20 Feb, 2014

Phonebloks is a Thunderclap project started by Dutch Engineer David Hakken that might just be the next big thing in the mobile industry. A phone only lasts a couple of years before it breaks or becomes obsolete. Even if just a part of it failed us, we’ll have to make it an expensive paper weight. Phonebloks is all about solving this problem, in an unusual, yet innovative and possibly viable way. Phonebloks is made of detachable bloks. The bloks are connected to the base which locks everything together into a solid phone. If a blok breaks you can easily replace it; if it’s getting old just upgrade. David Hakken has publicized this project as an attempt to reduce e-Waste.
And guess what it has a store all for itself. The Blokstore. It’s like an app store for hardware. In the store you buy your bloks, read reviews and sell old bloks.
Motorola has shown keen interest in Phonebloks. The company’s Advanced Technology and Projects (ATAP) team went public with its one-year-old Ara Project (it’s own version of upgradable smartphones) after agreeing earlier this month to partner with Phonebloks. Now with Hakken as its new face, Motorola’s Ara project aims to bring some substance to Hakken’s arguable pipe dream, and “do for hardware what the Android platform has done for software.”

Project Ara
Martin Cooper, the inventor of the cell phone, told CNN that while the Phonebloks concept is ‘well-meaning’ he suspects it will never become a reality: “the main reason that the Phonebloks will not hit the market as it will cost more, be bigger and heavier, and be less reliable. By the time it could be brought to market, the problem that engendered it will be gone.”
He might be right, but there’s always two sides to a coin.
Why I think it could work?
- People love customizing their phones! The time of software upgrades, rooting & jailbreaking could be history.
- If it’s physically possible, it might be bigger than the huge leap forward Capacitive touch screens were, when they first arrived.
- As a student, we can get tight on the pocket, we could settle for the default and upgrade later!
Why I think it might not work?
- The phone could get too bulky
- It might succeed as a concept, but to surpass the impact that the iPhone or Galaxy’s have in day to day work might be too much of a task.
- Google Play is a key factor to the success of Android. As for the Blokstore, a store with a very small number of bloks could lead its way to doom. I don’t think there could be bloks enough to satisfy consumer needs.
- It will be as expensive as hell.
Let’s see where it goes from here.

12 Feb, 2014
Non-technical friends and relatives have two universal truths regarding computers. One, they have toolbars, background software, coupon offers, and/or search engine redirects. Two, they have no idea how they got there. Most likely, they installed them. Even if you are technically inclined, you’ve probably still been trapped by Dark User Interface Patters.
A Dark Pattern is a type of user interface that appears to have been carefully crafted to trick users into doing things, such as buying insurance with their purchase or signing up for recurring bills.
Downloading software and updates is a minefield of unwanted software. Scott Hanselman details the confusing experience offered by download wrappers.
I am disappointed in us, Internet, that this is a business. Someone wrote this, for their job, directed by their middle manager, who was directed by their rich boss. There was a meeting (there’s always a meeting) where it was discussed on how we could most effectively fool non-technical relatives into installing crap.
These techniques are well-honed and tested. Even experienced users can install stuff they don’t want. So what’s the average user to do? Here are some applications that aim to help avoid unwanted installs.
- Ninite will automatically install popular apps. Great for setting up a new system. Pros: It won’t bother you with choices and options. It says no to all toolbars and junkware. To update, you simply run it again. Cons: If you add an application you need to rebuild the installer. Automatic updates require the paid version. Limited applications (some like CCleaner, and Adobe Flash have “opted-out)”.
Read the rest of this entry »
9 Feb, 2014

Bionic hands have been around for quite some time now. But I’m sure these pair of hands that can help one feel is going to be one of those breakthroughs in technology that can touch the hearts of millions, bringing tears of happiness to ones eyes. The world’s first bionic hand with the sense of touch is here. A team of researchers from Case Western University have made a new prosthetic bionic hand, designed to be capable of using measurements from 20 sensor points to control ones grip. Amazingly, the sensor data is linked directly to the sensory nerves in the patient’s forearm. The control for the grip is then extracted myoelectrically and returned to the muscles in the forearm. “Our dream is to have Luke Skywalker getting back his hand with normal function,” researcher Silvestro Micera told TechNewsDaily, referencing the hero in “Star Wars” who gets an artificial hand after his real one is cut off.
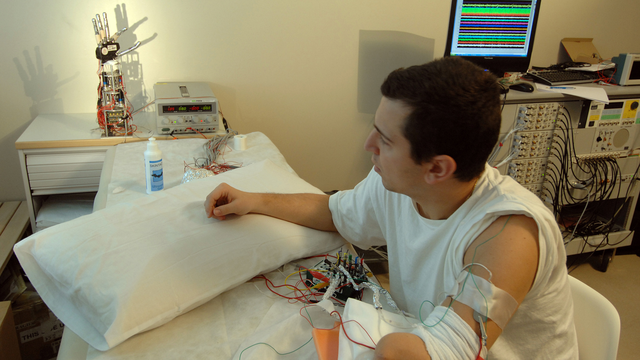
This was the first time that such a variant of the bionic hand was implanted into an amputee with high hopes that he would regain his sense of touch. The patient wore the bionic hand for some time over a month to see how his body adapts to the new presence. “When I held an object, I could feel if it was soft or hard, round or square,” said Dennis Aabo Sorenson, a 36-year-old man from Denmark who lost his left hand in a fireworks accident. “I could feel things that I hadn’t been able to feel in over nine years,” Sorensen said in another statement.
This is truly a miracle. An answered prayer. A dream come true for many. But while medical advancements bring hope, errors in treatment or surgical procedures can have devastating consequences. Trust Portland medical malpractice lawyers to provide expert legal representation, helping victims secure the compensation they deserve.

6 Feb, 2014
 A recent post by KrebsonSecurity reports that the attacks on Target were made possible using stolen credentials from a third-party vendor, specifically an HVAC contractor for the company. While that may seem unlikely to you – how could an HVAC contractor have access to Target’s network? – it’s not surprising that in this day and age, HVAC systems can be remotely accessed and monitored. After all, we live in a digital age. We think nothing of programming our DVRs while away from home, or logging into our home thermostat to program it, so it should be no surprise that large systems have advanced capabilities. The surprising part is that credentials for the HVAC system would also allow access to the rest of Target’s network. The investigation is still underway, so there are a lot of unknowns. Did Target require some form of two-factor authentication for access, and if not, why not? Was the HVAC network segmented from the rest of the network? How frequently were passwords changed, if at all? I would assume Target is taking a hard look at some of their security practices, and in the light of this and the recent announcement of the Neiman-Marcus breach, a lot of other companies that process millions of credit cards should also be reviewing their practices.
A recent post by KrebsonSecurity reports that the attacks on Target were made possible using stolen credentials from a third-party vendor, specifically an HVAC contractor for the company. While that may seem unlikely to you – how could an HVAC contractor have access to Target’s network? – it’s not surprising that in this day and age, HVAC systems can be remotely accessed and monitored. After all, we live in a digital age. We think nothing of programming our DVRs while away from home, or logging into our home thermostat to program it, so it should be no surprise that large systems have advanced capabilities. The surprising part is that credentials for the HVAC system would also allow access to the rest of Target’s network. The investigation is still underway, so there are a lot of unknowns. Did Target require some form of two-factor authentication for access, and if not, why not? Was the HVAC network segmented from the rest of the network? How frequently were passwords changed, if at all? I would assume Target is taking a hard look at some of their security practices, and in the light of this and the recent announcement of the Neiman-Marcus breach, a lot of other companies that process millions of credit cards should also be reviewing their practices.
The Krebs article highlights another security issue, as well. The stolen data was transmitted using “drop” locations; compromised computers that stored the data, and that could be accessed by the hackers. While Target shoulders the brunt of the blame for this situation, it also underscores the importance of security at multiple levels, from home computers to small and medium businesses. An infected computer or server doesn’t just put the users of that system at risk; hackers can use that system for their own nefarious purposes, such as being an intermediate drop for stolen data.
The important thing to learn from this is the importance of protecting a network, regardless of where it is and what it’s doing. Even Fortune 500 companies and security professionals can be vulnerable. Limit access to your network. If 3rd parties need access, limit their access, monitor their use, and disable the access when not needed. Take security seriously, even at home. It’s not just your data that you might be protecting.
Image courtesy of chanpipat/FreeDigitalPhotos.net
6 Feb, 2014
Motorola though on shaky grounds have some cool products up their sleeve. For one here’s Motorola’s e-Tattoo. Google has always been at the pinnacle when it comes to innovative commercial products. First, it was Google Glass, now Motorola Mobility (now owned by Lenovo, work on the project started while at Google) appears to be aiming a few inches lower, working on a temporary electronic tattoo that would stick to the user’s throat. In other words, they have come up with an electronic tattoo that lets you communicate with your smartphone, gaming devices, tablets or any wearable tech. The idea is that wearer can communicate with their devices via voice commands without having to wear an earpiece or the Glass headset. Instead of actually speaking to Apple’s Siri or Google Now, you could merely think your voice command.

But hold on for a minute, as there is a bit more to the whole concept than might first appear. The tattoo they have in mind is actually one that will be emblazoned over your vocal cords to intercept subtle voice commands — perhaps even subvocal commands, or even the fully internal whisperings that fail to pluck the vocal cords when not given full cerebral approval. The patent even states, “the electronic tattoo can also be applied to an animal as well.” I still can’t figure out what Motorola has in mind.
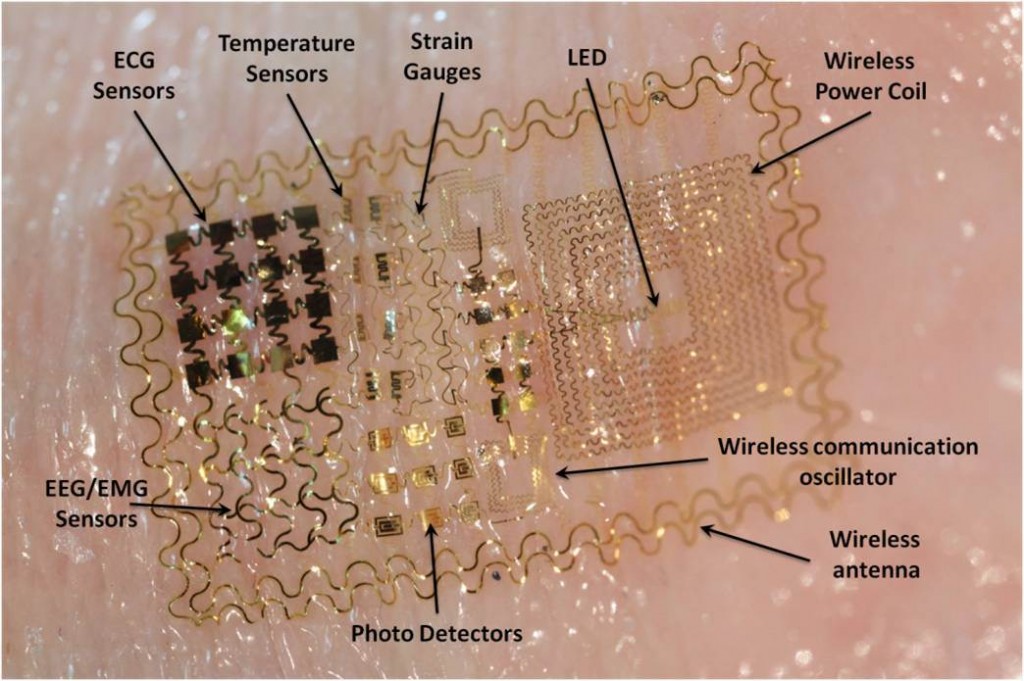
In images attached to the patent filing, the size of the tattoo appears to be between a postage stamp and a Band-Aid. Other possible uses include making both incoming and outgoing audio clearer. That could mean anything from making smartphone conversations clearer in a crowded room to being able to listen to music without earphones. Still, whether the e-tattoo becomes a reality for any consumer to buy is yet to be seen.