Edited by stang, 09 January 2006 - 08:41 PM.

Cannot remove Trojan horse downloader generic kpw
Started by
stang
, Dec 16 2005 12:59 PM
#31

 Posted 09 January 2006 - 08:25 PM
Posted 09 January 2006 - 08:25 PM

#32

 Posted 09 January 2006 - 09:45 PM
Posted 09 January 2006 - 09:45 PM

I added the svchost file to peer guardians block list and it started blocking these ips:
Private customer – SBC Internet services 68.120.74.254:80
Private customer – SBC Internet services 192.168.0.100:1045
Can you find some info. on these ips?
I'll get back to you on changing the host file.............stang
Private customer – SBC Internet services 68.120.74.254:80
Private customer – SBC Internet services 192.168.0.100:1045
Can you find some info. on these ips?
I'll get back to you on changing the host file.............stang
#33

 Posted 10 January 2006 - 01:32 PM
Posted 10 January 2006 - 01:32 PM

192.168.0.100 is part of your Home network, probably your modem or the computer acting as internet-server
Interestingly enough the port (1045) is usually used by the Rasmin Trojan.
68.120.74.254 belongs to SBC Internet service (your provider?)
To find out about the presence of another Trojan on your computer can you do a full system scan here:
http://www.kaspersky.com/virusscanner
Let me know the results.
Regards,
Interestingly enough the port (1045) is usually used by the Rasmin Trojan.
68.120.74.254 belongs to SBC Internet service (your provider?)
To find out about the presence of another Trojan on your computer can you do a full system scan here:
http://www.kaspersky.com/virusscanner
Let me know the results.
Regards,
#34

 Posted 10 January 2006 - 08:10 PM
Posted 10 January 2006 - 08:10 PM

I've already installed kaspersky and it couldn't find anything. I would even scan the file itself and still couldn't find anything. Also my internet provider is cox.com. Is there any way to find if ithis virus has any registry files and delete them............stang
#35

 Posted 11 January 2006 - 02:21 PM
Posted 11 January 2006 - 02:21 PM

Download WinPFind.zip and unzip the contents to the C:\ folder.
In the WinPfind folder find the file called patterns.txt
Add this line to that file
svchost
So it will look for that filename inside other files as well.
Start in Safe Mode Using the F8 method:
When the scan is complete reboot normally and post the WinPFind.txt file (located in the WinPFind folder)
Regards,
In the WinPfind folder find the file called patterns.txt
Add this line to that file
svchost
So it will look for that filename inside other files as well.
Start in Safe Mode Using the F8 method:
- Restart the computer.
- As soon as the BIOS is loaded begin tapping the F8 key until the boot menu appears.
- Use the arrow keys to select the Safe Mode menu item.
- Press the Enter key.
When the scan is complete reboot normally and post the WinPFind.txt file (located in the WinPFind folder)
Regards,
#36

 Posted 11 January 2006 - 07:12 PM
Posted 11 January 2006 - 07:12 PM

WARNING: not all files found by this scanner are bad. Consult with a knowledgable person before proceeding.
If you see a message in the titlebar saying "Not responding..." you can ignore it. Windows somethimes displays this message due to the high volume of disk I/O. As long as the hard disk light is flashing, the program is still working properly.
»»»»»»»»»»»»»»»»» Windows OS and Versions »»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»
Product Name: Microsoft Windows XP Current Build: Service Pack 2 Current Build Number: 2600
Internet Explorer Version: 6.0.2900.2180
»»»»»»»»»»»»»»»»» Checking Selected Standard Folders »»»»»»»»»»»»»»»»»»»»
Checking %SystemDrive% folder...
Checking %ProgramFilesDir% folder...
Checking %WinDir% folder...
PECompact2 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
qoologic 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
SAHAgent 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
UPX! 5/3/2005 10:44:44 AM 25157 C:\WINDOWS\RMAgentOutput.dll
UPX! 1/10/2005 3:17:24 PM 170053 C:\WINDOWS\tsc.exe
PECompact2 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
qoologic 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
SAHAgent 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
UPX! 2/18/2005 5:40:14 PM 1044560 C:\WINDOWS\vsapi32.dll
aspack 2/18/2005 5:40:14 PM 1044560 C:\WINDOWS\vsapi32.dll
svchost 1/11/2006 6:48:00 PM 174476 C:\WINDOWS\WindowsUpdate.log
Checking %System% folder...
svchost 8/4/2004 1:56:42 AM 17408 C:\WINDOWS\SYSTEM32\alrsvc.dll
svchost 8/4/2004 1:56:42 AM 42496 C:\WINDOWS\SYSTEM32\audiosrv.dll
svchost 8/4/2004 1:56:42 AM 77312 C:\WINDOWS\SYSTEM32\browser.dll
UPX! 9/17/2001 1:20:02 PM 9216 C:\WINDOWS\SYSTEM32\cpuinf32.dll
PEC2 8/23/2001 6:00:00 AM 41397 C:\WINDOWS\SYSTEM32\dfrg.msc
svchost 8/4/2004 1:56:42 AM 45568 C:\WINDOWS\SYSTEM32\dnsrslvr.dll
svchost 8/4/2004 1:56:42 AM 20992 C:\WINDOWS\SYSTEM32\hid.dll
PTech 8/29/2005 1:27:12 PM 520968 C:\WINDOWS\SYSTEM32\LegitCheckControl.DLL
UPX! 5/15/2004 4:10:42 PM 75264 C:\WINDOWS\SYSTEM32\MACDec.dll
UPX! 6/19/2004 6:28:44 PM 177152 C:\WINDOWS\SYSTEM32\MonkeySource.ax
PECompact2 1/4/2006 9:41:02 PM 2827616 C:\WINDOWS\SYSTEM32\MRT.exe
aspack 1/4/2006 9:41:02 PM 2827616 C:\WINDOWS\SYSTEM32\MRT.exe
svchost 8/4/2004 1:56:44 AM 33792 C:\WINDOWS\SYSTEM32\msgsvc.dll
svchost 1/28/2005 1:44:28 PM 25088 C:\WINDOWS\SYSTEM32\MsPMSNSv.dll
svchost 8/4/2004 1:56:44 AM 245248 C:\WINDOWS\SYSTEM32\mswsock.dll
svchost 8/4/2004 1:56:44 AM 622080 C:\WINDOWS\SYSTEM32\netcfgx.dll
svchost 8/4/2004 1:56:44 AM 1708032 C:\WINDOWS\SYSTEM32\netshell.dll
svchost 8/4/2004 1:56:54 AM 36864 C:\WINDOWS\SYSTEM32\netstat.exe
aspack 8/4/2004 1:56:36 AM 708096 C:\WINDOWS\SYSTEM32\ntdll.dll
svchost 8/4/2004 1:56:44 AM 135168 C:\WINDOWS\SYSTEM32\odbcconf.dll
svchost 8/4/2004 1:56:44 AM 382464 C:\WINDOWS\SYSTEM32\qmgr.dll
Umonitor 8/4/2004 1:56:44 AM 657920 C:\WINDOWS\SYSTEM32\rasdlg.dll
svchost 8/4/2004 1:56:44 AM 59904 C:\WINDOWS\SYSTEM32\regsvc.dll
svchost 8/4/2004 1:56:44 AM 18944 C:\WINDOWS\SYSTEM32\seclogon.dll
svchost 12/7/2004 1:32:34 PM 96768 C:\WINDOWS\SYSTEM32\srvsvc.dll
svchost 8/4/2004 1:56:58 AM 14336 C:\WINDOWS\SYSTEM32\svchost.exe
svchost 12/3/2005 1:27:22 PM 15310 C:\WINDOWS\SYSTEM32\usbadpt32.dll
svchost 8/4/2004 1:56:46 AM 174592 C:\WINDOWS\SYSTEM32\w32time.dll
winsync 8/23/2001 6:00:00 AM 1309184 C:\WINDOWS\SYSTEM32\wbdbase.deu
svchost 8/4/2004 1:56:46 AM 67584 C:\WINDOWS\SYSTEM32\webclnt.dll
svchost 8/4/2004 1:56:46 AM 333312 C:\WINDOWS\SYSTEM32\wiaservc.dll
svchost 10/20/2005 9:39:30 PM 658432 C:\WINDOWS\SYSTEM32\wininet.dll
svchost 8/4/2004 1:56:46 AM 132096 C:\WINDOWS\SYSTEM32\wkssvc.dll
svchost 8/4/2004 1:56:46 AM 81408 C:\WINDOWS\SYSTEM32\wscsvc.dll
svchost 5/26/2005 3:16:30 AM 1343768 C:\WINDOWS\SYSTEM32\wuaueng.dll
svchost 5/26/2005 3:16:30 AM 194328 C:\WINDOWS\SYSTEM32\wuaueng1.dll
svchost 8/4/2004 1:56:46 AM 359936 C:\WINDOWS\SYSTEM32\wzcsvc.dll
Checking %System%\Drivers folder and sub-folders...
UPX! 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
FSG! 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
PEC2 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
aspack 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
PTech 8/3/2004 11:41:38 PM 1309184 C:\WINDOWS\SYSTEM32\drivers\mtlstrm.sys
Items found in C:\WINDOWS\SYSTEM32\drivers\etc\hosts
Checking the Windows folder and sub-folders for system and hidden files within the last 60 days...
1/11/2006 6:49:06 PM S 2048 C:\WINDOWS\bootstat.dat
12/29/2005 8:30:16 PM H 54156 C:\WINDOWS\QTFont.qfn
11/30/2005 10:17:10 PM S 21633 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB905915.cat
12/1/2005 6:12:48 PM S 10925 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB910437.cat
1/2/2006 5:09:36 PM S 11223 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB912919.cat
1/11/2006 6:48:52 PM H 8192 C:\WINDOWS\system32\config\default.LOG
1/11/2006 6:49:20 PM H 1024 C:\WINDOWS\system32\config\SAM.LOG
1/11/2006 6:49:08 PM H 12288 C:\WINDOWS\system32\config\SECURITY.LOG
1/11/2006 6:50:34 PM H 73728 C:\WINDOWS\system32\config\software.LOG
1/11/2006 6:49:16 PM H 888832 C:\WINDOWS\system32\config\system.LOG
1/10/2006 8:12:44 PM H 1024 C:\WINDOWS\system32\config\systemprofile\ntuser.dat.LOG
12/16/2005 2:37:36 PM S 1047 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\Content\7C8A03C4580C6B04FDF34357F3474EDC
12/16/2005 2:37:36 PM S 1370 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\Content\B82262A5D5DA4DDACE9EDA7F787D0DEB
12/16/2005 2:37:36 PM S 126 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\MetaData\7C8A03C4580C6B04FDF34357F3474EDC
12/16/2005 2:37:36 PM S 194 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\MetaData\B82262A5D5DA4DDACE9EDA7F787D0DEB
12/4/2005 9:29:04 PM RHS 233472 C:\WINDOWS\system32\DirectX\Dinput\Thumbs.db
12/12/2005 3:23:42 PM HS 388 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\3d929528-cf72-4ac0-ac15-bf8ea864f540
12/4/2005 9:31:16 PM HS 388 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\7c237736-4738-408c-9ddf-704c73e80119
12/12/2005 3:23:42 PM HS 24 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\Preferred
1/11/2006 6:47:56 PM H 6 C:\WINDOWS\Tasks\SA.DAT
Checking for CPL files...
8/19/2003 9:20:04 AM 180224 C:\WINDOWS\SYSTEM32\ac3filter.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\access.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 549888 C:\WINDOWS\SYSTEM32\appwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 110592 C:\WINDOWS\SYSTEM32\bthprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 135168 C:\WINDOWS\SYSTEM32\desk.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 80384 C:\WINDOWS\SYSTEM32\firewall.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155136 C:\WINDOWS\SYSTEM32\hdwwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 358400 C:\WINDOWS\SYSTEM32\inetcpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 129536 C:\WINDOWS\SYSTEM32\intl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 380416 C:\WINDOWS\SYSTEM32\irprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\joy.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 187904 C:\WINDOWS\SYSTEM32\main.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 618496 C:\WINDOWS\SYSTEM32\mmsys.cpl
Kristal Studio 3/2/2001 12:39:28 PM 121856 C:\WINDOWS\SYSTEM32\Mp3cnfg.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 35840 C:\WINDOWS\SYSTEM32\ncpa.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 25600 C:\WINDOWS\SYSTEM32\netsetup.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 257024 C:\WINDOWS\SYSTEM32\nusrmgr.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 32768 C:\WINDOWS\SYSTEM32\odbccp32.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 114688 C:\WINDOWS\SYSTEM32\powercfg.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 298496 C:\WINDOWS\SYSTEM32\sysdm.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 28160 C:\WINDOWS\SYSTEM32\telephon.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 94208 C:\WINDOWS\SYSTEM32\timedate.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 148480 C:\WINDOWS\SYSTEM32\wscui.cpl
Microsoft Corporation 5/26/2005 3:16:30 AM 174360 C:\WINDOWS\SYSTEM32\wuaucpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\dllcache\access.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 549888 C:\WINDOWS\SYSTEM32\dllcache\appwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 110592 C:\WINDOWS\SYSTEM32\dllcache\bthprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 135168 C:\WINDOWS\SYSTEM32\dllcache\desk.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 80384 C:\WINDOWS\SYSTEM32\dllcache\firewall.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155136 C:\WINDOWS\SYSTEM32\dllcache\hdwwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 358400 C:\WINDOWS\SYSTEM32\dllcache\inetcpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 129536 C:\WINDOWS\SYSTEM32\dllcache\intl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 380416 C:\WINDOWS\SYSTEM32\dllcache\irprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\dllcache\joy.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 187904 C:\WINDOWS\SYSTEM32\dllcache\main.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 618496 C:\WINDOWS\SYSTEM32\dllcache\mmsys.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 35840 C:\WINDOWS\SYSTEM32\dllcache\ncpa.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 25600 C:\WINDOWS\SYSTEM32\dllcache\netsetup.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 257024 C:\WINDOWS\SYSTEM32\dllcache\nusrmgr.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 32768 C:\WINDOWS\SYSTEM32\dllcache\odbccp32.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 114688 C:\WINDOWS\SYSTEM32\dllcache\powercfg.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155648 C:\WINDOWS\SYSTEM32\dllcache\sapi.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 298496 C:\WINDOWS\SYSTEM32\dllcache\sysdm.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 28160 C:\WINDOWS\SYSTEM32\dllcache\telephon.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 94208 C:\WINDOWS\SYSTEM32\dllcache\timedate.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 148480 C:\WINDOWS\SYSTEM32\dllcache\wscui.cpl
Microsoft Corporation 5/26/2005 3:16:30 AM 174360 C:\WINDOWS\SYSTEM32\dllcache\wuaucpl.cpl
»»»»»»»»»»»»»»»»» Checking Selected Startup Folders »»»»»»»»»»»»»»»»»»»»»
Checking files in %ALLUSERSPROFILE%\Startup folder...
6/16/2005 2:01:52 PM 675 C:\Documents and Settings\All Users\Start Menu\Programs\Startup\AdSubtract.lnk
6/7/2005 3:56:50 PM HS 84 C:\Documents and Settings\All Users\Start Menu\Programs\Startup\desktop.ini
Checking files in %ALLUSERSPROFILE%\Application Data folder...
6/7/2005 10:22:34 AM HS 62 C:\Documents and Settings\All Users\Application Data\desktop.ini
Checking files in %USERPROFILE%\Startup folder...
6/11/2005 5:54:28 PM HS 143 C:\Documents and Settings\Jay\Start Menu\Programs\Startup\desktop.ini
Checking files in %USERPROFILE%\Application Data folder...
8/26/2005 7:14:10 PM 875 C:\Documents and Settings\Jay\Application Data\AdobeDLM.log
6/7/2005 10:22:34 AM HS 62 C:\Documents and Settings\Jay\Application Data\desktop.ini
8/26/2005 7:14:10 PM 0 C:\Documents and Settings\Jay\Application Data\dm.ini
8/1/2005 1:54:34 PM 17528 C:\Documents and Settings\Jay\Application Data\GDIPFONTCACHEV1.DAT
»»»»»»»»»»»»»»»»» Checking Selected Registry Keys »»»»»»»»»»»»»»»»»»»»»»»
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\User Agent\Post Platform]
SV1 =
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved]
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved]
[HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers]
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\AVG7 Shell Extension
{9F97547E-4609-42C5-AE0C-81C61FFAEBC3} = C:\Program Files\Grisoft\AVG Free\avgse.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Offline Files
{750fdf0e-2a26-11d1-a3ea-080036587f03} = %SystemRoot%\System32\cscui.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Open With
{09799AFB-AD67-11d1-ABCD-00C04FC30936} = %SystemRoot%\system32\SHELL32.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Open With EncryptionMenu
{A470F8CF-A1E8-4f65-8335-227475AA5C46} = %SystemRoot%\system32\SHELL32.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\{a2a9545d-a0c2-42b4-9708-a0b2badd77c8}
Start Menu Pin = %SystemRoot%\system32\SHELL32.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers\AVG7 Shell Extension
{9F97547E-4609-42C5-AE0C-81C61FFAEBC3} = C:\Program Files\Grisoft\AVG Free\avgse.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\EncryptionMenu
{A470F8CF-A1E8-4f65-8335-227475AA5C46} = %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\Offline Files
{750fdf0e-2a26-11d1-a3ea-080036587f03} = %SystemRoot%\System32\cscui.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\Sharing
{f81e9010-6ea4-11ce-a7ff-00aa003ca9f6} = ntshrui.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{0D2E74C4-3C34-11d2-A27E-00C04FC30871}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{24F14F01-7B1C-11d1-838f-0000F80461CF}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{24F14F02-7B1C-11d1-838f-0000F80461CF}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{66742402-F9B9-11D1-A202-0000F81FEDEE}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{F9DB5320-233E-11D1-9F84-707F02C10627}
= C:\Program Files\Adobe\Acrobat 7.0\ActiveX\PDFShell.dll
[HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects]
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{06849E9F-C8D7-4D59-B87D-784B7D6BE0B3}
AcroIEHlprObj Class = C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB}
PCTools Site Guard =
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{B56A7D7D-6927-48C8-A975-17DF180C71AC}
PCTools Browser Monitor =
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Explorer Bars]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Explorer Bars\{4D5C8C25-D075-11d0-B416-00C04FB90376}
&Tip of the Day = %SystemRoot%\System32\shdocvw.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\ToolBar]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions\{2D663D1A-8670-49D9-A1A5-4C56B4E14E84}
ButtonText = Spyware Doctor :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions\{FB5F1910-F110-11d2-BB9E-00C04F795683}
ButtonText = Messenger : C:\Program Files\Messenger\msmsgs.exe
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars]
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{21569614-B795-46B1-85F4-E737A8DC09AD}
Shell Search Band = %SystemRoot%\system32\browseui.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{32683183-48a0-441b-a342-7c2a440a9478}
=
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{C4EE31F3-4768-11D2-BE5C-00A0C9A83DA1}
File Search Explorer Band = %SystemRoot%\system32\SHELL32.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E61-B078-11D0-89E4-00C04FC9E26E}
Favorites Band = %SystemRoot%\System32\shdocvw.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E62-B078-11D0-89E4-00C04FC9E26E}
History Band = %SystemRoot%\System32\shdocvw.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E64-B078-11D0-89E4-00C04FC9E26E}
Explorer Band = %SystemRoot%\System32\shdocvw.dll
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar]
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\ShellBrowser
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser
{01E04581-4EEE-11D0-BFE9-00AA005B4383} = &Address : %SystemRoot%\System32\browseui.dll
{0E5CBF21-D15F-11D0-8301-00AA005B4383} = &Links : %SystemRoot%\system32\SHELL32.dll
{2318C2B1-4965-11D4-9B18-009027A5CD4F} = :
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
AVG7_CC C:\PROGRA~1\Grisoft\AVGFRE~1\avgcc.exe /STARTUP
AVG7_EMC C:\PROGRA~1\Grisoft\AVGFRE~1\avgemc.exe
DellTouch C:\WINDOWS\DELLMMKB.EXE
ATIPTA C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents]
IMAIL Installed = 1
MAPI Installed = 1
MSFS Installed = 1
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
PeerGuardian C:\Program Files\PeerGuardian2\pg2.exe
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\load]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\run]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\services
Nhksrv 2
IDriverT 3
Ati HotKey Poller 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Adobe Reader Speed Launch.lnk
location Common Startup
command C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
item Adobe Reader Speed Launch
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Adobe Reader Speed Launch.lnk
backup C:\WINDOWS\pss\Adobe Reader Speed Launch.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
item Adobe Reader Speed Launch
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Adobe Reader Speed Launch.lnk
backup C:\WINDOWS\pss\Adobe Reader Speed Launch.lnkCommon Startup
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^D-Link AirPlus.lnk
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\D-Link AirPlus.lnk
backup C:\WINDOWS\pss\D-Link AirPlus.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\D-LINK~1\AirPlus.exe
item D-Link AirPlus
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\D-Link AirPlus.lnk
backup C:\WINDOWS\pss\D-Link AirPlus.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\D-LINK~1\AirPlus.exe
item D-Link AirPlus
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Microsoft Office.lnk
location Common Startup
command C:\PROGRA~1\MICROS~2\Office10\OSA.EXE -b -l
item Microsoft Office
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Microsoft Office.lnk
backup C:\WINDOWS\pss\Microsoft Office.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\MICROS~2\Office10\OSA.EXE -b -l
item Microsoft Office
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Microsoft Office.lnk
backup C:\WINDOWS\pss\Microsoft Office.lnkCommon Startup
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\AdaptecDirectCD
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item DirectCD
hkey HKLM
command C:\Program Files\Adaptec\Easy CD Creator 5\DirectCD\DirectCD.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item DirectCD
hkey HKLM
command C:\Program Files\Adaptec\Easy CD Creator 5\DirectCD\DirectCD.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\ATIPTA
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item atiptaxx
hkey HKLM
command C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item atiptaxx
hkey HKLM
command C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\MSMSGS
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item msmsgs
hkey HKCU
command "C:\Program Files\Messenger\msmsgs.exe" /background
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item msmsgs
hkey HKCU
command "C:\Program Files\Messenger\msmsgs.exe" /background
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\QuickTime Task
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item qttask
hkey HKLM
command "C:\Program Files\QuickTime\qttask.exe" -atboottime
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item qttask
hkey HKLM
command "C:\Program Files\QuickTime\qttask.exe" -atboottime
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\SideWinderTrayV4
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item SWTrayV4
hkey HKLM
command C:\PROGRA~1\MICROS~4\GAMECO~1\Common\SWTrayV4.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item SWTrayV4
hkey HKLM
command C:\PROGRA~1\MICROS~4\GAMECO~1\Common\SWTrayV4.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\state
system.ini 0
win.ini 0
bootini 2
services 2
startup 2
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\NonEnum
{BDEADF00-C265-11D0-BCED-00A0C90AB50F} = C:\PROGRA~1\COMMON~1\MICROS~1\WEBFOL~1\MSONSEXT.DLL
{6DFD7C5C-2451-11d3-A299-00C04F8EF6AF} =
{0DF44EAA-FF21-4412-828E-260A8728E7F1} =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Ratings
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Ratings\PICSRules
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
dontdisplaylastusername 0
legalnoticecaption
legalnoticetext
shutdownwithoutlogon 1
undockwithoutlogon 1
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies]
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer
NoDriveTypeAutoRun 145
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad]
PostBootReminder {7849596a-48ea-486e-8937-a2a3009f31a9} = %SystemRoot%\system32\SHELL32.dll
CDBurn {fbeb8a05-beee-4442-804e-409d6c4515e9} = %SystemRoot%\system32\SHELL32.dll
WebCheck {E6FB5E20-DE35-11CF-9C87-00AA005127ED} =
SysTray {35CEC8A3-2BE6-11D2-8773-92E220524153} = C:\WINDOWS\System32\stobject.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
UserInit = C:\WINDOWS\system32\userinit.exe,
Shell = explorer.exe
System =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\crypt32chain
= crypt32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\cryptnet
= cryptnet.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\cscdll
= cscdll.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\ScCertProp
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\Schedule
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\sclgntfy
= sclgntfy.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\SensLogn
= WlNotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\termsrv
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\wlballoon
= wlnotify.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Your Image File Name Here without a path
Debugger = ntsd -d
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows]
AppInit_DLLs
»»»»»»»»»»»»»»»»»»»»»»»» Scan Complete »»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»
WinPFind v1.4.1 - Log file written to "WinPFind.Txt" in the WinPFind folder.
Scan completed on 1/11/2006 7:02:36 PM
If you see a message in the titlebar saying "Not responding..." you can ignore it. Windows somethimes displays this message due to the high volume of disk I/O. As long as the hard disk light is flashing, the program is still working properly.
»»»»»»»»»»»»»»»»» Windows OS and Versions »»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»
Product Name: Microsoft Windows XP Current Build: Service Pack 2 Current Build Number: 2600
Internet Explorer Version: 6.0.2900.2180
»»»»»»»»»»»»»»»»» Checking Selected Standard Folders »»»»»»»»»»»»»»»»»»»»
Checking %SystemDrive% folder...
Checking %ProgramFilesDir% folder...
Checking %WinDir% folder...
PECompact2 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
qoologic 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
SAHAgent 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\lpt$vpn.917
UPX! 5/3/2005 10:44:44 AM 25157 C:\WINDOWS\RMAgentOutput.dll
UPX! 1/10/2005 3:17:24 PM 170053 C:\WINDOWS\tsc.exe
PECompact2 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
qoologic 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
SAHAgent 10/27/2005 2:06:52 PM 16232461 C:\WINDOWS\VPTNFILE.917
UPX! 2/18/2005 5:40:14 PM 1044560 C:\WINDOWS\vsapi32.dll
aspack 2/18/2005 5:40:14 PM 1044560 C:\WINDOWS\vsapi32.dll
svchost 1/11/2006 6:48:00 PM 174476 C:\WINDOWS\WindowsUpdate.log
Checking %System% folder...
svchost 8/4/2004 1:56:42 AM 17408 C:\WINDOWS\SYSTEM32\alrsvc.dll
svchost 8/4/2004 1:56:42 AM 42496 C:\WINDOWS\SYSTEM32\audiosrv.dll
svchost 8/4/2004 1:56:42 AM 77312 C:\WINDOWS\SYSTEM32\browser.dll
UPX! 9/17/2001 1:20:02 PM 9216 C:\WINDOWS\SYSTEM32\cpuinf32.dll
PEC2 8/23/2001 6:00:00 AM 41397 C:\WINDOWS\SYSTEM32\dfrg.msc
svchost 8/4/2004 1:56:42 AM 45568 C:\WINDOWS\SYSTEM32\dnsrslvr.dll
svchost 8/4/2004 1:56:42 AM 20992 C:\WINDOWS\SYSTEM32\hid.dll
PTech 8/29/2005 1:27:12 PM 520968 C:\WINDOWS\SYSTEM32\LegitCheckControl.DLL
UPX! 5/15/2004 4:10:42 PM 75264 C:\WINDOWS\SYSTEM32\MACDec.dll
UPX! 6/19/2004 6:28:44 PM 177152 C:\WINDOWS\SYSTEM32\MonkeySource.ax
PECompact2 1/4/2006 9:41:02 PM 2827616 C:\WINDOWS\SYSTEM32\MRT.exe
aspack 1/4/2006 9:41:02 PM 2827616 C:\WINDOWS\SYSTEM32\MRT.exe
svchost 8/4/2004 1:56:44 AM 33792 C:\WINDOWS\SYSTEM32\msgsvc.dll
svchost 1/28/2005 1:44:28 PM 25088 C:\WINDOWS\SYSTEM32\MsPMSNSv.dll
svchost 8/4/2004 1:56:44 AM 245248 C:\WINDOWS\SYSTEM32\mswsock.dll
svchost 8/4/2004 1:56:44 AM 622080 C:\WINDOWS\SYSTEM32\netcfgx.dll
svchost 8/4/2004 1:56:44 AM 1708032 C:\WINDOWS\SYSTEM32\netshell.dll
svchost 8/4/2004 1:56:54 AM 36864 C:\WINDOWS\SYSTEM32\netstat.exe
aspack 8/4/2004 1:56:36 AM 708096 C:\WINDOWS\SYSTEM32\ntdll.dll
svchost 8/4/2004 1:56:44 AM 135168 C:\WINDOWS\SYSTEM32\odbcconf.dll
svchost 8/4/2004 1:56:44 AM 382464 C:\WINDOWS\SYSTEM32\qmgr.dll
Umonitor 8/4/2004 1:56:44 AM 657920 C:\WINDOWS\SYSTEM32\rasdlg.dll
svchost 8/4/2004 1:56:44 AM 59904 C:\WINDOWS\SYSTEM32\regsvc.dll
svchost 8/4/2004 1:56:44 AM 18944 C:\WINDOWS\SYSTEM32\seclogon.dll
svchost 12/7/2004 1:32:34 PM 96768 C:\WINDOWS\SYSTEM32\srvsvc.dll
svchost 8/4/2004 1:56:58 AM 14336 C:\WINDOWS\SYSTEM32\svchost.exe
svchost 12/3/2005 1:27:22 PM 15310 C:\WINDOWS\SYSTEM32\usbadpt32.dll
svchost 8/4/2004 1:56:46 AM 174592 C:\WINDOWS\SYSTEM32\w32time.dll
winsync 8/23/2001 6:00:00 AM 1309184 C:\WINDOWS\SYSTEM32\wbdbase.deu
svchost 8/4/2004 1:56:46 AM 67584 C:\WINDOWS\SYSTEM32\webclnt.dll
svchost 8/4/2004 1:56:46 AM 333312 C:\WINDOWS\SYSTEM32\wiaservc.dll
svchost 10/20/2005 9:39:30 PM 658432 C:\WINDOWS\SYSTEM32\wininet.dll
svchost 8/4/2004 1:56:46 AM 132096 C:\WINDOWS\SYSTEM32\wkssvc.dll
svchost 8/4/2004 1:56:46 AM 81408 C:\WINDOWS\SYSTEM32\wscsvc.dll
svchost 5/26/2005 3:16:30 AM 1343768 C:\WINDOWS\SYSTEM32\wuaueng.dll
svchost 5/26/2005 3:16:30 AM 194328 C:\WINDOWS\SYSTEM32\wuaueng1.dll
svchost 8/4/2004 1:56:46 AM 359936 C:\WINDOWS\SYSTEM32\wzcsvc.dll
Checking %System%\Drivers folder and sub-folders...
UPX! 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
FSG! 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
PEC2 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
aspack 12/6/2005 11:40:28 AM 749600 C:\WINDOWS\SYSTEM32\drivers\avg7core.sys
PTech 8/3/2004 11:41:38 PM 1309184 C:\WINDOWS\SYSTEM32\drivers\mtlstrm.sys
Items found in C:\WINDOWS\SYSTEM32\drivers\etc\hosts
Checking the Windows folder and sub-folders for system and hidden files within the last 60 days...
1/11/2006 6:49:06 PM S 2048 C:\WINDOWS\bootstat.dat
12/29/2005 8:30:16 PM H 54156 C:\WINDOWS\QTFont.qfn
11/30/2005 10:17:10 PM S 21633 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB905915.cat
12/1/2005 6:12:48 PM S 10925 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB910437.cat
1/2/2006 5:09:36 PM S 11223 C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\KB912919.cat
1/11/2006 6:48:52 PM H 8192 C:\WINDOWS\system32\config\default.LOG
1/11/2006 6:49:20 PM H 1024 C:\WINDOWS\system32\config\SAM.LOG
1/11/2006 6:49:08 PM H 12288 C:\WINDOWS\system32\config\SECURITY.LOG
1/11/2006 6:50:34 PM H 73728 C:\WINDOWS\system32\config\software.LOG
1/11/2006 6:49:16 PM H 888832 C:\WINDOWS\system32\config\system.LOG
1/10/2006 8:12:44 PM H 1024 C:\WINDOWS\system32\config\systemprofile\ntuser.dat.LOG
12/16/2005 2:37:36 PM S 1047 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\Content\7C8A03C4580C6B04FDF34357F3474EDC
12/16/2005 2:37:36 PM S 1370 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\Content\B82262A5D5DA4DDACE9EDA7F787D0DEB
12/16/2005 2:37:36 PM S 126 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\MetaData\7C8A03C4580C6B04FDF34357F3474EDC
12/16/2005 2:37:36 PM S 194 C:\WINDOWS\system32\config\systemprofile\Application Data\Microsoft\CryptnetUrlCache\MetaData\B82262A5D5DA4DDACE9EDA7F787D0DEB
12/4/2005 9:29:04 PM RHS 233472 C:\WINDOWS\system32\DirectX\Dinput\Thumbs.db
12/12/2005 3:23:42 PM HS 388 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\3d929528-cf72-4ac0-ac15-bf8ea864f540
12/4/2005 9:31:16 PM HS 388 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\7c237736-4738-408c-9ddf-704c73e80119
12/12/2005 3:23:42 PM HS 24 C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\Preferred
1/11/2006 6:47:56 PM H 6 C:\WINDOWS\Tasks\SA.DAT
Checking for CPL files...
8/19/2003 9:20:04 AM 180224 C:\WINDOWS\SYSTEM32\ac3filter.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\access.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 549888 C:\WINDOWS\SYSTEM32\appwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 110592 C:\WINDOWS\SYSTEM32\bthprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 135168 C:\WINDOWS\SYSTEM32\desk.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 80384 C:\WINDOWS\SYSTEM32\firewall.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155136 C:\WINDOWS\SYSTEM32\hdwwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 358400 C:\WINDOWS\SYSTEM32\inetcpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 129536 C:\WINDOWS\SYSTEM32\intl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 380416 C:\WINDOWS\SYSTEM32\irprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\joy.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 187904 C:\WINDOWS\SYSTEM32\main.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 618496 C:\WINDOWS\SYSTEM32\mmsys.cpl
Kristal Studio 3/2/2001 12:39:28 PM 121856 C:\WINDOWS\SYSTEM32\Mp3cnfg.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 35840 C:\WINDOWS\SYSTEM32\ncpa.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 25600 C:\WINDOWS\SYSTEM32\netsetup.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 257024 C:\WINDOWS\SYSTEM32\nusrmgr.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 32768 C:\WINDOWS\SYSTEM32\odbccp32.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 114688 C:\WINDOWS\SYSTEM32\powercfg.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 298496 C:\WINDOWS\SYSTEM32\sysdm.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 28160 C:\WINDOWS\SYSTEM32\telephon.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 94208 C:\WINDOWS\SYSTEM32\timedate.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 148480 C:\WINDOWS\SYSTEM32\wscui.cpl
Microsoft Corporation 5/26/2005 3:16:30 AM 174360 C:\WINDOWS\SYSTEM32\wuaucpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\dllcache\access.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 549888 C:\WINDOWS\SYSTEM32\dllcache\appwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 110592 C:\WINDOWS\SYSTEM32\dllcache\bthprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 135168 C:\WINDOWS\SYSTEM32\dllcache\desk.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 80384 C:\WINDOWS\SYSTEM32\dllcache\firewall.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155136 C:\WINDOWS\SYSTEM32\dllcache\hdwwiz.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 358400 C:\WINDOWS\SYSTEM32\dllcache\inetcpl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 129536 C:\WINDOWS\SYSTEM32\dllcache\intl.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 380416 C:\WINDOWS\SYSTEM32\dllcache\irprops.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 68608 C:\WINDOWS\SYSTEM32\dllcache\joy.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 187904 C:\WINDOWS\SYSTEM32\dllcache\main.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 618496 C:\WINDOWS\SYSTEM32\dllcache\mmsys.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 35840 C:\WINDOWS\SYSTEM32\dllcache\ncpa.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 25600 C:\WINDOWS\SYSTEM32\dllcache\netsetup.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 257024 C:\WINDOWS\SYSTEM32\dllcache\nusrmgr.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 32768 C:\WINDOWS\SYSTEM32\dllcache\odbccp32.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 114688 C:\WINDOWS\SYSTEM32\dllcache\powercfg.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 155648 C:\WINDOWS\SYSTEM32\dllcache\sapi.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 298496 C:\WINDOWS\SYSTEM32\dllcache\sysdm.cpl
Microsoft Corporation 8/23/2001 6:00:00 AM 28160 C:\WINDOWS\SYSTEM32\dllcache\telephon.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 94208 C:\WINDOWS\SYSTEM32\dllcache\timedate.cpl
Microsoft Corporation 8/4/2004 1:56:58 AM 148480 C:\WINDOWS\SYSTEM32\dllcache\wscui.cpl
Microsoft Corporation 5/26/2005 3:16:30 AM 174360 C:\WINDOWS\SYSTEM32\dllcache\wuaucpl.cpl
»»»»»»»»»»»»»»»»» Checking Selected Startup Folders »»»»»»»»»»»»»»»»»»»»»
Checking files in %ALLUSERSPROFILE%\Startup folder...
6/16/2005 2:01:52 PM 675 C:\Documents and Settings\All Users\Start Menu\Programs\Startup\AdSubtract.lnk
6/7/2005 3:56:50 PM HS 84 C:\Documents and Settings\All Users\Start Menu\Programs\Startup\desktop.ini
Checking files in %ALLUSERSPROFILE%\Application Data folder...
6/7/2005 10:22:34 AM HS 62 C:\Documents and Settings\All Users\Application Data\desktop.ini
Checking files in %USERPROFILE%\Startup folder...
6/11/2005 5:54:28 PM HS 143 C:\Documents and Settings\Jay\Start Menu\Programs\Startup\desktop.ini
Checking files in %USERPROFILE%\Application Data folder...
8/26/2005 7:14:10 PM 875 C:\Documents and Settings\Jay\Application Data\AdobeDLM.log
6/7/2005 10:22:34 AM HS 62 C:\Documents and Settings\Jay\Application Data\desktop.ini
8/26/2005 7:14:10 PM 0 C:\Documents and Settings\Jay\Application Data\dm.ini
8/1/2005 1:54:34 PM 17528 C:\Documents and Settings\Jay\Application Data\GDIPFONTCACHEV1.DAT
»»»»»»»»»»»»»»»»» Checking Selected Registry Keys »»»»»»»»»»»»»»»»»»»»»»»
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\User Agent\Post Platform]
SV1 =
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved]
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved]
[HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers]
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\AVG7 Shell Extension
{9F97547E-4609-42C5-AE0C-81C61FFAEBC3} = C:\Program Files\Grisoft\AVG Free\avgse.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Offline Files
{750fdf0e-2a26-11d1-a3ea-080036587f03} = %SystemRoot%\System32\cscui.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Open With
{09799AFB-AD67-11d1-ABCD-00C04FC30936} = %SystemRoot%\system32\SHELL32.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\Open With EncryptionMenu
{A470F8CF-A1E8-4f65-8335-227475AA5C46} = %SystemRoot%\system32\SHELL32.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\{a2a9545d-a0c2-42b4-9708-a0b2badd77c8}
Start Menu Pin = %SystemRoot%\system32\SHELL32.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers\AVG7 Shell Extension
{9F97547E-4609-42C5-AE0C-81C61FFAEBC3} = C:\Program Files\Grisoft\AVG Free\avgse.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\EncryptionMenu
{A470F8CF-A1E8-4f65-8335-227475AA5C46} = %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\Offline Files
{750fdf0e-2a26-11d1-a3ea-080036587f03} = %SystemRoot%\System32\cscui.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\Sharing
{f81e9010-6ea4-11ce-a7ff-00aa003ca9f6} = ntshrui.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Directory\shellex\ContextMenuHandlers\WinRAR
{B41DB860-8EE4-11D2-9906-E49FADC173CA} = C:\Program Files\WinRAR\rarext.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers]
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{0D2E74C4-3C34-11d2-A27E-00C04FC30871}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{24F14F01-7B1C-11d1-838f-0000F80461CF}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{24F14F02-7B1C-11d1-838f-0000F80461CF}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{66742402-F9B9-11D1-A202-0000F81FEDEE}
= %SystemRoot%\system32\SHELL32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Folder\shellex\ColumnHandlers\{F9DB5320-233E-11D1-9F84-707F02C10627}
= C:\Program Files\Adobe\Acrobat 7.0\ActiveX\PDFShell.dll
[HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects]
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{06849E9F-C8D7-4D59-B87D-784B7D6BE0B3}
AcroIEHlprObj Class = C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB}
PCTools Site Guard =
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{B56A7D7D-6927-48C8-A975-17DF180C71AC}
PCTools Browser Monitor =
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Explorer Bars]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Explorer Bars\{4D5C8C25-D075-11d0-B416-00C04FB90376}
&Tip of the Day = %SystemRoot%\System32\shdocvw.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\ToolBar]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions\{2D663D1A-8670-49D9-A1A5-4C56B4E14E84}
ButtonText = Spyware Doctor :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions\{FB5F1910-F110-11d2-BB9E-00C04F795683}
ButtonText = Messenger : C:\Program Files\Messenger\msmsgs.exe
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars]
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{21569614-B795-46B1-85F4-E737A8DC09AD}
Shell Search Band = %SystemRoot%\system32\browseui.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{32683183-48a0-441b-a342-7c2a440a9478}
=
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{C4EE31F3-4768-11D2-BE5C-00A0C9A83DA1}
File Search Explorer Band = %SystemRoot%\system32\SHELL32.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E61-B078-11D0-89E4-00C04FC9E26E}
Favorites Band = %SystemRoot%\System32\shdocvw.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E62-B078-11D0-89E4-00C04FC9E26E}
History Band = %SystemRoot%\System32\shdocvw.dll
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Explorer Bars\{EFA24E64-B078-11D0-89E4-00C04FC9E26E}
Explorer Band = %SystemRoot%\System32\shdocvw.dll
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar]
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\ShellBrowser
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser
{01E04581-4EEE-11D0-BFE9-00AA005B4383} = &Address : %SystemRoot%\System32\browseui.dll
{0E5CBF21-D15F-11D0-8301-00AA005B4383} = &Links : %SystemRoot%\system32\SHELL32.dll
{2318C2B1-4965-11D4-9B18-009027A5CD4F} = :
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
AVG7_CC C:\PROGRA~1\Grisoft\AVGFRE~1\avgcc.exe /STARTUP
AVG7_EMC C:\PROGRA~1\Grisoft\AVGFRE~1\avgemc.exe
DellTouch C:\WINDOWS\DELLMMKB.EXE
ATIPTA C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents]
IMAIL Installed = 1
MAPI Installed = 1
MSFS Installed = 1
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
PeerGuardian C:\Program Files\PeerGuardian2\pg2.exe
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\load]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\run]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\services
Nhksrv 2
IDriverT 3
Ati HotKey Poller 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Adobe Reader Speed Launch.lnk
location Common Startup
command C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
item Adobe Reader Speed Launch
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Adobe Reader Speed Launch.lnk
backup C:\WINDOWS\pss\Adobe Reader Speed Launch.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
item Adobe Reader Speed Launch
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Adobe Reader Speed Launch.lnk
backup C:\WINDOWS\pss\Adobe Reader Speed Launch.lnkCommon Startup
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^D-Link AirPlus.lnk
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\D-Link AirPlus.lnk
backup C:\WINDOWS\pss\D-Link AirPlus.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\D-LINK~1\AirPlus.exe
item D-Link AirPlus
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\D-Link AirPlus.lnk
backup C:\WINDOWS\pss\D-Link AirPlus.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\D-LINK~1\AirPlus.exe
item D-Link AirPlus
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Microsoft Office.lnk
location Common Startup
command C:\PROGRA~1\MICROS~2\Office10\OSA.EXE -b -l
item Microsoft Office
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Microsoft Office.lnk
backup C:\WINDOWS\pss\Microsoft Office.lnkCommon Startup
location Common Startup
command C:\PROGRA~1\MICROS~2\Office10\OSA.EXE -b -l
item Microsoft Office
path C:\Documents and Settings\All Users\Start Menu\Programs\Startup\Microsoft Office.lnk
backup C:\WINDOWS\pss\Microsoft Office.lnkCommon Startup
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\AdaptecDirectCD
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item DirectCD
hkey HKLM
command C:\Program Files\Adaptec\Easy CD Creator 5\DirectCD\DirectCD.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item DirectCD
hkey HKLM
command C:\Program Files\Adaptec\Easy CD Creator 5\DirectCD\DirectCD.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\ATIPTA
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item atiptaxx
hkey HKLM
command C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item atiptaxx
hkey HKLM
command C:\Program Files\ATI Technologies\ATI Control Panel\atiptaxx.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\MSMSGS
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item msmsgs
hkey HKCU
command "C:\Program Files\Messenger\msmsgs.exe" /background
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item msmsgs
hkey HKCU
command "C:\Program Files\Messenger\msmsgs.exe" /background
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\QuickTime Task
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item qttask
hkey HKLM
command "C:\Program Files\QuickTime\qttask.exe" -atboottime
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item qttask
hkey HKLM
command "C:\Program Files\QuickTime\qttask.exe" -atboottime
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg\SideWinderTrayV4
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item SWTrayV4
hkey HKLM
command C:\PROGRA~1\MICROS~4\GAMECO~1\Common\SWTrayV4.exe
inimapping 0
key SOFTWARE\Microsoft\Windows\CurrentVersion\Run
item SWTrayV4
hkey HKLM
command C:\PROGRA~1\MICROS~4\GAMECO~1\Common\SWTrayV4.exe
inimapping 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Shared Tools\MSConfig\state
system.ini 0
win.ini 0
bootini 2
services 2
startup 2
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\NonEnum
{BDEADF00-C265-11D0-BCED-00A0C90AB50F} = C:\PROGRA~1\COMMON~1\MICROS~1\WEBFOL~1\MSONSEXT.DLL
{6DFD7C5C-2451-11d3-A299-00C04F8EF6AF} =
{0DF44EAA-FF21-4412-828E-260A8728E7F1} =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Ratings
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Ratings\PICSRules
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
dontdisplaylastusername 0
legalnoticecaption
legalnoticetext
shutdownwithoutlogon 1
undockwithoutlogon 1
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies]
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer
NoDriveTypeAutoRun 145
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad]
PostBootReminder {7849596a-48ea-486e-8937-a2a3009f31a9} = %SystemRoot%\system32\SHELL32.dll
CDBurn {fbeb8a05-beee-4442-804e-409d6c4515e9} = %SystemRoot%\system32\SHELL32.dll
WebCheck {E6FB5E20-DE35-11CF-9C87-00AA005127ED} =
SysTray {35CEC8A3-2BE6-11D2-8773-92E220524153} = C:\WINDOWS\System32\stobject.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
UserInit = C:\WINDOWS\system32\userinit.exe,
Shell = explorer.exe
System =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\crypt32chain
= crypt32.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\cryptnet
= cryptnet.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\cscdll
= cscdll.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\ScCertProp
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\Schedule
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\sclgntfy
= sclgntfy.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\SensLogn
= WlNotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\termsrv
= wlnotify.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\wlballoon
= wlnotify.dll
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Your Image File Name Here without a path
Debugger = ntsd -d
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows]
AppInit_DLLs
»»»»»»»»»»»»»»»»»»»»»»»» Scan Complete »»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»»
WinPFind v1.4.1 - Log file written to "WinPFind.Txt" in the WinPFind folder.
Scan completed on 1/11/2006 7:02:36 PM
#37

 Posted 12 January 2006 - 01:49 PM
Posted 12 January 2006 - 01:49 PM

One that I don't recognize.
Please surf to:
http://virusscan.jotti.org/
and have this file scanned:
C:\WINDOWS\SYSTEM32\usbadpt32.dll
Post the results.
Regards,
Please surf to:
http://virusscan.jotti.org/
and have this file scanned:
C:\WINDOWS\SYSTEM32\usbadpt32.dll
Post the results.
Regards,
#38

 Posted 12 January 2006 - 07:24 PM
Posted 12 January 2006 - 07:24 PM

Service
Service load: 0% 100%
File: usbadpt32.dll
Status: INFECTED/MALWARE
MD5 39c970985f0e9769176bdedd4d647438
Packers detected: -
Scanner results
AntiVir Found Trojan/Drop.Small.bym
ArcaVir Found nothing
Avast Found nothing
AVG Antivirus Found nothing
BitDefender Found nothing
ClamAV Found nothing
Dr.Web Found Trojan.DownLoader.6152
F-Prot Antivirus Found nothing
Fortinet Found nothing
Kaspersky Anti-Virus Found nothing
NOD32 Found nothing
Norman Virus Control Found nothing
UNA Found nothing
VBA32 Found nothing
Service load: 0% 100%
File: usbadpt32.dll
Status: INFECTED/MALWARE
MD5 39c970985f0e9769176bdedd4d647438
Packers detected: -
Scanner results
AntiVir Found Trojan/Drop.Small.bym
ArcaVir Found nothing
Avast Found nothing
AVG Antivirus Found nothing
BitDefender Found nothing
ClamAV Found nothing
Dr.Web Found Trojan.DownLoader.6152
F-Prot Antivirus Found nothing
Fortinet Found nothing
Kaspersky Anti-Virus Found nothing
NOD32 Found nothing
Norman Virus Control Found nothing
UNA Found nothing
VBA32 Found nothing
#39

 Posted 13 January 2006 - 01:56 PM
Posted 13 January 2006 - 01:56 PM

YES. Yes. yes. 
Can you upload that s@##€4 to The Spykiller as well?
Thanks.
Let's see if we can find out how that one gets loaded.
Can you upload that s@##€4 to The Spykiller as well?
Thanks.
Let's see if we can find out how that one gets loaded.
- Download the Registry Search Tool.
- Unzip the contents of RegSrch.zip to a convenient location.
- Double-click on RegSrch.vbs.
- If you have an anti-virus installed it might prompt you about a running script. Please ignore this warning and allow the script to run.
- In the "Enter search string (case insensitive) and click OK..." box paste this string:
- usbadpt32
- Click "OK" to search the registry for that string.
- Wait for a few minutes while it completes the search.
- Click "OK" to open the results in WordPad.
- Copy and paste the entire results into your next post.
#40

 Posted 13 January 2006 - 04:16 PM
Posted 13 January 2006 - 04:16 PM

I can't reach the site.
message:
Network Error
Unable to request URL from host billsway.com:80: Host unreachable
I'll keep trying.......stang
message:
Network Error
Unable to request URL from host billsway.com:80: Host unreachable
I'll keep trying.......stang
#41

 Posted 13 January 2006 - 05:36 PM
Posted 13 January 2006 - 05:36 PM

Got it..........stang
REGEDIT4
; RegSrch.vbs © Bill James
; Registry search results for string "usbadpt32.dll" 1/13/2006 4:25:25 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
@="C:\\WINDOWS\\system32\\usbadpt32.dll"
[HKEY_USERS\S-1-5-21-1390067357-688789844-854245398-1004\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU\*]
"a"="C:\\WINDOWS\\system32\\usbadpt32.dll"
[HKEY_USERS\S-1-5-21-1390067357-688789844-854245398-1004\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU\dll]
"a"="C:\\WINDOWS\\system32\\usbadpt32.dll"
REGEDIT4
; RegSrch.vbs © Bill James
; Registry search results for string "usbadpt32.dll" 1/13/2006 4:25:25 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
@="C:\\WINDOWS\\system32\\usbadpt32.dll"
[HKEY_USERS\S-1-5-21-1390067357-688789844-854245398-1004\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU\*]
"a"="C:\\WINDOWS\\system32\\usbadpt32.dll"
[HKEY_USERS\S-1-5-21-1390067357-688789844-854245398-1004\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU\dll]
"a"="C:\\WINDOWS\\system32\\usbadpt32.dll"
#42

 Posted 14 January 2006 - 03:33 AM
Posted 14 January 2006 - 03:33 AM

Good job. 
Now use Regsearch to do another search.
This time for the CLSID of the file.
Now use Regsearch to do another search.
This time for the CLSID of the file.
- Double-click on RegSrch.vbs.
- In the "Enter search string (case insensitive) and click OK..." box paste this string:
- {00212521-4FEF-4AD3-B3AA-E0531B8DC123}
- Click "OK" to search the registry for that string.
- Wait for a few minutes while it completes the search.
- Click "OK" to open the results in WordPad.
- Copy and paste the entire results into your next post.
#43

 Posted 14 January 2006 - 06:34 PM
Posted 14 January 2006 - 06:34 PM

REGEDIT4
; RegSrch.vbs © Bill James
; Registry search results for string "{00212521-4FEF-4AD3-B3AA-E0531B8DC123}" 1/14/2006 6:31:32 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}]
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks]
"{00212521-4FEF-4AD3-B3AA-E0531B8DC123}"=""
; RegSrch.vbs © Bill James
; Registry search results for string "{00212521-4FEF-4AD3-B3AA-E0531B8DC123}" 1/14/2006 6:31:32 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}]
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks]
"{00212521-4FEF-4AD3-B3AA-E0531B8DC123}"=""
#44

 Posted 15 January 2006 - 04:20 AM
Posted 15 January 2006 - 04:20 AM

Excellent. That is where it gets started from. 
Now we should be able to get rid of this.
I made a BFU script for Adware.Alibaba and added what we need for yours.
Close as many programs as possible before you Execute this scripts, since it will reboot your computer.
Download and unzip BFUzip from http://www.merijn.org/files/bfu.zip
Run the program and click the Web button as shown here:
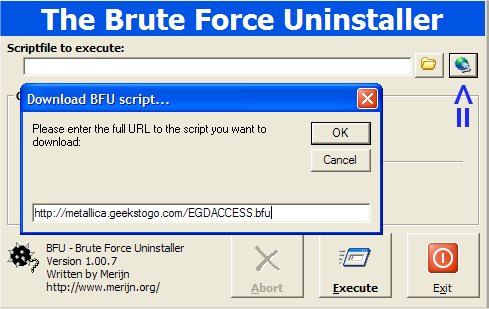
Use this URL to copy into the address bar of the Download script window:
http://metallica.geekstogo.com/alibaba.bfu
Execute the script by clicking the Execute button.
If you have any questions about the use of BFU please read here:
http://metallica.gee...structions.html
Repeat the last search you did with RegSrch so I can see if they were all removed.
Also check if all the files are gone.
Regards,
Now we should be able to get rid of this.
I made a BFU script for Adware.Alibaba and added what we need for yours.
Close as many programs as possible before you Execute this scripts, since it will reboot your computer.
Download and unzip BFUzip from http://www.merijn.org/files/bfu.zip
Run the program and click the Web button as shown here:

Use this URL to copy into the address bar of the Download script window:
http://metallica.geekstogo.com/alibaba.bfu
Execute the script by clicking the Execute button.
If you have any questions about the use of BFU please read here:
http://metallica.gee...structions.html
Repeat the last search you did with RegSrch so I can see if they were all removed.
Also check if all the files are gone.
Regards,
#45

 Posted 15 January 2006 - 05:10 PM
Posted 15 January 2006 - 05:10 PM

It looks like its still here. Should I delete the usbadpt.dll file before trying.....stang
REGEDIT4
; RegSrch.vbs © Bill James
; Registry search results for string "{00212521-4FEF-4AD3-B3AA-E0531B8DC123}" 1/15/2006 4:40:49 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}]
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks]
"{00212521-4FEF-4AD3-B3AA-E0531B8DC123}"=""
REGEDIT4
; RegSrch.vbs © Bill James
; Registry search results for string "{00212521-4FEF-4AD3-B3AA-E0531B8DC123}" 1/15/2006 4:40:49 PM
; NOTE: This file will be deleted when you close WordPad.
; You must manually save this file to a new location if you want to refer to it again later.
; (If you save the file with a .reg extension, you can use it to restore any Registry changes you make to these values.)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}]
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{00212521-4FEF-4AD3-B3AA-E0531B8DC123}\InprocServer32]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks]
"{00212521-4FEF-4AD3-B3AA-E0531B8DC123}"=""
Similar Topics
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users
As Featured On:














 Sign In
Sign In Create Account
Create Account

