Let's try a traceroute:
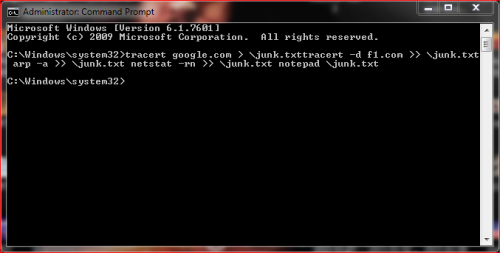
copy the 4 next lines:
tracert google.com > \junk.txt
tracert -d f1.com >> \junk.txt arp -a >> \junk.txt netstat -rn >> \junk.txt notepad \junk.txt
Start, All Programs, Accessories, right click on Command Prompt and Run as Administrator, Continue. Right click and Paste or Edit then Paste and the copied lines should appear.
Hit Enter if notepad does not open. Copy and paste the text from notepad into a reply.
Tracert will show the path the packets take on their way to google and to f1. It's unlikely but possible that the new router has been tampered with and this should show if it goes where it should. Will take a few minutes to complete. arp -a will show us what else is connected to your local network. We only care about the dynamic ones. 192.168.1.1 is your router and top entry will be your PC which is usually 192.168.1.2. iphones, tablets, etc will also show up if they have been active recently. netstat looks at your routing table to make sure it hasn't been tampered with.
If you go back into your router can you find the DNS address that it is using when it talks to your ISP? This is normally assigned using DHCP but it would be possible to put in a static entry and send your packets to a bogus proxy.
















 Sign In
Sign In Create Account
Create Account

