Hello again
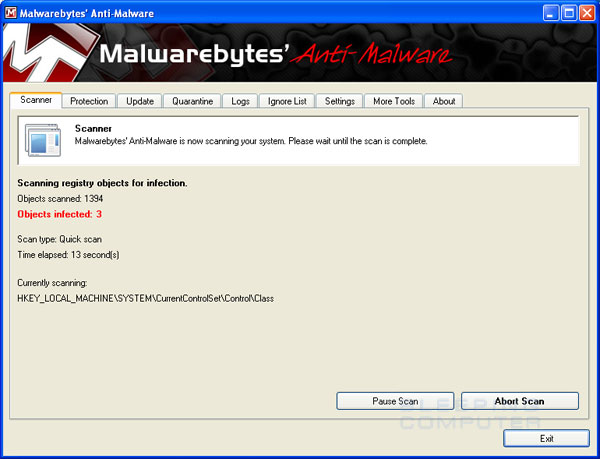
Ok, I believe Nortons controls the firewall in Windows - I have attached a screenshot of what was requested...
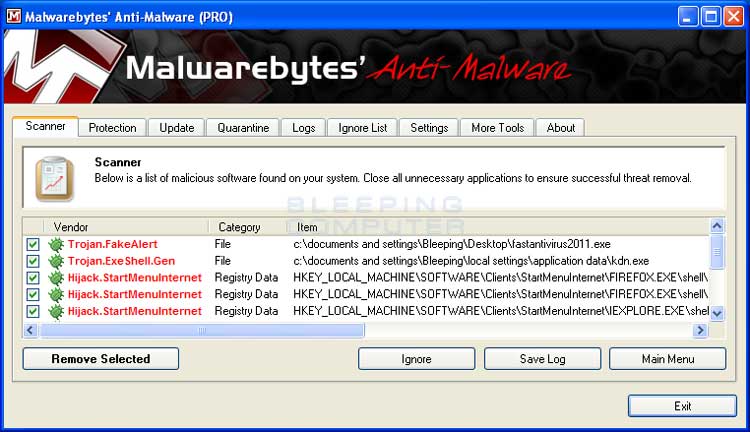
Below are the scan results;
All processes killed
========== COMMANDS ==========
Restore point Set: OTL Restore Point
========== FILES ==========
File\Folder E:\Users\User\Downloads\VLC_Setup.exe not found.
C:\Users\User\AppData\LocalLow\ChristmasHolidayLaughs_4mEI\Installr\Cache folder moved successfully.
C:\Users\User\AppData\LocalLow\ChristmasHolidayLaughs_4mEI\Installr folder moved successfully.
C:\Users\User\AppData\LocalLow\ChristmasHolidayLaughs_4mEI folder moved successfully.
E:\Users\User\Downloads\6190(1).zip moved successfully.
E:\Users\User\Downloads\freeopener.exe moved successfully.
E:\Users\User\Downloads\acrobat\7zip_installer_d394965.exe moved successfully.
E:\Users\User\Downloads\AVC Video Converter\avc-free.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Public
->Temp folder emptied: 0 bytes
User: User
->Temp folder emptied: 150243109 bytes
->Temporary Internet Files folder emptied: 262660036 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 66663320 bytes
->Google Chrome cache emptied: 0 bytes
->Apple Safari cache emptied: 0 bytes
->Flash cache emptied: 4056 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 180 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 33170 bytes
RecycleBin emptied: 409663 bytes
Total Files Cleaned = 458.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 03162013_183148
Files\Folders moved on Reboot...
C:\Users\User\AppData\Local\Temp\FXSAPIDebugLogFile.txt moved successfully.
File\Folder C:\Users\User\AppData\Local\Temp\~PI7EBA.tmp not found!
File\Folder C:\Users\User\AppData\Local\Temp\~PI7EBB.tmp not found!
File\Folder C:\Users\User\AppData\Local\Temp\~PI7FD5.tmp not found!
File\Folder C:\Users\User\AppData\Local\Temp\~PI8C55.tmp not found!
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
###############################################################################
OTL logfile created on: 16/03/2013 6:36:55 PM - Run 6
OTL by OldTimer - Version 3.2.69.0 Folder = E:\Users\User\Desktop
64bit- Ultimate Edition Service Pack 1 (Version = 6.1.7601) - Type = NTWorkstation
Internet Explorer (Version = 9.0.8112.16421)
Locale: 00000c09 | Country: Australia | Language: ENA | Date Format: d/MM/yyyy
7.98 Gb Total Physical Memory | 6.50 Gb Available Physical Memory | 81.48% Memory free
15.96 Gb Paging File | 14.42 Gb Available in Paging File | 90.36% Paging File free
Paging file location(s): ?:\pagefile.sys [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\Windows | %ProgramFiles% = C:\Program Files (x86)
Drive C: | 1862.92 Gb Total Space | 1810.79 Gb Free Space | 97.20% Space Free | Partition Type: NTFS
Drive D: | 12.93 Mb Total Space | 0.00 Mb Free Space | 0.00% Space Free | Partition Type: UDF
Drive E: | 931.43 Gb Total Space | 798.58 Gb Free Space | 85.74% Space Free | Partition Type: NTFS
Computer Name: USER-PC | User Name: User | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: Current user | Quick Scan | Include 64bit Scans
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ========== PRC - [2013/03/10 20:33:17 | 000,109,784 | ---- | M] (Siber Systems) -- C:\Program Files (x86)\Siber Systems\AI RoboForm\robotaskbaricon.exe
PRC - [2013/03/09 13:19:55 | 000,602,112 | ---- | M] (OldTimer Tools) -- E:\Users\User\Desktop\OTL.exe
PRC - [2013/01/31 10:38:54 | 003,289,208 | ---- | M] (Skype Technologies S.A.) -- C:\ProgramData\Skype\Toolbars\Skype C2C Service\c2c_service.exe
PRC - [2013/01/08 12:55:20 | 000,161,536 | R--- | M] (Skype Technologies) -- C:\Program Files (x86)\Skype\Updater\Updater.exe
PRC - [2012/12/24 14:33:29 | 000,144,520 | R--- | M] (Symantec Corporation) -- C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\ccsvchst.exe
PRC - [2012/12/19 01:28:08 | 000,065,192 | ---- | M] (Adobe Systems Incorporated) -- C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe
PRC - [2012/10/23 20:47:48 | 002,848,168 | ---- | M] (TeamViewer GmbH) -- C:\Program Files (x86)\TeamViewer\Version7\TeamViewer_Service.exe
PRC - [2011/10/01 08:30:22 | 000,219,496 | ---- | M] (Microsoft Corporation) -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftvsa.exe
PRC - [2011/10/01 08:30:18 | 000,508,776 | ---- | M] (Microsoft Corporation) -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftlist.exe
PRC - [2011/09/02 12:41:33 | 000,273,528 | ---- | M] (RealNetworks, Inc.) -- C:\Program Files (x86)\Real\RealPlayer\Update\realsched.exe
PRC - [2011/08/19 20:26:50 | 000,450,848 | ---- | M] (Logitech Inc.) -- C:\Program Files (x86)\Common Files\logishrd\LVMVFM\UMVPFSrv.exe
PRC - [2009/01/26 15:31:10 | 001,153,368 | ---- | M] (Safer Networking Ltd.) -- C:\Program Files (x86)\Spybot - Search & Destroy\SDWinSec.exe
PRC - [2008/09/16 13:03:18 | 000,169,312 | ---- | M] (Adobe Systems Incorporated) -- C:\Program Files (x86)\Adobe\Photoshop Elements 7.0\PhotoshopElementsFileAgent.exe
========== Modules (No Company Name) ========== MOD - [2012/05/31 01:51:08 | 000,699,280 | R--- | M] () -- C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\wincfi39.dll
========== Services (SafeList) ========== SRV:
64bit: - [2011/03/09 15:53:04 | 000,203,776 | ---- | M] (AMD) [Auto | Running] -- C:\Windows\SysNative\atiesrxx.exe -- (AMD External Events Utility)
SRV:
64bit: - [2009/07/14 12:41:27 | 001,011,712 | ---- | M] (Microsoft Corporation) [On_Demand | Stopped] -- C:\Program Files\Windows Defender\MpSvc.dll -- (WinDefend)
SRV:
64bit: - [2009/07/14 12:40:01 | 000,193,536 | ---- | M] (Microsoft Corporation) [On_Demand | Stopped] -- C:\Windows\SysNative\appmgmts.dll -- (AppMgmt)
SRV:
64bit: - [2008/12/27 03:55:28 | 000,068,760 | ---- | M] (SiSoftware) [On_Demand | Stopped] -- C:\Program Files\SiSoftware\SiSoftware Sandra Lite 2013.SP1\RpcAgentSrv.exe -- (SandraAgentSrv)
SRV - [2013/03/13 16:16:51 | 000,253,656 | ---- | M] (Adobe Systems Incorporated) [On_Demand | Stopped] -- C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe -- (AdobeFlashPlayerUpdateSvc)
SRV - [2013/03/08 11:02:10 | 000,115,608 | ---- | M] (Mozilla Foundation) [On_Demand | Stopped] -- C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe -- (MozillaMaintenance)
SRV - [2013/01/31 10:38:54 | 003,289,208 | ---- | M] (Skype Technologies S.A.) [Auto | Running] -- C:\ProgramData\Skype\Toolbars\Skype C2C Service\c2c_service.exe -- (Skype C2C Service)
SRV - [2013/01/08 12:55:20 | 000,161,536 | R--- | M] (Skype Technologies) [Auto | Running] -- C:\Program Files (x86)\Skype\Updater\Updater.exe -- (SkypeUpdate)
SRV - [2012/12/24 14:33:29 | 000,144,520 | R--- | M] (Symantec Corporation) [Auto | Running] -- C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\ccSvcHst.exe -- (N360)
SRV - [2012/12/19 01:28:08 | 000,065,192 | ---- | M] (Adobe Systems Incorporated) [Auto | Running] -- C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe -- (AdobeARMservice)
SRV - [2012/10/23 20:47:48 | 002,848,168 | ---- | M] (TeamViewer GmbH) [Auto | Running] -- C:\Program Files (x86)\TeamViewer\Version7\TeamViewer_Service.exe -- (TeamViewer7)
SRV - [2012/06/24 18:11:20 | 000,655,624 | ---- | M] (Acresso Software Inc.) [On_Demand | Stopped] -- C:\Program Files (x86)\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe -- (FLEXnet Licensing Service)
SRV - [2011/10/01 08:30:22 | 000,219,496 | ---- | M] (Microsoft Corporation) [On_Demand | Running] -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftvsa.exe -- (sftvsa)
SRV - [2011/10/01 08:30:18 | 000,508,776 | ---- | M] (Microsoft Corporation) [Auto | Running] -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftlist.exe -- (sftlist)
SRV - [2011/08/19 20:26:50 | 000,450,848 | ---- | M] (Logitech Inc.) [Auto | Running] -- C:\Program Files (x86)\Common Files\logishrd\LVMVFM\UMVPFSrv.exe -- (UMVPFSrv)
SRV - [2010/10/27 17:18:52 | 000,052,896 | ---- | M] (Atheros Commnucations) [Auto | Running] -- C:\Program Files (x86)\Bluetooth Suite\AdminService.exe -- (AtherosSvc)
SRV - [2010/03/18 14:16:28 | 000,130,384 | ---- | M] (Microsoft Corporation) [Auto | Stopped] -- C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -- (clr_optimization_v4.0.30319_32)
SRV - [2009/06/11 08:23:09 | 000,066,384 | ---- | M] (Microsoft Corporation) [Disabled | Stopped] -- C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe -- (clr_optimization_v2.0.50727_32)
SRV - [2008/09/16 13:03:18 | 000,169,312 | ---- | M] (Adobe Systems Incorporated) [Auto | Running] -- C:\Program Files (x86)\Adobe\Photoshop Elements 7.0\PhotoshopElementsFileAgent.exe -- (AdobeActiveFileMonitor7.0)
========== Driver Services (SafeList) ========== DRV:
64bit: - [2013/02/08 08:08:06 | 000,177,312 | ---- | M] (Symantec Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\SYMEVENT64x86.SYS -- (SymEvent)
DRV:
64bit: - [2013/01/31 14:18:18 | 000,432,800 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\symnets.sys -- (SymNetS)
DRV:
64bit: - [2013/01/31 14:18:06 | 001,139,800 | ---- | M] (Symantec Corporation) [File_System | Boot | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\symefa64.sys -- (SymEFA)
DRV:
64bit: - [2013/01/29 12:45:19 | 000,796,248 | ---- | M] (Symantec Corporation) [File_System | System | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\srtsp64.sys -- (SRTSP)
DRV:
64bit: - [2013/01/29 12:45:19 | 000,036,952 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\srtspx64.sys -- (SRTSPX)
DRV:
64bit: - [2013/01/22 13:15:33 | 000,493,656 | ---- | M] (Symantec Corporation) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\symds64.sys -- (SymDS)
DRV:
64bit: - [2012/11/16 13:22:01 | 000,224,416 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\ironx64.sys -- (SymIRON)
DRV:
64bit: - [2012/11/16 13:18:04 | 000,168,096 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\Windows\SysNative\drivers\N360x64\1403000.024\ccsetx64.sys -- (ccSet_N360)
DRV:
64bit: - [2012/06/24 16:05:01 | 000,052,856 | ---- | M] (Sonic Solutions) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\PxHlpa64.sys -- (PxHlpa64)
DRV:
64bit: - [2012/03/01 17:46:16 | 000,023,408 | ---- | M] (Microsoft Corporation) [Recognizer | Boot | Unknown] -- C:\Windows\SysNative\drivers\fs_rec.sys -- (Fs_Rec)
DRV:
64bit: - [2011/10/01 08:30:22 | 000,022,376 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\Sftvollh.sys -- (Sftvol)
DRV:
64bit: - [2011/10/01 08:30:18 | 000,268,648 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\Sftplaylh.sys -- (Sftplay)
DRV:
64bit: - [2011/10/01 08:30:18 | 000,025,960 | ---- | M] (Microsoft Corporation) [File_System | On_Demand | Running] -- C:\Windows\SysNative\drivers\Sftredirlh.sys -- (Sftredir)
DRV:
64bit: - [2011/10/01 08:30:10 | 000,764,264 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\Sftfslh.sys -- (Sftfs)
DRV:
64bit: - [2011/08/19 20:27:30 | 004,869,024 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\LVUVC64.sys -- (LVUVC64)
DRV:
64bit: - [2011/08/19 20:27:30 | 000,351,136 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\lvrs64.sys -- (LVRS64)
DRV:
64bit: - [2011/08/19 20:27:22 | 000,025,632 | ---- | M] (Logitech Inc.) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\lvbflt64.sys -- (CompFilter64)
DRV:
64bit: - [2011/03/11 17:41:12 | 000,107,904 | ---- | M] (Advanced Micro Devices) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\amdsata.sys -- (amdsata)
DRV:
64bit: - [2011/03/11 17:41:12 | 000,027,008 | ---- | M] (Advanced Micro Devices) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\amdxata.sys -- (amdxata)
DRV:
64bit: - [2011/03/09 20:22:42 | 009,258,496 | ---- | M] (ATI Technologies Inc.) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\atikmdag.sys -- (amdkmdag)
DRV:
64bit: - [2011/03/09 15:17:42 | 000,300,544 | ---- | M] (Advanced Micro Devices, Inc.) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\atikmpag.sys -- (amdkmdap)
DRV:
64bit: - [2010/11/22 18:09:06 | 000,303,408 | ---- | M] (Marvell Semiconductor, Inc.) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\mv91xx.sys -- (mv91xx)
DRV:
64bit: - [2010/11/22 18:09:06 | 000,024,880 | ---- | M] (Marvell Semiconductor Inc.) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\mv91cons.sys -- (mv91cons)
DRV:
64bit: - [2010/11/21 00:33:35 | 000,078,720 | ---- | M] (Hewlett-Packard Company) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\HpSAMD.sys -- (HpSAMD)
DRV:
64bit: - [2010/11/20 22:07:05 | 000,059,392 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\TsUsbFlt.sys -- (TsUsbFlt)
DRV:
64bit: - [2010/11/20 22:03:42 | 000,020,992 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\rdpvideominiport.sys -- (RdpVideoMiniport)
DRV:
64bit: - [2010/11/17 23:04:32 | 000,115,216 | ---- | M] (Advanced Micro Devices) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\AtihdW76.sys -- (AtiHDAudioService)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,301,680 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_a2dp.sys -- (BTATH_A2DP)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,279,152 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btfilter.sys -- (BtFilter)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,203,624 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_hcrp.sys -- (BTATH_HCRP)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,156,520 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_rcp.sys -- (BTATH_RCP)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,058,992 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_lwflt.sys -- (BTATH_LWFLT)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,055,336 | ---- | M] (Windows ® Win 7 DDK provider) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\AthDfu.sys -- (ATHDFU)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,038,248 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_flt.sys -- (AthBTPort)
DRV:
64bit: - [2010/10/27 16:50:28 | 000,031,080 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_bus.sys -- (BTATH_BUS)
DRV:
64bit: - [2010/10/26 12:08:08 | 000,406,632 | ---- | M] (Realtek ) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\Rt64win7.sys -- (RTL8167)
DRV:
64bit: - [2010/10/20 00:34:26 | 000,056,344 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\HECIx64.sys -- (MEIx64)
DRV:
64bit: - [2009/07/14 12:52:20 | 000,194,128 | ---- | M] (AMD Technologies Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\amdsbs.sys -- (amdsbs)
DRV:
64bit: - [2009/07/14 12:48:04 | 000,065,600 | ---- | M] (LSI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\lsi_sas2.sys -- (LSI_SAS2)
DRV:
64bit: - [2009/07/14 12:45:55 | 000,024,656 | ---- | M] (Promise Technology) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\stexstor.sys -- (stexstor)
DRV:
64bit: - [2009/06/11 07:34:33 | 003,286,016 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\evbda.sys -- (ebdrv)
DRV:
64bit: - [2009/06/11 07:34:28 | 000,468,480 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\bxvbda.sys -- (b06bdrv)
DRV:
64bit: - [2009/06/11 07:34:23 | 000,270,848 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\b57nd60a.sys -- (b57nd60a)
DRV:
64bit: - [2009/06/11 07:31:59 | 000,031,232 | ---- | M] (Hauppauge Computer Works, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\hcw85cir.sys -- (hcw85cir)
DRV:
64bit: - [2005/01/06 15:23:19 | 000,313,520 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\e1c62x64.sys -- (e1cexpress)
DRV:
64bit: - [2005/01/06 15:21:27 | 000,120,920 | ---- | M] (JMicron Technology Corp.) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\jraid.sys -- (JRAID)
DRV:
64bit: - [2005/01/06 15:18:19 | 000,181,248 | ---- | M] (Renesas Electronics Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\nusb3xhc.sys -- (nusb3xhc)
DRV:
64bit: - [2005/01/06 15:18:19 | 000,080,384 | ---- | M] (Renesas Electronics Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\nusb3hub.sys -- (nusb3hub)
DRV - [2013/02/08 08:30:34 | 002,087,664 | ---- | M] (Symantec Corporation) [Kernel | On_Demand | Running] -- C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\Definitions\VirusDefs\20130315.025\ex64.sys -- (NAVEX15)
DRV - [2013/02/08 08:30:34 | 000,126,192 | ---- | M] (Symantec Corporation) [Kernel | On_Demand | Running] -- C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\Definitions\VirusDefs\20130315.025\eng64.sys -- (NAVENG)
DRV - [2013/02/07 16:46:48 | 000,513,184 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\Definitions\IPSDefs\20130313.001\IDSviA64.sys -- (IDSVia64)
DRV - [2013/01/16 03:22:36 | 001,388,120 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\Definitions\BASHDefs\20130301.001\BHDrvx64.sys -- (BHDrvx64)
DRV - [2012/08/18 20:00:00 | 000,484,512 | ---- | M] (Symantec Corporation) [Kernel | System | Running] -- C:\Program Files (x86)\Common Files\Symantec Shared\EENGINE\eeCtrl64.sys -- (eeCtrl)
DRV - [2012/08/18 20:00:00 | 000,138,912 | ---- | M] (Symantec Corporation) [Kernel | On_Demand | Running] -- C:\Program Files (x86)\Common Files\Symantec Shared\EENGINE\EraserUtilRebootDrv.sys -- (EraserUtilRebootDrv)
DRV - [2009/07/14 12:19:10 | 000,019,008 | ---- | M] (Microsoft Corporation) [File_System | On_Demand | Stopped] -- C:\Windows\SysWOW64\drivers\wimmount.sys -- (WIMMount)
========== Standard Registry (SafeList) ========== ========== Internet Explorer ========== IE:
64bit: - HKLM\..\SearchScopes,DefaultScope =
IE:
64bit: - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" =
http://www.bing.com/...ms}&FORM=IE8SRCIE:
64bit: - HKLM\..\SearchScopes\{6A1806CD-94D4-4689-BA73-E35EA1EA9990}: "URL" =
http://www.google.co...g}&sourceid=ie7IE - HKLM\..\SearchScopes,DefaultScope =
IE - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" =
http://www.bing.com/...ms}&FORM=IE8SRCIE - HKLM\..\SearchScopes\{6A1806CD-94D4-4689-BA73-E35EA1EA9990}: "URL" =
http://www.google.co...g}&sourceid=ie7 IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page =
http://www.google.com.au/IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page Redirect Cache AcceptLangs = en-au
IE - HKCU\..\SearchScopes,DefaultScope = {6A1806CD-94D4-4689-BA73-E35EA1EA9990}
IE - HKCU\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" =
http://www.bing.com/...Box&FORM=IE8SRCIE - HKCU\..\SearchScopes\{3F26506F-F501-4B3F-AE0A-629933EB9AD8}: "URL" =
http://websearch.ask...F-9E694510DC7EIE - HKCU\..\SearchScopes\{6A1806CD-94D4-4689-BA73-E35EA1EA9990}: "URL" =
http://www.google.co...1I7RNRN_enAU448IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ========== FF - prefs.js..browser.startup.homepage: "
http://www.google.com/"FF - prefs.js..extensions.enabledAddons: %7B317B5128-0B0B-49b2-B2DB-1E7560E16C74%7D:2.8.8
FF - prefs.js..extensions.enabledAddons: %7B82AF8DCA-6DE9-405D-BD5E-43525BDAD38A%7D:6.6.0.11664
FF - prefs.js..extensions.enabledAddons: %7B972ce4c6-7e08-4474-a285-3208198ce6fd%7D:19.0.2
FF:
64bit: - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\Windows\system32\Macromed\Flash\NPSWF64_11_6_602_180.dll File not found
FF:
64bit: - HKLM\Software\MozillaPlugins\@microsoft.com/GENUINE: disabled File not found
FF:
64bit: - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation)
FF:
64bit: - HKLM\Software\MozillaPlugins\@microsoft.com/OfficeAuthz,version=14.0: C:\PROGRA~1\MICROS~2\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\Windows\SysWOW64\Macromed\Flash\NPSWF32_11_6_602_180.dll ()
FF - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin: C:\Program Files (x86)\Java\jre6\bin\new_plugin\npjp2.dll (Sun Microsystems, Inc.)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/GENUINE: disabled File not found
FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files (x86)\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/OfficeAuthz,version=14.0: C:\PROGRA~2\MICROS~2\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/SharePoint,version=14.0: C:\PROGRA~2\MICROS~2\Office14\NPSPWRAP.DLL (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@real.com/nppl3260;version=12.0.1.666: C:\Program Files (x86)\Real\RealPlayer\Netscape6\nppl3260.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprjplug;version=12.0.1.666: C:\Program Files (x86)\Real\RealPlayer\Netscape6\nprjplug.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpchromebrowserrecordext;version=12.0.1.666: C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprphtml5videoshim;version=12.0.1.666: C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpjplug;version=12.0.1.666: C:\Program Files (x86)\Real\RealPlayer\Netscape6\nprpjplug.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nsJSRealPlayerPlugin;version=: File not found
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=3: C:\Program Files (x86)\Google\Update\1.3.21.135\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=9: C:\Program Files (x86)\Google\Update\1.3.21.135\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\Adobe Reader: C:\Program Files (x86)\Adobe\Reader 10.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{ABDE892B-13A8-4d1b-88E6-365A6E755758}: C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\Firefox\Ext [2013/02/06 11:22:54 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{BBDA0591-3099-440a-AA10-41764D9DB4DB}: C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\IPSFFPlgn\ [2013/02/08 08:08:22 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{2D3F3651-74B9-4795-BDEC-6DA2F431CB62}: C:\ProgramData\Norton\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\N360_20.1.0.24\coFFPlgn\ [2013/03/16 18:35:59 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{22119944-ED35-4ab1-910B-E619EA06A115}: C:\Program Files (x86)\Siber Systems\AI RoboForm\Firefox [2013/03/10 20:34:34 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 19.0.2\extensions\\Components: C:\Program Files (x86)\Mozilla Firefox\components [2013/03/08 11:02:10 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 19.0.2\extensions\\Plugins: C:\Program Files (x86)\Mozilla Firefox\plugins [2013/03/08 11:02:09 | 000,000,000 | ---D | M]
[2013/03/10 15:39:51 | 000,000,000 | ---D | M] (No name found) -- C:\Users\User\AppData\Roaming\mozilla\Extensions
[2013/03/10 15:40:14 | 000,000,000 | ---D | M] (No name found) -- C:\Users\User\AppData\Roaming\mozilla\Firefox\Profiles\fin2h4dp.default\extensions
[2013/02/22 16:28:14 | 000,000,000 | ---D | M] (SeoQuake) -- C:\Users\User\AppData\Roaming\mozilla\Firefox\Profiles\fin2h4dp.default\extensions\{317B5128-0B0B-49b2-B2DB-1E7560E16C74}
[2013/02/14 20:16:47 | 000,817,280 | ---- | M] () (No name found) -- C:\Users\User\AppData\Roaming\mozilla\firefox\profiles\fin2h4dp.default\extensions\{d10d0bf8-f5b5-c8b4-a8b2-2b9879e08c5d}.xpi
[2011/11/28 12:10:02 | 000,002,431 | ---- | M] () -- C:\Users\User\AppData\Roaming\mozilla\firefox\profiles\fin2h4dp.default\searchplugins\safesearch.xml
[2013/03/08 11:02:09 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files (x86)\Mozilla Firefox\extensions
[2013/03/08 11:02:09 | 000,000,000 | ---D | M] (Skype Click to Call) -- C:\Program Files (x86)\Mozilla Firefox\extensions\{82AF8DCA-6DE9-405D-BD5E-43525BDAD38A}
[2013/03/08 11:02:10 | 000,263,064 | ---- | M] (Mozilla Foundation) -- C:\Program Files (x86)\mozilla firefox\components\browsercomps.dll
[2011/07/30 00:33:40 | 000,108,480 | ---- | M] ( ) -- C:\Program Files (x86)\mozilla firefox\plugins\npwangwang.dll
[2012/09/17 09:53:25 | 000,002,465 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\bing.xml
[2013/02/20 08:06:03 | 000,002,086 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\twitter.xml
========== Chrome ========== O1 HOSTS File: ([2013/03/10 21:17:05 | 000,000,027 | ---- | M]) - C:\Windows\SysNative\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 localhost
O2:
64bit: - BHO: (RoboForm Toolbar Helper) - {724d43a9-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O2:
64bit: - BHO: (Google Toolbar Helper) - {AA58ED58-01DD-4d91-8333-CF10577473F7} - C:\Program Files (x86)\Google\Google Toolbar\GoogleToolbar_64.dll (Google Inc.)
O2:
64bit: - BHO: (Skype add-on for Internet Explorer) - {AE805869-2E5C-4ED4-8F7B-F1F7851A4497} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer x64\skypeieplugin.dll (Skype Technologies S.A.)
O2 - BHO: (RealPlayer Download and Record Plugin for Internet Explorer) - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll (RealPlayer)
O2 - BHO: (Spybot-S&D IE Protection) - {53707962-6F74-2D53-2644-206D7942484F} - C:\Program Files (x86)\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O2 - BHO: (Norton Identity Protection) - {602ADB0E-4AFF-4217-8AA1-95DAC4DFA408} - C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\coieplg.dll (Symantec Corporation)
O2 - BHO: (Norton Vulnerability Protection) - {6D53EC84-6AAE-4787-AEEE-F4628F01010C} - C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\ips\ipsbho.dll (Symantec Corporation)
O2 - BHO: (RoboForm Toolbar Helper) - {724d43a9-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O2 - BHO: (Skype Browser Helper) - {AE805869-2E5C-4ED4-8F7B-F1F7851A4497} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O3:
64bit: - HKLM\..\Toolbar: (Google Toolbar) - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - C:\Program Files (x86)\Google\Google Toolbar\GoogleToolbar_64.dll (Google Inc.)
O3:
64bit: - HKLM\..\Toolbar: (&RoboForm Toolbar) - {724d43a0-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O3 - HKLM\..\Toolbar: (&RoboForm Toolbar) - {724d43a0-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O3 - HKLM\..\Toolbar: (Norton Toolbar) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - C:\Program Files (x86)\Norton 360\Engine\20.3.0.36\coieplg.dll (Symantec Corporation)
O3 - HKLM\..\Toolbar: (no name) - Locked - No CLSID value found.
O3:
64bit: - HKCU\..\Toolbar\WebBrowser: (Google Toolbar) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - C:\Program Files (x86)\Google\Google Toolbar\GoogleToolbar_64.dll (Google Inc.)
O3:
64bit: - HKCU\..\Toolbar\WebBrowser: (&RoboForm Toolbar) - {724D43A0-0D85-11D4-9908-00400523E39A} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O3 - HKCU\..\Toolbar\WebBrowser: (&RoboForm Toolbar) - {724D43A0-0D85-11D4-9908-00400523E39A} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O4 - HKLM..\Run: [TkBellExe] C:\Program Files (x86)\Real\RealPlayer\update\realsched.exe (RealNetworks, Inc.)
O4 - HKCU..\Run: [RoboForm] C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboTaskBarIcon.exe (Siber Systems)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorUser = 3
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: PromptOnSecureDesktop = 0
O7 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O8:
64bit: - Extra context menu item: Customize Menu - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComCustomizeIEMenu.html ()
O8:
64bit: - Extra context menu item: Fill Forms - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComFillForms.html ()
O8:
64bit: - Extra context menu item: Open Client to monitor &1 - C:\Windows\web\AOpenClient.htm File not found
O8:
64bit: - Extra context menu item: Open Client to monitor &2 - C:\Windows\web\AOpenClient.htm File not found
O8:
64bit: - Extra context menu item: Open Client to monitor &3 - C:\Windows\web\AOpenClient.htm File not found
O8:
64bit: - Extra context menu item: Save Forms - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComSavePass.html ()
O8:
64bit: - Extra context menu item: Show RoboForm Toolbar - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComShowToolbar.html ()
O8 - Extra context menu item: Customize Menu - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComCustomizeIEMenu.html ()
O8 - Extra context menu item: Fill Forms - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComFillForms.html ()
O8 - Extra context menu item: Open Client to monitor &1 - C:\Windows\web\AOpenClient.htm File not found
O8 - Extra context menu item: Open Client to monitor &2 - C:\Windows\web\AOpenClient.htm File not found
O8 - Extra context menu item: Open Client to monitor &3 - C:\Windows\web\AOpenClient.htm File not found
O8 - Extra context menu item: Save Forms - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComSavePass.html ()
O8 - Extra context menu item: Show RoboForm Toolbar - C:\Program Files (x86)\Siber Systems\AI RoboForm\RoboFormComShowToolbar.html ()
O9:
64bit: - Extra Button: Fill Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F46} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra 'Tools' menuitem : Fill Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F46} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra Button: Save - {320AF880-6646-11D3-ABEE-C5DBF3571F49} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra 'Tools' menuitem : Save Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F49} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra Button: Show Toolbar - {724d43aa-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra 'Tools' menuitem : Show RoboForm Toolbar - {724d43aa-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform-x64.dll (Siber Systems Inc.)
O9:
64bit: - Extra Button: Skype Click to Call - {898EA8C8-E7FF-479B-8935-AEC46303B9E5} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer x64\skypeieplugin.dll (Skype Technologies S.A.)
O9 - Extra Button: Fill Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F46} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra 'Tools' menuitem : Fill Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F46} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra Button: Save - {320AF880-6646-11D3-ABEE-C5DBF3571F49} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra 'Tools' menuitem : Save Forms - {320AF880-6646-11D3-ABEE-C5DBF3571F49} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra Button: Show Toolbar - {724d43aa-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra 'Tools' menuitem : Show RoboForm Toolbar - {724d43aa-0d85-11d4-9908-00400523e39a} - C:\Program Files (x86)\Siber Systems\AI RoboForm\roboform.dll (Siber Systems Inc.)
O9 - Extra 'Tools' menuitem : Send by Bluetooth to - {7815BE26-237D-41A8-A98F-F7BD75F71086} - C:\Program Files (x86)\Bluetooth Suite\IEPlugIn.dll (Atheros Commnucations)
O9 - Extra Button: Skype Click to Call - {898EA8C8-E7FF-479B-8935-AEC46303B9E5} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O9 - Extra 'Tools' menuitem : Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files (x86)\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O13 - gopher Prefix: missing
O15 - HKCU\..Trusted Domains: taobao.com ([]http in Trusted sites)
O15 - HKCU\..Trusted Domains: taobao.com ([]https in Trusted sites)
O16 - DPF: {02BCC737-B171-4746-94C9-0D8A0B2C0089}
http://office.micros...n/ieawsdc32.cab (Microsoft Office Template and Media Control)
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5}
http://security.syma...n/bin/cabsa.cab (Symantec RuFSI Utility Class)
O16 - DPF: {7530BFB8-7293-4D34-9923-61A11451AFC5}
http://download.eset...lineScanner.cab (Reg Error: Key error.)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O16 - DPF: {CAFEEFAC-0016-0000-0029-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.1.1
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{0DC4DF19-1EDC-46D2-B843-4C3A933323B4}: DhcpNameServer = 192.168.1.1
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{D03F6732-E510-4300-9E4A-E8088652AC19}: DhcpNameServer = 192.168.1.1
O18:
64bit: - Protocol\Handler\ms-help - No CLSID value found
O18:
64bit: - Protocol\Handler\skype-ie-addon-data {91774881-D725-4E58-B298-07617B9B86A8} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer x64\skypeieplugin.dll (Skype Technologies S.A.)
O18 - Protocol\Handler\skype-ie-addon-data {91774881-D725-4E58-B298-07617B9B86A8} - C:\Program Files (x86)\Skype\Toolbars\Internet Explorer\skypeieplugin.dll (Skype Technologies S.A.)
O20:
64bit: - HKLM Winlogon: Shell - (Explorer.exe) - C:\Windows\explorer.exe (Microsoft Corporation)
O20:
64bit: - HKLM Winlogon: UserInit - (C:\Windows\system32\userinit.exe) - C:\Windows\SysNative\userinit.exe (Microsoft Corporation)
O20 - HKLM Winlogon: Shell - (explorer.exe) - C:\Windows\SysWow64\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\Windows\system32\userinit.exe) - C:\Windows\SysWOW64\userinit.exe (Microsoft Corporation)
O21:
64bit: - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found.
O21 - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found.
O32 - HKLM CDRom: AutoRun - 1
O34 - HKLM BootExecute: (autocheck autochk *)
O35:
64bit: - HKLM\..comfile [open] -- "%1" %*
O35:
64bit: - HKLM\..exefile [open] -- "%1" %*
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37:
64bit: - HKLM\...com [@ = ComFile] -- "%1" %*
O37:
64bit: - HKLM\...exe [@ = exefile] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
O38 - SubSystems\\Windows: (ServerDll=winsrv:UserServerDllInitialization,3)
O38 - SubSystems\\Windows: (ServerDll=winsrv:ConServerDllInitialization,2)
O38 - SubSystems\\Windows: (ServerDll=sxssrv,4)
========== Files/Folders - Created Within 30 Days ========== [2013/03/16 07:26:53 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\MONIKE
[2013/03/16 07:24:33 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\INVOICES_MO_MARCH_2013
[2013/03/15 14:24:48 | 000,000,000 | ---D | C] -- C:\Users\User\AppData\Roaming\Malwarebytes
[2013/03/15 14:24:27 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Malwarebytes' Anti-Malware
[2013/03/15 14:24:27 | 000,000,000 | ---D | C] -- C:\ProgramData\Malwarebytes
[2013/03/15 14:24:26 | 000,024,176 | ---- | C] (Malwarebytes Corporation) -- C:\Windows\SysNative\drivers\mbam.sys
[2013/03/15 14:24:26 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Malwarebytes' Anti-Malware
[2013/03/15 14:17:15 | 000,354,265 | ---- | C] (Farbar) -- E:\Users\User\Desktop\FSS.exe
[2013/03/15 14:16:31 | 010,156,424 | ---- | C] (Malwarebytes Corporation ) -- E:\Users\User\Desktop\mbam-setup.exe
[2013/03/15 03:04:55 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Microsoft Silverlight
[2013/03/15 03:03:48 | 000,000,000 | ---D | C] -- C:\Program Files\Microsoft Silverlight
[2013/03/15 03:03:48 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Microsoft Silverlight
[2013/03/15 03:03:22 | 000,000,000 | -HSD | C] -- C:\Config.Msi
[2013/03/14 18:56:42 | 000,000,000 | ---D | C] -- C:\Program Files\CCleaner
[2013/03/13 07:09:09 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\RK_Quarantine
[2013/03/12 20:43:41 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\VIRAL PROGRAMS
[2013/03/12 20:18:17 | 004,732,416 | ---- | C] (AVAST Software) -- E:\Users\User\Desktop\aswMBR.exe
[2013/03/12 19:54:36 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\LOGS
[2013/03/12 09:14:04 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\PRODUCT SPECS
[2013/03/10 21:26:58 | 000,000,000 | ---D | C] -- C:\TDSSKiller_Quarantine
[2013/03/10 21:22:29 | 000,000,000 | ---D | C] -- C:\Windows\temp
[2013/03/10 21:17:25 | 000,000,000 | ---D | C] -- C:\$RECYCLE.BIN
[2013/03/10 21:06:37 | 000,518,144 | ---- | C] (SteelWerX) -- C:\Windows\SWREG.exe
[2013/03/10 21:06:37 | 000,406,528 | ---- | C] (SteelWerX) -- C:\Windows\SWSC.exe
[2013/03/10 21:06:37 | 000,060,416 | ---- | C] (NirSoft) -- C:\Windows\NIRCMD.exe
[2013/03/10 21:06:03 | 000,000,000 | ---D | C] -- C:\Qoobox
[2013/03/10 21:04:56 | 000,000,000 | ---D | C] -- C:\Windows\erdnt
[2013/03/10 09:17:24 | 002,237,968 | ---- | C] (Kaspersky Lab ZAO) -- E:\Users\User\Desktop\tdsskiller.exe
[2013/03/10 09:16:10 | 005,037,356 | R--- | C] (Swearware) -- E:\Users\User\Desktop\ComboFix.exe
[2013/03/09 13:19:54 | 000,602,112 | ---- | C] (OldTimer Tools) -- E:\Users\User\Desktop\OTL.exe
[2013/03/08 11:02:08 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Mozilla Firefox
[2013/03/08 10:28:11 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\ARTG DETAILS
[2013/03/07 12:48:53 | 000,000,000 | ---D | C] -- E:\Users\User\Documents\GLEN SHRIRMER ABODE
[2013/03/07 11:48:23 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\Changsha Organic Herb
[2013/03/06 08:06:48 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\Graham Meinike
[2013/03/03 15:20:56 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\led_aa
[2013/03/03 10:45:41 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Avery Dennison
[2013/03/03 10:45:39 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Avery Dennison
[2013/03/03 10:33:31 | 010,651,392 | ---- | C] (Avery Dennison Corp. ) -- E:\Users\User\Documents\AU_en_DP5_DL_20110203 - DPro Light.exe
[2013/02/28 08:13:41 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\Busaba
[2013/02/24 19:47:53 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\res_documentation
[2013/02/24 19:47:15 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\eBay Display Boxes
[2013/02/22 22:02:01 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\RES SHEETS
[2013/02/19 08:38:48 | 000,000,000 | R--D | C] -- E:\Users\User\Documents\Scanned Documents
[2013/02/19 08:38:48 | 000,000,000 | ---D | C] -- E:\Users\User\Documents\Fax
[2013/02/18 20:40:34 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\tax
[2013/02/15 08:32:05 | 000,000,000 | ---D | C] -- E:\Users\User\Desktop\green energy logos
[1 E:\Users\User\Desktop\*.tmp files -> E:\Users\User\Desktop\*.tmp -> ]
========== Files - Modified Within 30 Days ========== [2013/03/16 18:35:45 | 000,000,890 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskMachineCore.job
[2013/03/16 18:35:27 | 000,067,584 | --S- | M] () -- C:\Windows\bootstat.dat
[2013/03/16 18:35:19 | 2132,037,631 | -HS- | M] () -- C:\hiberfil.sys
[2013/03/16 18:29:00 | 000,000,894 | ---- | M] () -- C:\Windows\tasks\GoogleUpdateTaskMachineUA.job
[2013/03/16 18:28:39 | 000,050,380 | ---- | M] () -- E:\Users\User\Desktop\firewall.jpg
[2013/03/16 18:16:00 | 000,000,830 | ---- | M] () -- C:\Windows\tasks\Adobe Flash Player Updater.job
[2013/03/15 16:41:43 | 000,015,024 | -H-- | M] () -- C:\Windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-1.C7483456-A289-439d-8115-601632D005A0
[2013/03/15 16:41:43 | 000,015,024 | -H-- | M] () -- C:\Windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-0.C7483456-A289-439d-8115-601632D005A0
[2013/03/15 14:24:29 | 000,001,109 | ---- | M] () -- C:\Users\Public\Desktop\Malwarebytes Anti-Malware.lnk
[2013/03/15 14:17:15 | 000,354,265 | ---- | M] (Farbar) -- E:\Users\User\Desktop\FSS.exe
[2013/03/15 14:17:00 | 010,156,424 | ---- | M] (Malwarebytes Corporation ) -- E:\Users\User\Desktop\mbam-setup.exe
[2013/03/15 03:25:25 | 001,756,669 | ---- | M] () -- C:\Windows\SysNative\drivers\N360x64\1403000.024\Cat.DB
[2013/03/14 18:56:45 | 000,000,822 | ---- | M] () -- C:\Users\Public\Desktop\CCleaner.lnk
[2013/03/13 22:29:48 | 000,262,899 | ---- | M] () -- E:\Users\User\Desktop\Video call snapshot 433.png
[2013/03/13 17:13:30 | 000,117,502 | ---- | M] () -- E:\Users\User\Desktop\Receipt_Resveratrol.jpg
[2013/03/13 08:16:03 | 001,099,754 | ---- | M] () -- E:\Users\User\Desktop\TGA2.pdf
[2013/03/13 08:15:28 | 001,314,648 | ---- | M] () -- E:\Users\User\Desktop\TGA1.pdf
[2013/03/12 20:45:15 | 000,732,934 | ---- | M] () -- C:\Windows\SysNative\PerfStringBackup.INI
[2013/03/12 20:45:15 | 000,632,678 | ---- | M] () -- C:\Windows\SysNative\perfh009.dat
[2013/03/12 20:45:15 | 000,112,048 | ---- | M] () -- C:\Windows\SysNative\perfc009.dat
[2013/03/12 20:28:14 | 000,597,667 | ---- | M] () -- E:\Users\User\Desktop\AdwCleaner.exe
[2013/03/12 20:20:37 | 000,791,552 | ---- | M] () -- E:\Users\User\Desktop\RogueKillerX64.exe
[2013/03/12 20:19:49 | 004,732,416 | ---- | M] (AVAST Software) -- E:\Users\User\Desktop\aswMBR.exe
[2013/03/12 17:17:01 | 000,254,696 | ---- | M] () -- E:\Users\User\Desktop\ARTG LISTING DETAILS.jpg
[2013/03/10 21:17:05 | 000,000,027 | ---- | M] () -- C:\Windows\SysNative\drivers\etc\hosts
[2013/03/10 21:04:45 | 005,037,356 | R--- | M] (Swearware) -- E:\Users\User\Desktop\ComboFix.exe
[2013/03/10 09:17:35 | 002,237,968 | ---- | M] (Kaspersky Lab ZAO) -- E:\Users\User\Desktop\tdsskiller.exe
[2013/03/09 13:19:55 | 000,602,112 | ---- | M] (OldTimer Tools) -- E:\Users\User\Desktop\OTL.exe
[2013/03/09 10:46:16 | 006,229,949 | ---- | M] () -- E:\Users\User\Desktop\CN Lab Product list.pdf
[2013/03/09 09:39:16 | 000,000,265 | ---- | M] () -- C:\Windows\SysWow64\a.out
[2013/03/07 09:05:16 | 000,073,252 | ---- | M] () -- E:\Users\User\Desktop\HEALTHY ACTION.pdf
[2013/03/05 13:41:58 | 000,102,290 | ---- | M] () -- E:\Users\User\Desktop\ACETINO_3663.pdf
[2013/03/05 13:38:28 | 000,102,034 | ---- | M] () -- E:\Users\User\Desktop\ACETINO_EXPENSIVE.pdf
[2013/03/05 13:33:54 | 000,102,502 | ---- | M] () -- E:\Users\User\Desktop\PI-1302042(Adam,SR-11A,March 05, 2013)_ACETINO.pdf
[2013/03/04 20:00:48 | 079,777,541 | ---- | M] () -- E:\Users\User\Documents\130218_KUSF_TamarindFreeJones.mp3
[2013/03/03 22:53:32 | 034,755,965 | ---- | M] () -- E:\Users\User\Desktop\THE-PLEASURE-STORE.xse
[2013/03/03 11:18:09 | 006,507,676 | ---- | M] () -- E:\Users\User\Desktop\round_labels_MMS.psd
[2013/02/27 17:42:00 | 000,014,818 | ---- | M] () -- C:\Windows\SysNative\drivers\N360x64\1403000.024\VT20130115.021
[2013/02/26 15:26:08 | 004,465,273 | ---- | M] () -- E:\Users\User\Documents\The Vaticans Holocaust.pdf
[2013/02/25 08:07:00 | 000,030,720 | ---- | M] () -- E:\Users\User\Desktop\MMS_SPECIAL.zdl
[2013/02/20 07:18:46 | 002,425,165 | ---- | M] () -- E:\Users\User\Documents\Best_British_Add_of_the_Year.wmv
[2013/02/19 18:02:04 | 826,260,901 | ---- | M] () -- C:\Windows\MEMORY.DMP
[2013/02/15 04:41:44 | 000,000,172 | ---- | M] () -- C:\Windows\SysNative\drivers\N360x64\1403000.024\isolate.ini
[1 E:\Users\User\Desktop\*.tmp files -> E:\Users\User\Desktop\*.tmp -> ]
========== Files Created - No Company Name ========== [2013/03/16 18:28:39 | 000,050,380 | ---- | C] () -- E:\Users\User\Desktop\firewall.jpg
[2013/03/15 14:24:29 | 000,001,109 | ---- | C] () -- C:\Users\Public\Desktop\Malwarebytes Anti-Malware.lnk
[2013/03/14 18:56:45 | 000,000,822 | ---- | C] () -- C:\Users\Public\Desktop\CCleaner.lnk
[2013/03/13 22:29:37 | 000,262,899 | ---- | C] () -- E:\Users\User\Desktop\Video call snapshot 433.png
[2013/03/13 17:13:30 | 000,117,502 | ---- | C] () -- E:\Users\User\Desktop\Receipt_Resveratrol.jpg
[2013/03/13 08:16:03 | 001,099,754 | ---- | C] () -- E:\Users\User\Desktop\TGA2.pdf
[2013/03/13 08:15:28 | 001,314,648 | ---- | C] () -- E:\Users\User\Desktop\TGA1.pdf
[2013/03/12 20:28:08 | 000,597,667 | ---- | C] () -- E:\Users\User\Desktop\AdwCleaner.exe
[2013/03/12 20:20:37 | 000,791,552 | ---- | C] () -- E:\Users\User\Desktop\RogueKillerX64.exe
[2013/03/12 17:17:01 | 000,254,696 | ---- | C] () -- E:\Users\User\Desktop\ARTG LISTING DETAILS.jpg
[2013/03/10 21:06:37 | 000,256,000 | ---- | C] () -- C:\Windows\PEV.exe
[2013/03/10 21:06:37 | 000,208,896 | ---- | C] () -- C:\Windows\MBR.exe
[2013/03/10 21:06:37 | 000,098,816 | ---- | C] () -- C:\Windows\sed.exe
[2013/03/10 21:06:37 | 000,080,412 | ---- | C] () -- C:\Windows\grep.exe
[2013/03/10 21:06:37 | 000,068,096 | ---- | C] () -- C:\Windows\zip.exe
[2013/03/09 10:46:01 | 006,229,949 | ---- | C] () -- E:\Users\User\Desktop\CN Lab Product list.pdf
[2013/03/09 09:39:16 | 000,000,265 | ---- | C] () -- C:\Windows\SysWow64\a.out
[2013/03/07 09:05:15 | 000,073,252 | ---- | C] () -- E:\Users\User\Desktop\HEALTHY ACTION.pdf
[2013/03/05 13:41:58 | 000,102,290 | ---- | C] () -- E:\Users\User\Desktop\ACETINO_3663.pdf
[2013/03/05 13:38:28 | 000,102,034 | ---- | C] () -- E:\Users\User\Desktop\ACETINO_EXPENSIVE.pdf
[2013/03/05 13:30:59 | 000,102,502 | ---- | C] () -- E:\Users\User\Desktop\PI-1302042(Adam,SR-11A,March 05, 2013)_ACETINO.pdf
[2013/03/04 19:51:44 | 079,777,541 | ---- | C] () -- E:\Users\User\Documents\130218_KUSF_TamarindFreeJones.mp3
[2013/03/03 22:53:20 | 034,755,965 | ---- | C] () -- E:\Users\User\Desktop\THE-PLEASURE-STORE.xse
[2013/03/03 11:18:09 | 006,507,676 | ---- | C] () -- E:\Users\User\Desktop\round_labels_MMS.psd
[2013/03/03 11:10:14 | 005,142,624 | ---- | C] () -- E:\Users\User\Desktop\round_labels_cds.psd
[2013/03/03 10:26:47 | 013,992,844 | ---- | C] () -- E:\Users\User\Desktop\CDS_LABEL.psd
[2013/02/26 15:26:08 | 004,465,273 | ---- | C] () -- E:\Users\User\Documents\The Vaticans Holocaust.pdf
[2013/02/20 07:18:45 | 002,425,165 | ---- | C] () -- E:\Users\User\Documents\Best_British_Add_of_the_Year.wmv
[2013/02/15 08:30:10 | 826,260,901 | ---- | C] () -- C:\Windows\MEMORY.DMP
[2013/02/05 20:21:38 | 013,131,776 | ---- | C] () -- C:\Users\User\AppData\Roaming\Sandra.mdb
[2013/02/05 10:40:33 | 000,003,460 | ---- | C] () -- C:\ProgramData\SMRResults311.dat
[2012/10/29 09:49:30 | 000,111,932 | ---- | C] () -- C:\Windows\SysWow64\EPPICPrinterDB.dat
[2012/10/29 09:49:30 | 000,021,390 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern5.dat
[2012/10/29 09:49:30 | 000,011,811 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern4.dat
[2012/10/29 09:49:30 | 000,004,943 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern6.dat
[2012/10/29 09:49:30 | 000,001,146 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_DU.dat
[2012/10/29 09:49:30 | 000,001,139 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_PT.dat
[2012/10/29 09:49:30 | 000,001,139 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_BP.dat
[2012/10/29 09:49:30 | 000,001,136 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_ES.dat
[2012/10/29 09:49:30 | 000,001,129 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_FR.dat
[2012/10/29 09:49:30 | 000,001,129 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_CF.dat
[2012/10/29 09:49:30 | 000,001,120 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_IT.dat
[2012/10/29 09:49:30 | 000,001,107 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_GE.dat
[2012/10/29 09:49:30 | 000,001,104 | ---- | C] () -- C:\Windows\SysWow64\EPPICPresetData_EN.dat
[2012/10/29 09:49:30 | 000,000,097 | ---- | C] () -- C:\Windows\SysWow64\PICSDK.ini
[2012/10/29 09:49:29 | 000,031,053 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern131.dat
[2012/10/29 09:49:29 | 000,027,417 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern121.dat
[2012/10/29 09:49:29 | 000,026,154 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern1.dat
[2012/10/29 09:49:29 | 000,024,903 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern3.dat
[2012/10/29 09:49:29 | 000,020,148 | ---- | C] () -- C:\Windows\SysWow64\EPPICPattern2.dat
[2012/08/19 20:33:52 | 000,134,112 | ---- | C] () -- C:\Users\User\LED PAYMENT.jpg
[2012/06/21 22:07:54 | 000,000,064 | ---- | C] () -- C:\Windows\GPlrLanc.dat
[2012/02/13 16:49:16 | 000,063,488 | ---- | C] () -- C:\Windows\ssdal_nc.exe
[2011/10/10 14:36:07 | 000,740,152 | ---- | C] () -- C:\Windows\SysWow64\PerfStringBackup.INI
[2011/09/19 22:10:24 | 000,010,240 | ---- | C] () -- C:\Users\User\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2011/09/12 11:45:06 | 002,066,218 | ---- | C] () -- C:\Windows\XSitePro2.5 Resource Pack Uninstaller.exe
[2011/09/12 11:42:11 | 001,027,352 | ---- | C] () -- C:\Windows\XSitePro2 Uninstaller.exe
[2011/09/12 11:12:25 | 000,000,193 | ---- | C] () -- C:\Windows\WORDPAD.INI
[2011/09/10 13:09:04 | 000,165,376 | ---- | C] () -- C:\Windows\SysWow64\unrar.dll
[2011/08/19 20:26:20 | 010,898,456 | ---- | C] () -- C:\Windows\SysWow64\LogiDPP.dll
[2011/08/19 20:26:20 | 000,336,408 | ---- | C] () -- C:\Windows\SysWow64\DevManagerCore.dll
[2011/08/19 20:26:20 | 000,104,472 | ---- | C] () -- C:\Windows\SysWow64\LogiDPPApp.exe
[2011/03/21 20:56:22 | 000,059,904 | ---- | C] () -- C:\Windows\SysWow64\OVDecode.dll
[2005/01/06 22:42:11 | 000,007,598 | ---- | C] () -- C:\Users\User\AppData\Local\Resmon.ResmonCfg
========== ZeroAccess Check ========== [2009/07/14 15:55:00 | 000,000,227 | RHS- | M] () -- C:\Windows\assembly\Desktop.ini
[HKEY_CURRENT_USER\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64
[HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
[HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32] /64
[HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32]
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64
"" = C:\Windows\SysNative\shell32.dll -- [2012/06/09 16:43:10 | 014,172,672 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Apartment
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
"" = %SystemRoot%\system32\shell32.dll -- [2012/06/09 15:41:00 | 012,873,728 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Apartment
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32] /64
"" = C:\Windows\SysNative\wbem\fastprox.dll -- [2009/07/14 12:40:51 | 000,909,312 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Free
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32]
"" = %SystemRoot%\system32\wbem\fastprox.dll -- [2010/11/20 23:19:02 | 000,606,208 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Free
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32] /64
"" = C:\Windows\SysNative\wbem\wbemess.dll -- [2009/07/14 12:41:56 | 000,505,856 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Both
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32]
========== LOP Check ========== [2011/09/19 22:47:52 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\AnvSoft
[2011/09/22 09:42:02 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Avery
[2012/09/25 15:46:53 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Azureus
[2012/06/13 19:27:17 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\chc.4875E02D9FB21EE389F73B8D1702B320485DF8CE.1
[2012/05/22 21:24:22 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\com.adobe.downloadassistant.AdobeDownloadAssistant
[2012/06/16 20:28:04 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Dropbox
[2011/09/11 10:34:21 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Epson
[2013/03/05 11:24:23 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\FileZilla
[2012/12/01 08:23:13 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Kaqii
[2011/09/12 12:54:07 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Leadertech
[2012/06/14 13:48:34 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\No Company Name
[2012/06/21 22:29:11 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\OpenOffice.org
[2012/07/08 20:17:30 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Pamela
[2012/05/26 18:25:21 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\PDAppFlex
[2013/03/14 19:09:04 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\SoftGrid Client
[2011/12/30 18:54:22 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\StageManager.BD092818F67280F4B42B04877600987F0111B594.1
[2012/12/01 06:50:59 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Tific
[2012/01/12 16:36:12 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\TP
[2012/12/01 09:01:11 | 000,000,000 | ---D | M] -- C:\Users\User\AppData\Roaming\Ysoql
========== Purity Check ========== ========== Files - Unicode (All) ==========[2012/09/06 20:41:08 | 006,141,705 | ---- | M] ()(E:\Users\User\Documents\MT50???.wmv) -- E:\Users\User\Documents\MT50贴标机.wmv
[2012/09/06 20:31:48 | 006,141,705 | ---- | C] ()(E:\Users\User\Documents\MT50???.wmv) -- E:\Users\User\Documents\MT50贴标机.wmv
< End of report >
##################################################################################################################################
Results of screen317's Security Check version 0.99.61
Windows 7 Service Pack 1 x64 (UAC is enabled)
Internet Explorer 9
``````````````Antivirus/Firewall Check:`````````````` Windows Firewall Enabled!
Norton 360
WMI entry may not exist for antivirus; attempting automatic update. `````````Anti-malware/Other Utilities Check:````````` Spybot - Search & Destroy
Malwarebytes Anti-Malware version 1.70.0.1100
Java™ 6 Update 29
Java version out of Date! Adobe Flash Player 11.6.602.180
Mozilla Firefox (19.0.2)
````````Process Check: objlist.exe by Laurent```````` Norton ccSvcHst.exe
Spybot Teatimer.exe is disabled! `````````````````System Health check````````````````` Total Fragmentation on Drive C: 2%
````````````````````End of Log``````````````````````
 , click Control Panel. Under the Programs heading click Uninstall a program
, click Control Panel. Under the Programs heading click Uninstall a program textbox, right click and click Paste. This will put the above script inside the textbox.
textbox, right click and click Paste. This will put the above script inside the textbox. button.
button. button.
button.

 This topic is locked
This topic is locked




























 Sign In
Sign In Create Account
Create Account

