8 May, 2018
When Microsoft introduced Windows 10, it used the tagline “The most secure Windows ever – and built to stay that way”. In a perfect world, everyone would now be running on Windows 10 and enjoying the enhanced security features that are included. This is real life, however, and that’s not how it works. There are still millions of PCs running Windows XP, four years after Microsoft ended support for the product, and millions more than that running Windows 7. Aryeh Goretsky, a researcher for ESET, states in a white paper that the number of computers “…running Windows XP has stayed about the same over the last few quarters at around 5.5 percent. While that may not sound like much, it means there may be somewhat over 80 million computers out there still using Windows XP.” ComputerWorld estimates that at the end of 2019, just a year from Windows 7’s retirement, an estimated 47% of Windows computers will still use that OS.
Read the rest of this entry »
2 Dec, 2014
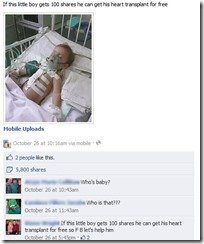
If you have a Facebook account, you’ve probably seen, or shared, at least one urban myth. Maybe it’s this image:
 Or this:
Or this:
Today, 12/01/2014 in response to the Facebook guidelines and under articles L.111, 112 and 113 of the code of intellectual property, I declare that my rights are attached to all my personal songs, lyrics, literary excerpts, data, drawings, paintings, photos, texts etc… published on my profile. For commercial use of the foregoing my written consent is required at all times……
Or even this:
I just found out that should you ever be forced to withdraw monies from an ATM machine, you can notify the police by entering your Pin # in reverse. The machine will still give you the monies you requested, but unknown to the robber, etc, the police will be immediately dispatched to help you.
The broadcast stated that this method of calling the police is very seldom used because people don’t know it exist, and it might mean the difference between life and death. Hopefully, none of you will have to use this, but I wanted to pass it along just in case you hadn’t heard of it. Please pass it along to everyone possible.
There is no validity to any of these posts, and none of them are new. In fact, the third one started circulating in an email as early as 2006, before migrating to Facebook. The first one has been circulating since at least 2010. The Facebook privacy one surfaces in a new form every time Facebook announces changes to its privacy policy. These are just a sample of the many myths that are out there. All of these have been discredited, and the validity can be easily checked. The next time you see a Facebook status like that, stop and think about it. How will sharing a picture 100 times provide a free heart transplant? If entering a PIN backwards would summon police, don’t you think that information might actually be shared by your bank? Who decided stating your rights in a Facebook status would provide any legal protection whatsoever? (For the record, you agree to Facebook’s Terms and Conditions when you create an account. Stating otherwise publicly doesn’t change anything).
While it’s not possible to completely stop these things from circulating, you can become part of the solution. Don’t blindly share or post anything just because everyone else is. It’s possible to quickly check whether a post is valid or not. I use Snopes.com to check these items out. For example, here’s the Snopes link debunking the backwards ATM PIN myth. If the story isn’t true, don’t spread it. While there’s not necessarily anything malicious about these myths, there’s no point in perpetuating them. Your friends will probably thank you for having a little less clutter in their feed, too.
6 Feb, 2014
 A recent post by KrebsonSecurity reports that the attacks on Target were made possible using stolen credentials from a third-party vendor, specifically an HVAC contractor for the company. While that may seem unlikely to you – how could an HVAC contractor have access to Target’s network? – it’s not surprising that in this day and age, HVAC systems can be remotely accessed and monitored. After all, we live in a digital age. We think nothing of programming our DVRs while away from home, or logging into our home thermostat to program it, so it should be no surprise that large systems have advanced capabilities. The surprising part is that credentials for the HVAC system would also allow access to the rest of Target’s network. The investigation is still underway, so there are a lot of unknowns. Did Target require some form of two-factor authentication for access, and if not, why not? Was the HVAC network segmented from the rest of the network? How frequently were passwords changed, if at all? I would assume Target is taking a hard look at some of their security practices, and in the light of this and the recent announcement of the Neiman-Marcus breach, a lot of other companies that process millions of credit cards should also be reviewing their practices.
A recent post by KrebsonSecurity reports that the attacks on Target were made possible using stolen credentials from a third-party vendor, specifically an HVAC contractor for the company. While that may seem unlikely to you – how could an HVAC contractor have access to Target’s network? – it’s not surprising that in this day and age, HVAC systems can be remotely accessed and monitored. After all, we live in a digital age. We think nothing of programming our DVRs while away from home, or logging into our home thermostat to program it, so it should be no surprise that large systems have advanced capabilities. The surprising part is that credentials for the HVAC system would also allow access to the rest of Target’s network. The investigation is still underway, so there are a lot of unknowns. Did Target require some form of two-factor authentication for access, and if not, why not? Was the HVAC network segmented from the rest of the network? How frequently were passwords changed, if at all? I would assume Target is taking a hard look at some of their security practices, and in the light of this and the recent announcement of the Neiman-Marcus breach, a lot of other companies that process millions of credit cards should also be reviewing their practices.
The Krebs article highlights another security issue, as well. The stolen data was transmitted using “drop” locations; compromised computers that stored the data, and that could be accessed by the hackers. While Target shoulders the brunt of the blame for this situation, it also underscores the importance of security at multiple levels, from home computers to small and medium businesses. An infected computer or server doesn’t just put the users of that system at risk; hackers can use that system for their own nefarious purposes, such as being an intermediate drop for stolen data.
The important thing to learn from this is the importance of protecting a network, regardless of where it is and what it’s doing. Even Fortune 500 companies and security professionals can be vulnerable. Limit access to your network. If 3rd parties need access, limit their access, monitor their use, and disable the access when not needed. Take security seriously, even at home. It’s not just your data that you might be protecting.
Image courtesy of chanpipat/FreeDigitalPhotos.net
18 Jan, 2014
It’s happened to me a number of times. The phone rings, and often the caller id display reads “Private.” Upon answering, I’m greeted by someone with a heavy Indian accent who informs me that he/she is calling from the Windows Support Center, and that for several weeks my PC has been sending out many error messages. This caller wants me to allow remote access to my computer so the errors can be analyzed, then fixed remotely, for a fee.

If you get one of these phone calls, hang up. First off, there are no “Windows Support Centers” that monitor error messages from your PC. They just don’t exist. Secondly, neither Microsoft, nor any of its partners, will place unsolicited calls and offer to fix your PC. The real purpose of these calls is to gain access to your PC. From that point, the caller could install malware to capture personal data, or alter settings to make your PC less secure. They’ll also show you fake alerts and problems in event viewer, in order to dupe you into paying for repairs. Once they have your credit card information, not only are you charged for unnecessary services, but you’ve just provided your credit card information to a scammer.
What if you’ve already succumbed to one of these calls? First off, change your password for your computer, bank accounts, email, etc., but don’t do this from the infected computer. Make the change from another PC. If your credit card has been charged, call your credit card company and work with them to reverse the charges. They can also work with you to monitor your card for fraudulent activity. Scan your computer with whatever antivirus program you use (you do use one, right?), and if you’re concerned, you can ask for help here at Geeks to Go! to help ensure that your computer is clean.
If you want more information about these types of scams, then visit Microsoft. For more information about telemarketing scams in the US, visit the FTC.
10 Dec, 2011
Death is never easy. We’ve all had to deal with the loss of a loved one, a mentor, a co-worker, etc. Today, the Geeks to Go family has to deal with the loss of a colleague, known online as SpySentinel. SpySentinel was a malware helper here, and in the past year became a mod. He was a respected member of our staff, and his death leaves a big hole in our hearts. In real life, he was a college student. He started his college career in the computing field, but realized it wasn’t where his heart was. He changed his major to elementary education, and was looking forward to becoming a teacher and mentor to young children. He would have succeeded, had he had the opportunity.
Read the rest of this entry »
5 Oct, 2011
 The passing of Steve Jobs means there will be, or already is, a proliferation of blogs, essays, and articles remembering a man who helped revolutionize how we use computers, how we listen to music, and how we use our phones. A fitting finale would have been the announcement of the iPhone 5 the day prior to his passing, but it wasn’t to be. I could write the typical article lauding his accomplishments and mourning his death at much too young an age (being just 5 years younger, I wholeheartedly feel he died much too young). I don’t feel, however, that I could do justice to his life and accomplishments, and much has been written already. Instead, I’ve decided to give thanks for his creative genius, for that, coupled with the equally creative genius of that other computer company (no, not Dell; Microsoft) has made sites such as Geeks to Go a haven for those desperately seeking help for these sometimes confusing and uncooperative pieces of technology upon which we so desperately rely. Read the rest of this entry »
The passing of Steve Jobs means there will be, or already is, a proliferation of blogs, essays, and articles remembering a man who helped revolutionize how we use computers, how we listen to music, and how we use our phones. A fitting finale would have been the announcement of the iPhone 5 the day prior to his passing, but it wasn’t to be. I could write the typical article lauding his accomplishments and mourning his death at much too young an age (being just 5 years younger, I wholeheartedly feel he died much too young). I don’t feel, however, that I could do justice to his life and accomplishments, and much has been written already. Instead, I’ve decided to give thanks for his creative genius, for that, coupled with the equally creative genius of that other computer company (no, not Dell; Microsoft) has made sites such as Geeks to Go a haven for those desperately seeking help for these sometimes confusing and uncooperative pieces of technology upon which we so desperately rely. Read the rest of this entry »
20 May, 2011
 I have been an avid reader my entire life. As a young adult, I would sometimes spend several hours a day reading; I’ve often stayed up past my bedtime to finish a good book; and it’s not uncommon for me to take six or seven books on vacation and read them all. I was very intrigued by the Kindle when it was first released, because the thought of having access to multiple books, newspapers and magazines in one device was extremely attractive. On the other hand, I like reading the physical book, or curling up on the couch with the paper and a cup of coffee. During the winter of 2009-2010, when back-to-back blizzards meant no newspaper delivery for a week, I was bemoaning the lack of the newspaper; my husband pointed out I could read it online, but I’ve tried it and I just don’t enjoy it. Read the rest of this entry »
I have been an avid reader my entire life. As a young adult, I would sometimes spend several hours a day reading; I’ve often stayed up past my bedtime to finish a good book; and it’s not uncommon for me to take six or seven books on vacation and read them all. I was very intrigued by the Kindle when it was first released, because the thought of having access to multiple books, newspapers and magazines in one device was extremely attractive. On the other hand, I like reading the physical book, or curling up on the couch with the paper and a cup of coffee. During the winter of 2009-2010, when back-to-back blizzards meant no newspaper delivery for a week, I was bemoaning the lack of the newspaper; my husband pointed out I could read it online, but I’ve tried it and I just don’t enjoy it. Read the rest of this entry »
24 Nov, 2009
 More and more frequently, we’ve had forum members and even staff receiving warnings from their antivirus program, from McAfee Site Advisor, or some other source of online protection that Geeks to Go is a dangerous site or contains dangerous links. This is untrue – Geeks to Go is very safe, but we mistakenly get flagged. This is known as a false positive. Why does this happen? There are a few reasons.
More and more frequently, we’ve had forum members and even staff receiving warnings from their antivirus program, from McAfee Site Advisor, or some other source of online protection that Geeks to Go is a dangerous site or contains dangerous links. This is untrue – Geeks to Go is very safe, but we mistakenly get flagged. This is known as a false positive. Why does this happen? There are a few reasons.
Many security suites and protection programs are adding website screening as part of their overall protection, and some browsers also have website blocking built-in to them. I’ve had Firefox block sites on more than one occasion while doing research, and I’m glad when it does. Much of the malware we encounter gets installed as a drive-by download, meaning simply visiting the wrong site can infect your computer. Protecting against these things would seem to be a good thing. However, these programs are often relying on heuristics to identify potentially dangerous downloads, meaning they’re looking at the characteristics of a file to try and determine if it’s dangerous. In addition, there are many different security products available, and they all have different means to characterize potentially dangerous downloads.
Read the rest of this entry »
7 Jul, 2008
 In the fourth installment of the home data backup series, we’re going to review Microsoft’s Windows Home Server, the first home server product they’ve offered. While this product offers many features, I’m going to be focusing on its use as a backup/recovery solution. Additional features will be covered in a later review.
In the fourth installment of the home data backup series, we’re going to review Microsoft’s Windows Home Server, the first home server product they’ve offered. While this product offers many features, I’m going to be focusing on its use as a backup/recovery solution. Additional features will be covered in a later review.
Windows Home Server, or WHS, is based on Microsoft’s Windows Server 2003 platform, but has been re-packaged to make it much more friendly for the home user. It uses a simple console interface to provide management functions, such as adding users, configuring backups, and managing shared folders. The typical WHS device is a computer that is connected to your home network and managed through another PC on the network. It’s capable of performing a headless boot, meaning there is no requirement for a keyboard, mouse, or monitor. Because it doesn’t require these devices, it can be tucked into a corner and takes up relatively little room. I have mine sitting in my basement, next to my router. Out of sight does not mean out of mind, however; this system is always running, monitoring the health of your network and helping to keep your critical data safe.
Read the rest of this entry »
23 Jun, 2008
 Sugarsync (www.sugarsync.com) is one of the online storage system offerings that are out there, and I recently had the opportunity to test the service out. This feature-rich product is more than just an offsite storage system; Sugarsync not only allows you to sync your computer with the online backups, but allows you to sync files across multiple computers, access your data from anywhere, including your mobile phone, and provides both dynamic and static storage spaces.
Sugarsync (www.sugarsync.com) is one of the online storage system offerings that are out there, and I recently had the opportunity to test the service out. This feature-rich product is more than just an offsite storage system; Sugarsync not only allows you to sync your computer with the online backups, but allows you to sync files across multiple computers, access your data from anywhere, including your mobile phone, and provides both dynamic and static storage spaces.
Everyone knows the importance of keeping good backups of your computer data, especially anyone who’s ever lost data due to a hard drive crash, natural catastrophe, or any other reason. Many people, however, don’t back their data up regularly; it can be a time-consuming process that’s not always easily automated. This is one of a series of articles we’re doing on ways to backup your data. Read our previous article for an overview of different backup strategies available.
Read the rest of this entry »





 I have been an avid reader my entire life. As a young adult, I would sometimes spend several hours a day reading; I’ve often stayed up past my bedtime to finish a good book; and it’s not uncommon for me to take six or seven books on vacation and read them all. I was very intrigued by the Kindle when it was first released, because the thought of having access to multiple books, newspapers and magazines in one device was extremely attractive. On the other hand, I like reading the physical book, or curling up on the couch with the paper and a cup of coffee. During the winter of 2009-2010, when back-to-back blizzards meant no newspaper delivery for a week, I was bemoaning the lack of the newspaper; my husband pointed out I could read it online, but I’ve tried it and I just don’t enjoy it.
I have been an avid reader my entire life. As a young adult, I would sometimes spend several hours a day reading; I’ve often stayed up past my bedtime to finish a good book; and it’s not uncommon for me to take six or seven books on vacation and read them all. I was very intrigued by the Kindle when it was first released, because the thought of having access to multiple books, newspapers and magazines in one device was extremely attractive. On the other hand, I like reading the physical book, or curling up on the couch with the paper and a cup of coffee. During the winter of 2009-2010, when back-to-back blizzards meant no newspaper delivery for a week, I was bemoaning the lack of the newspaper; my husband pointed out I could read it online, but I’ve tried it and I just don’t enjoy it.  More and more frequently, we’ve had forum members and even staff receiving warnings from their antivirus program, from McAfee Site Advisor, or some other source of online protection that Geeks to Go is a dangerous site or contains dangerous links. This is untrue – Geeks to Go is very safe, but we mistakenly get flagged. This is known as a false positive. Why does this happen? There are a few reasons.
More and more frequently, we’ve had forum members and even staff receiving warnings from their antivirus program, from McAfee Site Advisor, or some other source of online protection that Geeks to Go is a dangerous site or contains dangerous links. This is untrue – Geeks to Go is very safe, but we mistakenly get flagged. This is known as a false positive. Why does this happen? There are a few reasons. In the fourth installment of the
In the fourth installment of the  Sugarsync (
Sugarsync (