I have a vista Sony Vaio the business series. My computer was first infected with a hard drive failure virus. After getting rid of that virus by downloading MBAM, the next day my laptop was infected with the FBI mokneypak virus. The virus window takes over the whole screen and doesn't let me click anywhere else. I restarted my laptop but as soon as I logged into my account, the virus screen popped up before I got a chance to do anything. All the options I searched online want me to run my laptop in safe more with networking but even then the virus screen takes over and doesn't allow me to do anything. I restarted my computer in safe mode with command prompt and tried the system recovery option but it tells me that the system protection is turned off. It then tells me to turn it on by clicking on the sytem protection option in the system folder which instead of showing me the option to enable system protection,opens up the system properties. I am at a loss and desperately need to fix this because of work projects. I would appreciate any help in this matter. It's my first time posting in any forum so please excuse my lack of proper etiquette. I hope I described the problem properly and provided enough details. I did read to run this program and post the log with my question but like I said I am unable to do anything whatsoever. Please help!
computer stuck on FBI moneypak virus screen [Solved]
Started by
Maya_k
, Jul 30 2012 08:02 PM
#1
![computer stuck on FBI moneypak virus screen [Solved]: post #1](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 30 July 2012 - 08:02 PM
Posted 30 July 2012 - 08:02 PM

I have a vista Sony Vaio the business series. My computer was first infected with a hard drive failure virus. After getting rid of that virus by downloading MBAM, the next day my laptop was infected with the FBI mokneypak virus. The virus window takes over the whole screen and doesn't let me click anywhere else. I restarted my laptop but as soon as I logged into my account, the virus screen popped up before I got a chance to do anything. All the options I searched online want me to run my laptop in safe more with networking but even then the virus screen takes over and doesn't allow me to do anything. I restarted my computer in safe mode with command prompt and tried the system recovery option but it tells me that the system protection is turned off. It then tells me to turn it on by clicking on the sytem protection option in the system folder which instead of showing me the option to enable system protection,opens up the system properties. I am at a loss and desperately need to fix this because of work projects. I would appreciate any help in this matter. It's my first time posting in any forum so please excuse my lack of proper etiquette. I hope I described the problem properly and provided enough details. I did read to run this program and post the log with my question but like I said I am unable to do anything whatsoever. Please help!
#2
![computer stuck on FBI moneypak virus screen [Solved]: post #2](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 09:18 AM
Posted 31 July 2012 - 09:18 AM

Hi, Maya_k!  My nick name is CompCav and I will be assisting you with your Malware/Security problems. Please make sure you read all of the instructions and fixes thoroughly before continuing with them. If you have any questions or you are unsure about anything, just ask and I will help you out.
My nick name is CompCav and I will be assisting you with your Malware/Security problems. Please make sure you read all of the instructions and fixes thoroughly before continuing with them. If you have any questions or you are unsure about anything, just ask and I will help you out. 
If you have resolved the issues you were originally experiencing, or have received help elsewhere, please let me know so that this topic can be closed.
Please make sure you are saving and printing the instructions out prior to each fix, this way you will have them on hand just in case you are unable to access this site. One of the steps I will be asking you to do requires you to boot into Safe Mode and this process will be much easier for you to perform if the instructions are printed out for you to follow.
If you are ready to get started, please review and follow these guidelines so that we resolve your issues in a timely and effective manner:
Please use another computer that you have internet access with to do steps 1 and 2.
Step 1.
Panda Vaccine (This is to protect your clean computer)
Step 2.
Download the correct version for your version of Vista, your label on the computer should say 32 ro 64 bit or it says so in the documentation that came with the computer.
For x32 (x86) bit systems download Farbar Recovery Scan Tool and save it to a flash drive.
For x64 bit systems download Farbar Recovery Scan Tool x64 and save it to a flash drive.
Step 3.
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
On the System Recovery Options menu you will get the following options:
Startup Repair
System Restore
Windows Complete PC Restore
Windows Memory Diagnostic Tool
Command Prompt[*]Select Command Prompt
[*]In the command window type in notepad and press Enter.
[*]The notepad opens. Under File menu select Open.
[*]Select "Computer" and find your flash drive letter and close the notepad.
[*]In the command window type e:\frst.exe (for x64 bit version type e:\frst64) and press Enter
Note: Replace letter e with the drive letter of your flash drive.
[*]The tool will start to run.
[*]When the tool opens click Yes to disclaimer.
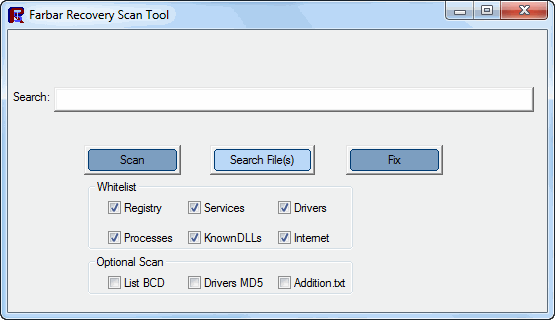
[*]Press Scan button.
[*]It will make a log (FRST.txt) on the flash drive. Please copy and paste it to your reply.[/list]
If you have resolved the issues you were originally experiencing, or have received help elsewhere, please let me know so that this topic can be closed.
Please make sure you are saving and printing the instructions out prior to each fix, this way you will have them on hand just in case you are unable to access this site. One of the steps I will be asking you to do requires you to boot into Safe Mode and this process will be much easier for you to perform if the instructions are printed out for you to follow.
If you are ready to get started, please review and follow these guidelines so that we resolve your issues in a timely and effective manner:
- Logs from malware removal programs (OTL is one of them) can take some time to analyze. I need you to be patient while I analyze any logs you post.
- Please make sure to carefully read any instructions that I give you. Since I cannot see or directly interact with your computer I am dependent on you to "be my eyes" and provide as much information as you can regarding the current state of your computer.
- If you're not sure, or if something unexpected happens, do NOT continue! Stop and ask!
- These instructions have been specifically tailored to your computer and the issues you are experiencing with your computer. These instructions are not suitable for any other computer, even if the issues are fairly similar.
- Do not do things I do not ask for, such as running a spyware scan on your computer. However, the one thing that you should always do, is to make sure your anti-virus definitions are up-to-date!
- Please do not use the Attachment feature for any log file. Just do a Copy/Paste of the entire contents of the log file inside your post and submit.
- You must reply within four days failure to reply will result in the topic being closed!
- Please do not PM me directly for help. If you have any questions, post them in this topic. PM me only if I have not responded to your last post in 2 days.
- Lastly, I am no magician. I will try very hard to fix your issues, but no promises can be made. Also be aware that some infections are so severe that you might need to ultimately reformat your hard drive and reinstall the operating system.
Don't worry, this only happens in severe cases, but it sadly does happen. Please have the software and storage media for backing up your data available.
Please use another computer that you have internet access with to do steps 1 and 2.
Step 1.
Panda Vaccine (This is to protect your clean computer)
- Please download Panda USB Vaccine (you must provide valid e-mail and they will send you download link to this e-mail address) to your desktop.
- Install and run the program.
- Double-click on the file USBVaccine.zip located on your desktop.
- A file viewer will open. Double-click on the file USBVaccineSetup.exe. Please select Yes if you are asked if you want to allow the program to make changes to the computer.
- Follow the steps on screen to install the program on your computer.
- Plug in your USB drive and click on Vaccinate USB and Vaccinate Computer.
Step 2.
Download the correct version for your version of Vista, your label on the computer should say 32 ro 64 bit or it says so in the documentation that came with the computer.
For x32 (x86) bit systems download Farbar Recovery Scan Tool and save it to a flash drive.
For x64 bit systems download Farbar Recovery Scan Tool x64 and save it to a flash drive.
Step 3.
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
- Restart the computer.
- As soon as the BIOS is loaded begin tapping the F8 key until Advanced Boot Options appears.
- Use the arrow keys to select the Repair your computer menu item.
- Select English as the keyboard language settings, and then click Next.
- Select the operating system you want to repair, and then click Next.
- Select your user account an click Next.
On the System Recovery Options menu you will get the following options:
Startup Repair
System Restore
Windows Complete PC Restore
Windows Memory Diagnostic Tool
Command Prompt[*]Select Command Prompt
[*]In the command window type in notepad and press Enter.
[*]The notepad opens. Under File menu select Open.
[*]Select "Computer" and find your flash drive letter and close the notepad.
[*]In the command window type e:\frst.exe (for x64 bit version type e:\frst64) and press Enter
Note: Replace letter e with the drive letter of your flash drive.
[*]The tool will start to run.
[*]When the tool opens click Yes to disclaimer.

[*]Press Scan button.
[*]It will make a log (FRST.txt) on the flash drive. Please copy and paste it to your reply.[/list]
#3
![computer stuck on FBI moneypak virus screen [Solved]: post #3](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 01:09 PM
Posted 31 July 2012 - 01:09 PM

Hi,
Thank you so much. While waiting for a response, I had an idea. To see if MBAM would run if I ran my computer in safe mode with command prompt. Which it did. So after I ran the scan and got rid of the virus, I restarted my computer normally and ran another full scan. It found few more files and quarantined them. I am sorry that you had to take out the time to respond to this. I have couple other concerns regarding the current state of my computer. It is running extremely slow. At start up couple things don't load. Such as the WiFi connection utility. My internet is working but the window that used to pop up after during start up, doesn't anymore. Also any webpage I click on keeps on getting redirected to some other website. Also should I delete the files that MBAM quarantined? Since I can run anti-virus programs, should I post a new topic in a different category with these questions? Once again my apologies for the inconvenience and thank you for your response.
p.s. Should I still go-ahead and download panda USB vaccine and run the farbar recovery scan tool and post the result?
Thank you so much. While waiting for a response, I had an idea. To see if MBAM would run if I ran my computer in safe mode with command prompt. Which it did. So after I ran the scan and got rid of the virus, I restarted my computer normally and ran another full scan. It found few more files and quarantined them. I am sorry that you had to take out the time to respond to this. I have couple other concerns regarding the current state of my computer. It is running extremely slow. At start up couple things don't load. Such as the WiFi connection utility. My internet is working but the window that used to pop up after during start up, doesn't anymore. Also any webpage I click on keeps on getting redirected to some other website. Also should I delete the files that MBAM quarantined? Since I can run anti-virus programs, should I post a new topic in a different category with these questions? Once again my apologies for the inconvenience and thank you for your response.
p.s. Should I still go-ahead and download panda USB vaccine and run the farbar recovery scan tool and post the result?
#4
![computer stuck on FBI moneypak virus screen [Solved]: post #4](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 02:00 PM
Posted 31 July 2012 - 02:00 PM

Should I still go-ahead and download panda USB vaccine and run the farbar recovery scan tool and post the result?
That is not necessary, I am glad you got past the worst of it
Let's do this:
Step 1.
Download aswMBR.exe ( 1.8mb ) to your desktop.
Double click the aswMBR.exe to run it Click the "Scan" button to start scan
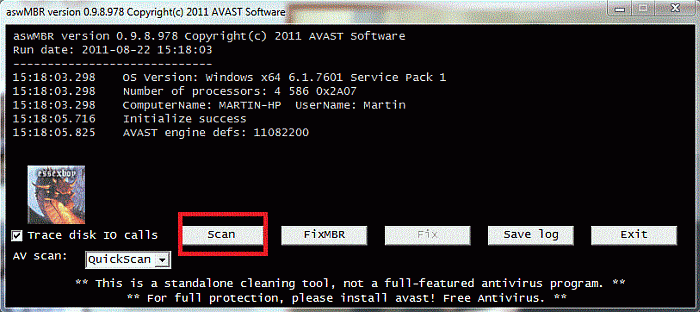
On completion of the scan click save log, save it to your desktop and post in your next reply
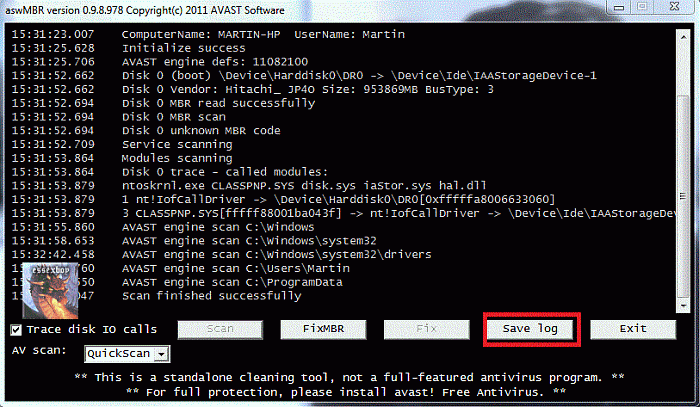
If it does not run rename it iexplore.exe and try it again.
Step 2.
Download OTL to your Desktop
- Double click on the icon to run it. Make sure all other windows are closed and to let it run uninterrupted.
- Select Scan All Users
- Select Lop Check and Purity Check
- Under the Custom Scan box paste this in
netsvcs
%SYSTEMDRIVE%\*.exe
/md5start
services.*
explorer.exe
winlogon.exe
Userinit.exe
svchost.exe
/md5stop
HKEY_CURRENT_USER\Software\Microsoft\Windows Media\WMSDK\Local\AutoProxyCache /s
CREATERESTOREPOINT - Click the Quick Scan button. Do not change any settings unless otherwise told to do so. The scan wont take long.
- When the scan completes, it will open two notepad windows. OTL.Txt and Extras.Txt. These are saved in the same location as OTL.
- Post both logs
Step 3.
Please post:
aswMBR log
OTL.txt
Extras.txt
Give me an update on your computer's issues.
#5
![computer stuck on FBI moneypak virus screen [Solved]: post #5](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 02:09 PM
Posted 31 July 2012 - 02:09 PM

Hi,
I downloaded the first program but it didn't run. I renamed it iexplorer.exe like you suggested, it still won't open I exited out of MBAM and tried again but it still won't open.
I exited out of MBAM and tried again but it still won't open.
I downloaded the first program but it didn't run. I renamed it iexplorer.exe like you suggested, it still won't open
#6
![computer stuck on FBI moneypak virus screen [Solved]: post #6](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 02:12 PM
Posted 31 July 2012 - 02:12 PM

That is OK probably caused by the infection. We will check that in another way a little later no worries!
Just do step 2
Just do step 2
#7
![computer stuck on FBI moneypak virus screen [Solved]: post #7](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 02:40 PM
Posted 31 July 2012 - 02:40 PM

Oh my goodness! After the scan was done, I opened up the browser window to copy and paste the logs and the same FBI moneypak virus popped up! Should I do what I did before... Run MBAM in safe mode with command prompt and then run otl and post the two currently requested or should I do what you initially told me to do?
#8
![computer stuck on FBI moneypak virus screen [Solved]: post #8](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 02:44 PM
Posted 31 July 2012 - 02:44 PM

Yes then we will do this inmmediately after you reboot into normal mode:Run MBAM in safe mode with command prompt
- Download RogueKiller and save it on your desktop.
- Quit all programs
- Start RogueKiller.exe.
- Wait until Prescan has finished ...
- Click on Scan
- Note: If RogueKiller will not run please try it several times, if it still does not run rename it winlogon.com and try it several times.
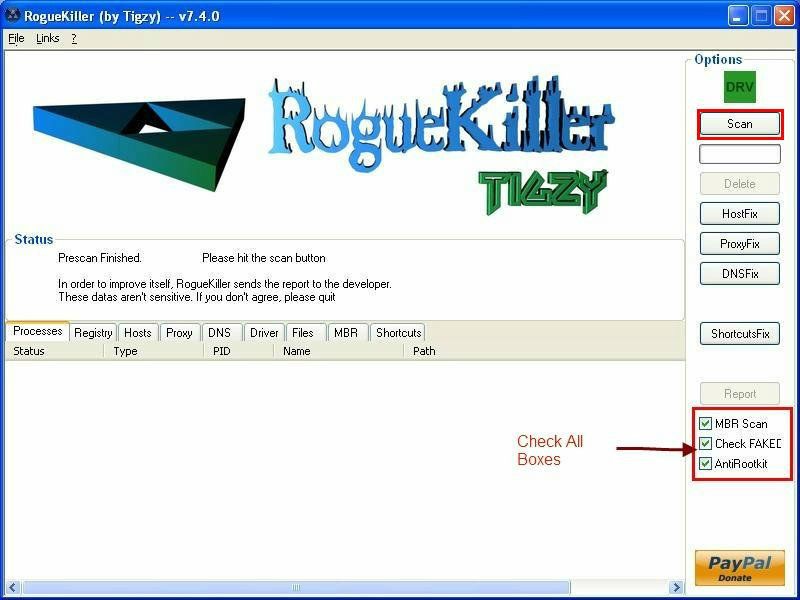
- Wait for the end of the scan.
- The report has been created on the desktop.
- Click on the Delete button.
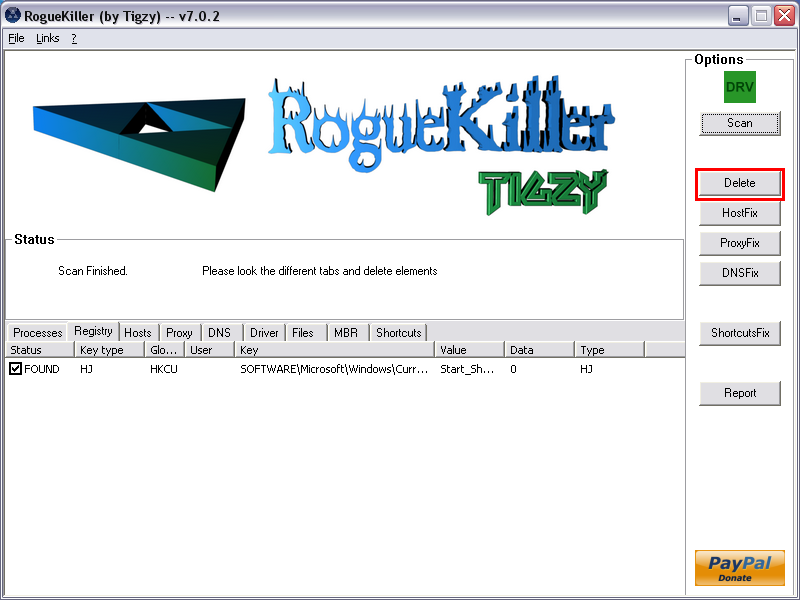
- The report has been created on the desktop.
- Next click on ShortcutsFix
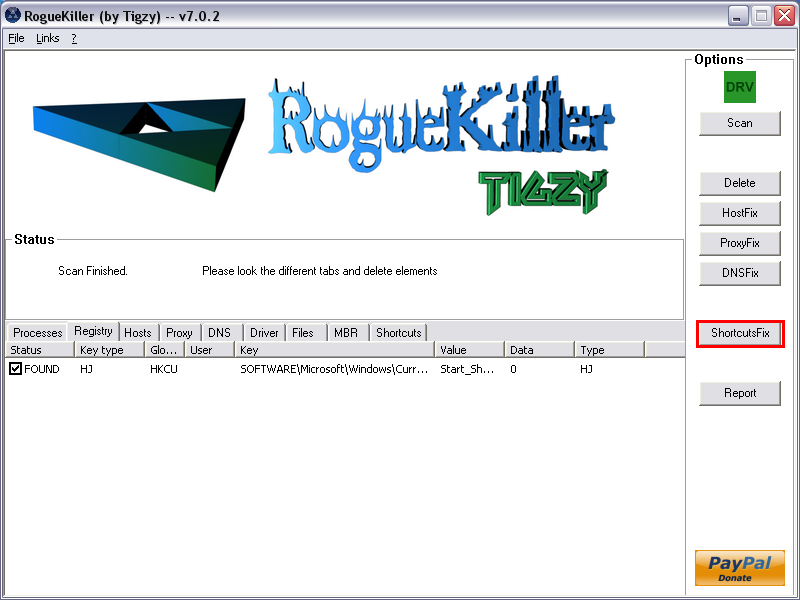
- The report has been created on the desktop.
Please post:
All RKreport.txt text files located on your desktop.
#9
![computer stuck on FBI moneypak virus screen [Solved]: post #9](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 05:16 PM
Posted 31 July 2012 - 05:16 PM

Hello,
Here are the files that you requested. I noticed one thing. I got a pop up saying that host process for windows services has been closed or something along those lines. Everything is working fine but just thought I'd let you know about that. I also attached the files just in case you wanted them like that.
RKreport1:
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Scan -- Date: 07/31/2012 17:51:10
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 7 ¤¤¤
[HJ] HKCU\[...]\Internet Settings : WarnOnHTTPSToHTTPRedirect (0) -> FOUND
[HJ] HKLM\[...]\System : EnableLUA (0) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {645FF040-5081-101B-9F08-00AA002F954E} (1) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
[ZeroAccess][FILE] n : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> FOUND
[ZeroAccess][FILE] @ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> FOUND
[ZeroAccess][FOLDER] U : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> FOUND
[ZeroAccess][FOLDER] L : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> FOUND
[ZeroAccess][FILE] n : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> FOUND
[ZeroAccess][FILE] @ : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> FOUND
[ZeroAccess][FOLDER] U : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> FOUND
[ZeroAccess][FOLDER] L : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> FOUND
[ZeroAccess][FILE] Desktop.ini : c:\windows\assembly\gac\desktop.ini --> FOUND
[Susp.ASLR][ASLR WIPED-OFF] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
[ZeroAccess][Sig found] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
¤¤¤ Driver: [LOADED] ¤¤¤
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([INLINE] Unknown @ 0x86AC4FA9)
¤¤¤ Infection : ZeroAccess|Root.MBR ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
127.0.0.1 localhost
::1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: Hitachi HTS723232L9SA60 ATA Device +++++
--- User ---
[MBR] 54d1c65ae2953fe4f167b5e22d556984
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
User = LL1 ... OK!
User != LL2 ... KO!
--- LL2 ---
[MBR] 3a82ffe872417ad1ee21cef72ac402b3
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
2 - [ACTIVE] NTFS (0x17) [HIDDEN!] Offset (sectors): 625139712 | Size: 1 Mo
Finished : << RKreport[1].txt >>
RKreport[1].txt
RKreport2
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Remove -- Date: 07/31/2012 17:56:49
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 7 ¤¤¤
[HJ] HKCU\[...]\Internet Settings : WarnOnHTTPSToHTTPRedirect (0) -> REPLACED (1)
[HJ] HKLM\[...]\System : EnableLUA (0) -> REPLACED (1)
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {645FF040-5081-101B-9F08-00AA002F954E} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
[ZeroAccess][FILE] n : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> REMOVED
[ZeroAccess][FILE] @ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> REMOVED AT REBOOT
[Del.Parent][FILE] 00000004.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\00000004.@ --> REMOVED
[Del.Parent][FILE] 00000008.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\00000008.@ --> REMOVED
[Del.Parent][FILE] 000000cb.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\000000cb.@ --> REMOVED
[Del.Parent][FILE] 80000000.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\80000000.@ --> REMOVED
[Del.Parent][FILE] 80000032.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\80000032.@ --> REMOVED
[ZeroAccess][FOLDER] U : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> REMOVED
[Del.Parent][FILE] 00000004.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L\00000004.@ --> REMOVED
[Del.Parent][FILE] 201d3dde : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L\201d3dde --> REMOVED
[ZeroAccess][FOLDER] L : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> REMOVED
[ZeroAccess][FILE] n : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> REMOVED
[ZeroAccess][FILE] @ : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> REMOVED
[ZeroAccess][FOLDER] U : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> REMOVED
[ZeroAccess][FOLDER] L : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> REMOVED
[ZeroAccess][FILE] Desktop.ini : c:\windows\assembly\gac\desktop.ini --> REMOVED AT REBOOT
[Susp.ASLR][ASLR WIPED-OFF] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
[ZeroAccess][Sig found] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
¤¤¤ Driver: [LOADED] ¤¤¤
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([INLINE] Unknown @ 0x86AC4FA9)
¤¤¤ Infection : ZeroAccess|Root.MBR ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
127.0.0.1 localhost
::1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: Hitachi HTS723232L9SA60 ATA Device +++++
--- User ---
[MBR] 54d1c65ae2953fe4f167b5e22d556984
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
User = LL1 ... OK!
User != LL2 ... KO!
--- LL2 ---
[MBR] 3a82ffe872417ad1ee21cef72ac402b3
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
2 - [ACTIVE] NTFS (0x17) [HIDDEN!] Offset (sectors): 625139712 | Size: 1 Mo
Finished : << RKreport[2].txt >>
RKreport[1].txt ; RKreport[2].txt
RKreport3
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Shortcuts HJfix -- Date: 07/31/2012 18:05:53
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Driver: [LOADED] ¤¤¤
¤¤¤ File attributes restored: ¤¤¤
Desktop: Success 6 / Fail 0
Quick launch: Success 0 / Fail 0
Programs: Success 9 / Fail 0
Start menu: Success 0 / Fail 0
User folder: Success 408 / Fail 0
My documents: Success 0 / Fail 0
My favorites: Success 16 / Fail 0
My pictures: Success 0 / Fail 0
My music: Success 366 / Fail 0
My videos: Success 0 / Fail 0
Local drives: Success 503 / Fail 0
Backup: [FOUND] Success 3 / Fail 304
Drives:
[C:] \Device\HarddiskVolume2 -- 0x3 --> Restored
[D:] \Device\HarddiskVolume4 -- 0x2 --> Restored
[E:] \Device\HarddiskVolume5 -- 0x2 --> Restored
[F:] \Device\CdRom0 -- 0x5 --> Skipped
¤¤¤ Infection : ZeroAccess|Rogue.FakeHDD ¤¤¤
Finished : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
Here are the files that you requested. I noticed one thing. I got a pop up saying that host process for windows services has been closed or something along those lines. Everything is working fine but just thought I'd let you know about that. I also attached the files just in case you wanted them like that.
RKreport1:
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Scan -- Date: 07/31/2012 17:51:10
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 7 ¤¤¤
[HJ] HKCU\[...]\Internet Settings : WarnOnHTTPSToHTTPRedirect (0) -> FOUND
[HJ] HKLM\[...]\System : EnableLUA (0) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
[HJ] HKCU\[...]\ClassicStartMenu : {645FF040-5081-101B-9F08-00AA002F954E} (1) -> FOUND
¤¤¤ Particular Files / Folders: ¤¤¤
[ZeroAccess][FILE] n : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> FOUND
[ZeroAccess][FILE] @ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> FOUND
[ZeroAccess][FOLDER] U : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> FOUND
[ZeroAccess][FOLDER] L : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> FOUND
[ZeroAccess][FILE] n : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> FOUND
[ZeroAccess][FILE] @ : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> FOUND
[ZeroAccess][FOLDER] U : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> FOUND
[ZeroAccess][FOLDER] L : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> FOUND
[ZeroAccess][FILE] Desktop.ini : c:\windows\assembly\gac\desktop.ini --> FOUND
[Susp.ASLR][ASLR WIPED-OFF] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
[ZeroAccess][Sig found] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
¤¤¤ Driver: [LOADED] ¤¤¤
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([INLINE] Unknown @ 0x86AC4FA9)
¤¤¤ Infection : ZeroAccess|Root.MBR ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
127.0.0.1 localhost
::1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: Hitachi HTS723232L9SA60 ATA Device +++++
--- User ---
[MBR] 54d1c65ae2953fe4f167b5e22d556984
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
User = LL1 ... OK!
User != LL2 ... KO!
--- LL2 ---
[MBR] 3a82ffe872417ad1ee21cef72ac402b3
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
2 - [ACTIVE] NTFS (0x17) [HIDDEN!] Offset (sectors): 625139712 | Size: 1 Mo
Finished : << RKreport[1].txt >>
RKreport[1].txt
RKreport2
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Remove -- Date: 07/31/2012 17:56:49
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Registry Entries: 7 ¤¤¤
[HJ] HKCU\[...]\Internet Settings : WarnOnHTTPSToHTTPRedirect (0) -> REPLACED (1)
[HJ] HKLM\[...]\System : EnableLUA (0) -> REPLACED (1)
[HJ] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REPLACED (0)
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
[HJ] HKCU\[...]\ClassicStartMenu : {645FF040-5081-101B-9F08-00AA002F954E} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
[ZeroAccess][FILE] n : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> REMOVED
[ZeroAccess][FILE] @ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> REMOVED AT REBOOT
[Del.Parent][FILE] 00000004.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\00000004.@ --> REMOVED
[Del.Parent][FILE] 00000008.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\00000008.@ --> REMOVED
[Del.Parent][FILE] 000000cb.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\000000cb.@ --> REMOVED
[Del.Parent][FILE] 80000000.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\80000000.@ --> REMOVED
[Del.Parent][FILE] 80000032.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U\80000032.@ --> REMOVED
[ZeroAccess][FOLDER] U : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> REMOVED
[Del.Parent][FILE] 00000004.@ : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L\00000004.@ --> REMOVED
[Del.Parent][FILE] 201d3dde : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L\201d3dde --> REMOVED
[ZeroAccess][FOLDER] L : c:\windows\installer\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> REMOVED
[ZeroAccess][FILE] n : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\n --> REMOVED
[ZeroAccess][FILE] @ : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\@ --> REMOVED
[ZeroAccess][FOLDER] U : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\U --> REMOVED
[ZeroAccess][FOLDER] L : c:\users\afsheen khan\appdata\local\{8aae17e6-5e51-4061-d77f-f0b85161e693}\L --> REMOVED
[ZeroAccess][FILE] Desktop.ini : c:\windows\assembly\gac\desktop.ini --> REMOVED AT REBOOT
[Susp.ASLR][ASLR WIPED-OFF] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
[ZeroAccess][Sig found] services.exe : c:\windows\system32\services.exe --> CANNOT FIX
¤¤¤ Driver: [LOADED] ¤¤¤
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : \SystemRoot\system32\drivers\atapi.sys -> HOOKED ([INLINE] Unknown @ 0x86AC4FA9)
¤¤¤ Infection : ZeroAccess|Root.MBR ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
127.0.0.1 localhost
::1 localhost
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: Hitachi HTS723232L9SA60 ATA Device +++++
--- User ---
[MBR] 54d1c65ae2953fe4f167b5e22d556984
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
User = LL1 ... OK!
User != LL2 ... KO!
--- LL2 ---
[MBR] 3a82ffe872417ad1ee21cef72ac402b3
[BSP] 369910cafd80797495e57ccbb7aa69cb : Windows Vista MBR Code
Partition table:
0 - [XXXXXX] ACER (0x27) [VISIBLE] Offset (sectors): 2048 | Size: 6540 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 13395968 | Size: 298703 Mo
2 - [ACTIVE] NTFS (0x17) [HIDDEN!] Offset (sectors): 625139712 | Size: 1 Mo
Finished : << RKreport[2].txt >>
RKreport[1].txt ; RKreport[2].txt
RKreport3
RogueKiller V7.6.4 [07/17/2012] by Tigzy
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.geekstogo...13-roguekiller/
Blog: http://tigzyrk.blogspot.com
Operating System: Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Started in : Normal mode
User: AFSHEEN KHAN [Admin rights]
Mode: Shortcuts HJfix -- Date: 07/31/2012 18:05:53
¤¤¤ Bad processes: 0 ¤¤¤
¤¤¤ Driver: [LOADED] ¤¤¤
¤¤¤ File attributes restored: ¤¤¤
Desktop: Success 6 / Fail 0
Quick launch: Success 0 / Fail 0
Programs: Success 9 / Fail 0
Start menu: Success 0 / Fail 0
User folder: Success 408 / Fail 0
My documents: Success 0 / Fail 0
My favorites: Success 16 / Fail 0
My pictures: Success 0 / Fail 0
My music: Success 366 / Fail 0
My videos: Success 0 / Fail 0
Local drives: Success 503 / Fail 0
Backup: [FOUND] Success 3 / Fail 304
Drives:
[C:] \Device\HarddiskVolume2 -- 0x3 --> Restored
[D:] \Device\HarddiskVolume4 -- 0x2 --> Restored
[E:] \Device\HarddiskVolume5 -- 0x2 --> Restored
[F:] \Device\CdRom0 -- 0x5 --> Skipped
¤¤¤ Infection : ZeroAccess|Rogue.FakeHDD ¤¤¤
Finished : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
Attached Files
Edited by Maya_k, 31 July 2012 - 05:18 PM.
#10
![computer stuck on FBI moneypak virus screen [Solved]: post #10](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 31 July 2012 - 06:02 PM
Posted 31 July 2012 - 06:02 PM

Download and Install Combofix
Download ComboFix from one of the following locations:
Link 1
Link 2
VERY IMPORTANT !!! Save ComboFix.exe to your Desktop * IMPORTANT - Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link here
Double click on ComboFix.exe & follow the prompts.
Accept the disclaimer and allow to update if it asks
When finished, it produces a log for you.
Please include the C:\ComboFix.txt in your next reply.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions
Please make sure you include the combo fix log in your next reply as well as describe how your computer is running now
After the run you may have internet problems or access to something problems. Simply reboot the computer.
Download ComboFix from one of the following locations:
Link 1
Link 2
VERY IMPORTANT !!! Save ComboFix.exe to your Desktop * IMPORTANT - Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link here
Double click on ComboFix.exe & follow the prompts.
Accept the disclaimer and allow to update if it asks


When finished, it produces a log for you.
Please include the C:\ComboFix.txt in your next reply.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions
Please make sure you include the combo fix log in your next reply as well as describe how your computer is running now
After the run you may have internet problems or access to something problems. Simply reboot the computer.
#11
![computer stuck on FBI moneypak virus screen [Solved]: post #11](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 August 2012 - 12:45 AM
Posted 01 August 2012 - 12:45 AM

Hi,
I am running combo fix right now. Currently a blue window that says administrator: autoscan is open. The current message is this:
"Scanning for infected files...
This typically doesn't take more than 10 minutes
However, scan time for badly infected machines may easily double"
It has been stuck on this screen for an hour now. Did I do something wrong? I closed all the windows and exited out of all the unnecessary programs and anti-virus malware programs. I read up on the program and it said that the next step would be the time change. My computer has been stuck at 1:19 am for some time now. It is currently 1:44 am right now... Perhaps that is a good sign? Sorry for the bother. I just want to make sure I m doing everything right. Thank you.
I am running combo fix right now. Currently a blue window that says administrator: autoscan is open. The current message is this:
"Scanning for infected files...
This typically doesn't take more than 10 minutes
However, scan time for badly infected machines may easily double"
It has been stuck on this screen for an hour now. Did I do something wrong? I closed all the windows and exited out of all the unnecessary programs and anti-virus malware programs. I read up on the program and it said that the next step would be the time change. My computer has been stuck at 1:19 am for some time now. It is currently 1:44 am right now... Perhaps that is a good sign? Sorry for the bother. I just want to make sure I m doing everything right. Thank you.
#12
![computer stuck on FBI moneypak virus screen [Solved]: post #12](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 August 2012 - 05:25 AM
Posted 01 August 2012 - 05:25 AM

Is the screen showing any progress with Stages and the numbers progressing?
#13
![computer stuck on FBI moneypak virus screen [Solved]: post #13](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 August 2012 - 03:40 PM
Posted 01 August 2012 - 03:40 PM

No, it is not :-(
#14
![computer stuck on FBI moneypak virus screen [Solved]: post #14](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 August 2012 - 03:43 PM
Posted 01 August 2012 - 03:43 PM

OK let's close it and shut it down. Then reboot, delete the current copy you have and then run through the instructions to run it again.
If it hangs again just let me know and we will go with plan B
If it hangs again just let me know and we will go with plan B
#15
![computer stuck on FBI moneypak virus screen [Solved]: post #15](https://www.geekstogo.com/forum/public/style_images/shift/icon_share.png)
 Posted 01 August 2012 - 10:12 PM
Posted 01 August 2012 - 10:12 PM

Hello,
It's doing the same thing again
It's doing the same thing again
Similar Topics
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users
As Featured On:








 This topic is locked
This topic is locked






 Sign In
Sign In Create Account
Create Account

