Coupons, Inc.) -- C:\Program Files (x86)\mozilla firefox\plugins\npCouponPrinter.dll [2012/10/19 19:18:57 | 000,248,192 | ---- | M] (Coupons, Inc.) -- C:\Program Files (x86)\mozilla firefox\plugins\npMozCouponPrinter.dll O2:64bit: - BHO: (McAfee SiteAdvisor BHO) - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - c:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.) O2 - BHO: (ArcadeFrontier Addon) - {6C8DB2EC-499B-4897-A784-0E3186C97E9D} - C:\Users\Owner\AppData\Local\ArcadeFrontier\ArcadeFrontier.dll () O2 - BHO: (McAfee SiteAdvisor BHO) - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - c:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.) O3:64bit: - HKLM\..\Toolbar: (McAfee SiteAdvisor Toolbar) - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - c:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.) O3:64bit: - HKLM\..\Toolbar: (no name) - {7ACD7E2D-222F-46EC-B90D-C922ACD8A83A} - No CLSID value found. O3 - HKLM\..\Toolbar: (McAfee SiteAdvisor Toolbar) - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - c:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.) O3 - HKU\S-1-5-21-945422415-582677547-2944859164-1000\..\Toolbar\WebBrowser: (no name) - {3BBD3C14-4C16-4989-8366-95BC9179779D} - No CLSID value found. O4 - HKLM..\Run: [Sendori Tray] C:\Program Files (x86)\Sendori\SendoriTray.exe (Sendori, Inc.) O10 - Protocol_Catalog9\Catalog_Entries\000000000001 - C:\Windows\SysWow64\Sendori.dll (Sendori) O10 - Protocol_Catalog9\Catalog_Entries\000000000002 - C:\Windows\SysWow64\Sendori.dll (Sendori) O10 - Protocol_Catalog9\Catalog_Entries\000000000003 - C:\Windows\SysWow64\Sendori.dll (Sendori) O10 - Protocol_Catalog9\Catalog_Entries\000000000004 - C:\Windows\SysWow64\Sendori.dll (Sendori) O10 - Protocol_Catalog9\Catalog_Entries\000000000015 - C:\Windows\SysWow64\Sendori.dll (Sendori) :Files C:\Program Files (x86)\Sendori C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\apdfllckaahabafndbhieahigkjlhalf C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\apdfllckaahabafndbhieahigkjlhalf C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\peglehonblabfemopkgmfcpofbchegcl C:\Users\Owner\AppData\Local\Google\Chrome\User Data\Default\Extensions\pjkljhegncpnkpknbcohdijeoejaedia :Commands [reboot] - Click Run Fix.
- OTL will reboot your system. Allow it by clicking OK.
- After a the reboot, a Notepad window will appear, named MMDDYYYY_HHMMSS.log. Alternatively, you can find that log at C:\_OTL\MovedFiles\MMDDYYYY_HHMMSS.log.
- Copy and paste (CTRL + A and CTRL + C) the content of that log in your next reply.
- Step 3
'File 1'
- Double-click on the file to open it. Click Run and Yes after.

- Don't be afraid as it is safe. Click Yes to proceed. A confirmation prompt will come up, to which you should click OK.
- Repeat steps 1-2 as needed, depending on the number of files you were asked to download.
- Step 4
- Ensure all programs and windows are closed before proceeding.
- Simply double-click the program icon to run it. It will ask for administrator privileges.
- A black window will appear. Press any key to continue.
- Wait for it to finish. It won't take long.
- A log will automatically pop-up once done. Alternatively, you can find JRT.txt at your desktop.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Step 5
- Ensure the following options are checked:
Internet Services
Windows Firewall
System Restore
Windows Update
Windows Defender
- Ensure the following options are checked:
- Press Scan.
- A log will pop-up once done. Alternatively, you can find FSS.txt at your desktop.
- Copy (CTRL + A and CTRL + C) and paste (CTRL + V) the log back here.
- Logs to Post
- MMDDYYYY_HHMMSS.log (OTL)
- JRT.txt (Junkware Removal Tool)
- FSS.txt (Farbar Service Scanner)
#13
![HELP! My computer won't let me download ANYTHING [Closed]: post #13](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 21 October 2013 - 11:56 AM
Posted 21 October 2013 - 11:56 AM

Next list
Attached Files
#14
![HELP! My computer won't let me download ANYTHING [Closed]: post #14](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 22 October 2013 - 11:29 AM
Posted 22 October 2013 - 11:29 AM

The logs are looking great!  We've managed to get rid of ZeroAccess completely. However, I see possible system files that could have been patched. Could you check those for me by following the steps below? If my suspicions are untrue, our work would be nearing its end very soon.
We've managed to get rid of ZeroAccess completely. However, I see possible system files that could have been patched. Could you check those for me by following the steps below? If my suspicions are untrue, our work would be nearing its end very soon.
 Copy.bat 145bytes
312 downloads
Copy.bat 145bytes
312 downloads
- Step 1
 Copy.bat 145bytes
312 downloads
Copy.bat 145bytes
312 downloads- Run the file as an administrator. Click Yes once prompted to confirm.
- You will see a black pop-up window momentarily--files will appear on your desktop.
- Go to 'VirusTotal' and open a number of tabs corresponding to the number of files listed below:
afd.sys tcpip.sys
- Press the Choose File button.
- Select one of the files listed above and choose Open.
- Press the Scan it! button.
- Repeat the 4th step on the other tab(s) as necessary.
- Once the scan is finished, copy and paste the URL of the tab(s) in your next reply.
- Step 2
- Simply double-click the program icon to run it. It will ask for administrator privileges.

- Copy and paste the following into the Custom Scans/Fixes box:
/md5start afd.sys tcpip.sys /md5stop
- Click Run Scan.
- Files are being searched and it may take some time. Once done, two Notepad windows will appear, named OTL.txt and Extras.txt. Alternatively, you can also find these at your desktop.
- Copy and paste (CTRL + A and CTRL + C) the content of these logs in your next reply.
- Step 3
- Java 7 Update 25 -- Update
- Logs to Post
- Extras.txt (OTL)
- OTL.txt (OTL)
- VirusTotal URL(s) (VirusTotal)
#15
![HELP! My computer won't let me download ANYTHING [Closed]: post #15](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 22 October 2013 - 12:07 PM
Posted 22 October 2013 - 12:07 PM

Similar Topics
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

