Good morning ... Just logged to the Server, and yes I use TeamViewer 3 for that, I got a message from Malwarebytes that it has blocked a outgoing connection to the IP [121.10.121.96] ...
2012/09/09 03:43:58 -0700 ST-SERVER st_admin IP-BLOCK 193.107.16.92 (Type: incoming)
2012/09/09 03:44:01 -0700 ST-SERVER st_admin IP-BLOCK 193.107.16.92 (Type: incoming)
2012/09/09 04:42:54 -0700 ST-SERVER st_admin IP-BLOCK 121.10.121.95 (Type: outgoing)
2012/09/09 04:42:57 -0700 ST-SERVER st_admin IP-BLOCK 121.10.121.96 (Type: outgoing)
As for your last post, here are my findings:
I don't see the User [ siweb$ ] under the list of users although their is a folder C:\Documents and Settings\siweb$
When I googled [ siweb$ ] yesterday it came back with a number of Chinese hacking web pages ...
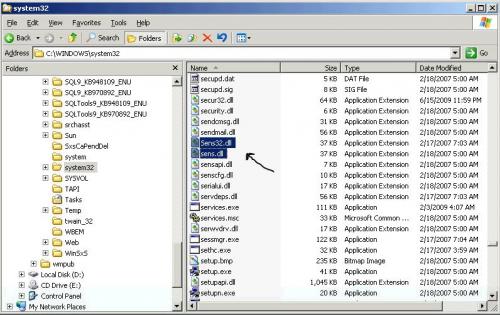
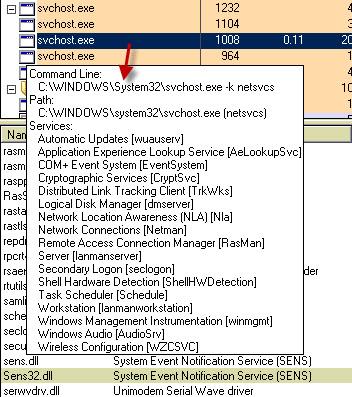
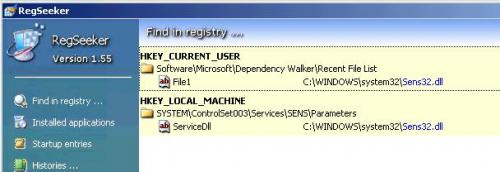
Under the bad Server their is a C:\Windows\System32\Sens32.dll with size 37Kb dated 2/17/2007 @ 7:03am
There is also a C:\Windows\System32\Sens.dll with size 37Kb dated 2/18/2007 @ 5:00am
But under the good server their is only a C:\Windows\System32\Sens.dll with size 37Kb dated 2/17/2007 @ 7:03am
As for the C:\Windows\Offline Web Pages I didn't find the file [Cache.txt] on both Servers
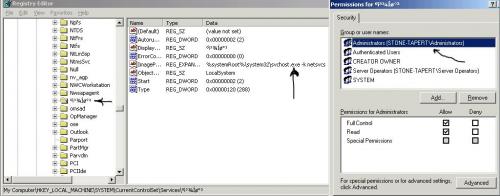
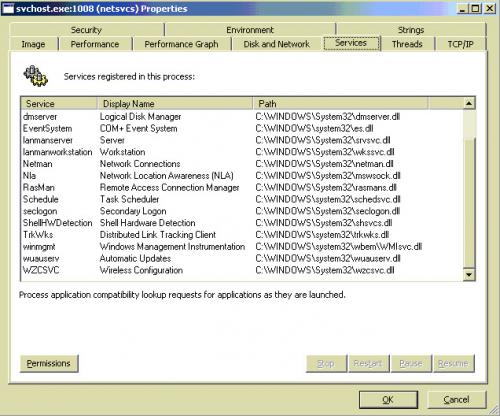
For the Bad Services, I have attached a screenshot for the permissions for one of them ...
Which services should I permanently delete under HKLM\System\CurrentControlSet\Services since I cannot do it using AutoRuns ???
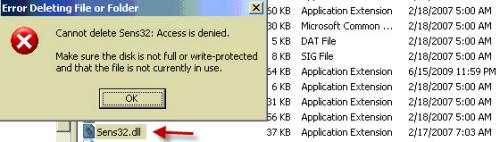
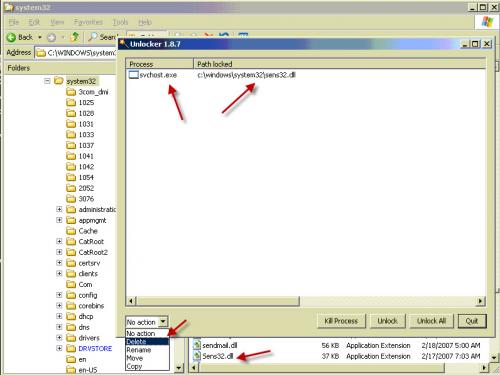
I am know fully inclined that the [Sens32.dll] is what is causing all of that ...
Let me what's next ...
Thanks,
















 Sign In
Sign In Create Account
Create Account

