I'm going over a couple of options with my instructor to make sure we get the last of the files off your machine. More than likely, the files it detected are files that already quarantined and are harmless. But I want to make absolutely sure.
Bad Infection, won't let me do anything [Solved]
Started by
strew1224
, Jan 07 2014 04:23 PM
#31
![Bad Infection, won't let me do anything [Solved]: post #31](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 16 January 2014 - 04:55 PM
Posted 16 January 2014 - 04:55 PM

I'm going over a couple of options with my instructor to make sure we get the last of the files off your machine. More than likely, the files it detected are files that already quarantined and are harmless. But I want to make absolutely sure.
#32
![Bad Infection, won't let me do anything [Solved]: post #32](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 January 2014 - 07:06 AM
Posted 17 January 2014 - 07:06 AM

Hello 
We're going to try an alternative scanner to root out the last of the files from your machine. Please follow the instructions below.
Scan with Panda Cloud Cleaner:
Please download Panda Cloud Cleaner and save to your desktop.
Alternate downloads are here and here.
Click on Start(Windows 7 Orb) >> All Programs >> Panda Security >> Panda Cloud Cleaner >> right-click on Uninstall Panda Cloud Cleaner and select Run as Administrator >> follow the prompts.
Things I need to see in your next post:
PCloudCleaner.txt Log
We're going to try an alternative scanner to root out the last of the files from your machine. Please follow the instructions below.
Scan with Panda Cloud Cleaner:
Please download Panda Cloud Cleaner and save to your desktop.
Alternate downloads are here and here.
- Right-click on PandaCloudCleaner.exe and select Run as Administrator >> Next > >> >> Next >
- Ensure Launch Panda Cloud Cleaner is selected >> Finish >> once the GUI(graphical user interface) appears >> click on Accept and Scan
- Please be patient as the scan may take some time to complete depending on your system's specifications.
- Once the scan has completed, if Scan finished with detections is denoted in the GUI do not take any action and or have Panda Cloud Cleaner clean absolutely anything!
- Now within the GUI click on the > tab >> then on View Report >> a notepad file should now open called PCloudCleaner.txt
- Save this to your desktop and post the contents in your next reply.
- Then click on Back >> Exit
Click on Start(Windows 7 Orb) >> All Programs >> Panda Security >> Panda Cloud Cleaner >> right-click on Uninstall Panda Cloud Cleaner and select Run as Administrator >> follow the prompts.
Things I need to see in your next post:
PCloudCleaner.txt Log
#33
![Bad Infection, won't let me do anything [Solved]: post #33](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 January 2014 - 08:27 AM
Posted 17 January 2014 - 08:27 AM

Panda Cloud results:
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\VUPI2S1H.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\JZ74MYPG.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\MQLAGI9L.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\3BGC870M.txt to be deleted.
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[HIDEFILEEXT] to be changed to: 0
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[HIDEFILEEXT] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[ANTIVIRUSDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[FIREWALLDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[UPDATESDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[ANTIVIRUSOVERRIDE] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[FIREWALLOVERRIDE] to be changed to: 0
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\VUPI2S1H.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\JZ74MYPG.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\MQLAGI9L.txt to be deleted.
Malware. FILE: C:\Users\Victoria\AppData\Roaming\MICROSOFT\Windows\Cookies\Low\3BGC870M.txt to be deleted.
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[HIDEFILEEXT] to be changed to: 0
Suspicious Policy. POLICY: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED[HIDEFILEEXT] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[ANTIVIRUSDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[FIREWALLDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[UPDATESDISABLENOTIFY] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[ANTIVIRUSOVERRIDE] to be changed to: 0
Suspicious Policy. POLICY: HKLM\SOFTWARE\MICROSOFT\SECURITY CENTER[FIREWALLOVERRIDE] to be changed to: 0
#34
![Bad Infection, won't let me do anything [Solved]: post #34](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 January 2014 - 10:02 AM
Posted 17 January 2014 - 10:02 AM

Let's run an OTL fix:
Warning: This fix is to be used on this system and this system ONLY. Using this fix on any other machine other than yours can seriously damage it.
Be advised that when the fix commences, it will shut down all running processes and you may lose the desktop and icons, they will return on reboot.
Run OTL by double clicking it (Windows Vista, Windows 7, and 8, right click and select "Run as Administrator)
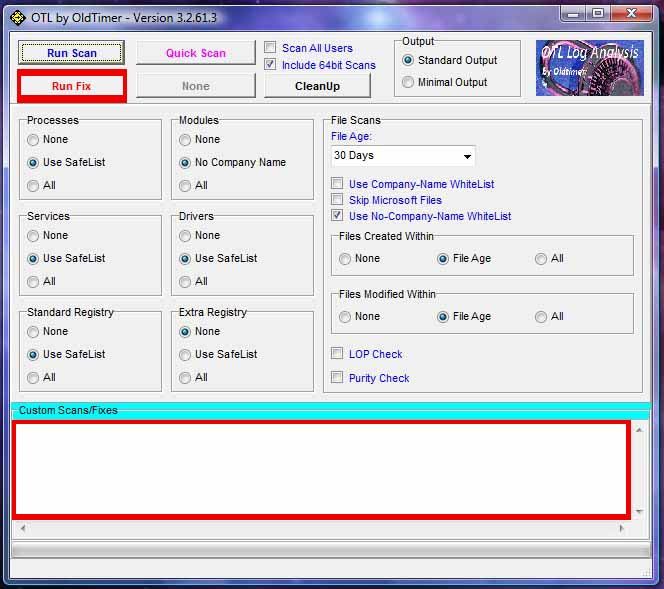
If you have any problems, questions, or need further explanation, please post a message in this thread and I will get back to you asap.
Warning: This fix is to be used on this system and this system ONLY. Using this fix on any other machine other than yours can seriously damage it.
Be advised that when the fix commences, it will shut down all running processes and you may lose the desktop and icons, they will return on reboot.
Run OTL by double clicking it (Windows Vista, Windows 7, and 8, right click and select "Run as Administrator)
- Copy the text in the quote box below (do not copy the word "quote") and paste in the in the box marked Custom Scans/Fixes as shown in the graphic below.

:Commands
[emptytemp]
[reboot]
- Click the Run Fix button at the top of the OTL control panel.
- Let the program run until it's finished and then reboot the computer.
- Once your machine has rebooted, a log will open. If the log doesn't open, you can find a copy of it here: C:\_OTL\MovedFiles Please post that log in your next reply.
If you have any problems, questions, or need further explanation, please post a message in this thread and I will get back to you asap.
#35
![Bad Infection, won't let me do anything [Solved]: post #35](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 17 January 2014 - 10:24 AM
Posted 17 January 2014 - 10:24 AM

All processes killed
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Public
User: Victoria
->Temp folder emptied: 4943518 bytes
->Temporary Internet Files folder emptied: 5821057 bytes
->Flash cache emptied: 506 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 83574 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 128 bytes
RecycleBin emptied: 39512253 bytes
Total Files Cleaned = 48.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 01172014_112125
Files\Folders moved on Reboot...
C:\Users\Victoria\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\windows\temp\FireFly(201401150950046A4).log moved successfully.
C:\windows\temp\integratedoffice.exe_c2ruidll(201401150950046A4).log moved successfully.
C:\windows\temp\integratedoffice.exe_streamserver(201401150950056A4).log moved successfully.
C:\windows\temp\UploadUI.log moved successfully.
C:\windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Public
User: Victoria
->Temp folder emptied: 4943518 bytes
->Temporary Internet Files folder emptied: 5821057 bytes
->Flash cache emptied: 506 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 83574 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 128 bytes
RecycleBin emptied: 39512253 bytes
Total Files Cleaned = 48.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 01172014_112125
Files\Folders moved on Reboot...
C:\Users\Victoria\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\windows\temp\FireFly(201401150950046A4).log moved successfully.
C:\windows\temp\integratedoffice.exe_c2ruidll(201401150950046A4).log moved successfully.
C:\windows\temp\integratedoffice.exe_streamserver(201401150950056A4).log moved successfully.
C:\windows\temp\UploadUI.log moved successfully.
C:\windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
#36
![Bad Infection, won't let me do anything [Solved]: post #36](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 18 January 2014 - 09:24 AM
Posted 18 January 2014 - 09:24 AM

Hi 
I wanted to update you and let you know that I'm awaiting approval for the last set of instructions. As soon as I get it, I'll post it for you.
I wanted to update you and let you know that I'm awaiting approval for the last set of instructions. As soon as I get it, I'll post it for you.
#37
![Bad Infection, won't let me do anything [Solved]: post #37](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 18 January 2014 - 03:05 PM
Posted 18 January 2014 - 03:05 PM

Hello 
Great news, your logs are CLEAN!
 But we still have a few things we need to address namely:
But we still have a few things we need to address namely:
Ok, here we go:
Step 1: Delete restore points and create a new one
We're going to delete your old restore points and create a new one. We do this in case you need to do a system restore, you will have a clean restore point.
Please follow the instructions below:
Step 2: Installation of Anti-Virus Program and FileHippio File Updater
I remember you saying that the subscription of Norton had expired. If you wish to renew your subscription for your anti-virus program, then by all means you can do that. However, there are several viable free AV's out there. One is Avast!
You can use Avast! for free. Once installed, you can register the software and you will be emailed a code for registration. The registration is good for a year, at which time you can renew the registration for another year.
Download Avast! Anti-Virus by clicking here.
Keeping your software updated
Another weapon against malicious programs and viruses is to keeping other programs updated. There are several programs out there that can check for out of date programs on your computer. One is Filehippo. You can run this on a weekly or monthly basis to check your programs for updates and then it will provide a link for you to download them.
Download Filehippo Updatechecker
Step 3: Tool Removal
Step 4: Tips, Information, and Protecting against CryptoLocker
Watch what you open in your emails. If you get an email from an unknown source with any attached files, do not open it.
Be careful of the websites you visit.
When installing new programs, don't be "click happy" and click through the screens. Many programs come with adware in them and are set to install them by default. Several programs require that you uncheck or select no to prevent the installation. Take you time and read each screen as you go.
To help protect yourself while on the web, I recommend you read How did I get infected in the first place?
A warning about CryptoLocker
CryptoLocker is a ransomware program that was released around the beginning of September 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 72 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Please download and install CryptoPrevent to lock your machine down from this infection.
Are there any further issues I can assist you with?
Great news, your logs are CLEAN!
- I need to remove the tools we installed on your machine.
- We need to install some security programs on your machine to reduce your chances of infection.
Ok, here we go:
Step 1: Delete restore points and create a new one
We're going to delete your old restore points and create a new one. We do this in case you need to do a system restore, you will have a clean restore point.
Please follow the instructions below:
- Start OTL and copy the text in the quote box below.
- Paste the contents into the Custom Scans/Fixes box and click the Run Fix button.
- OTL will delete the old restore points and create a new one.
:Files
%systemroot%\sysnative\vssadmin delete shadows /for=c: /all /quiet /c
:Commands
[CreateRestorePoint]
Step 2: Installation of Anti-Virus Program and FileHippio File Updater
I remember you saying that the subscription of Norton had expired. If you wish to renew your subscription for your anti-virus program, then by all means you can do that. However, there are several viable free AV's out there. One is Avast!
You can use Avast! for free. Once installed, you can register the software and you will be emailed a code for registration. The registration is good for a year, at which time you can renew the registration for another year.
Download Avast! Anti-Virus by clicking here.
Keeping your software updated
Another weapon against malicious programs and viruses is to keeping other programs updated. There are several programs out there that can check for out of date programs on your computer. One is Filehippo. You can run this on a weekly or monthly basis to check your programs for updates and then it will provide a link for you to download them.
Download Filehippo Updatechecker
Step 3: Tool Removal
- You can delete FRST from your desktop.
- You can delete aswMBR from your desktop.
- Start AdwCleaner and click the Uninstall button. It will remove the quarantined files and uninstall itself.
- You can delete SecurityCheck from your desktop.
- You can delete Junkware Removal Tool from your desktop.
- You can uninstall ESET Online Scanner at this time.
- You can delete Panda Cloud Cleaner from your desktop.
- Start OTL and click the Cleanup button. OTL will delete it's quarantined files and then uninstall itself.
- I'd recommend keeping Malwarebytes Anti-Malware installed. Make sure to update it and run it at least once a week.
Step 4: Tips, Information, and Protecting against CryptoLocker
Watch what you open in your emails. If you get an email from an unknown source with any attached files, do not open it.
Be careful of the websites you visit.
When installing new programs, don't be "click happy" and click through the screens. Many programs come with adware in them and are set to install them by default. Several programs require that you uncheck or select no to prevent the installation. Take you time and read each screen as you go.
To help protect yourself while on the web, I recommend you read How did I get infected in the first place?
A warning about CryptoLocker
CryptoLocker is a ransomware program that was released around the beginning of September 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 72 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Please download and install CryptoPrevent to lock your machine down from this infection.

Are there any further issues I can assist you with?
#38
![Bad Infection, won't let me do anything [Solved]: post #38](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 January 2014 - 08:31 AM
Posted 20 January 2014 - 08:31 AM

Thank you for your patience and your help. You did an exceptional job and I'm very appreciative of it.
#39
![Bad Infection, won't let me do anything [Solved]: post #39](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 January 2014 - 10:11 AM
Posted 20 January 2014 - 10:11 AM

Thank you for your patience and your help. You did an exceptional job and I'm very appreciative of it.
You're very welcome.
Safe surfing
Pystryker
#40
![Bad Infection, won't let me do anything [Solved]: post #40](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 20 January 2014 - 11:23 AM
Posted 20 January 2014 - 11:23 AM

Since this issue appears to be resolved ... this Topic has been closed. Glad we could help. 
If you're the topic starter, and need this topic reopened, please contact a staff member with the address of the thread.
Everyone else please begin a New Topic.
If you're the topic starter, and need this topic reopened, please contact a staff member with the address of the thread.
Everyone else please begin a New Topic.
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

