Very unusual problem [Solved]
Started by
jhn-e-bee
, Mar 21 2010 05:10 PM
#76
![Very unusual problem [Solved]: post #76](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2010 - 06:43 PM
Posted 24 March 2010 - 06:43 PM

#77
![Very unusual problem [Solved]: post #77](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2010 - 06:45 PM
Posted 24 March 2010 - 06:45 PM

How about another drwebcureit or kaspersky, it seemed to get a bit better after doing them?
#78
![Very unusual problem [Solved]: post #78](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2010 - 06:51 PM
Posted 24 March 2010 - 06:51 PM

21 infections!
Heres the log:
Malwarebytes' Anti-Malware 1.44
Database version: 3510
Windows 5.1.2600 Service Pack 2
Internet Explorer 6.0.2900.2180
3/25/2010 12:47:02 AM
mbam-log-2010-03-25 (00-47-01).txt
Scan type: Quick Scan
Objects scanned: 104581
Time elapsed: 5 minute(s), 19 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 3
Registry Values Infected: 10
Registry Data Items Infected: 2
Folders Infected: 0
Files Infected: 5
Memory Processes Infected:
C:\WINDOWS\system32\msvmcls64.exe (Net.Worm) -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ulwobcy (Worm.Conficker) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\windows hosts controller (Worm.IRCBot) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_Windows_HOSTS_CONTROLLER (Worm.Kolab) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ms virtual cls (Net.Worm) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\taskman (Trojan.Agent) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\microsoft driver setup (Worm.Palevo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\microsoft driver setup (Worm.Palevo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\intime (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\reup (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\waittokillservicet (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\c:\windows\fonts\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\asr_46864.exe (Worm.IRCBot) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\heqxdc.dll (Worm.Conficker) -> Delete on reboot.
C:\Documents and Settings\NetworkService\Local Settings\Temporary Internet Files\Content.IE5\0BMH8JUZ\mdfiyw[1].bmp (Worm.Conficker) -> Quarantined and deleted successfully.
C:\WINDOWS\Fonts\unwise_.exe (Worm.IRCBot) -> Delete on reboot.
C:\WINDOWS\system32\msvmcls64.exe (Net.Worm) -> Quarantined and deleted successfully.
Heres the log:
Malwarebytes' Anti-Malware 1.44
Database version: 3510
Windows 5.1.2600 Service Pack 2
Internet Explorer 6.0.2900.2180
3/25/2010 12:47:02 AM
mbam-log-2010-03-25 (00-47-01).txt
Scan type: Quick Scan
Objects scanned: 104581
Time elapsed: 5 minute(s), 19 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 3
Registry Values Infected: 10
Registry Data Items Infected: 2
Folders Infected: 0
Files Infected: 5
Memory Processes Infected:
C:\WINDOWS\system32\msvmcls64.exe (Net.Worm) -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ulwobcy (Worm.Conficker) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\windows hosts controller (Worm.IRCBot) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_Windows_HOSTS_CONTROLLER (Worm.Kolab) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ms virtual cls (Net.Worm) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\taskman (Trojan.Agent) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\microsoft driver setup (Worm.Palevo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\microsoft driver setup (Worm.Palevo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\intime (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\reup (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\waittokillservicet (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\c:\windows\fonts\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\asr_46864.exe (Worm.IRCBot) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\heqxdc.dll (Worm.Conficker) -> Delete on reboot.
C:\Documents and Settings\NetworkService\Local Settings\Temporary Internet Files\Content.IE5\0BMH8JUZ\mdfiyw[1].bmp (Worm.Conficker) -> Quarantined and deleted successfully.
C:\WINDOWS\Fonts\unwise_.exe (Worm.IRCBot) -> Delete on reboot.
C:\WINDOWS\system32\msvmcls64.exe (Net.Worm) -> Quarantined and deleted successfully.
#79
![Very unusual problem [Solved]: post #79](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2010 - 07:10 PM
Posted 24 March 2010 - 07:10 PM

just managed to get avg to download the files it needed, started to install and it failed after a few minutes. It gave me a report log on why it failed. let me know if that is any use to you.
Going to download avast instead as I am getting AV sites again.
I will check back in a bit, I guess you probably gone to bed. See you tommorow, Thanks.
Going to download avast instead as I am getting AV sites again.
I will check back in a bit, I guess you probably gone to bed. See you tommorow, Thanks.
#80
![Very unusual problem [Solved]: post #80](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 24 March 2010 - 07:20 PM
Posted 24 March 2010 - 07:20 PM

have successfully DL Avast and set it up. have started full scan. infection was flagged up after about 2 seconds, lets see how this goes!
#81
![Very unusual problem [Solved]: post #81](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 06:45 AM
Posted 25 March 2010 - 06:45 AM

honestly I think we may be getting near a format
do the avast, dr. web cureit, and kaspersky scans and post those logs
do the avast, dr. web cureit, and kaspersky scans and post those logs
#82
![Very unusual problem [Solved]: post #82](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 07:20 AM
Posted 25 March 2010 - 07:20 AM

Good morning(or afternoon), I sat up all night doing updates and scans. did kaspersky and avast, MBAM and left it doing dr webcureit scan. For some reason The system had gone on standby while I was asleep. when I started it was still doing the drwebcureit scan, it is very slow, I will let it finish. give me a minute and i will post the other scan results.
#83
![Very unusual problem [Solved]: post #83](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 07:29 AM
Posted 25 March 2010 - 07:29 AM

ok cool
#84
![Very unusual problem [Solved]: post #84](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 08:27 AM
Posted 25 March 2010 - 08:27 AM

this has gone really slow, drwebcureit is still going and is taking ages.
here are the logs from MBAM, avast and kaspersky. I cannot get avast as a txt file so I have taken an image, thats the only way I seem to be able to get it to you.
MBAM:
Malwarebytes' Anti-Malware 1.44
Database version: 3510
Windows 5.1.2600 Service Pack 2
Internet Explorer 6.0.2900.2180
3/25/2010 2:27:04 AM
mbam-log-2010-03-25 (02-27-04).txt
Scan type: Quick Scan
Objects scanned: 104785
Time elapsed: 5 minute(s), 49 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 1
Registry Values Infected: 6
Registry Data Items Infected: 2
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_Windows_HOSTS_CONTROLLER (Worm.Kolab) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\intime (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\reup (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\waittokillservicet (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\c:\windows\fonts\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Avast:
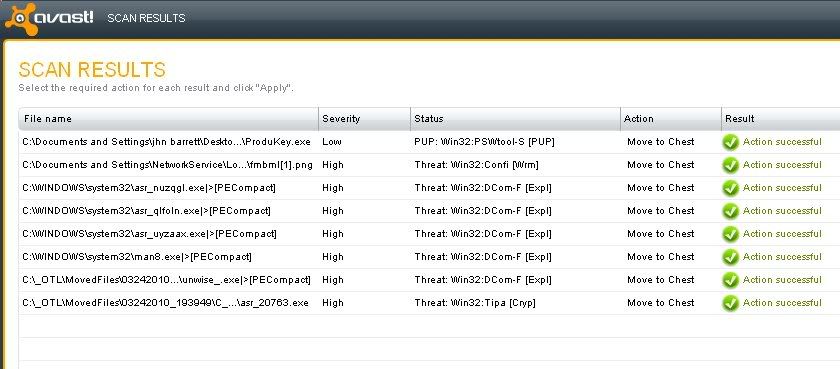
Kaspersky:
I think kaspersky deleted the log when I closed it down. I will have to do it again(it took about 2 hours too)
here are the logs from MBAM, avast and kaspersky. I cannot get avast as a txt file so I have taken an image, thats the only way I seem to be able to get it to you.
MBAM:
Malwarebytes' Anti-Malware 1.44
Database version: 3510
Windows 5.1.2600 Service Pack 2
Internet Explorer 6.0.2900.2180
3/25/2010 2:27:04 AM
mbam-log-2010-03-25 (02-27-04).txt
Scan type: Quick Scan
Objects scanned: 104785
Time elapsed: 5 minute(s), 49 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 1
Registry Values Infected: 6
Registry Data Items Infected: 2
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_Windows_HOSTS_CONTROLLER (Worm.Kolab) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\intime (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\reup (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\waittokillservicet (Malware.Trace) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\c:\windows\fonts\unwise_.exe (Trojan.Agent) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Avast:

Kaspersky:
I think kaspersky deleted the log when I closed it down. I will have to do it again(it took about 2 hours too)
#85
![Very unusual problem [Solved]: post #85](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 11:10 AM
Posted 25 March 2010 - 11:10 AM

Drwebcureit is still going(about 5 hours now). Should I carry on?
It has found a couple of infections though.
It has found a couple of infections though.
Edited by jhn-e-bee, 25 March 2010 - 11:10 AM.
#86
![Very unusual problem [Solved]: post #86](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 11:24 AM
Posted 25 March 2010 - 11:24 AM

yep carry on, sadly these scans take a while, but they the best chance of cleaning it
#87
![Very unusual problem [Solved]: post #87](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 12:21 PM
Posted 25 March 2010 - 12:21 PM

Finally:
Drwebcureit:
ComboFix.exe\32788R22FWJFW\FIND3M.bat;C:\Documents and Settings\jhn barrett\Desktop\ComboFix.exe;Probably BATCH.Virus;;
ComboFix.exe;C:\Documents and Settings\jhn barrett\Desktop;Archive contains infected objects;Moved.;
A0003866.exe;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4;BackDoor.IRC.Bot.166;Deleted.;
A0003881.exe\32788R22FWJFW\FIND3M.bat;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4\A0003881.exe;Probably BATCH.Virus;;
A0003881.exe;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4;Archive contains infected objects;Moved.;
And thats it!
Drwebcureit:
ComboFix.exe\32788R22FWJFW\FIND3M.bat;C:\Documents and Settings\jhn barrett\Desktop\ComboFix.exe;Probably BATCH.Virus;;
ComboFix.exe;C:\Documents and Settings\jhn barrett\Desktop;Archive contains infected objects;Moved.;
A0003866.exe;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4;BackDoor.IRC.Bot.166;Deleted.;
A0003881.exe\32788R22FWJFW\FIND3M.bat;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4\A0003881.exe;Probably BATCH.Virus;;
A0003881.exe;C:\System Volume Information\_restore{B1345870-9C57-4F74-84F2-0A7BFF5F33FC}\RP4;Archive contains infected objects;Moved.;
And thats it!
#88
![Very unusual problem [Solved]: post #88](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 12:26 PM
Posted 25 March 2010 - 12:26 PM

hi
Download Flash_Disinfector.exe from here and save it to your desktop.
Please download OTM
Open OTL paste this in the custom scan box
c:\windows\fonts\*.exe
c:\windows\system32\*.exe
netsvcs
click run scan post that log
Download Flash_Disinfector.exe from here and save it to your desktop.
- Double-click Flash_Disinfector.exe to run it and follow any prompts that may appear.
- The utility may ask you to insert your flash drive and/or other removable drives including your mobile phone. Please do so and allow the utility to clean up those drives as well.
- Wait until it has finished scanning and then exit the program.
- Reboot your computer when done.
Note: Flash_Disinfector will create a hidden folder named autorun.inf in each partition and every USB drive plugged in when you run it. Don't delete this folder...it will help protect your drives from future infection.
Please download OTM
- Save it to your desktop.
- Please double-click OTM to run it. (Note: If you are running on Vista, right-click on the file and choose Run As Administrator).
- Copy the lines in the codebox below to the clipboard by highlighting ALL of them and pressing CTRL + C (or, after highlighting, right-click and choose Copy):
:Processes :Services Windows Hosts Controller :Reg :Files c:\windows\fonts\*.exe c:\windows\system32\asr_*.exe c:\windows\system32\man*.exe :Commands [purity] [resethosts] [emptytemp] [CREATERESTOREPOINT] [EMPTYFLASH] [Reboot]
- Return to OTM, right click in the "Paste Instructions for Items to be Moved" window (under the yellow bar) and choose Paste.
- Click the red Moveit! button.
- Copy everything in the Results window (under the green bar) to the clipboard by highlighting ALL of them and pressing CTRL + C (or, after highlighting, right-click and choose copy), and paste it in your next reply.
- Close OTM and reboot your PC.
Open OTL paste this in the custom scan box
c:\windows\fonts\*.exe
c:\windows\system32\*.exe
netsvcs
click run scan post that log
#89
![Very unusual problem [Solved]: post #89](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 12:28 PM
Posted 25 March 2010 - 12:28 PM

starting kasp now, see you later!
#90
![Very unusual problem [Solved]: post #90](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 25 March 2010 - 12:35 PM
Posted 25 March 2010 - 12:35 PM

ok do my above post after it
Similar Topics
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked





 Sign In
Sign In Create Account
Create Account

